Release 2 (9.2)
Part Number A96573-01
Home |
Book List |
Contents |
Index |
 Master Index |
 Feedback |
| Oracle Advanced Security Administrator's Guide Release 2 (9.2) Part Number A96573-01 |
|
This appendix describes how to configure and use Microsoft Active Directory as the LDAP directory for Oracle Advanced Security Enterprise User Security in the following topics:
Oracle9i provides two features which make use of a directory server. These features are briefly described in the following sections:
Both features have been enabled to work with Microsoft's Active Directory.
This feature enables clients to connect to the database server making use of information stored centrally in an LDAP-compliant directory server such as Active Directory. For example, any net service name previously stored in the tnsnames.ora file can now be stored in Active Directory.
|
Note: Database service and net service name entries stored in an Oracle Names Server can be migrated to a directory server using the Oracle Names Server Control utility. See Oracle9i Net Services Administrator's Guide for more information. |
This feature enables you to create and store Oracle9i database information as directory objects in an LDAP-compliant directory server. For example, an administrator can create and store enterprise users and roles for the Oracle9i database in the directory, which helps centralize the administration of users and roles across multiple databases.
This appendix assumes you are familiar with enterprise user security terms and concepts. If any of the following terms are unfamiliar to you, then you should review Chapter 15, "Managing Enterprise User Security" and Chapter 19, "Using Oracle Enterprise Security Manager".
|
Note: You must license Oracle Advanced Security to use Active Directory to manage an enterprise role. |
In addition to directory naming and enterprise user security integration with a directory server, the following Oracle9i features have been specifically integrated with Active Directory:
Active Directory is the LDAP-compliant directory server included with Windows 2000. Active Directory stores all Windows 2000 information, including users, groups, and policies. Active Directory also stores information about network resources (such as databases) and makes this information available to application users and network administrators. Active Directory enables users to access network resources with a single login. The scope of Active Directory can range from storing all the resources of a small computer network to storing all the resources of several wide areas networks (WANs).
When using Oracle features that support Active Directory using LDAP, ensure that the Active Directory computer can be successfully reached using all of the TCP/IP hostname forms possible to reach the domain controller. For example, if the hostname of the domain controller is server1 in the domain acme.com, then ensure that you can ping that computer using all of the following:
Active Directory often issues referrals back to itself in one or more of these forms, depending upon the operation being performed. If all of the forms cannot be used to reach the Active Directory computer, then some LDAP operations may fail.
Oracle Net Configuration Assistant enables you to configure client computer and Oracle9i database server access to a directory server. When Oracle Net Configuration Assistant starts at the end of Oracle9i database installation or is manually started after installation, it prompts you to specify a directory server type to use. When you select Active Directory as the directory server type, Oracle Net Configuration Assistant automatically:
If the Active Directory server through which client connections are accessing an Oracle9i database is shut down, another Active Directory server is automatically discovered and begins providing connection information. This minimizes client connection downtime.
When using the Oracle Net Configuration Assistant to complete directory usage configuration against Active Directory, Oracle schema creation can fail due to Active Directory display not being populated with all 24 default languages. Before running the Oracle Net Configuration Assistant to complete directory access configuration, verify that display specifiers for all 24 languages are populated by entering the following at the command prompt:
ldifde -p OneLevel -d cn=DisplaySpecifiers,cn=Configuration,domain context -f temp file
where:
domain context is the domain context for this Active Directory server. For example dc=acme,dc=comtemp file is a file where you want to put the output.If the command reports that less than 24 entries were found, you can still use the Oracle Net Configuration Assistant. However, it will report that Oracle schema creation failed when all that happened was that display specifiers for some languages were not created.
Oracle9i database services, net service names, and enterprise role entries in Active Directory can be displayed and tested in two Windows 2000 tools:
Windows Explorer displays the hierarchical structure of files, directories, and local and network drives on your computer. It can display and test Oracle9i database service and net service name objects.
Active Directory Users and Computers is an administrative tool installed on Windows servers configured as domain controllers. This tool enables you to add, modify, delete, and organize Windows 2000 accounts and groups and publish resources in your organization's directory. Like Windows Explorer, it can display and test Oracle9i database service and net service name objects. But it can also manage access control.
The property menus of Oracle9i database service and net service name objects in Windows Explorer and Active Directory Users and Computers have been enhanced. When you right-click these Oracle directory objects, you now see two new options for testing connectivity:
The Test option starts an application that tests whether the username, password, and net service name you initially entered can actually connect to the Oracle9i database. The Connect with SQL*Plus option starts SQL*Plus, which enables you to perform database administration, run scripts, and so on.
| See Also:
"Testing Connectivity from Microsoft Tools" for more information |
Oracle directory object type descriptions in Active Directory have been enhanced to make them easier to understand. In the right pane of Figure E-1, for example, the Type column reveals that ss2 is an Oracle NetService.
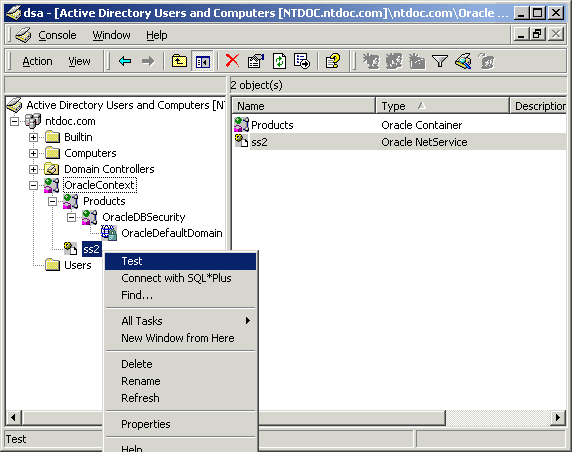
Text description of the illustration adtest.gif
The Oracle9i database and configuration tools can use the login credentials of the currently logged on Windows user to connect to Active Directory automatically (that is, without having to re-enter the login credentials). This feature has two benefits:
If the Oracle9i database and Oracle Net Services are installed and configured to access Active Directory, then Active Directory Users and Computers will display Oracle directory objects, as illustrated in Figure E-2:
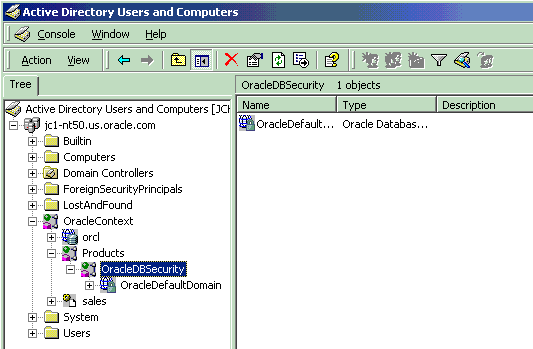
Text description of the illustration adusrext.gif
Table E-1 describes the Oracle directory objects appearing in Figure E-2.
| Object | Description |
|---|---|
|
|
The domain in which you created your Oracle Context. This domain (also known as the administrative context) contains various Oracle entries to support directory naming and enterprise user security. Oracle Net Configuration Assistant automatically discovers this information during Oracle9i database integration with Active Directory. |
|
|
The top-level Oracle entry in the Active Directory tree. It contains Oracle9i database service and net service name object information. All Oracle software information is placed in this folder. |
|
|
This example's Oracle9i database service name |
|
|
A folder for Oracle product information. |
|
|
A folder for database security information. |
|
|
The default enterprise domain created. You can create additional enterprise domains with Oracle Enterprise Security Manager. |
|
|
This example's net service name object |
|
|
The folder for the three Oracle security groups. See section "Access Control List Management for Oracle Directory Objects" for more information. Enterprise users and roles created with Oracle Enterprise Security Manager also appear in this folder. |
If you want to use Net Directory Naming or Enterprise User Security with Active Directory, then you must have certain Microsoft and Oracle software releases, and you must create an Oracle Schema and an Oracle Context. These requirements are discussed in the following sections:
|
Note: The Oracle schema and Oracle Context can both be created by running Oracle Net Configuration Assistant. |
If you are using Active Directory with Oracle on Windows 2000 or Windows NT, then ping the DNS domain name of your Windows 2000 domain. If this does not work, then perform either of the following tasks:
For example, if your Windows 2000 domain is sales, the DNS domain name for this domain is sales.acme.com. The IP address is of the form 001.002.003.0.
hosts or lmhosts file.
On the Windows 2000 computer, either 001.002.003.0 can be set as the DNS, or 001.002.003.0 sales.acme.com can be added to the hosts or lmhosts file.
If this step is not performed, then errors such as the following are returned when using Active Directory:
Cannot Chase Referrals
On Windows NT and Windows 2000, the Oracle database service runs in the security context of the LocalSystem or a specific local or domain user. When using Oracle8i release 8.1.7 with Active Directory, if the database service runs in the security context of LocalSystem, manually add the computer name in which the database service is running. This enables you to access control entries on the OracleDBSecurity container object in the Active Directory with read permissions on the OracleDBSecurity container object.
For example, if the database service OracleServiceORCL is running in the security context of LocalSystem in the computer mypc1, then add mypc1 with READ permissions ON OracleDBSecurity object to the access control entries on the OracleDBSecurity container object.
You must create an Oracle schema to use net directory naming and enterprise user security features with Active Directory. A schema is a set of rules for Oracle Net Services and Oracle9i database entries and their attributes stored in Active Directory. The following restrictions apply to creating an Oracle schema to use with Active Directory:
To create an Oracle schema:
See Also:
|
You must create an Oracle Context to use net directory naming and enterprise user security features with Active Directory. Oracle Context is the top-level Oracle entry in the Active Directory tree. It contains Oracle9i database service and Oracle Net service name object information.
See Also:
|
For client computers from which you want to manage Oracle9i enterprise users, roles and domains, you must have Oracle8i Client release 8.1.6 or later and one of the following Microsoft products:
For the database server you must have Oracle8i Database release 8.1.6 or later. This is required for registering the database service as an object in Active Directory. The database server can use either of the following Microsoft products:
In addition to these software requirements, both the client computers and the database server must be running in a Windows 2000 domain.
For the database server you must have Oracle8i Database release 8.1.6 or later. This is required for registering the database service as an object in Active Directory. The database server can use either of the following Microsoft products:
The remote computer must have Oracle Enterprise Manager Console release 2.1 or later, which includes:
The remote computer can use either of the following Microsoft products:
In addition to these software requirements, both the remote computer and the database server must be running in a Windows 2000 domain.
Oracle9i integration with Active Directory enables you to take advantage of operating system user authentication and role authorization. Perform the following tasks to integrate Oracle components with Active Directory:
Read "Integration with Active Directory", "Requirements for Using Oracle9i with Active Directory", and the Oracle9i Database Installation Guide for Windows for information on pre-installation and configuration issues.
Set the OSAUTH_X509_NAME registry parameter to true to enable client users to access the Oracle9i database as X.509-compliant enterprise users. Active Directory will then be used to identify the client username and authorize roles. This parameter setting is required only if you want to use enterprise users and roles.
When the parameter is set to false (the default setting), the client user is identified as an external user, and the user's role authorization uses the Oracle9i database data dictionary.
To set the OSAUTH_X509_NAME registry parameter:
> Run.regedt32 in the Open field, and click OK.
The Registry Editor window appears.
HKEY_LOCAL_MACHINE\SOFTWARE\ORACLE\HOMEID.
where ID is the Oracle home that you want to edit.
OSAUTH_X509_NAME exists, double-click OSAUTH_X509_NAME.
A String Editor dialog box appears.
Otherwise, add OSAUTH_X509_NAME as a registry value of type REG_EXPAND_SZ.
true in the String field.The registry editor exits.
Oracle Enterprise Security Manager is included as an integrated application with Oracle Enterprise Manager. You can use Oracle Enterprise Security Manager to create and manage enterprise users, roles, and domains. You can also use it to assign enterprise users and groups to enterprise roles.
The administrator using Oracle Enterprise Security Manager must be a member of the security group OracleDBSecurityAdmin. By default, the administrator who created the Oracle Context (that is, configured the Oracle9i database to work with a directory server) is a member of this security group. Only members of this security group are authorized to use all features of Oracle Enterprise Security Manager. To add additional users manually, see "Access Control List Management for Oracle Directory Objects".
Select Login from the Directory Server main menu to access a dialog box for selecting the authentication protocol appropriate to your environment. Choose NT Native Authentication if you are running an Oracle9i database on a Windows NT 4.0 or Windows 2000 computer in a Windows 2000 domain with Active Directory. Oracle Enterprise Security Manager automatically uses Windows native authentication if running in a Windows 2000 domain.
Choose Simple Authentication if the other available selections do not work. Simple authentication can be used with either Oracle Internet Directory or Active Directory, but it is less secure.
This section describes how to connect to an Oracle9i database through Active Directory. This section contains these topics:
When using Oracle Net directory naming, client computers connect to a database by specifying the database or net service name entry that appears in the Oracle Context. For example, if the database entry under the Oracle Context in Active Directory is orcl, and the client and Oracle9i database are in the same domain, then a user connects to the database through SQL*Plus by entering the following connect string:
SQL> CONNECT scott/tiger@orcl
If the client and Oracle9i database are in different domains, a user connects to the database through SQL*Plus by entering:
SQL> CONNECT scott/tiger@orcl.domain
where domain is the domain in which the Oracle9i database is located.
These connect strings follow DNS-style conventions. While Active Directory also supports connections using X.500 naming conventions, Oracle recommends DNS-style conventions because they are easier to use.
DNS-style conventions enable client users to access an Oracle9i database through a directory server by entering minimal connection information, even when the client computer and Oracle9i database are in separate domains. Names following the X.500 convention are longer, especially when the client and Oracle9i database are located in different domains (also known as administrative contexts).
| See Also:
"Configuration Management Concepts" in the Oracle9i Net Services Administrator's Guide for more information about X.500 naming conventions |
Oracle directory objects in Active Directory are integrated with two Microsoft tools:
You can perform the following tasks from within these Microsoft tools:
To test connectivity:
To start Windows Explorer:
To start Active Directory Users and Computers:
Choose Start > Programs > Administrative Tools > Active Directory Users and Computers
A menu appears with several options. The two that concern us here are Test and Connect with SQL*Plus:

A status message appears describing the status of your connection attempt:
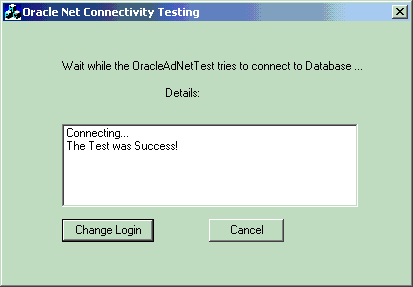
The Oracle SQL*Plus Login dialog appears:
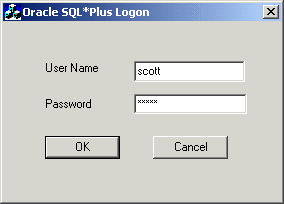
A status message appears describing the status of your connection attempt.
Access Control Lists provide Active Directory security by specifying:
Three security groups are automatically created when the Oracle Context is created in Active Directory. The user configuring access (and thus creating the Oracle Context) is automatically added to each group. The groups are:
The OracleDBSecurityAdmin group is for the creator of the Oracle Context. Users in this group can also:
The OracleDBCreator group is for the creator of the Oracle9i database. The domain administrator is automatically a member of this group.Users in this group can:
Users in the OracleNetAdmins group can:
You can add or remove users or change permission settings in all three security groups with Active Directory Users and Computers. You can also use Oracle Enterprise Security Manager with OracleDBSecurityAdmin and OracleDBCreator but not with OracleNetAdmins.
This section describes how to use Active Directory Users and Computers.
|
Note: Use Active Directory Users and Computers to perform the procedures described in this section. Windows Explorer does not provide the necessary functionality. |
To add or remove users or change permission settings:
This enables you to view and edit information that is normally hidden.
The three security groups appear in the right window pane:
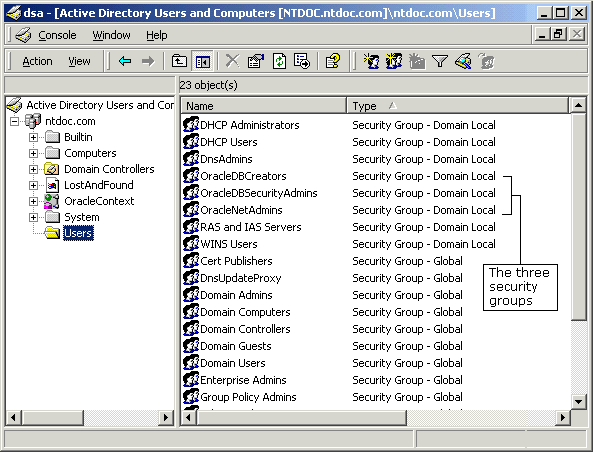
A menu appears with several options.
If you want to add or remove users, proceed to step 8.
The Properties dialog for the group you selected appears (in this example, OracleDBSecurityAdmins):
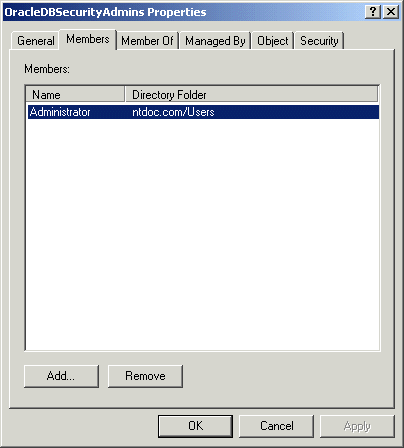
The Select Users, Contacts, Computers, or Groups dialog appears.
Your selections appear in the Select Users, Contacts, Computers, or Groups dialog.
The Permission Entry dialog for the security group you selected appears:
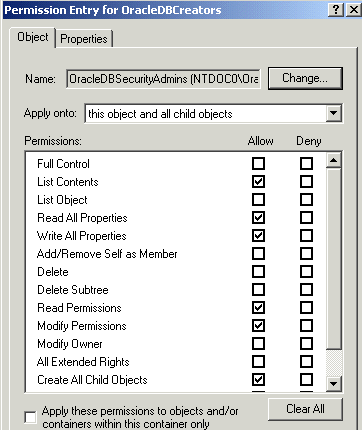
A default enterprise domain, OracleDefaultDomain, is created in your Oracle Context. If you do not want to use this domain or if you want to create another domain, then use Oracle Enterprise Security Manager to create additional enterprise domains. These domains are added under the OracleDBSecurity folder.
|
 Copyright © 1996, 2002 Oracle Corporation. All Rights Reserved. |
|