Defining a Request Security Group
Beyond this short introduction, request groups and request security groups are discussed in greater detail, as part of a broader range of topics not necessarily limited to application security, in Chapter 7 - Managing Concurrent Programs and Reports.
See:
Organizing Programs into Request Groups
Request Groups
Using Request Security
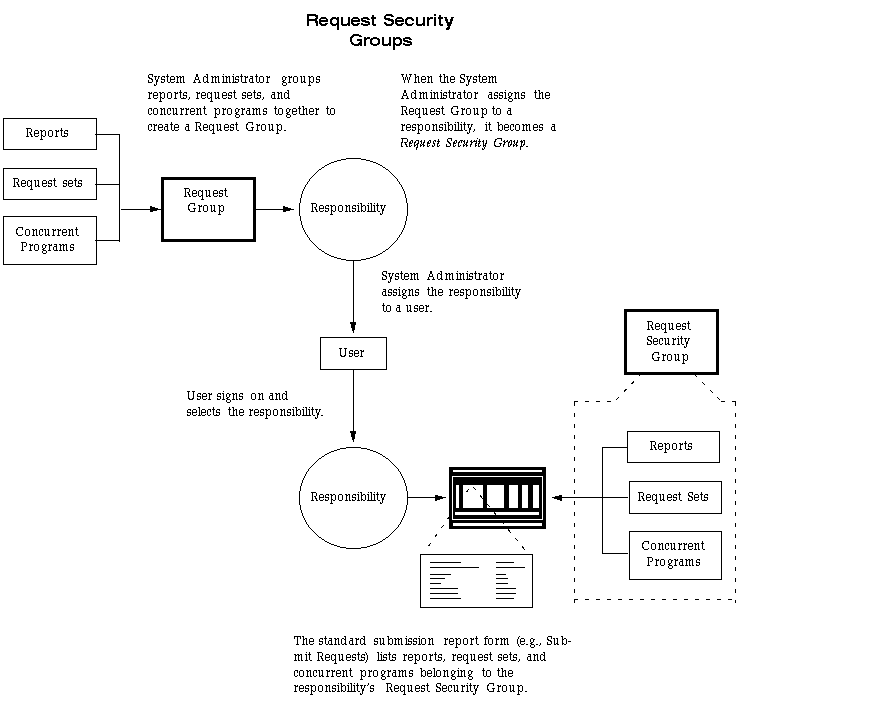
You use request security to specify the reports, request sets, and concurrent programs that your users can run from a standard submission form, such as the Submit Requests form.
To set up request security, you define a request group using the Request Groups form. Using the Responsibilities form, you assign the request group to a responsibility. The request group is then referred to as a request security group. See: Request Security Groups.
You can define a request group to contain single requests, request sets, or all the requests and request sets in an application.
If you choose to include all the requests and requests sets in an application, the user has automatic access to any new requests and request sets (without owners) in the future.
A request security group can contain requests and request sets from different applications. If you want to define request security groups that own requests from different applications, please refer to the discussion on Data Groups. See: Defining Data Groups.
Individual Requests and Request Sets
Reports or concurrent programs that are not included in a request security group on an individual basis, but that do belong to a request set included in a request security group, have the following privileges:
- Users cannot use the Submit Requests form to run single requests and request sets that are not in their responsibility's request security group.
- Users can, however, run request sets that contain requests that are not in their request security group, if the request set is in their request security group.
If you assign a request set, but not the requests in the set, to a request security group, the user:
- cannot edit request information in the request set definition
- cannot stop specific requests in the set from running
- can edit the request set by deleting requests from it or adding other requests to it, only if the user is the assigned owner of the request set
The Request Security Groups figure illustrates the relationship between a request security group, application user, and a responsibility.
See Also
Request Sets and Owners
System Administrator Request Set Privileges
Overview of Oracle Applications Security
Defining a Responsibility
Form Functions
Menus
Responsibilities
Users
Security Reports
