| Oracle® Access Manager Identity and Common Administration Guide 10g (10.1.4.0.1) Part Number B25343-01 |
|
|
View PDF |
| Oracle® Access Manager Identity and Common Administration Guide 10g (10.1.4.0.1) Part Number B25343-01 |
|
|
View PDF |
Both the Identity System and the Access System provide support for Active Directory Services Interface (ADSI) client applications. This chapter summarizes requirements and procedures when you are running Oracle Access Manager with Active Directory forests and the Active Directory Services Interface (ADSI).
This appendix contains the following sections:
For additional information and procedures, see the Oracle Access Manager Installation Guide.
Active Directory runs on Windows® 2000 and Windows Server 2003 domain controllers. Client applications using ADSI may be written and run on other windows platforms.
ADSI is a set of COM interfaces that enable tight integration with Active Directory. For example, ADSI:
Abstracts the capabilities of different directory services from multiple vendors to present a single interface for managing network resources.
Allows administrators and developers to manage the resources in a directory service, regardless of which network environment contains the resource.
Enables administrators to automate common tasks such as adding users and groups, managing printers, and setting permissions on network resources.
|
Important: Enabling ADSI allows Oracle Access Manager to take advantage of Active Directory's implicit failover and password-change capabilities. |
With ADSI, Oracle Access Manager components do not have to bind to a specific host and port to access Active Directory data. Instead, ADSI allows Oracle Access Manager components to connect to the nearest available domain controller for accessing any user, group, or Oracle Access Manager configuration information.
As described in the Oracle Access Manager Installation Guide, the credentials for ADSI are used to bind to the entire forest. A forest can contain multiple Active Directory hosts. When user data and configuration data are stored on separate Active Directory hosts in separate forests, you cannot connect to these simultaneously using ADSI.
ADSI does not require specific host and port numbers for different domains in the forest. ADSI connects to Active Directory hosts using an LDAP URL like the following:
LDAP://domain.oblix.com/ou=oblix,dc=domain,dc=oblix,dc=com
For details about enabling ADSI during installation, see the Oracle Access Manager Installation Guide.
Active Directory replicates the entire tree structure. Due to potential replication delays, Oracle recommends you not replicate the directory tree containing Oracle configuration data. Changes to configuration data may not be immediately available. For example, a change made to a user's access permissions in the Policy Manager may not be available to the Access Server if they are talking to different domain controllers.
If you must replicate the Oblix tree, modify the replication frequency between the domain controllers on Active Directory.
Oracle Access Manager supports a flexible combination of ADSI and LDAP that relates to your choice of authentication options and binding options.
|
Note: SSL is not required with ADSI and Oracle Access Manager. However, your business may require SSL for other reasons. For example, directory binds are in clear text and SSL is not automatically provided. |
This section includes the following topics:
With a pure ADSI setup, a single ADSI database agent is created during Identity System setup for the primary domain controller in your Active Directory tree. You must add additional agents for each child domain.
Additionally, if you have a noncontiguous forest of domain trees, you need to associate a separate ADSI database agent for each primary domain controller as shown in Figure B-1.
See "Managing Directory Server Profiles" for more information about multiple directory profiles and DB agents.
ADSI authentication may be slower than LDAP. For this reason, you may want to use LDAP for authentication when other operations, such as read, write, and search are handled by ADSI. An ADSI agent must be associated with every domain.
To associate an ADSI agent with every domain
Select the "Use LDAP for authentication" check box next to Microsoft Active Directory (using ADSI) on the Create Directory Profile page in the Identity System Console.
See "Managing Directory Server Profiles" for more information about multiple directory profiles and DB agents.
Repeat as needed.
|
Note: The Global Catalog is not required with this release. |
For more information, see "Bind Mechanisms for the Access Server" and "Oracle Access Manager ADSI Configuration Files".
ADSI provides several ways for the Identity Server to bind to Active Directory. There is no advantage to any particular method. Instead, it depends on which credentials you want to use. For example:
Implicitly: Using the credential of the current process. This is the default for the Identity Server.
This corresponds to the service logon credentials for the Identity Server. For implicit bind, the useImplicitBind flag in the adsi_params.xml file should be set to 0. See "Oracle Access Manager ADSI Configuration Files" for details.
|
Note: You must create an account for the Identity Server to bind to Active Directory. |
The account that enables the Identity Server to bind to the Active Directory must be equivalent to the root DN that you specify during setup of the Identity Server. It should have all the administrative privileges for operations that are to be performed using Oracle Access Manager. In an Active Directory forest, this user should be delegated control over all the other domains in the forest.
Explicitly Using the DN of the user: The useImplicitBind flag in the adsi_params.xml file should be set to 1. The user DN should be specified with the adsiCredential parameter located in the adsi_params.xml file. See "Oracle Access Manager ADSI Configuration Files" for details.
Explicitly Using the userPrincipleName: The useImplicitBind flag in the adsi_params.xml file should be set to 2. The UPN should be specified in the adsiUPN parameter in the adsi_para.xml file. See "Oracle Access Manager ADSI Configuration Files" for details.
ADSI configuration parameters are maintained in two files:
\IdentityServer_install_dir\identity\oblix\apps\common\bin\globalparams.xml \IdentityServer_install_dir\identity\oblix\config\adsi_params.xml
where IdentityServer_install_dir is the directory in which you installed the Identity Server.
This section shows a sample globalparams.xml file followed by a table of parameter values.
The install program in \IdentityServer_install_dir\identity\oblix\apps\common\bin\ globalparams.xml creates the adsiEnable parameter and sets its value to true when you enable ADSI for the default directory profile. This parameter refers to a system level directory profile that contains Oracle configuration data.
|
Note: You must restart the Identity Server after changing any parameters. However, do not change the ADSIEnabled parameter value. |
<SimpleList> <NameValPair ParamName="ActiveDirectory" Value="true" /> </SimpleList> <SimpleList> <NameValPair ParamName="ADSIEnabled" Value="true" /> </SimpleList>
Table B-1 Parameters and Values in globalparams Files
| globalparams Parameters | Values |
|---|---|
|
ActiveDirectory |
true | false True when the Master Administrator selects Active Directory as the directory server type during Identity Server configuration |
|
ADSIEnabled |
true | false True when the Master Administrator enables ADSI during Identity Server configuration |
This section shows a sample adsi_params.xml file followed by a table of parameter values. By default, adsi_params.xml includes a value for the adsiCredential parameter and the password, as shown in the following example. This enables you to change the bind mechanism to be Explicit after initial setup.
The adsiPassword is encrypted and can only be generated by Oracle Access Manager during setup. The following is an example of this file:
<?xml version="1.0" ?>
- <ParamsCtlg xmlns="http://www.oblix.com" CtlgName="adsi_params">
- <CompoundList ListName="adsi_params">
- <ValNameList ListName="adsi_params">
<NameValPair ParamName="sizeLimit" Value="0" />
<NameValPair ParamName="timeLimit" Value="0" />
<NameValPair ParamName="pagesize" Value="100" />
<NameValPair ParamName="useImplicitBind" Value="0" />
<NameValPair ParamName="adsiCredential"
Value="cn=Administrator,cn=users,dc=goodwill,dc=oblix,dc=com" />
<NameValPair ParamName="adsiPassword" Value="0243455B5B5F5C4C5651595D41" />
<NameValPair ParamName="useGCForAuthn" Value="false" />
<NameValPair ParamName="encryption" Value="false" />
<NameValPair ParamName="asynchronousSearch" Value="true" />
<NameValPair ParamName="useDNSPrefixedLDAPPaths" Value="false" />
</ValNameList>
</CompoundList>
..</ParamsCtlg>
By default, encryption is set to false in adsi_params.xml. If you set it to true when running in open mode and restart the Identity Server, the Identity Server will not work.
|
Note: You must restart the Identity Server after changing any parameters. |
Table B-2 describes parameters and values within the adsi_params files, next.
Table B-2 Parameters and Values in adsi_params Files
| adsi_params Parameters | Values |
|---|---|
|
sizeLimit |
Integer value that limits the number of query results returned for authentication. |
|
timeLimit |
Integer value that limits the number of seconds before a query times out. |
|
pageSize |
Page size of results that ADSI request from the server. |
|
useImplicitBind |
0 = Implicit credentials 1 = Explicit credentials 2 = Use userPrincipalName |
|
adsiCredential |
An LDAP specification of a user, such as cn=Administrator,cn=users,dc=myhost,dc=mydomain,dc=com |
|
adsiPassword |
An encoded text string representing the LDAP user's password. |
|
useGCForAuthn |
true/false False |
|
aynchronousSearch |
true/false By default ADSI is enabled to perform asynchronous searches. If set to false, it does synchronous searches. |
|
adsiUPN |
This parameter needs to be added if useImplicitBind is set to 2. The value of the parameter should be the UPN (userPrincipalName) of the user. |
|
pageSize |
Setting the pageSize value to a finite value (the default is 0) turns off LDAP referrals. This can improve performance when client applications perform directory searches. |
|
chaseReferral |
Setting this flag to false turns off LDAP referrals. |
Like the Identity System, the Access System provides the support for both ADSI and ADSI with LDAP authentication.
The Access System also supports multiple Active Directory domains and you must perform the steps for enabling ADSI for the default directory profile created during Oracle Access Manager setup.
This section includes the following topics:
The Access Server authenticates to Active Directory using ADSI. This is the default when you enable ADSI on these components.
The Policy Manager uses the same authentication mode as the Identity Server. Still, you must enable ADSI for the Policy Manager.
See "Configuring ADSI for the Access System" for details.
The Access Server can communicate directly with all directory servers in the forest and no longer requires the Global Catalog for LDAP authentication.
For a list of ADSI installation and setup considerations, see the Oracle Access Manager Installation Guide appendix on installing with Active Directory.
Authentication Mechanisms
When users authenticate to Active Directory, the mechanism is the domain controller, which uses respective domain controllers for authentication with ADSI.
See "Access System ADSI Configuration Files" for details.
Bind Mechanisms for the Access Server
ADSI provides several ways for the Access Server and Policy Manager to bind to Active Directory. There is no advantage to a particular method. Instead, it depends on which credentials you wish to use:
Implicitly: Using the credential of the current process (default for the Access Server).
This corresponds to the service logon credentials for the Access Server. For implicit bind, the useImplicitBind flag in the adsi_params.xml file should be set to 0. See "Access System ADSI Configuration Files" for details.
|
Note: You need to create an account for the Access Service to bind to Active Directory. This account must be equivalent to the Root DN that you specify during setup of the Access Server. It should have all the administrative privileges for the operations that are to be performed using Oracle Access Manager. In an Active Directory Forest, this user should be delegated control over all the other domains in the forest. |
Explicitly Using the DN of the User: The useImplicitBind flag in the adsi_params.xml file should be set to 1.
The user DN should be specified with the adsiCredential parameter located in the adsi_params.xml file. See "Access System ADSI Configuration Files" for details.
Explicitly Using the userPrincipleName: The useImplicitBind flag in the adsi_params.xml file should be set to 2.
The UPN should be specified in the adsiUPN parameter in the adsi_params.xml file. See "Access System ADSI Configuration Files" for details.
In a multi-domain Active Directory forest the only supported explicit bind mechanism is userPrincipleName. The Policy Manager supports only this mechanism.
Both the Policy Manager and Access Server each have two configuration files for modifying ADSI related parameters. Although the files are maintained in separate locations, and must be modified separately for each component, their contents are the same. The configuration files for the Policy Manager and Access Server are as follows:
\PolicyManager_install_dir\access\oblix\apps\common\bin\globalparams.xml \PolicyManager_install_dir\access\oblix\config\adsi_params.xml
\AccessServer_install_dir\access\oblix\apps\common\bin\globalparams.xml \AccessServer_install_dir\access\oblix\config\adsi_params.xml
These files are discussed in the following sections.
Policy Manager ADSI Configuration
This section shows a sample global-parameters configuration file, followed by a table of parameter values.
|
Note: When you install Policy Manager and Access Server, if you do not choose the ADSI option, you do not see the ADSIEnabled parameter in globalparams.xml. However, you do still see the useLDAPBind parameter, though it serves no purpose without ADSIEnabled. |
BEGIN:vCompoundList ... useLDAPBind:false ADSIEnabled:true ActiveDirectory:true END:vCompoundList
The parameters and their values are described in Table B-3.
Table B-3 Parameters and Values in globalparams Files
| globalparams Parameters | Values |
|---|---|
|
useLDAPBind |
true | false True when the Master Administrator selects "Microsoft Active Directory using LDAP" during Policy Manager configuration. The ADSIEnabled flag must be true for this flag to have effect. The default is false. |
|
ADSIEnabled |
true | false True when the Master Administrator enables ADSI during Policy Manager configuration. |
|
ActiveDirectory |
true | false True when the Master Administrator selects Active Directory as the Directory Server type during Policy Manager configuration. |
Access Server ADSI Configuration
This section shows a sample adsi parameters configuration file, followed by Table B-4 of parameter values.
Table B-4 Parameters and Values in adsi_params Files
| adsi_params Parameters | Values |
|---|---|
|
sizeLimit |
Integer value that limits the number of query results returned for authentication. |
|
timeLimit |
Integer value that limits the number of seconds before a query times out. |
|
pageSize |
Page size of results that adsi request from the server. The default is 0. |
|
useImplicitBind |
0 = Implicit Credentials 1 = Explicit Credentials 2 = Use UserPrincipalName |
|
adsiCredential |
An LDAP specification of a user, such as "cn=Administrator,cn=users,dc=myhost,dc=mydomain,dc=com" |
|
adsiPassword |
An encoded text string representing the LDAP user's password. |
|
adsiUPN |
Text string of UserPrincipalName when use ImplicitBind=2. A UPN string is typically an email address with the format: user@company.com |
|
useGCForAuthn |
True/False Change the useGCForAuthentication parameter to false. |
|
asynchronousSearch |
True/False By default, ADSI is enabled to perform asynchronous searches. If set to false, it does synchronous searches |
|
asynchronousSearch |
adsiUPN This parameter needs to be added if useImplicitBind is set to 2. The value of the parameter should be the UPN (userPrincipalName) of the user. |
There are several tasks involved in configuring ADSI for the Identity System. Details are provided in the Oracle Access Manager Installation Guide.
Task overview: Configuring ADSI for the Identity System
Prepare your Active Directory, as described in your Microsoft documentation and the Oracle Access Manager Installation Guide.
Specify ADSI when you install and set up Oracle Access Manager, as described in the Oracle Access Manager Installation Guide.
By default, this creates a pure ADSI configuration in which a single ADSI directory profile (DB agent) enables associated Identity Servers to perform all operations with a primary domain controller in your Active Directory tree using an Implicit Bind.
Set up Active Directory attributes and enable change-password permissions, as described in the Oracle Access Manager Installation Guide.
Configure the default directory profile, as described in "Enabling ADSI for a Default Directory Profile" .
Enable ADSI for additional directory profiles, if desired, as discussed under "Enabling ADSI for Other Directory Profiles".
The Identity System automatically creates a default directory profile during installation. You can enable ADSI for the default profile during Identity System setup.
The default database agent is automatically assigned a name using the convention default-ois-machine name. You should modify this name to the respective domain name because users must enter this name during authentication.
If you have a noncontiguous forest of domain trees, you need to associate a separate ADSI database agent for each primary domain controller. Additional directory profiles are configured after Identity System installation and set up, as outlined in the following procedure and described in "Specifying Identity System Administrators".
To enable ADSI for additional directory profiles
Navigate to the Identity System Console.
http://hostname:port/identity/oblix
From the Identity System Console, click the System Configuration sub-tab, then click the Directory Profiles link in the left navigation pane.
Click the Add button to display the Create Directory Server profile page.
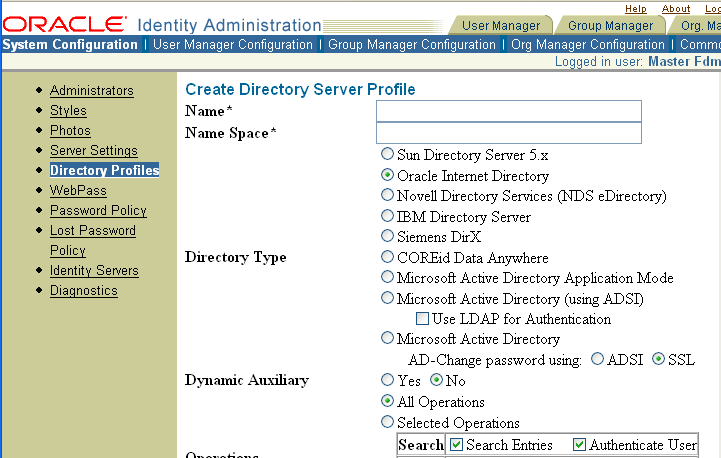
Oracle recommends using the respective domain names as the profile names because users must enter this name during authentication.
Enter a name for this directory profile.
You must configure a directory profile for each Domain and Sub_domain controller. For more information, see "Configuring ADSI for the Identity System".
Enter a namespace for this directory profile.
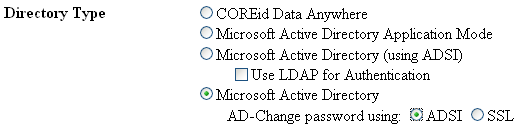
There are multiple choices for the directory type. To use Active Directory without ADSI enabled, you should select Microsoft Active Directory.
|
Note: You still have the option to enable ADSI or SSL for changing passwords. Also, you can enable LDAP by selecting the secondary check box, Use LDAP for Authentication. When LDAP is enabled, an ADSI DB Agent associates with the primary domain controller. An LDAP agent needs to be configured for whichever Sub_domain controller you want to use to authenticate. |
Select the appropriate directory type. For example:
Select the operations supported for this directory profile, for example:
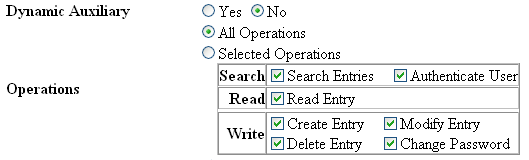
If this is a directory profile configured for a domain controller, select all operations.
Complete the rest of the directory profile and save it, as usual.
See "Managing Directory Server Profiles" for more information about configuring directory profiles. See also "Managing Directory Server Profiles" for more information about multiple directory profiles (DB agents).
The Policy Manager uses the Identity Server for authentication. Therefore, the login operation uses the same mode (ADSI or LDAP) as the Identity Server it talks to. During Policy Manager setup, by default, you use an Explicit Bind to enable the Policy Manager and Access System Console to perform all operations except authentication in the Active Directory tree.
|
Note: SSL is not required for ADSI configurations with Oracle Access Manager. However your business may require SSL for other reasons. For example, directory binds are in clear text, and SSL is not automatically provided. |
By default, enabling ADSI for the Access Server creates a pure ADSI configuration in which the Access Server performs all operations with a primary domain controller in your Active Directory tree using an Implicit Bind.
Configuring ADSI support in the Access System involves the following tasks.
Task overview: Configure ADSI for the Access System
Validate your setup, as described in the Oracle Access Manager Installation Guide appendix.
Install and set up the Policy Manager, as described in the Oracle Access Manager Installation Guide.
Install the Access Server and setup ADSI, as described in the Oracle Access Manager Installation Guide.
Install the WebGate, as described in the Oracle Access Manager Installation Guide.
Enable LDAP authentication for the Access Server, if desired, as described in "Enabling LDAP Authentication for the Access Server".
Enabling LDAP Authentication for the Access Server
ADSI authentication may be slower than LDAP. For that reason, you may wish to use LDAP for authentication while other operations such as authorization and auditing are handled by ADSI.
To enable LDAP authentication for the Access Server
Open AccessServer_install_dir\access\oblix\apps\common\bin\globalparams.xml with a text editor.
Change the value of useLDAPBind to true.
Save globalparams.xml.
Create a copy of ConfigDBfailover.xml located in AccessServer_install_dir\access\oblix\config\ and name it AppDBfailover.xml.
Both files should reside in the same directory.
Save.
Restart the Access Server.
Based on your Active Directory forest deployment you may need to change the page-size parameter in the adsi_params file. For example, in Figure B-2 you have a parent-child relationship between your Active Directory domains, and you have user(s) in both the parent and child domain with the same samaccountname.
Assume the authentication scheme is Oracle Access and Identity for an Active Directory forest. In this case:
For user1k1 to log in to the Child1 domain, the user can enter their user ID as Chidl1\user1k1.
For user1k2 to log in to the Child2 domain, the user can enter their user ID as Child2\user1k2.
However, if the pageSize parameter is set to 0, for user1k1 from the parent domain to log in entering Parent\user1k1 produces an error: "The credentials Parent\user1k1 used in the login correspond to more than one user profile in the Identity System. The correspondence must be unique."
This is because when the page size is set to 0, ADSI searches the subdomains, therefore finding two users who satisfy the criteria. For user1k1 and user1k2 to log in to the parent domain you need to set the pageSize parameter to a finite value. Oracle recommends using 100.
For information on troubleshooting, see "Troubleshooting Oracle Access Manager".