| Oracle® Enterprise Manager Advanced Configuration 10g Release 5 (10.2.0.5) Part Number E10954-03 |
|
|
PDF · Mobi · ePub |
| Oracle® Enterprise Manager Advanced Configuration 10g Release 5 (10.2.0.5) Part Number E10954-03 |
|
|
PDF · Mobi · ePub |
This chapter describes how to configure Oracle Enterprise Manager Security. Specifically, this chapter contains the following sections:
Oracle Enterprise Manager provides tools and procedures to help you ensure that you are managing your Oracle environment in a secure manner. The following sections describe the security features provided by Enterprise Manager.
The goals of Oracle Enterprise Manager security are:
To be sure that only users with the proper privileges have access to critical monitoring and administrative data.
This goal is met by requiring username and password credentials before users can access the Enterprise Manager consoles and appropriate privileges for accessing the critical data. This includes access to the Oracle Enterprise Manager 10g Grid Control Console and the Oracle Enterprise Manager 10g Application Server Control Console.
To be sure that all data transferred between Enterprise Manager components is transferred in a secure manner and that all data gathered by each Oracle Management Agent can be transferred only to the Oracle Management Service for which the Management Agent is configured.
This goal is met by enabling Enterprise Manager Framework Security. Enterprise Manager Framework Security automates the process of securing the Enterprise Manager components installed and configured on your network.
Oracle Enterprise Manager supports different classes of Oracle users, depending upon the environment you are managing and the context in which you are using Oracle Enterprise Manager 10g. For example:
The Grid Control Console provides support for creating and managing Enterprise Manager administrator accounts.
The Enterprise Manager administrators you create and manage in the Grid Control Console are granted privileges and roles to log in to the Grid Control Console and to manage specific target types and to perform specific management tasks.
The default super administrator for the Grid Control Console is the SYSMAN user, which is a database user associated with the Oracle Management Repository. You define the password for the SYSMAN account during the Enterprise Manager installation procedure.
Oracle Application Server administrators use the Oracle Application Server administrator account (ias_admin) to log in to the Application Server Control Console.
You use the ias_admin account to manage the components of a specific Oracle Application Server instance. You define the password for the ias_admin account during the Oracle Application Server installation procedure.
By restricting access to privileged users and providing tools to secure communications between Oracle Enterprise Manager 10g components, Enterprise Manager protects critical information in the Oracle Management Repository.
The Management Repository contains management data that Enterprise Manager uses to help you monitor the performance and availability of your entire enterprise. This data provides you with information about the types of hardware and software you have deployed, as well as the historical performance and specific characteristics of the applications, databases, applications servers, and other targets that you manage.
The Management Repository also contains information about the Enterprise Manager administrators who have the privileges to access the management data.
Authorization and access enforcement for Enterprise Manager is controlled as follows:
When you use the Grid Control Console, you create and manage Enterprise Manager administrator accounts. The SYSMAN super administrator can assign specific privileges and roles to each of the additional administrators. These privileges and roles control the targets an administrator can manage and the specific types of tasks the administrator can perform.
See Also:
"About Administrators and Roles" in the Enterprise Manager online HelpWhen you use the Application Server Control Console, access to the Console is restricted to administrators who use the ias_admin administrator's account. The ias_admin account is set up automatically and you assign a password for the account during the Oracle Application Server installation procedure.
See Also:
Oracle Application Server 10g Administrator's Guide for more information about theias_admin accountSee Also:
"About Administrators and Roles" in the Enterprise Manager online HelpAs a Web-based application, Enterprise Manager relies on industry-standard technologies to provide secure access to the Oracle Enterprise Manager 10g Grid Control Console and Application Server Control Console.
When you configure security for the Oracle Enterprise Manager 10g Grid Control Console, Enterprise Manager Framework Security provides secure communications between the components of your Enterprise Manager installation.
See Also:
"Configuring Security for Grid Control" for more information about the Enterprise Manager Framework SecurityOracle HTTP Server Administrator's Guide for information about configuring security for your Oracle HTTP Server
Enterprise Manager Grid Console application is deployed in a OPMN managed OC4J instance. When you configure security for the Grid Console, Enterprise Manager uses the standard security services of OC4J znd OHS to protect your management data.
Oracle Enterprise Manager 10g takes advantage of Oracle Identity Management in two ways:
First, you can configure the Grid Control Console so it uses Oracle Application Server Single Sign-On. Administrators can then use their Single Sign-On credentials to log in to the Grid Control Console.
See Also:
Oracle Application Server Single Sign-On Administrator's Guide for general information about Oracle Application Server Single Sign-OnSecond, you can take advantage of the Enterprise User Security features of the Oracle database. Enterprise User Security provides single sign-on (SSO) or single password authentication for your database users.
See Also:
"Managing Enterprise User Security" in the Oracle Advanced Security Administrator's GuideNote:
You can configure Enterprise Manager to either use Oracle Application Server Single Sign-On or the Enterprise User Security features. You cannot use both options at the same time.This section contains the following topics:
Overview of the Steps Required to Enable Enterprise Manager Framework Security
Enabling Security with Multiple Management Service Installations
Enterprise Manager Framework Security provides safe and secure communication channels between the components of Enterprise Manager. For example, Framework Security provides secure connections between your Oracle Management Service and its Management Agents.
See Also:
Oracle Enterprise Manager Concepts for an overview of Enterprise Manager componentsEnterprise Manager Framework Security works in concert with—but does not replace—the security features you should enable for your Oracle HTTP Server. Oracle HTTP Server is part of the Oracle Application Server instance that is used to deploy the Management Service J2EE Web application.
Figure 6-1 shows how Enterprise Manager Framework Security provides security for the connections between the Enterprise Manager components.
Figure 6-1 Enterprise Manager Framework Security
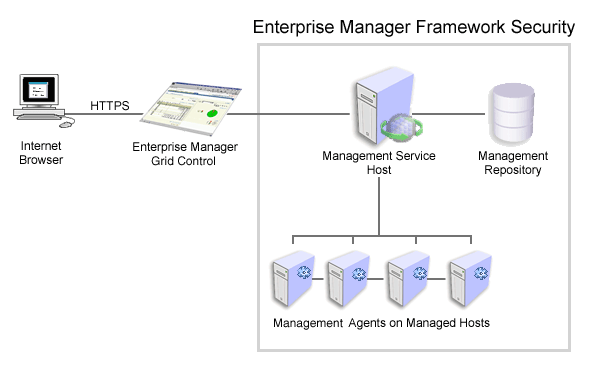
Enterprise Manager Framework Security implements the following types of secure connections between the Enterprise Manager components:
HTTPS and Public Key Infrastructure (PKI) components, including signed digital certificates, for communications between the Management Service and the Management Agents.
See Also:
Oracle Security Overview for an overview of Public Key Infrastructure features, such as digital certificates and public keysOracle Advanced Security for communications between the Management Service and the Management Repository.
To enable Enterprise Manager Framework Security, you must configure each of the Enterprise Manager components in a specific order. The following list outlines the process for securing the Management Service and the Management Agents that upload data to the Management Service:
Note:
The Enterprise Manager components are configured during installation. You can use the following commands if you want to reconfigure any of the components.Use the opmnctl stopall command to stop the Management Service, the Oracle HTTP Server, and the other components of the Oracle Application Server that are used to deploy the Management Service.
Use emctl secure oms to enable security for the Management Service.
Restart the Management Service, the Oracle HTTP Server, OracleAS Web Cache, and the other application server components using the opmnctl startall command.
For each Management Agent, stop the Management Agent, use the emctl secure agent command to enable security for the Management Agent, and restart the Management Agent.
After security is enabled for all the Management Agents, use the emctl secure lock command to restrict HTTP Access to the Management Service. This will ensure that Management Agents for which security has not been enabled will not be able upload data to the Management Service.
The following sections describe how to perform each of these steps in more detail.
Note:
To resolve errors fromemctl secure operations, refer to $ORACLE_HOME/sysman/log/secure.log for more details.To enable Enterprise Manager Framework Security for the Management Service, you use the emctl secure oms utility, which is located in the following subdirectory of the Management Service home directory:
$ORACLE_HOME/bin
The emctl secure oms utility performs the following actions:
Generates a Root Key within your Management Repository. The Root Key is used during distribution of Oracle Wallets containing unique digital certificates for your Management Agents.
Modifies your Oracle HTTP Server to enable an HTTPS channel between your Management Service and Management Agents, independent from any existing HTTPS configuration that may be present in your Oracle HTTP Server.
Enables your Management Service to accept requests from Management Agents using Enterprise Manager Framework Security.
To run the emctl secure oms utility you must first choose an Agent Registration Password. The Agent Registration password is used to validate that future installation sessions of Oracle Management Agents and Oracle Management Services are authorized to load their data into this Enterprise Manager installation.
To enable Enterprise Manager Framework Security for the Oracle Management Service:
Change directory to the following directory in the Management Service home:
ORACLE_HOME/opmn/bin
Stop the Management Service, the Oracle HTTP Server, and the other application server components using the following command:
$PROMPT> ./opmnctl stopall
Change directory to the following directory in the Management Service home:
ORACLE_HOME/bin
Enter the following command:
$PROMPT> ./emctl secure oms
You will be prompted for the Enterprise Manager Root Password. Enter the SYSMAN password.
You will be prompted for the Agent Registration Password, which is the password required for any Management Agent attempting to secure with the Management Service. Specify an Agent Registration Password for the Management Service.
When the operation is complete, restart the Management Service, the Oracle HTTP Server, and OracleAS Web Cache:
$PROMPT> cd $ORACLE_HOME/opmn/bin $PROMPT> ./opmnctl startall
After the Management Service restarts, test the secure connection to the Management Service by browsing to the following secure URL using the HTTPS protocol:
https://hostname.domain:https_upload_port/em
For example:
https://mgmthost1.acme.com:1159/em
If the Management Service security has been enabled, your browser displays the Enterprise Manager Login page.
Note:
The 1159 port number is the default secure port used by the Management Agents to upload data to the Management Service. This port number may vary if the default port is unavailable.Caution:
While theemctl secure oms command provides immediate HTTPS browser access to the Grid Control Console by using the secure Management Agent upload port, it does not enable security for the default OracleAS Web Cache port that your administrators use to display the Grid Control Console.
To enable security for users who access the Grid Control through OracleAS Web Cache, refer to Oracle Application Server 10g Security Guide.
Example 6-1 Sample Output of the emctl secure oms Command
$PROMPT> ./emctl secure oms Oracle Enterprise Manager 10g Release 5 Grid ControlCopyright (c) 1996, 2009 Oracle Corporation. All rights reserved.Securing OMS... Started.Securing OMS... Successful
Alternatively, you can enter the emctl secure oms command all on one line, but if you enter the command on one line, the passwords you enter will be displayed on the screen as you type the command.
Example 6-2 Usage of the emctl secure oms Command (II)
$PROMPT> emctl secure oms [-sysman_pwd <sysman password>][-reg_pwd <registration password>][-host <hostname>][-reset][-secure_port <secure_port>][-upload_http_port <upload_http_port>][-slb_port <slb port>][-slb_console_port <slb console port>][-root_dc <root_dc>][-root_country <root_country>][-root_state <root_state>][-root_loc <root_loc>][-root_org <root_org>][-root_unit <root_unit>] [-root_email <root_email>][-wallet <wallet_loc> -trust_certs_loc <certs_loc>] [-wallet_pwd <pwd>][-key_strength <strength>][-cert_validity <validity>]
The parameters are explained below:
sysman_pwd - Oracle Management Repository user password.
reg_pwd - The Management Agent registration password.
host - The host name to be used in the certificate used by the Oracle Management Service. You may need to use the SLB host name if there is an SLB before the Management Service.
reset - If the Oracle Management Service is secured with this option, a new root certificate is generated. All the agents and the Oracle Management Services need to be resecured for use with the new root certificate.
secure_port - The port to be used for secure communication. The default value is 4888.
upload_http_port - The port used for upload communications.
slb_port - This parameter is required when Server Load Balancer is used. It specifies the secure upload port configured in the Server Load Balancer.
slb_console_port - This parameter is required when Server Load Balancer is used. It specifies the secure upload port configured in the Server Load Balancer.
trust_certs_loc - The location of the trusted_certs.txt (required when third party certificates are used).
root_dc - The domain component used in the root certificate. The default value is com.
root_country - The country to be used in the root certificate. The default value is US.
root_state - The state to be used in the root certificate. The default value is CA.
root_loc - The location to be used in the root certificate. The default value is EnterpriseManager on <hostname>.
root_org - The organization name to be used in the root certificate. The default value is EnterpriseManager on <hostname>.
root_unit - The organizational unit to be used in the root certificate. The default value is EnterpriseManager on <hostname>.
root_email - The email address to be used in the root certificate. The default value is EnterpriseManager@<hostname>.
wallet: This is the directory where the wallet to be used in the https upload port is located.
wallet_pwd: This is the wallet password and is required only if the wallet is not an SSO wallet.
key_strength: The strength of the key to be used. Valid values are 512, 1024, 2048, and 4096.
cert_validity: The number of days for which the self-signed certificate is valid. The valid range is between 1 to 3650.
Note:
Thekey_strength and cert_validity parameters are applicable only when the -wallet option is not used.You can check whether security has been enabled for the Management Service by entering the emctl status oms -secure command.
Example 6-3 Sample Output of the emctl secure status oms Command
$prompt> emctl status oms -secure Oracle Enterprise Manager 10g Release 5 Grid Control Copyright (c) 1996, 2009 Oracle Corporation. All rights reserved. Checking the security status of the OMS at location set in /OH/oms10g/sysman/config/emoms.properties... Done. OMS is secure on HTTPS Port 1159
When you install the Management Agent on a host, you must identify the Management Service that will be used by the Management Agent. If the Management Service you specify has been configured to take advantage of Enterprise Manager Framework Security, you will be prompted for the Agent Registration Password and Enterprise Manager Framework Security will be enabled for the Management Agent during the installation.
Otherwise, if the Management Service has not been configured for Enterprise Manager Framework Security or if the Registration Password was not specified during installation, then security will not be enabled for the Management Agent. In those cases, you can later enable Enterprise Manager Framework Security for the Management Agent.
To enable Enterprise Manager Framework Security for the Management Agent, use the emctl secure agent utility, which is located in the following directory of the Management Agent home directory:
AGENT_HOME/bin (UNIX) AGENT_HOME\bin (Windows)
The emctl secure agent utility performs the following actions:
Obtains an Oracle Wallet from the Management Service that contains a unique digital certificate for the Management Agent. This certificate is required in order for the Management Agent to conduct SSL communication with the secure Management Service.
Obtains an Agent Key for the Management Agent that is registered with the Management Service.
Configures the Management Agent so it is available on your network over HTTPS and so it uses the Management Service HTTPS upload URL for all its communication with the Management Service.
To enable Enterprise Manager Framework Security for the Management Agent:
Ensure that your Management Service and the Management Repository are up and running.
Change directory to the following directory:
AGENT_HOME/bin (UNIX) AGENT_HOME\bin (Windows)
Stop the Management Agent:
$PROMPT> ./emctl stop agent
Enter the following command:
$PROMPT> ./emctl secure agent (UNIX) $PROMPT> emctl secure agent (Windows)
The emctl secure agent utility prompts you for the Agent Registration Password, authenticates the password against the Management Service, and reconfigures the Management Agent to use Enterprise Manager Framework Security.
Note:
Alternatively, you can enter the command all on one line, but if you enter the command on one line, the password you enter will be displayed on the screen as you type:$PROMPT> ./emctl secure agent agent_registration_pwd (UNIX) $PROMPT> emctl secure agent agent_registration_pwd (Windows)
shows sample output of the emctl secure agent utility.
Restart the Management Agent:
$PROMPT> ./emctl start agent
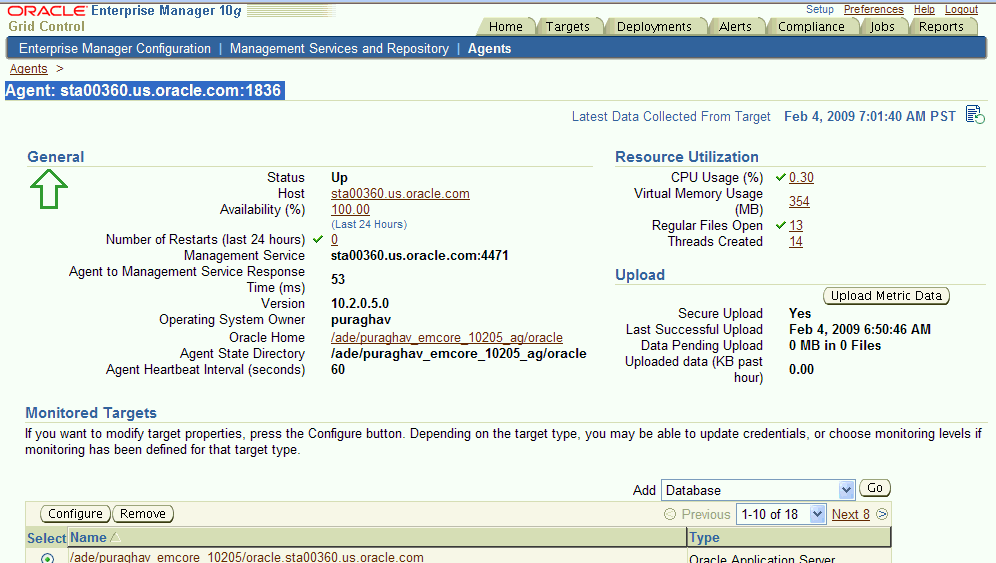
Confirm that the Management Agent is secure by checking the Management Agent home page.
Note:
You can also check if the Agent Management is secure by running theemctl status agent -secure command, or by checking the Agent and Repository URLs in the output of the emctl status agent command.In the General section of the Management Agent home page (Figure 6-2), the Secure Upload field indicates whether or not Enterprise Manager Framework Security has been enabled for the Management Agent.
See Also:
"Checking the Status of an Oracle Management Agent" in the Enterprise Manager online HelpExample 6-4 Sample Output of the emctl secure agent Utility
$PROMPT> ./emctl secure agent Oracle Enterprise Manager 10g Release 5 Grid Control 10.2.0.5.0. Copyright (c) 1996, 2009 Oracle Corporation. All rights reserved. Securing agent... Started Securing agent... Successful.
Example 6-5 Sample Output of the emctl secure status agent Command
[oracle@stang14 bin]$ ./emctl status agent -secure Oracle Enterprise Manager 10g Release 5 Grid Control 10.2.0.5.0. Copyright (c) 1996, 2009 Oracle Corporation. All rights reserved. Checking the security status of the Agent at location set in /private/home/oracle/product/102/em/agent10g/sysman/config/emd.properties... Done. Agent is secure at HTTPS Port 3872. Checking the security status of the OMS at http://gridcontrol.oraclecorp.com:4889/em/upload/... Done. OMS is secure on HTTPS Port 4888
Figure 6-2 Secure Upload Field on the Management Agent Home Page
If you already have a secure Management Service running and you install an additional Management Service that uses the same Management Repository, you will need to enable Enterprise Manager Framework Security for the new Management Service. This task is executed using the same procedure that you used to secure the first Management Service, by running the emctl secure oms utility.
Because you have already established at least one Agent Registration Password and a Root Key in your Management Repository, they must be used for your new Management Service. Your secure Management Agents can then operate against either Management Service. For more information on multiple Management Service installations, refer to Using Multiple Management Service Installations.
All the registration passwords assigned to the current Management Repository are listed on the Registration Passwords page in the Oracle Enterprise Manager 10g Grid Control Console.
See Also:
"Managing Agent Registration Passwords"If you install a new Management Service that uses a new Management Repository, the new Management Service is considered to be a distinct enterprise. There is no way for the new Management Service to partake in the same security trust relationship as another Management Service that uses a different Management Repository. Secure Management Agents of one Management Service will not be able to operate against the other Management Service.
By default, when you enable Enterprise Manager Framework Security on your Oracle Management Service there are no default restrictions on HTTP access. The Grid Control Console can also be accessed over HTTP and the Oracle Management Agents will be able to upload over HTTP as well as HTTPS.
However, it is important that only secure Management Agent installations that use the Management Service HTTPS channel are able to upload data to your Management Repository and Grid Control console is accessible via HTTPS only.
To restrict access so Management Agents can upload data to the Management Service only over HTTPS:
Stop the Management Service, the Oracle HTTP Server, and the other application server components:
$PROMPT> cd $ORACLE_HOME/opmn/bin $PROMPT> ./opmnctl stopall
Change directory to the following location in the Management Service home:
$ORACLE_HOME/bin
Enter the following command to prevent Management Agents from uploading data to the Management Service over HTTP:
$PROMPT> emctl secure lock -upload
Note:
To lock the console and prevent HTTP access to the console, enter the following command:
emctl secure lock -console
To lock both, enter either of the following commands:
emctl secure lock or emctl secure lock -upload -console
To lock both the console access and uploads from Agents while enabling security on the Management Service, enter the following command:
emctl secure oms -lock [other options]
Restart the Management Service, the Oracle HTTP Server, and the other application server components:
$PROMPT> cd $ORACLE_HOME/opmn/bin $PROMPT> ./opmnctl startall
Verify that you cannot access the Management Agent upload URL using the HTTP protocol:
For example, navigate to the following URL:
http://hostname.domain:4889/em/upload
You should receive an error message similar to the following:
ForbiddenYou don't have permission to access /em/upload on this server
Verify that you can access the Management Agent Upload URL using the HTTPS protocol:
For example, navigate to the following URL:
https://hostname.domain:4888/em/upload
You should receive the following message, which confirms the secure upload port is available to secure Management Agents:
Http XML File receiverHttp Recceiver Servlet active!
To allow the Management Service to accept uploads from unsecure Management Agents, use the following command:
$PROMPT> emctl secure unlock -upload
Note:
To unlock the console and allow HTTP access to the console, enter the following command:
emctl secure unlock -console
To unlock both, enter either of the following command:
emctl secure unlock emctl secur unlock -console -upload
Example 6-6 Sample Output of the emctl secure lock Command
$prompt> emctl secure lock Oracle Enterprise Manager 10g Release 5 Grid Control Copyright (c) 1996, 2009 Oracle Corporation. All rights reserved. OMS Console is locked. Access the console over HTTPS ports. Agent Upload is locked. Agents must be secure and upload over HTTPS port.
Example 6-7 Sample Output of the emctl secure unlock Command
$prompt> emctl secure unlock Oracle Enterprise Manager 10g Release 5 Grid Control Copyright (c) 1996, 2009 Oracle Corporation. All rights reserved. OMS Console is unlocked. HTTP ports too can be used to access console. Agent Upload is unlocked. Unsecure Agents may upload over HTTP.
To restrict HTTP access to the Oracle Enterprise Manager 10g Grid Control Console, use the emctl secure lock -console command.
Enterprise Manager uses the Agent Registration password to validate that installations of Oracle Management Agents are authorized to load their data into the Oracle Management Service.
The Agent Registration password is created during installation when security is enabled for the Oracle Management Service.
Note:
To avoid new Agents from being installed, you can delete all the registration passwords.You can use the Grid Control Console to manage your existing registration passwords or create additional registration passwords:
Click Setup at the top of any Grid Control Console page.
Click Registration Passwords.
Enterprise Manager displays the Registration Passwords page (Figure 6-3). The registration password you created when you ran the emctl secure oms command appears in the Registration Passwords table.
Use the Registration Passwords page to change your registration password, create additional registration passwords, or remove registration passwords associated with the current Management Repository.
Figure 6-3 Managing Registration Passwords in the Grid Control Console
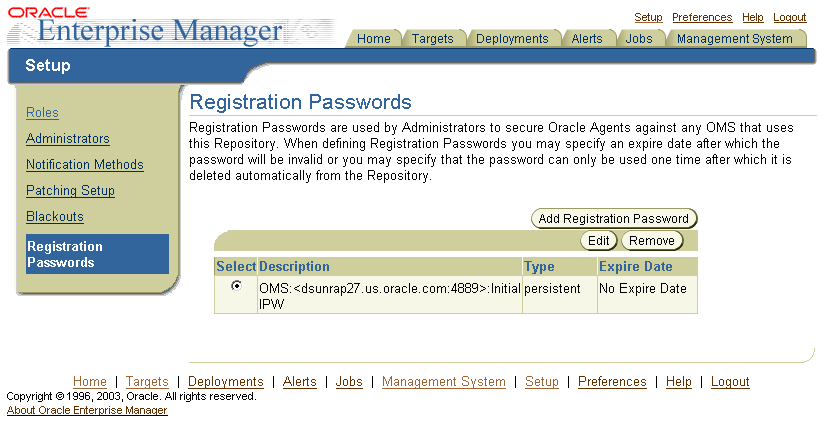
When you create or edit an Agent Registration Password on the Registration Passwords page, you can determine whether the password is persistent and available for multiple Management Agents or to be used only once or for a predefined period of time.
For example, if an administrator requests to install a Management Agent on a particular host, you can create a one-time-only password that the administrator can use to install and configure one Management Agent.
On the other hand, you can create a persistent password that an administrator can use for the next two weeks before it expires and the administrator must ask for a new password.
To add a new Agent Registration Password, use the following emctl command on the machine on which the Management Service has been installed:
$PROMPT> emctl secure setpwd [sysman pwd] [new registration pwd]
The emctl secure setpwd command requires that you provide the password of the Enterprise Manager super administrator user, sysman, to authorize the resetting of the Agent Registration Password.
If you change the Agent Registration Password, you must communicate the new password to other Enterprise Manager administrators who need to install new Management Agents, enable Enterprise Manager Framework Security for existing Management Agents, or install additional Management Services.
As with other security passwords, you should change the Agent Registration Password on a regular and frequent basis to prevent it from becoming too widespread.
When you deploy a Management Service that is available behind a Server Load Balancer (SLB), special attention must be given to the DNS host name over which the Management Service will be available. Although the Management Service may run on a particular local host, for example myhost.mycompany.com, your Management Agents will access the Management Service using the host name that has been assigned to the Server Load Balancer. For example, oracleoms.mycompany.com.
As a result, when you enable Enterprise Manager Framework Security for the Management Service, it is important to ensure that the Server Load Balancer host name is embedded into the Certificate that the Management Service uses for SSL communications. To do so, enter the following commands:
This may be done by using emctl secure oms and specifying the host name in the with an extra -host parameter as follows:
Specify the -host parameter with the emctl secure oms command as follows:
$PROMPT>emctl secure oms -host <hostname>
Set UseCanonicalName directive to On in the OMS_Home/Apache/Apache/conf/httpd.conf file.
Enable security on the Management Service by entering the following command:
$PROMPT>emctl secure oms -host <slb_hostname> [-slb_console_port <slb UI port>] [-slb_port <slb upload port>] [other params]
Create virtual servers and pools on the Server Load Balancer.
Verify that the console can be accessed using the following URL:
https://slbhost:slb_console_port/em
Re-secure the Agents with Server Load Balancer by using the following command:
$PROMPT>emctl secure agent -emdWalletSrcUrl <SLB Upload url>
This section describes how to enable Security for the Oracle Management Repository. This section includes the following topics:
About Oracle Advanced Security and the sqlnet.ora Configuration File
Configuring the Management Service to Connect to a Secure Management Repository Database
Enabling Oracle Advanced Security for the Management Repository
Enabling Security for a Management Agent Monitoring a Secure Management Repository or Database
You enable security for the Management Repository by using Oracle Advanced Security. Oracle Advanced Security ensures the security of data transferred to and from an Oracle database.
To enable Oracle Advanced Security for the Management Repository database, you must make modifications to the sqlnet.ora configuration file. The sqlnet.ora configuration file is used to define various database connection properties, including Oracle Advanced Security parameters.
The sqlnet.ora file is located in the following subdirectory of the Database home:
ORACLE_HOME/network/admin
After you have enabled Security for the Management Repository and the Management Services that communicate with the Management Repository, you must also configure Oracle Advanced Security for the Management Agent by modifying the sqlnet.ora configuration file in the Management Agent home directory.
See Also:
"Enabling Security for a Management Agent Monitoring a Secure Management Repository or Database"It is important that both the Management Service and the Management Repository are configured to use Oracle Advanced Security. Otherwise, errors will occur when the Management Service attempts to connect to the Management Repository. For example, the Management Service might receive the following error:
ORA-12645: Parameter does not exist
To correct this problem, be sure both the Management Service and the Management Repository are configured as described in the following sections.
Note:
The procedures in this section describe how to manually modify thesqlnet.ora configuration file to enable Oracle Advanced Security. Alternatively, you can make these modifications using the administration tools described in the Oracle Database Advanced Security Administrator's Guide.If you have enabled Oracle Advanced Security for the Management Service database—or if you plan to enable Oracle Advanced Security for the Management Repository database—use the following procedure to enable Oracle Advanced Security for the Management Service:
Stop the Management Service:
$PROMPT> ORACLE_HOME/bin/emctl stop oms
Locate the following configuration file in the Management Service home directory:
ORACLE_HOME/sysman/config/emoms.properties
Using a text editor, add the entries described in Table 6-1 to the emoms.properties file.
The entries described in the table correspond to valid parameters you can set when you configure network data encryption for the Oracle Database.
See Also:
"Configuring Network Data Encryption and Integrity for Oracle Servers and Clients" in the Oracle Application Server 10g Administrator's GuideSave your changes and exit the text editor.
Restart the Management Service.
$PROMPT> ORACLE_HOME/bin/emctl start oms
Table 6-1 Oracle Advanced Security Properties in the Enterprise Manager Properties File
| Property | Description |
|---|---|
|
Defines whether or not Enterprise Manager will use encryption between Management Service and Management Repository.Possible values are TRUE and FALSE. The default value is FALSE.For example:
|
|
|
Defines the Management Service encryption requirement.Possible values are REJECTED, ACCEPTED, REQUESTED, and REQUIRED.The default value is REQUESTED. In other words, if the database supports secure connections, then the Management Service uses secure connections, otherwise the Management Service uses insecure connections. For example:
|
|
|
Defines the different types of encryption algorithms the client supports.Possible values should be listed within parenthesis. The default value is For example:
|
|
|
Defines the Client's checksum requirements. Possible values are REJECTED, ACCEPTED, REQUESTED, and REQUIRED. The default value is REQUESTED. In other words, if the server supports checksum enabled connections, then the Management Service uses them, otherwise it uses normal connections. For example:
|
|
|
This property defines the different types of checksums algorithms the client supports. Possible values should be listed within parentheses. The default value is ( MD5 ). For example:
|
To be sure your database is secure and that only encrypted data is transferred between your database server and other sources, review the security documentation available in the Oracle Database 10g documentation library.
The following instructions provide an example of how you can confirm that Oracle Advanced Security is enabled for your Management Repository database and its connections with the Management Service:
Locate the sqlnet.ora configuration file in the following directory of the database Oracle Home:
ORACLE_HOME/network/admin
Using a text editor, look for the following entries (or similar entries) in the sqlnet.ora file:
SQLNET.ENCRYPTION_SERVER = REQUESTED SQLNET.CRYPTO_SEED = "abcdefg123456789"
See Also:
"Configuring Network Data Encryption and Integrity for Oracle Servers and Clients" in the Oracle Application Server 10g Administrator's GuideSave your changes and exit the text editor.
After you have enabled Oracle Advanced Security for the Management Repository, you must also enable Advanced Security for the Management Agent that is monitoring the Management Repository:
Locate the sqlnet.ora configuration file in the following directory inside the home directory for the Management Agent that is monitoring the Management Repository:
AGENT_HOME/network/admin (UNIX) AGENT_HOME\network\admin (Windows)
Using a text editor, add the following entry to the sqlnet.ora configuration file:
SQLNET.CRYPTO_SEED = "abcdefg123456789"
See Also:
"Configuring Network Data Encryption and Integrity for Oracle Servers and Clients" in the Oracle Application Server 10g Administrator's GuideSave your changes and exit the text editor.
Restart the Management Agent.
You can configure third party certificates for:
Configuring Third Party Certificate for HTTPS Upload Virtual Host
Configuring Third Party Certificate for HTTPS Apache Virtual Host
You can configure the third party certificate for the HTTPS Upload Virtual Host in two ways:
Method I
Create a wallet for each OMS in the grid.
While creating the wallet, specify the host name of the machine where the OMS is installed or the Load Balancer Name if the OMS is behind the Load Balancer for Common Name.
Write the certificates of all the Certificate Authorities in the certificate chain (like the Root Certificate Authority, Intermediate Certificate Authority) into a file named trusted_certs.txt.
Download or copy the trusted_certs.txt file to the host machines on which each Agent that is communicating with the OMS is running.
Run the following command on each Agent and restart the Agent:
emctl secure add_trust_cert -trust_certs_loc <location of the trusted_certs.txt file>
Run the following command on each OMS:
emctl secure oms -wallet <location of wallet> -trust_certs_loc <loc of trusted_certs.txt> [any other options]
Note:
If the wallet is not a single sign-on wallet, you will be prompted for the password.Method 2
Create a wallet for each OMS in the grid.
Specify the host name of the machine where the OMS is installed or the Load Balancer Name if the OMS is behind the Server Load Balancer for Common Name (CN).
Write the certificates of all the Certificate Authorities in the certificate chain (like the Root Certificate Authority, Intermediate Certificate Authority) into a file named trusted_certs.txt.
Download or copy the trusted_certs.txt file to the host machines on which each Agent that is communicating with the OMS is running.
Run the following command on each OMS:
emctl secure oms -wallet <location of wallet> -trust_certs_loc <loc of trusted_certs.txt> [any other options]
Note:
If the wallet is not a single sign-on wallet, you will be prompted for the password.Either re-secure the Agent by running the emctl secure agent command or import the trust points by running the emctl secure add_trust_cert -trust_certs_loc <location of the trusted_certs.txt file> command.
To configure the third party certificate for HTTPS Apache Virtual Host:
Create a wallet for each OMS in the grid. Specify the host name of the machine where the OMS is installed or the Load Balancer Name if the OMS is behind the Server Load Balancer for Common Name.
Run the following command on each OMS:
emctl secure console -wallet <location of wallet>
Note:
If the wallet is not a single sign-on wallet, your are prompted for the wallet's password.Caution:
Before you use theemctl secure agent command to secure the Application Server Control Console, be sure to stop the Application Server Control Console.To configure security for the Application Server Control, use the following procedure:
Stop the Application Server Control Console by entering the following command in the IAS_HOME/bin directory:
$PROMPT> ./emctl stop iasconsole
Enter the following command in the ORACLE_HOME/bin directory:
$PROMPT> ./emctl secure em
Enterprise Manager secures the Application Server Control Console. Sample output of the emctl secure em command is shown in .
Start the Application Server Control Console by entering the following command in the IAS_HOME/bin directory:
$PROMPT> ./emctl start iasconsole
Test the security of the Application Server Control Console by entering the following URL in your Web browser:
https://hostname:port/
For example:
https://mgmthost1:1812/
Example 6-8 Sample Output from the emctl secure em Command
$PROMPT> ./emctl secure em Oracle Enterprise Manager 9.0.4 Copyright (c) 2002, 2003 Oracle Corporation. All rights reserved. Generating Standalone Console Root Key (this takes a minute)... Done. Fetching Standalone Console Root Certificate... Done. Generating Standalone Console Agent Key... Done. Generating Oracle Wallet for the Standalone Console Agent... Done. Configuring Agent for HTTPS... Done. EMD_URL set in /dsk01/oracle/appserver1/sysman/config/emd.properties Generating Standalone Console Java Keystore... Done. $PROMPT>
This section describes the architecture and configuration of security for the Oracle Enterprise Manager 10g Grid Control.
See Also:
Oracle strongly recommends that you use the Secure Socket Layer (SSL) protocol and HTTPS for all connections to Enterprise Manager and that you use a valid digital security certificate.
To configure security for the Database Control:
Stop the Database Control by entering the following command in the ORACLE_HOME/bin directory (UNIX) or the ORACLE_HOME\bin (Windows):
$PROMPT> ./emctl stop dbconsole (UNIX) $PROMPT> emctl stop dbconsole (Windows)
Change directory to the ORACLE_HOME/bin directory or the ORACLE_HOME\bin (Windows) and enter the following emctl command
$PROMPT> ./emctl secure dbconsole (UNIX) $PROMPT> emctl secure dbconsole (Windows)
Enterprise Manager prompts you for the Enterprise Manager Root Password.
Enter the password for the SYSMAN database user.
Enterprise Manager prompts you to specify an Agent Registration Password, which is a new password that will be required for any Management Agents that attempt to connect to the Management Service.
Specify an Agent Registration Password for the Management Service.
Enterprise Manager prompts you to confirm the host name of the Management Service.
Enter the name of the host where the Management Service resides.
The emctl secure utility reconfigures the Management Service to enable Framework Security. If the Management Service is up and running, Enterprise Manager restarts the Management Service.
When the operation is complete, communications between the Enterprise Manager components is secure.
In addition, you can access the Grid Control Console using the HTTPS protocol.
Start the Database Control by entering the following command in the ORACLE_HOME/bin directory or the ORACLE_HOME\bin (Windows):
$PROMPT> ./emctl start dbconsole (UNIX) $PROMPT> emctl start dbconsole (Windows)
Test the security of the Database Control by entering the following URL in your Web browser:
https://hostname:port/em
For example:
https://dbhost1:1820/em
Note:
Alternatively, you can enter theemctl secure dbconsole command all on one line, but if you enter the command on one line, the passwords you enter will be displayed on the screen as you type:
$PROMPT> emctl secure dbconsole sysman_pwd agent_reg_pwd
This section describes the various user administration tasks that can be performed. It contains the following sections:
Configuring Enterprise Manager for Use with Oracle Application Server Single Sign-On
Configuring Enterprise Manager for Use with Enterprise User Security
You can create and manage Enterprise Manager administrator accounts. Each administrator account includes its own login credentials, as well as a set of roles and privileges that are assigned to the account. There are three administrator access categories:
Super Administrator: Powerful Enterprise Manager administrator with full access privileges to all targets and administrator accounts within the Enterprise Manager environment. The Super Administrator, SYSMAN is created by default when Enterprise Manager is installed. The Super Administrator can create other administrator accounts.
Administrator: Regular Enterprise Manager administrator.
Repository Owner: Database administrator for the Management Repository. This account cannot be modified, duplicated, or deleted.
The types of management tasks that the administrator can perform and targets that he can access depends on the roles, system privileges, and target privileges that he is granted. The Super Administrator can choose to let certain administrators perform only certain management tasks, or access only certain targets, or perform certain management tasks on certain targets. In this way, the Super Administrator can divide the workload among his administrators. To create, edit, or view an administrator:
Click Setup at the top of any Grid Control Console page.
Click Administrators. The Administrators page is displayed.
Click the appropriate task button on the Administrators page.
Enterprise Manager displays a wizard page for the task you have chosen. Click Help from the wizard page for more information on administrators.
If you are currently using Oracle Application Server Single Sign-On to control access and authorization for your enterprise, you can extend those capabilities to the Grid Control Console.
By default, when you navigate to the Grid Control Console, Enterprise Manager displays the Enterprise Manager login page. However, you can configure Enterprise Manager so it uses Oracle Application Server Single Sign-On to authorize your Grid Control Console users. Instead of seeing the Enterprise Manager login page, Grid Control Console users will see the standard Oracle Application Server Single Sign-On login page. From the login page, administrators can use their Oracle Application Server Single Sign-On credentials to access the Oracle Enterprise Manager 10g Grid Control Console.
Note:
You can configure Enterprise Manager to either use Oracle Application Server Single Sign-On or the Enterprise User Security features. You cannot use both options at the same time.
When Enterprise Manager is configured to use Single Sign-On with Server Load Balancer, make sure that the correct monitoring settings have been defined. For details, refer to the chapter on Grid Control Common Configurations.
The following sections describe how to configure Enterprise Manager as an OracleAS Single Sign-On Partner Application:
Configuring Enterprise Manager to Use the Single Sign-On Logon Page
Configuring Enterprise Manager to Use Single Sign-On with the osso.conf File
Registering Single Sign-On Users as Enterprise Manager Administrators
To configure the Grid Control Console for use with Oracle Application Server Single Sign-On:
Set the ORACLE_HOME environment variables to the Management Service home directory.
For example:
$PROMPT> setenv ORACLE_HOME /dev01/oracle/em10g_GridControl
Change directory to the bin directory of the Management Service Oracle home:
$PROMPT> cd $ORACLE_HOME/opmn/bin
Stop the Management Service, the Oracle HTTP Server, and the other components of the application server:
$PROMPT> ./opmnctl stopall
Change directory to the bin directory of the Management Service Oracle home:
$PROMPT> cd $ORACLE_HOME/bin
Enter the following command at the operating system prompt:
$PROMPT> ./emctl config oms sso -host ssoHost -port ssoPort -sid ssoSid -pass ssoPassword -das http://ssohost:port/
For example:
$PROMPT> ./emctl config oms sso -host sshost1.acme.com -port 1521 -sid asdb -pass Ch22x5xt -das http://ssohost1.acme.com:7777
Table 6-2 describes the arguments on the emctl config oms sso command line.
shows the typical output generated by the emctl config oms sso command.
Note:
You can use the osso.conf file to configure the Grid Control for use with Oracle Application Server Single Sign-On. For more details, refer to Registering HTTP Port With Single Sign On Server.
By default the emctl config oms sso command registers https URL with the SSO server. You can use the -unsecure option to register the http URL.
Restart the Management Service, Oracle HTTP Server, and the other application server components:
$PROMPT> cd $ORACLE_HOME/opmn/bin $PROMPT> ./opmnctl startall
Go the Grid Control Console URL.
For example:
https://mgmthost1.acme.com:7777/em
The browser is redirected to the standard Single Sign-On Logon page.
Note:
You can remove the single sign-on configuration and restore Grid control authentication by using the following command:emctl config oms sso -remove
Table 6-2 Arguments for the emctl sso Command
| Argument | Description |
|---|---|
|
-host |
The name of the host computer where the Oracle Application Server Single Sign-On server resides. Be sure to use the fully-qualified host name. |
|
-port |
The port for the Oracle Application Server Single Sign-On database, for example, 1521. |
|
-sid |
The system identifier (SID) for the Oracle Application Server Single Sign-On database. |
|
-pass |
The password for the Oracle Application Server Single Sign-On schema ( To obtain the password, see "Obtaining the Single Sign-On Schema Password" in the Oracle Application Server Single Sign-On Administrator's Guide. |
|
-das |
The URL containing the host and port for the Delegated Administration Service (DAS). Generally, the DAS host name and port are the same as the host name and port of the Oracle Application Server Single Sign-On server. For example:
|
|
-ossoconf |
This is the fully qualified name of the |
|
-unsecure |
This parameter is used to register the http port with the Single Sign-On Server. This is an optional parameter. |
|
-sitename |
The sitename that will be used to list the partner applications with the Single Sign-On Server. |
|
-emurl |
This parameter is used to specify the URL for the Load Balancer. If this parameter is not specified, the URL is constructed using the default host and port settings. |
Example 6-9 Sample Output of the emctl config oms sso Command
$prompt> ./emctl config oms sso -host <host>.com -port 1521 -sid orcl -pass W5RB9YD3 -das http://<host>.com:7777 oracle Oracle Enterprise Manager 10g Release 5 Grid Control 10.2.0.5.0. Copyright (c) 1996, 2009 Oracle Corporation. All rights reserved. /scratch/smptest/mm9/oms10g/Apache/Apache/conf/httpd.conf has been modified. /scratch/smptest/mm9/oms10g/sysman/config/emoms.properties has been modified. Registering to SSO server, please wait... Parameters passed to SSO registration tool : param0:-oracle_home_path param1:/scratch/smptest/mm9/oms10g param2:-host param3: <host>.com param4:-port param5:1521 param6:-sid param7:orcl param8: -schema param9:orasso param10:-pass param11:**** param12:-site_name param13:stam <host>.com:4889 param14:-success_url param15:http://<host>.com :4889/osso_login_success param16:-logout_url param17:http://<host>.com:4889/osso_logout_success param18:-cancel_url param19:http://stamt03.us.oracle. com:4889/ param20:-home_url param21:http://<host>.com:4889/ param22:- config_mod_osso param23:TRUE param24: param25:oracle param26:-sso_server_versi on param27:v1.2 -DinstallType= -DoldOracleHome= -DoldOHSUser=root Check /scratch/smptest/mm9/oms10g/sso/log/ssoreg.log for details of this registration SSO registration tool finished successfully. Done!
By default, the https port is registered with the Single Sign-on server. If you want to register the http port with the Single Sign-on server, you can specify the -unsecure parameter as follows
$prompt>emctl config oms sso -host ssoHost -port ssoPort -sid ssoSid -pass ssoPassword -das dasURL -unsecure
where:
host ssoHost: is the fully qualified host name.
port ssoPort: is the listener port for the SSO database.
sid ssoSid: is the SSO database SID
pass ssoPassword: is the orasso user password. This parameter is optional.
das dasURL: stands for the http://host:port where host is the ssoHost, port is the http port for the OIDDAS URL.
unsecure: is used to register the http port with the Single Sign-On Server.
In some environments, the Single Sign-On Server may be managed by different administrators who may not share the credentials. The osso.conf file can be used or the necessary parameter values required to create the osso.conf file can be specified.
To register Enterprise Manager as a partner application manually, follow these steps:
Enter the following URL to navigate to the SSO Administration page.
http://sso_host:sso_port/pls/orasso
Login as orcladmin user and click SSO Administration.
Click Administer Partner Applications and then click Add Partner Application.
Enter the following information on the Add Partner Application page.
Name: <EMPartnerName> Home URL: protocol://em_host:em_port Success URL: protocol://em_host:em_port/osso_login_success Logout URL: protocol://em_host:em_port/osso_logout_success Administrator Email: user@host.com
where host, port, and protocol refer to the EM Host, port and the protocol (http or https) used.
After entering these details, click Edit <EMPartnerName> and enter the following parameters to generate the osso.txt. Sample values for these parameters are shown below:
sso_server_version: v1.2 cipher_key: <EncryptionKeyValue> site_id: <IDValue> site_token: <TokenValue> login_url: protocol://sso_host:sso_port/pls/orasso/orasso.wwsso_app_admin.lslogin logout_url=protocol://sso_host:sso_port/pls/orasso/orasso.wwsso_app_admin.ls_logout cancel_url=protocol://em_host:em_port sso_timeout_cookie_name=SSO_ID_TIMEOUT sso_timeout_cookie_key=9E231B3C1A3A808A
Enter the following command to generate the osso.conf file:
$ORACLE_HOME/Apache/Apache/bin/iasobf osso.txt osso.conf root
Use the osso.conf file for registration as follows:
$emctl config oms sso -ossoconf osso.conf -das http://sso_host:sso_port/
Restart Apache and OMS as follows:
Opmnctl stopall Opmnctl startall
After you have configured Enterprise Manager to use the Single Sign-On logon page, you can register any Single Sign-On user as an Enterprise Manager administrator:
Go the Grid Control Console URL.
For example:
http://mgmthost1.acme.com:7777/em
The browser is redirected to the standard Single Sign-On Logon page.
Enter the credentials for a valid Single Sign-On user.
If the Single Sign-On user is not an Enterprise Manager administrator, the browser is redirected to a modified version of the Enterprise Manager logon page (Figure 6-5).
Log in to Enterprise Manager as a Super Administrator.
Click Setup and then click Administrators to display the Administrators page.
See Also:
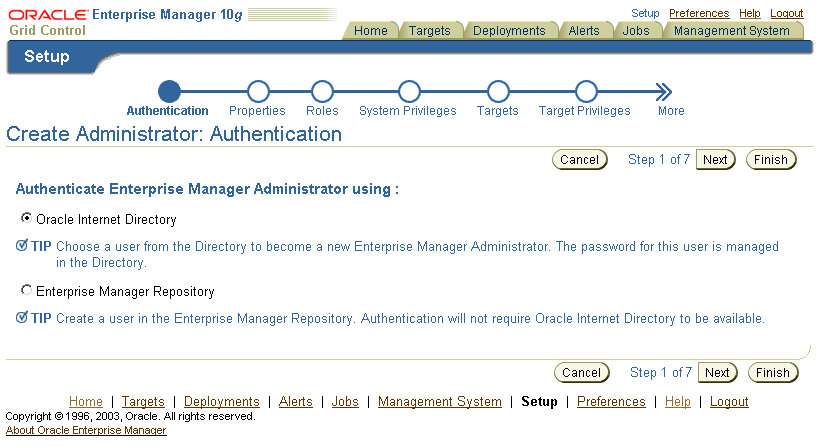
"Creating, Editing, and Viewing Administrators" in the Enterprise Manager online HelpBecause Enterprise Manager has been configured to use Single Sign-On, the first page in the Create Administrator wizard now offers you the option of creating an administrator based on a registered Oracle Internet Directory user (Figure 6-6).
Select Oracle Internet Directory and advance to the next page in the wizard.
Enter the name and e-mail address of the Oracle Internet Directory user, or click the flashlight icon to search for a user name in the Oracle Internet Directory.
Use the rest of the wizard pages to define the roles, system privileges, and other characteristics of the Enterprise Manager administrator and then click Finish.
Enterprise Manager displays a summary page that lists the characteristics of the administrator account.
Click Finish to create the new Enterprise Manager administrator.
The OID user is now included in the list of Enterprise Manager administrators. You can now verify the account by logging out of the Grid Control Console and logging back in using the OID user credentials on the Single Sign-On logon page.
Figure 6-5 Modified Enterprise Manager Logon Page When Configuring SSO
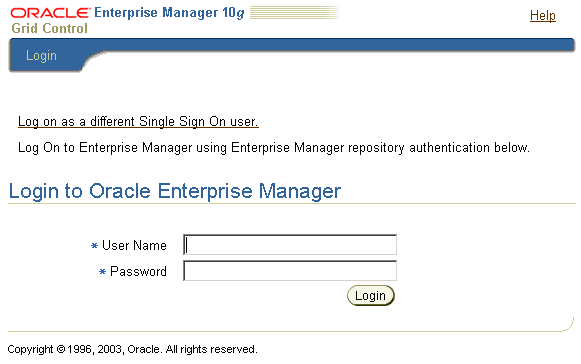
Figure 6-6 Create Administrator Page When SSO Support Is Enabled
You can use the following EMCLI command to create Single Sign-On users:
./emcli create_user -name=ssouser -type=EXTERNAL_USER
This command creates a user with the name ssouser who is authenticated against the single sign-on user.
| Argument | Description |
|---|---|
| -name | Name of the administrator. |
| -type | The type of user. The default value for this parameter is EM_USER. The other possible values are:
|
| -password | The password for the administrator. |
| -roles | The list of roles that can be granted to this administrator. |
| The list of email addresses for this administrator. | |
| -privilege | The system privileges that can be granted to the administrator. This option can be specified more than once. |
| -profile | The name of the database profile. This is an optional parameter. The default profile used is DEFAULT. |
| -desc | The description of the user being added. |
| -expired | This parameter is used to set the password to "expired" status. This is an optional parameter and is set to False by default. |
| -prevent_change_password | When this parameter is set to True, the user cannot change the password. This is an optional parameter and is set to False by default. |
| input_file | This parameter allows the administrator to provide the values for any of these arguments in an input file. The format of value is name_of_argument:file_path_with_file_name. |
Example 1
emcli create_user -name="new_admin" -password="oracle" -email="first.last@oracle.com;joe.shmoe@shmoeshop.com" -roles="public" -privilege="view_job;923470234ABCDFE23018494753091111" -privilege="view_target;<host>.com:host"
This example creates an Enterprise Manager administrator named new_admin. This administrator has two privileges: the ability to view the job with ID 923470234ABCDFE23018494753091111 and the ability to view the target <host>.com:host. The administrator new_admin is granted the PUBLIC role.
Example 2
emcli create_user -name="User1" -type="EXTERNAL_USER" -input_file="privilege:/home/user1/priv_file" Contents of priv_file are: view_target;<host>.com:host
This example makes user1 which has been created externally as an Enterprise Manager user. user1 will have view privileges on <host>.com:host.
Example 3
emcli create_user -name="User1" -desc="This is temp hire."
-prevent_change_password="true" -profile="MGMT_ADMIN_USER_PROFILE
This example sets user1 as an Enterprise Manager user with some description. The prevent_change_password is set to true to indicate that the password cannot be changed by user1 and the profile is set to MGMT_ADMIN_USER_PROFILE.
Example 4
emcli create_user -name="User1" -desc="This is temp hire." -expire="true"
This example sets user1 as an Enterprise Manager with some description. Since the password is set to expire immediately, when the user logs in for the first time, he is prompted to change the password.
The emctl config oms sso command adds the Oracle Enterprise Manager 10g Grid Control Console as an Oracle Application Server Single Sign-On partner application. Partner applications are those applications that have delegated authentication to the Oracle Application Server Single Sign-On Server.
To see the list of partner applications, navigate to the following URL:
http://hostname:port/pls/orasso/orasso.home
For example:
http://ssohost1.acme.com:7777/pls/orasso/orasso.home
After you configure Enterprise Manager to use the Single Sign-On logon page, you can bypass the Single Sign-On page at any time and go directly to the Enterprise Manager logon page by entering the following URL:
http://hostname.domain:port/em/console/logon/logon
For example:
http://mgmthost1.acme.com:7777/em/console/logon/logon
Enterprise User Security enables you to create and store Oracle9i database information as directory objects in an LDAP-compliant directory server. For example, an administrator can create and store enterprise users and roles for the Oracle9i database in the directory, which helps centralize the administration of users and roles across multiple databases.
See Also:
"Enterprise User Security Configuration Tasks and Troubleshooting" in the Oracle Database Advanced Security Administrator's GuideIf you currently use Enterprise User Security for all your Oracle9i databases, you can extend this feature to Enterprise Manager. Configuring Enterprise Manager for use with Enterprise User Security simplifies the process of logging in to database targets you are managing with the Oracle Enterprise Manager 10g Grid Control Console.
To configure Enterprise Manager for use with Enterprise User Security:
Ensure that you have enabled Enterprise User Security for your Oracle Management Repository database, as well as the database targets you will be managing with the Grid Control Console. Refer to Oracle Database Advanced Security Administrator's Guide for details.
Change directory to the ORACLE_HOME/sysman/config directory and open the emoms.properties file with your favorite text editor.
Add the following entries in the emoms.properties file:
oracle.sysman.emSDK.sec.DirectoryAuthenticationType=EnterpriseUser oracle.sysman.emSDK.sec.eus.Domain=<ClientDomainName> (For example: mydomain.com) oracle.sysman.emSDK.sec.eus.DASHostUrl=<das_url> (For example: oracle.sysman.emSDK.sec.eus.DASHostUrl=http://my.dashost.com:7777 )
Save and close the emoms.properties file.
Stop the Oracle Management Service.
Start the Management Service.
The next time you use the Oracle Enterprise Manager 10g Grid Control Console to drill down to a managed database, Enterprise Manager will attempt to connect to the database using Enterprise User Security. If successful, Enterprise Manager will connect you to the database without displaying a login page. If the attempt to use Enterprise User Security fails, Enterprise Manager will prompt you for the database credentials.
After you have configured Enterprise Manager to use Enterprise Users, you can register existing enterprise uses as Enterprise Manager Users and grant them the necessary privileges so that they can manage Enterprise Manager effectively by following these steps:
Log into Enterprise Manager as a Super Administrator.
Click Setup and then click Administrators to display the Administrators page. Since Enterprise Manager has been configured to use Enterprise Users, the first page of the Create Administrator wizard will provide the option to create an administrator based on a registered Oracle Internet Directory user (see Figure 6-6) or a normal database user.
Select Oracle Internet Directory and click Continue to go to the next page in the wizard.
Enter the name and e-mail address of the Oracle Internet Directory user or click the flashlight icon to search for a user name in the Oracle Internet Directory.
Use the rest of the wizard pages to define the roles, system privileges, and other characteristics of the Enterprise Manager administrator and then click Finish. Enterprise Manager displays a summary page that lists the characteristics of the administrator account.
Click Finish to create the new Enterprise Manager administrator.
The OID user is now included in the list of Enterprise Manager administrators. You can now verify the account by logging out of the Grid Control Console and logging back in using the OID user credentials on the Single Sign-On logon page.
To register Enterprise Users as Enterprise Manager users, enter the following command:
./emcli create_user -name=eususer -type=DB_EXTERNAL_USER
This command registers the eususer as an Enterprise Manager user where eususer is an existing Enterprise User. For more details, refer to Creating Single Sign-On Users Using EMCLI.
This section describes the following:
To change the password of the SYSMAN user, enter the following command:
emctl config oms -change_repos_pwd [-change_in_db] [-old_pwd <old_pwd>] [-new_pwd <new_pwd>] [-use_sys_pwd [-sys_pwd <sys_pwd>]]
You must run this command on each Management Service in your environment.
| Parameter | Description |
|---|---|
-change_in_db |
This parameter is optional and is used to change the SYSMAN password in the repository. If there are multiple Management Services running, this parameter must be set to true for at least one Management service.
If this parameter is not specified, the emoms.properties file will be updated with the new SYSMAN password. |
-old_pwd |
This is the current SYSMAN password. |
-new_pwd |
This is the new password. |
-use_sys_pwd |
This parameter is optional and is used to connect to the database as a SYS user. |
-sys_pwd |
This is the password for the SYS user. |
To change the password of the MGMT_VIEW user, enter the following command:
emctl config oms -change_view_user_pwd [-sysman_pwd <sysman_pwd>] [-user_pwd <user_pwd>] [-auto_generate]
| Parameter | Description |
|---|---|
-sysman_pwd |
The password for the SYSMAN user. |
-user_pwd |
The new password for theMGMT_VIEW user.This is an optional parameter and if it is not specified, the password is auto generated. |
-auto_generate |
If this option is specified, the password is auto generated. |
All operations performed by Enterprise Manager users such as creating users, granting privileges, starting a remote job like patching or cloning, need to be audited to ensure compliance with the Sarbanes-Oxley Act of 2002 (SAS 70). This act defines standards an auditor must use to assess the contracted internal controls of a service organization. Auditing an operation enables an administrator to monitor, detect, and investigate problems and enforce enterprise wide security policies.
Irrespective of how the user has logged into Enterprise Manager, if auditing is enabled, each user action is audited and the audit details are stored in a record.
You can configure the Enterprise Manager Audit System by using the following options:
You can use the following emcli commands:
enable_audit: Enables auditing for all user operations.
disable_audit: Disables auditing for all user operations.
show_audit_actions_list: Shows a list of the user operations being audited.
show_audit_settings: Shows the audit status, operation list, externalization service details, and purge period details.
To set up the audit system in Enterprise Manager:
The audit function is turned off by default. Log in to the Enterprise Manager Management Repository as the sysman user. To turn on the audit function, enter the following commands:
SQL> exec mgmt_audit_admin.enable_audit; SQL> commit;
After enabling auditing, you must restart the Oracle Management Service to ensure that this change has taken effect.
You can then login to Enterprise Manager and perform other user operations.
Notes:
You can disable the auditing function by entering the following command:
SQL> exec mgmt_audit_admin.disable_audit; SQL> commit;
After disabling auditing, you must restart the Oracle Management Service to ensure that this change has taken effect.
All the Super Administrators can view the audit data.
To view the audit data, login into Enterprise Manager and click the Setup option. On the Setup page, click the Management Services and Repository tab. In the Overview page, click the Audit Data link under the Audit section to view the audit data.
Audit data needs to be protected and maintained for several years. The volume of audit data may become very large and impact the performance of the system. To limit the amount of data stored in the repository, the audit data must be externalized or archived at regular intervals. The archived audit data is stored in an XML file complying with the ODL format. To externalize the audit data, the EM_AUDIT_EXTERNALIZATION API is used. Records of the format <file-prefix>.NNNNN.xml, where NNNN is a number are generated. The numbers start with 00001 and continue to 99999.
You can set up the audit externalization service for exporting audit data into the file system by using the following emcli command:
update_audit_setting -file_prefix=<file_prefix> -directory_name=<directory_name> -file_size = <file size> -data_retention_period=<period in days>: Sets up the externalization service for exporting audit data to the file system.
file_prefix: The prefix of the file which contains the audit data.
directory_name: The name of the database directory that is mapped to the OS directory.
file_size: The file size is the size of the file the data is written to.
data_retention_period: The period for which the audit data is to be retained inside the repository.
For more details on the EMCLI verbs, refer to Enterprise Manager Command Line Reference.
You can search for audit data that has been generated over a specified period. You can also search for the following:
Audit details of a specific user operation or all user operations.
Audit details of operations with a Success or Failure status or All operations.
To view the audit data, click the Setup option. On the Setup page, click the Management Services and Repository tab. The Overview page is displayed. Click the Audit Data link under the Audit section. The Audit Data page is displayed.
Specify the search criteria in the fields and click Go. The results are displayed in the Summary table.
To view the details of each record that meets the search criteria, select Detailed in the View drop-down list. To drill down to the full record details, click on the Timestamp. The Audit Record page is displayed.
| Field Name | Description |
|---|---|
| General | |
| Operation Timestamp | The date and time on which the operation took place. |
| Administrator | The id of the administrator who has logged into Enterprise Manager. |
| Operation | The type of operation being audited. |
| Status | The status of the operation which can be success or failure. |
| Message | A descriptive message indicating the status of the operation. |
| Normalized Timestamp | This is the UTC timestamp. |
| Client Information | |
| Session | This can either be the HTTP Session ID or the DBMS Session ID. |
| IP Address | The IP address of the client's host machine. |
| Hostname | The name of the client's host machine. |
| Upstream Component Type | The type of client, Console, Web Service, EMCLI, being used. |
| Authentication Type | The nature of the session (HTTP Session, DB Session). |
| Upstream Component Name | The name of the client being used. |
| OMS Information | |
| Hostname | The host name of the Oracle Management Service. |
| IP Address | The IP address of the Oracle Management Service. |
| Instance ID | The Instance ID of the Oracle Management Service. |
| Operation Specific Information | |
| Object Name | The operation being performed on an object |
The emkey is an encryption key that is used to encrypt and decrypt sensitive data in Enterprise Manager such as host passwords, database passwords and others. By default, the emkey is stored in the $ORACLE_HOME/sysman/config/emkey.ora file. The location of this file can be changed.
WARNING:
If the emkey.ora file is lost or corrupted, all the encrypted data in the Management Repository becomes unusable. Maintain a backup copy of this file on another system.
During startup, the Oracle Management Service checks the status of the emkey. If the emkey has been properly configured, it uses it encrypting and decrypting data. If the emkey has not been configured properly, the following error message is displayed.
Example 6-10 emctl start oms Command
$prompt> emctl start omsOracle Enterprise Manager 10g Release 10.2.0.0.0 Copyright (c) 1996, 2005 Oracle Corporation. All rights reserved.Starting HTTP Server ...Starting Oracle Management Server ...Checking Oracle Management Server Status ...Oracle Management Server is not functioning because of the following reason:The Em Key is not configured properly. Run "emctl status emkey" for more details.
The emkey is a random number that is generated during the installation of the Oracle Management Repository and is stored in a table. When the Oracle Management Service is installed, the emkey is copied from the Management Repository to the emkey.ora file and stored in the ORACLE_HOME/sysman/config/ directory of each Oracle Management Service.
WARNING:
After the emkey has been copied, you must remove it from the Management Repository as it is not considered secure. If it is not removed, data such as database passwords, server passwords and other sensitive information can be easily decrypted. To remove the emkey from the Management Repository, enter the following command:
$prompt> emctl config emkey - remove_from_repos
The emctl commands related to emkey are given below:
emctl status emkey
emctl config emkey -repos
emctl config emkey -emkeyfile
emctl config emkey -emkey
emctl config emkey -remove_from_repos
emctl config emkey -copy_to_repos
The usage of these commands is given below:
$prompt> emctl status emkey [-sysman_pwd <sysman password>] $prompt> emctl config emkey -repos [-emkeyfile <emkey.ora path>] [-force] [-sysman_pwd <sysman password>] $prompt> emctl config emkey -emkeyfile <emkey.ora path> [-force] [-sysman_pwd <sysman password>] $prompt> emctl config emkey -emkey [-emkeyfile <emkey.ora path>] [-force] [-sysman_pwd <sysman password>] $prompt> emctl config emkey -remove_from_repos [-sysman_pwd <sysman password>] $prompt> emctl config emkey -copy_to_repos [-sysman_pwd <sysman password>]
This command shows the health or status of the emkey. Depending on the status of the emkey, the following messages are displayed:
When the emkey has been correctly configured in the Management Service but is still present in the Management Repository, the following message is displayed.
When the emkey has been correctly configured in the Management Service and has been removed from the Management Repository, the following message is displayed.
When the emkey.ora file is corrupt or missing and is present in the Management Repository, the following message is displayed.
Example 6-13 emctl status emkey - Example 3
Oracle Enterprise Manager 10g Release 10.2.0.0.0 Copyright (c) 1996, 2005 Oracle Corporation. All rights reserved.The Em Key exists in the Management Repository, but is not configured properly or is corrupted in the file system.Configure the Em Key by running "emctl config emkey -repos".
When the emkey.ora file is corrupt or missing and is not present in the Management Repository, the following message is displayed.
Example 6-14 emctl status emkey - Example 4
Oracle Enterprise Manager 10g Release 10.2.0.0.0 Copyright (c) 1996, 2005 Oracle Corporation. All rights reserved.The Em Key is not configured properly or is corrupted in the file system and does not exist in the Management Repository. To correct the problem:1) Copy the emkey.ora file from another OMS or backup machine to the OH/sysman/config directory.2) Configure the emkey.ora file by running "emctl config emkey -emkeyfile <emkey.ora file location>".
This command copies the emkey from the Management Repository to the emkey.ora file.
Example 6-15 Sample Output of the emctl config emkey -repos Command
$ emctl config emkey -repos -emkeyfile /tmp/emkey.ora.0 -forceOracle Enterprise Manager 10g Release 10.2.0.0.0 Copyright (c) 1996, 2005 Oracle Corporation. All rights reserved.Please enter repository password: The Em Key has been configured successfully.
In this example, the emkey is copied from the Management Repository to the /tmp/emkey.ora.0 file. The command configures the oracle.sysman.emkeyfile property in the emoms.properties to point to this file.
Note:
The-force option is required only if the emkey file is already configured.
If the -emkeyfile option is not provided in the Management Repository, the emkey is overwritten to the already configured emkey.ora file.
This command can be used to configure a new emkey.ora file.
Example 6-16 Sample Output of emctl config emkey -emkeyfile Command
$ emctl config emkey -emkeyfile /tmp/emkey.ora.1 -forceOracle Enterprise Manager 10g Release 10.2.0.0.0 Copyright (c) 1996, 2005 Oracle Corporation. All rights reserved.Please enter repository password: The Em Key has been configured successfully.
This command configures the /tmp/emkey.ora.1 file as the new emkey.ora file. It also modifies the oracle.sysman.emkeyfile property in emoms.properties to point to this file. The -force option is required only if the emkey.ora file has already been configured.
This command is used to configure a new emkey.
Example 6-17 Sample Output of emctl config emkey -emkey Command
$ emctl config emkey -emkey -emkeyfile /tmp/emkey.ora.2 -forceOracle Enterprise Manager 10g Release 10.2.0.0.0 Copyright (c) 1996, 2005 Oracle Corporation. All rights reserved.Please enter repository password: Please enter the em key: The Em Key has been configured successfully.
This command writes the emkey provided as standard input into the /tmp/emkey.ora.2 file and configures it. The -force option is required only if the emkey.ora file has already been configured. If the -emkeyfile option is not provided, the emkey is overwritten to the already configured emkey.ora file.
This command removes the emkey from the Management Repository.
Example 6-18 Sample Output of emctl config emkey -remove_from_repos Command
$ emctl config emkey -remove_from_reposOracle Enterprise Manager 10g Release 10.2.0.0.0 Copyright (c) 1996, 2005 Oracle Corporation. All rights reserved.Please enter repository password: The Em Key has been removed from the Management Repository.Make a backup copy of OH/sysman/config/emkey.ora file and store it on another machine.WARNING: Encrypted data in Enterprise Manager will become unusable if the emkey.ora file is lost or corrupted.
This command copies the emkey back to the Management Repository.
Example 6-19 Sample Output of emctl config emkey_copy_to_repos Command
$ emctl config emkey -copy_to_reposOracle Enterprise Manager 10g Release 10.2.0.0.0 Copyright (c) 1996, 2005 Oracle Corporation. All rights reserved.Please enter repository password: The Em Key has been copied to the Management Repository. This operation will cause the Em Key to become unsecure.
Note:
This command is used during the additional Oracle Management Service install (See Section 6.6.3). When you use this command, the emkey will be present in the Management Repository, which is not considered secure. You can secure it after the additional Oracle Management Service install by running the command:emctl config emkey -remove_from_reposThis section explains the install and upgrade scenarios for emkey.
A new emkey is generated as a strong random number when the Management Repository is installed.
When the Oracle Management Service is installed, the installer copies the emkey from the Management Repository and stores it in the emkey.ora file.
Note:
After installation, the emkey will be present in the Management Repository. This is not considered secure. The user can secure the emkey by running the emctl command emctl config emkey -remove_from_reposSimilar to the first Oracle Management Service install, the installer will copy the emkey from the Management Repository to the emkey.ora file of the additional Oracle Management Service.
Note:
After the first Oracle Management Service install, you may have removed the emkey from the Management Repository using the emctl command.Before the additional Oracle Management Service is installed, run the following command from the first Oracle Management Service home to copy the emkey to the Management Repository.
emctl config emkey -copy_to_repos
If the additional Oracle Management Service install is done without the emkey in the Management Repository, the installer will prompt the user to run the command mentioned above.
The Management Repository is upgraded as usual. When the Oracle Management Service is upgraded, the upgrade script copies the emkey from the Management Repository to the emkey.ora file of each Oracle Management Service.
Note:
After all the Oracle Management Service have been upgraded, you can secure the emkey, that is, remove it from the Management Repository by running the following command:emctl config emkey -remove_from_repos
When the Management Repository is recreated, a new emkey is generated. This new key will not be in synchronization with the existing emkey.ora in the Oracle Management Service home directory. Enter the emctl config emkey -repos -force command to overwrite the new emkey to the emkey.ora file.
After you enable security for the Enterprise Manager components and framework, there are additional security considerations. This section provides the following topics:
This section describes how to respond to browser-specific security alert dialog boxes when you are using Enterprise Manager in a secure environment.
The security alert dialog boxes described in this section should appear only if you have enabled Enterprise Manager Framework Security, but you have not completed the more extensive procedures to secure your Oracle HTTP Server properly.
This section contains the following topics:
Responding to the Internet Explorer Security Alert Dialog Box
Responding to the Netscape Navigator New Site Certificate Dialog Box
Preventing the Display of the Internet Explorer Security Information Dialog Box
If you enable security for the Management Service, but do not enable the more extensive security features of your Oracle HTTP Server, you will likely receive a Security Alert dialog box similar to the one shown in Figure 6-10 when you first attempt to display the Grid Control Console using the HTTPS URL in Internet Explorer.
Note:
The instructions in this section apply to Internet Explorer 5.5. The instructions may vary for other supported browsers.Figure 6-10 Internet Explorer Security Alert Dialog Box
When Internet Explorer displays the Security Alert dialog box, use the following instructions to install the certificate and avoid viewing this dialog box again in future Enterprise Manager sessions:
In the Security Alert dialog box, click View Certificate.
Click the Certificate Path tab and select the first entry in the list of certificates as shown in Figure 6-11.
Click View Certificate to display a second Certificate dialog box.
Click Install Certificate to display the Certificate Import wizard.
Accept the default settings in the wizard, click Finish when you are done, and then click Yes in the Root Certificate Store dialog box.
Internet Explorer displays a message box indicating that the Certificate was imported successfully.
Click OK to close each of the security dialog boxes and click Yes on the Security Alert dialog box to continue with your browser session.
You should no longer receive the Security Alert dialog box in any future connections to Enterprise Manager when you use this browser.
Figure 6-11 Certificate Path Tab on the Internet Explorer Certificate Dialog Box
If you enable security for the Management Service, but you do not enable the more extensive security features of your Oracle HTTP Server, you will likely receive a New Site Certificate dialog box similar to the one shown in Figure 6-12 when you first attempt to display the Grid Control Console using the HTTPS URL in Netscape Navigator.
Note:
The instructions in this section apply to Netscape Navigator 4.79. The instructions may vary for other supported browsers.When Netscape Navigator displays the New Site Certificate dialog box, use the following instructions to install the certificate and avoid viewing this dialog box again in future Enterprise Manager sessions:
Review the instructions and information on each wizard page; click Next until you are prompted to accept the certificate.
Select Accept this certificate forever (until it expires) from the list of options.
On the last screen of the wizard, click Finish to close the wizard and continue with your browser session.
You should no longer receive the New Site Certificate dialog box when using the current browser.
Figure 6-12 Netscape Navigator New Site Certificate Dialog Box
After you enable Security for the Management Service, you may receive a dialog box similar to the one shown in Figure 6-13 whenever you access certain Enterprise Manager pages.
Note:
The instructions in this section apply to Internet Explorer 6.0. The instructions may vary for other supported browsers.Figure 6-13 Internet Explorer Security Information Dialog Box
To stop this dialog box from displaying:
Select Internet Options from the Internet Explorer Tools menu.
Click the Security tab.
Select Internet and then click Custom Level.
Internet Explorer displays the Security Settings dialog box.
Scroll down to Miscellaneous settings and enable the Display Mixed Content option.
Oracle Beacons provide application performance availability and performance monitoring. They are part of the Application Service Level Management features of Enterprise Manager.
See Also:
"About Application Service Level Management" in the Enterprise Manager Online HelpWhen a Beacon is used to monitor a URL over Secure Sockets Layer (SSL) using an HTTPS URL, the Beacon must be configured to recognize the Certificate Authority that has been used by the Web site where that URL resides.
See Also:
"The Public Key Infrastructure Approach to Security" in Oracle Security Overview for an overview of Public Key Infrastructure features, such as Certificate AuthoritiesThe Beacon software is preconfigured to recognize most commercial Certificate Authorities that are likely to be used by a secure Internet Web Site. However, you may encounter Web Sites that, although available over HTTPS, do not have a Certificate that has been signed by a commercial Certificate Authority recognized by the Beacon. The following are out-of-box certificates recognized by Beacons:
Class 1 Public Primary Certification Authority by VeriSign, Inc.
Class 2 Public Primary Certification Authority by VeriSign, Inc.
Class 3 Public Primary Certification Authority by VeriSign, Inc.
Secure Server Certification Authority by RSA Data Security, Inc.
GTE CyberTrust Root by GTE Corporation
GTE CyberTrust Global Root by GTE CyberTrust Solutions, Inc.
Entrust.net Secure Server Certification Authority by Entrust.net ((c) 1999
Entrust.net Limited, www.entrust.net/CPS incorp. by ref. (limits liab.))
Entrust.net Certification Authority (2048) by Entrust.net ((c) 1999
Entrust.net Limited, www.entrust.net/CPS_2048 incorp. by ref. (limits liab.))
Entrust.net Secure Server Certification Authority by Entrust.net ((c) 2000
Entrust.net Limited, www.entrust.net/SSL_CPS incorp. by ref. (limits liab.))
In those cases, for example, if you attempt to use the Test section of the Beacon Performance page to test the HTTP Response of the secure URL, the following error appears in the Status Description column of the Response Metrics table on the URL Test Page:
javax.net.ssl.SSLException: SSL handshake failed: X509CertChainIncompleteErr--https://mgmtsys.acme.com/OracleMyPage.Home
See Also:
"Using Beacons to Monitor Remote URL Availability" in the Enterprise Manager online helpTo correct this problem, you must allow the Beacon to recognize the Certificate Authority that was used by the Web Site to support HTTPS. You must add the Certificate of that Certificate Authority to the list of Certificate Authorities recognized by Beacon.
To configure the Beacon to recognize the Certificate Authority:
Obtain the Certificate of the Web Site's Certificate Authority, as follows:
In Microsoft Internet Explorer, connect to the HTTPS URL of the Web Site you are attempting to monitor.
Double-click the lock icon at the bottom of the browser screen, which indicates that you have connected to a secure Web site.
The browser displays the Certificate dialog box, which describes the Certificate used for this Web site. Other browsers offer a similar mechanism to view the Certificate detail of a Web Site.
Click the Certificate Path tab and select the first entry in the list of certificates as shown in Figure 6-11.
Click View Certificate to display a second Certificate dialog box.
Click the Details tab on the Certificate window.
Click Copy to File to display the Certificate Manager Export wizard.
In the Certificate Manager Export wizard, select Base64 encoded X.509 (.CER) as the format you want to export and save the certificate to a text file with an easily-identifiable name, such as beacon_certificate.cer.
Open the certificate file using a text editor.
The content of the certificate file will look similar to the content shown in .
Update the list of Beacon Certificate Authorities as follows:
Locate the b64InternetCertificate.txt file in the following directory of Agent Home of the Beacon host:
agent_home/sysman/config/
This file contains a list of Base64 Certificates.
Edit the b64InternetCertificate.txt file and add the contents of the Certificate file you just exported to the end of the file, taking care to include all the Base64 text of the Certificate including the BEGIN and END lines.
Restart the Management Agent.
After you restart the Management Agent, the Beacon detects your addition to the list of Certificate Authorities recognized by Beacon and you can successfully monitor the availability and performance of the secure Web site URL.
This section describes Enterprise Manager security features.
Oracle Enterprise Manager 10g Release 2 introduces the concept of ORACLE_HOME credentials to designate the owner of the ORACLE_HOME with special credentials for the ORACLE_HOME. The operating system user who installs the software will also need to perform the patching. In Oracle Enterprise Manager 10g Release 2, one can explicitly set the ORACLE_HOME credential and store it in the Management Repository. While patching, the user can use existing operating system credentials or override it under special circumstances. The user can specify ORACLE_HOME credentials and in the same interface choose to store it in the Management Repository for future use.
The Enterprise Manager Command line interface (EM CLI) also provides a facility to set ORACLE_HOME credentials. This is useful in cases where the Super Administrator sets the credentials and the user who initiates the patching job is unaware of the actual credentials. For auditing in security-hardened data centers, the owner of the software is usually different from the user who initiates the patching job. The patching application internally switches the user context to the owner of the software and patches the software. To emulate such a case, the patch administrator will set the ORACLE_HOME credentials to the owner of the ORACLE_HOME. The Grid Control user who executes the patching job will be unaware of the credentials. The patching job will internally execute as the owner of the ORACLE_HOME. Grid Control will audit the patching job and capture the name of the Grid Control user who initiated the job. For example, if the owner of the ORACLE_HOME is "X", the patch super administrator in Grid Control is "Y" and the target administrator in Grid Control is "Y". "Y" will set the ORACLE_HOME credential to "X" with the password, using EMCLI. "Z" will submit the patching job using the already stored preferred credentials. Grid Control will audit the job as submitted by "Z".
The following is an example for setting the Oracle Home credentials using command line:
./emcli set_credential -target_type=host -target_name=val1 -credential_set=OHCreds -column="OHUsername:val2;OHPassword:val3" -oracle_homes="val4"
where:
val1 = Hostname
val2 = Oracle Home user name
val3 = Oracle Home password
val4 = Oracle Home location
You can also set credentials for multiple Oracle Homes on the same host using the following command:
./emcli set_credential -target_type=host -target_name=val1 -credential_set=OHCreds -column="OHUsername:val2;OHPassword:val3" -oracle_homes="val4;val5
where
val1 = Hostname
val2 = Oracle Home user name
val3 = Oracle Home password
val4 = Oracle Home location 1
val5 = Oracle Home location 2
Note:
Only one host can be passed to the verb.* If one wants multiple Oracle Home credentials on multiple hosts, then you will need Shell or Perl script to read lines, one at a time, from a file containing the host, credential values, and home location, and call the emcli set_credential verb for each row in the file.The emcli set_credential command sets preferred credentials for given users. Table 6-3 describes the input values to the emcli set_credential command.
Table 6-3 emcli set_credential Parameters
| Parameter | Input Value | Description |
|---|---|---|
|
-target_type |
-target_type ="ttype" |
Type of target. Must be "host" in case the "-oracle_homes" parameter is specified. |
|
-target_name |
[-target_name="tname"] |
Name of target. Omit this argument to set enterprise preferred credentials. Must be hostname in case "-oracle_homes" parameter is specified |
|
-credential_set |
-credential_set="cred_set" |
Credential set affected. |
|
-user |
[-user="user"] |
Enterprise Manager user whose credentials are affected. If omitted, the current user's credentials are affected. |
|
-columns |
-columns="col1:newval1;col2:newval2;..." |
The name and new value of the column(s) to set. Every column of the credential set must be specified. Alternatively, a tag from the -input_file argument may be used so that the credential values are not seen on the command line. This argument may be specified more than once. |
|
-input_file |
[-input_file="tag1:file_path1;tag2:file_path2;..."] |
Path of file that has -columns argument(s). This option is used to hide passwords. Each path must be accompanied by a tag which is referenced in the -columns argument. This argument may be specified more than once. |
|
-oracle_homes |
[-oracle_homes="home1;home2"] |
Name of Oracle Homes on the target host. Credentials will be added/updated for all specified home |
To patch an Oracle Home used by a user "Oracle" and the user is locked:
Edit the default patching script and prepend sudo or sudo -u or pbrun -u to the default patching step. You need to set a policy (by editing the sudoers file) to allow the user submitting the job (who must be a valid operating system user) to be able to run sudo or pbrun without being prompted for password.
Note:
You cannot patch Oracle Homes without targets. This must be done by using the Patching wizard.The cloning application is wizard-driven. The source of the Oracle Home being cloned may be either an installed Oracle Home or a Software Library. Following are the steps in the cloning process:
If the source is an installed Oracle Home, then, after selecting the Oracle Home, a user will need to specify the Oracle Home credentials. These credentials once specified for an Oracle Home are stored in the repository. The next time a user clones the same Oracle Home, these credentials are automatically populated. Other parameters queried from the user at this point is a temporary location (on the source computer) and the list of files to be excluded from the Oracle Home. If the cloning source is a Software Library, the source Oracle Home credentials will not be queried for.
The user needs to specify the target location and provide the required credentials for each target location. These credentials will be the Oracle Home credentials for each of these target locations. Subsequently, if a user selects any of these cloned Oracle Homes as a source, the Oracle Home credentials are automatically populated.
Depending on the product being cloned, the user can view the Enterprise Manager page where query parameters required for the particular product being cloned are displayed.
The user can, then, view the execution of user-supplied pre-cloning and post-cloning scripts and the root.sh script. The root.sh script will always be run with sudo privileges, but the user has the option to decide if the pre-cloning and post-cloning scripts run with sudo privileges.Finally, the user can schedule the cloning job at a convenient time.
For more information about cloning, refer to the Enterprise Manager Online Help.
sudo allows a permitted user to execute a command as the superuser or another user, as specified in the sudoers file. You need to set a policy (by editing the sudoers file) to allow the user submitting the job (who must be a valid operating system user) to be able to use sudo. For more information, see the manual page on sudo (man sudo) on Unix. Enterprise Manager authenticates the user using sudo, and executes the script as sudo.
For example, if the command to be executed is foo -arg1 -arg2, it will be executed as sudo -S foo -arg1 -arg2.