| Oracle® Access Manager Integration Guide 10g (10.1.4.0.1) Part Number B25347-01 |
|
|
View PDF |
| Oracle® Access Manager Integration Guide 10g (10.1.4.0.1) Part Number B25347-01 |
|
|
View PDF |
This chapter describes the integration of Oracle Access Manager with mySAP.com e-business platform.
This chapter covers the following topics:
Integrating Oracle Access Manager with mySAP enables the use of Oracle Access Manager functionality across all mySAP Web-based applications and other Oracle Access Manager-protected enterprise resources and applications.
Integrating Oracle Access Manager with mySAP provides the following Oracle Access Manager features to mySAP implementations:
Access System single sign-on (SSO) for mySAP applications and other Access System-protected resources.
Authentication, authorization, and auditing services for mySAP applications.
The following Access System authentication schemes to provide single sign-on for mySAP applications:
Form
Basic
Custom
X509 Certificates
Integrated Windows Authentication
Microsoft .Net Passport
Ability to use the Identity System for identity management.
The Identity System provides identity management features such as portal inserts, delegated administration, workflows, and self-registration to applications such as mySAP.
The integration of Access System single sign-on with mySAP involves the SAP components described in the following sections.
SAP Internet Transaction Server (ITS) is a mySAP.com component that provides a Web front-end and allows access to data from the SAP R/3 applications. SAP R/3 provides Enterprise Resource Planning (ERP) functionality for the mySAP.com e-business platform.
SAP ITS consists of two major components: AGate and WGate.
The AGate is responsible for session management including mapping of SAP R/3 screens or function modules to HTML. AGate manages Web sessions including timeout handling and SAP R/3 connection pooling. Based on SAP R/3 information, it generates HTML documents that are forwarded to WGate.
The WGate passes requests to AGate and receives HTML pages back from AGate. The WGate supports various HTTP server interfaces such as Apache, Netscape Server Application Programming Interface (NSAPI), and Internet Server Application Programming Interface (ISAPI).
The Pluggable Authentication Service (PAS) is a part of the Internet Transaction Server that is used for single sign-on between SAP and third-party security providers. PAS enables Oracle Access Manager to authenticate users who attempt to access SAP.com resources.
The following figure illustrates the integration between Oracle Access Manager and SAP ITS and the SAP Enterprise Portal. The process overview that follows describes a scenario where the user first authenticates to a resource that is protected by the Access System. The user is then granted access to an SAP resource.
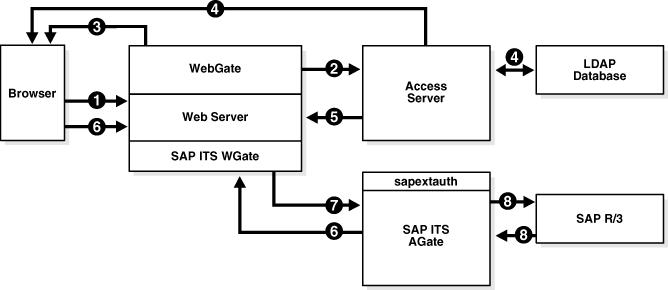
Process overview: Integration with SAP ITS
A user attempts to access content or an application on a company's server.
The WebGate intercepts the request and queries the Access Server for the security policy that determines if the resource is protected.
The security policy consists of an authentication scheme, authorization rules, and allowed operations. Based on the authentication and authorization success or failure, specified actions are performed.
If the resource is protected, the WebGate prompts the user for authentication credentials.
The credentials that the WebGate requests depend on the authentication scheme configured in the Access System, for example, Basic over LDAP or Form-based authentication.
If the credentials are validated, the Access System authenticates the user and sets an encrypted ObSSOCookie in the user's browser.
After authenticating, the authorization rules defined in the Access System are applied based on the security policy.
Specific actions are performed based on the authorization rules. If the user is authorized, access to the requested content is allowed.
If the user is not authenticated or authorized, he or she is denied access and redirected to another URL, as determined by the administrator.
The user enters the URL for the Oracle Access Manager-specific ITS PAS service.
For integration with mySAP, an ITS-specific HTTP header variable is created and filled with unique Oracle Access Manager-SAP R/3-mapped user ID information.
The Oracle Access Manager-specific ITS service uses the sapextauth module to extract the HTTP header variable and identify the Oracle Access Manager-SAP R/3-mapped user ID.
Optionally, the SAP Workplace Server maps the external Oracle Access Manager user ID to the SAP System ID.
It is recommended that Oracle Access Manager extract the correct SAP user ID from the LDAP directory that is used for the initial authenticated user. In this case, no lockup table is required in the SAP system.
If mapping is successful, the AccessGate issue the user an SAP Logon Ticket and redirects the user to either the Workplace service or any other ITS service. Future ITS URLs will use issued SAP Logon Tickets for passing logon information to the SAP R/3 system.
Oracle Access Manager supports the following versions of SAP Server and the SAP Enterprise Portal:
| SAP | SAP Portal |
|---|---|
| SAP R3 v4.6DSAP ITS v6.10 and v6.20 | v 6.0 SP2 |
Before you can integrate Oracle Access Manager with SAP, you must complete the following tasks.
To prepare for the integration with SAP
Install the following SAP applications:
SAP ITS v 6.10 with Patch Level 11, Compilation 4 with Patch Level 340 or later (refer to SAPNet Note: 494984).
An SAP ITS component configured to talk to the R3 System through Secure NetWork Communications (SNC).
SNC is required to generate SSO2 security tickets.
sapntauth library (refer to SAPNet Note: 493107).
Refer to SAP documentation for information on installing SAP applications and components.
Install the following Oracle Access Manager components:
Identity Server
WebPass
Access Server
Policy Manager
WebGate
See the Oracle Access Manager Installation Guide for information on installation.
For each Web server instance that has ITS installed, install and configure a WebGate.
Ensure that mySAP and Oracle Access Manager components are able to communicate with each other through TCP/IP.
Ensure that the servers on which SAP ITS and Oracle Access Manager components are installed have a fully qualified domain name.
For example, integrate-1.oblix.net.
Synchronize the time on all servers where SAP and Oracle Access Manager components are installed.
Ensure that the users exist in the Oracle Access Manager LDAP directory as well as on the SAP R3 system database.
The user ID in Oracle Access Manager and SAP must be same or be mapped to each other. Any attribute in a user's profile can be configured as the SAP ID and passed directly to SAP. Alternatively, SAP can be configured to map the SAP ID to any user attribute that it receives from Oracle Access Manager.
Configure the Web browser to allow cookies.
Setting up Oracle Access Manager single sign-on for mySAP requires the installation and configuration of several SAP and Oracle Access Manager components.
Task overview: Setting Up Oracle Access Manager single sign-on for mySAP
Set up SAP, including the following items, as described in "Setting Up SAP for Integration with Oracle Access Manager":
Install the SAP GUI.
Install and configure Web server instances for SAP ITS.
Install SAP ITS.
Test connections between ITS and SAP R/3.
Install and configure SAP SNC.
Configure SAP PAS for Access System header variables.
|
Note: For instructions on installing SAP components, refer to your SAP documentation. |
Set up the Access System, including the following items, as described in "Setting Up Oracle Access Manager for Integration with SAP".
Install a WebGate
Create access control policies in the Access System to protect SAP resources
Complete activities in "Testing Integration Between Oracle Access Manager and SAP".
The following procedures describe setting up SAP for the integration.
To set up SAP for integration with Oracle Access Manager
Install the SAP Graphic User Interface (GUI) on the client machine.
This is the Web interface for SAP R/3 applications. It dynamically converts SAP transaction screens to HTML pages.
Install and configure two Web server instances; one instance for administrative (ADM) purposes and the second instance as an interface to SAP R/3 applications.
After you have configured the instances, test the connection from ITS to SAP R/3 for both instances.
To test the ADM instance installation
Open a Web browser and enter the URL to log in to the ADM instance; for example:
http://host:port/scripts/wgate/admin/!
or
http://host:port/scripts/wgate/adminremote/!
where host is a fully qualified name of the host machine such as xyz.domain.com, and port is the port number of the host machine.
To test SAP R/3 instance installation
Open a Web browser and enter the following URL to access the GUI of the SAP R/3 instance:
http://host:port/scripts/wgate/webgui/!
Where host is a fully qualified name of the host machine such as xyz.domain.com and port is the port number of the host machine.
The mySAP.com login screen appears.
Install and configure SAP Secure Network Communication (SNC).
SAP SNC provides secure connectivity from the AGate to the SAP R/3 applications. SNC is recommended because Oracle Access Manager provides an authenticated user ID to SAP.
If the WGate is installed on a different server than the AGate, it is recommended that you configure SAP SNC between the two servers.
To set up SAP PAS for integration with Oracle Access Manager
Configure the SAP PAS system to use Header Variables for SSO:
Configure WGate to pass the Access System header variables to AGate. To do this, use the parameter PassHeader located in the wgate.conf file.
For example:
Ex.PassHeader HTTP_SAPUID
Refer to the SAP documentation for the location of the wgate.conf file.
Define the information that PAS requires to use the Access System as an external authentication provider.
To do this, you must configure the PAS Service for Oracle Access Manager in the Oblix.srvc file located in SAP_install_dir\ITS\2.0\ITSInstanceName\templates
Where SAP_install_dir is the directory where you installed SAP, and ITSInstanceName is the name of the ITS instance that you configured.
Create and configure PAS templates to handle login, error, and redirect actions that may occur when using the Access System's authentication service.
Save these templates in the SAP_install_dir\ITS\2.0\ITSInstanceName\templates directory.
Create the directory structure and files as follows:
<Name of Service> <Name of Theme> login.html extautherror.html redirect.html
Name of Service is the name of the service file; for example, oblix.srvc.
Name of Theme is the name of the theme parameter in the oblix.srvc file.
The following procedures describe setting up Oracle Access Manager for this integration.
To set up Oracle Access Manager for integration with SAP
Install a WebGate on the Web server instance supporting the ITS connection to the SAP R/3 system.
See the Oracle Access Manager Installation Guide for information on installing a WebGate.
In the Access System, create a policy domain to protect SAP resources under /scripts/wgate.
To do this, create a policy domain that protects the Web servers where SAP ITS and WebGate are installed. The Access System sets header variables that are passed on to the Oracle Access Manager-specific ITS service, allowing access only to specified users.
See the Oracle Access Manager Access Administration Guide for information on creating policy domains.
In the Authentication Rule, Actions page of the policy domain, configure the action to set an Access System header variable uid to the SAP uid.
The following example maps uid to the SAPUID:
HeaderVar HTTP_SAPUID uid
In the Authorization Rules, Allow Access page of the policy domain, select the Oracle Access Manager/SAP users to whom you want to grant access to the resources that are protected by the policy domain.
The single sign-on configuration is now complete.
After you have integrated Oracle Access Manager with SAP, test for successful Access System authentication and single sign-on with mySAP.
The following procedures test the following scenarios:
A valid login to an SAP R/3 application with a user ID that is authorized both in the Access System and in SAP.
A valid login to an SAP R/3 application with a user ID that is authorized in the Access System but is unauthorized in SAP.
A valid login to the Identity System and an SAP R/3 application with a user ID that is authorized in both the Access System and SAP.
A valid login to the Identity System and an SAP R/3 application with a user ID that is authorized in the Access System but is unauthorized in SAP.
If Access System authentication was set up correctly, as an authorized user in both Oracle Access Manager and SAP, you will be allowed to access the Identity System as well as any SAP R/3 application. If you are an authorized user only in Oracle Access Manager, you will be allowed to access only the Identity System but not a SAP R/3 application.
If single sign-on has been set up correctly in the Access System, as an authorized user in both Oracle Access Manager and SAP you will need to authenticate to Oracle Access Manager only once. After successful authentication, you will be able to access the Identity System and multiple SAP R/3 applications without authenticating again.
To test Access System authentication
Access any SAP R/3 application.
If integration was successful, the Access System will challenge you for your credentials.
Log in with an authorized Oracle Access Manager/SAP user ID.
You will be allowed to access the R/3 application.
Attempt to log in to a SAP R/3 application with a user ID that is authorized in Oracle Access Manager but is unauthorized in SAP.
Login will fail with message stating that your password is invalid.
|
Note: The message is incorrect. The message should state that your user ID is invalid. |
To test Oracle Access Manager single sign-on
Access any SAP R/3 application.
If the integration was successful, the Access System will challenge you for credentials.
Log in with an authorized Oracle Access Manager/SAP user ID.
You will be allowed to access the R/3 application.
Attempt to log in to the Identity System.
If single sign-on is successful, you will be able to log in to the Identity System without being challenged by the Access System.
Attempt to log in to the Identity System and a SAP R/3 application with a user ID that is authorized in Oracle Access Manager but is unauthorized in SAP.
You will be able to log in to the Identity System but not into SAP. SAP will display a message stating that your password is invalid.
A portal provides a single point of access to enterprise data and applications, presenting a unified and personalized view of information to employees, customers, and business partners.
The SAP Enterprise Portal, which runs on top of SAP R/3, provides unified information from enterprise applications, data warehouses, unstructured document collections, and the Internet.
Integrating Oracle Access Manager with the SAP Portal provides the following Oracle Access Manager functionality:
Ability to use the Identity System to manage users and groups.
Oracle Access Manager and SAP Enterprise Portal share the same LDAP directory. When a new user or group is created in the Identity System, the SAP user repository is updated with the new data.
|
Note: The SAP Portal supports only static groups. |
Access System single sign-on for SAP Enterprise Portal and other Access System-protected resources.
The Access System authenticates and authorizes users who attempt to access the SAP Portal. After successful authentication and authorization, users can access any Access System-protected resource or application without being prompted again for credentials.
This section discusses the following topics:
Architecture for the Integration with SAP Enterprise Portal 6.0 SP2
Supported Platforms for Integrating with SAP Enterprise Portal 6.0 SP2
Configure Oracle Access Manager for SAP Enterprise Portal 6.0
Configure SAP Enterprise Portal 6.0 for External Authentication
Troubleshooting the Integration with SAP Enterprise Portal 6.0
The following diagram illustrates this integration:
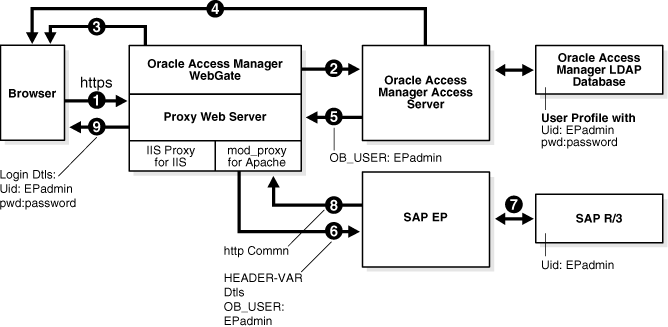
Process overview: Integration with SAP ITS and SAP Enterprise Portal 6.0 SP2
A user attempts to access content via the SAP Enterprise Portal.
For example, the user may enter the following URL to access an HR application through a proxy server:
https://host:port/irj
The WebGate intercepts the request and queries the Access Server for the security policy that determines if the resource is protected.
The security policy consists of an authentication scheme, authorization rules, and allowed operations. Based on the authentication and authorization success or failure, specified actions are performed.
The Access System security policy for the SAP /irj login URL is applicable to all resources accessed via the https://host:port/irj URL.
Note that the SAP Enterprise Portal has its own authorization system that can be configured to set user access to iViews.
If the resource is protected, the WebGate prompts the user for authentication credentials.
The credentials that the WebGate requests depend on the authentication scheme configured in the Access System, for example, Basic over LDAP or Form-based authentication.
If the credentials are validated, the Access System authenticates the user and sets an encrypted ObSSOCookie in the user's browser.
After authenticating, the authorization rules defined in the Access System are applied based on the security policy.
Specific actions are performed based on the authorization rules. If the user is authorized, access to the SAP Portal login (the requested content) is allowed. For SAP Enterprise Portal header variable integration, the Access Server sets the authenticated user ID in a header variable.
If the user is not authenticated or authorized, he or she is denied access and redirected to another URL, as determined by the administrator. For example, the user may be redirected to an "invalid credentials" page.
For the integration with SAP Enterprise Portal, the proxy Web server redirects the request to the SAP Enterprise Portal internal Web server that contains the header variable details.
SAP Enterprise Portal uses the header variable value to check the mapping of the user ID against the configured back-end, for example, SAP R/3.
Both the Oracle Access Manager and SAP Enterprise Portal back-ends must contain the same user ID value.
Upon successful mapping, SAP Enterprise Portal allows the user to access the requested resource.
SAP Enterprise Portal sends a response to the proxy, and the proxy redirects to the client browser.
All interaction with the SAP Enterprise Portal takes place through the proxy server.
The following tables list the supported platforms.
Table 12-1 Integration with Oracle Access Manager 6.x
| SAP Enterprise Portal | Oracle Access ManagerIdentity Server | SAP Enterprise Portal Proxy | Oracle Access ManagerAccess Server |
|---|---|---|---|
|
SAP Enterprise Portal 6.0 SP2 patch 4 or higher on Windows |
6.5.x |
Apache 1.3.x on AIX |
6.1.1.x WebGate (SSL or non-SSL) |
|
SAP Enterprise Portal 6.0 SP2 patch 4 or higher on Windows |
6.5.x |
Apache 2.0.x on Windows |
6.5.2 WebGate |
Table 12-2 Integration with Oracle Access Manager 7.x
| SAP Enterprise Portal | Oracle Access ManagerIdentity Server | SAP Enterprise Portal Proxy | Oracle Access ManagerAccess Server |
|---|---|---|---|
|
SAP Enterprise Portal 6.0 SP2 patch 4 or higher on Windows |
7.0.4 |
Apache 1.3.x on AIX |
7.0.4 WebGate (SSL or non-SSL) |
|
SAP Enterprise Portal 6.0 SP2 patch 4 or higher on Windows |
7.0.4 |
Apache 2.0.x on Windows |
7.0.4 WebGate |
Complete the following tasks before integrating Oracle Access Manager with the SAP Enterprise Portal 6.0.
Task overview: Integration prerequisites for SAP Portal 6.0 integration:
Confirm the installation of SAP Enterprise Portal 6.0 SP2 and its components and applications:
Ensure SAP J2EE Engine version 6.2 patch level 26 or higher is installed, according to the instructions in the SAP note 616501.
Apply SAP Enterprise Portal 6.0 patch level 4 or higher. This is required for the SAP logout URL redirection functionality.
Confirm that SAP Enterprise Portal is functional and able to access the applications.
Ensure that the Identity System and Access System are installed and running.
Ensure that the Oracle Access Manager and the SAP Enterprise Portal back-ends contain the same user ID information.
This is essential for this integration.
Complete the following tasks before integrating Oracle Access Manager with the SAP Enterprise Portal 6.0.
Task overview: Integration prerequisites for Oracle Access Manager integration:
Configure a proxy server to access SAP Enterprise Portal 6.0.
Configure Oracle Access Manager for the SAP Enterprise Portal 6.0.
Configure a WebGate on the proxy server.
Configure SAP Enterprise Portal 6.0 for external authentication.
The following procedure describes how to configure a proxy to access SAP Enterprise Portal 6.0.
To configure Apache Web server 1.3.x or 2.0.1
Set up the Apache proxy in non-SSL mode or SSL mode, as described in the Apache documentation.
If https communication is used with the SAP Enterprise Portal 6.0, use SSL mode.
To enable the proxy to the SAP Enterprise Portal 6.0, enter the following in httpd.conf:
ProxyRequests Off ProxyPass /irj http://sap_host:port/irj ProxyPassReverse /irj http://sap_host:port/irj ProxyPreserveHost On
Where sap_host is the name of the machine hosting the SAP Enterprise Portal 6.0 instance and port is the listen port for the SAP Enterprise Portal 6.0 instance. This set of directives specifies that all of the requests to this Web server of the form http://apache_host:port/irj or https://apache_host:port/irj are redirected to http://sap_host:port/irj or https://sap_host:port/irj.
Restart the proxy Web server.
Access the following URL:
Non-SSL—http://apachehost:port/irj
SSL—https://apachehost:port/irj
This request should be redirected to the SAP Enterprise Portal 6.0 login.
Log in using the SAP Enterprise Portal 6.0 administrator login ID.
The administrator should be able to perform the available administrative functions.
Log in as a non-administrative user.
This user should be able to perform non-administrative functions.
The following procedure describes configuration of the security policy in Oracle Access Manager to protect logins to SAP Enterprise Portal 6.0. For more information on configuring policy domains, see Oracle Access Manager Access Administration Guide.
To configure Oracle Access Manager for SAP Enterprise Portal 6.0
Log in to the Access System Console as a Master Access Administrator.
Click the Access System Configuration tab.
Click Add New AccessGate in the left navigation pane.
Configure a WebGate that you will install on the proxy server, as follows:
AccessGate name—Enter any meaningful name, for example, SAP_AG. Use an alphanumeric string, and do not include spaces in the name.
Host name—Enter the name of the Apache proxy machine.
Access Management Service—Click the option to enable this service.
Click Save, then click List Access Servers at the bottom of the page to associate this WebGate with a defined Access Server.
Click Host Identifiers in the left navigation pane and configure the host identifiers using the fully qualified proxy machine name and port for the Apache proxy.
Click the link for the Policy Manager at the top of the page.
Click Create Policy Domain in the left navigation pane and create a new policy named SAP EP Security Policy.
Click the Resources tab, click Add, and define the resources for the policy as follows:
Name—SAP EP Security Policy
Type—http
Host identifiers—Enter the proxy host URL prefix: /irj.
Description—SAP EP Login URL
Click the authorization rules tab, then click Add, and define the authorization rules for the policy as follows:
Name—SAP Authorization Rule
Enabled—Yes
Allow takes precedence—Yes
Click Save, then click the Allow Access tab, then click Add and add a valid user or group list.
Click Save, then click the Actions tab, and configure the following actions:
Authorization Success Returns—Configure a Type of HeaderVar, a Name of OB_USER, and a Return Attribute of uid.
Authorization Failure—Configure an appropriate failure action. For example, you can configure a redirect to a proxy URL page that displays an "Invalid login credentials" message.
Click the Default Rules tab, click the Authentication Rule sub-tab, click Add, and define the default authentication rule as follows:
Name—SAP Authentication Rule
Authentication Scheme—Select either Basic over LDAP or Form based authentication. Oracle recommends that you use a form-based authentication scheme. If you use the basic authentication scheme, also set the Challenge Redirect field to another WebGate to ensure that the ObSSOCookie is set.
In the Default Rules tab, click the Authorization expression sub-tab, click Add, and create an authorization expression that uses the SAP Authorization Rule.
If you configured a form-based authentication scheme, ensure that a login.html page is configured in the proxy server document root.
This form will be used to get the user credentials. See the Oracle Access Manager Access Administration Guide for details.
Also, if you configured a form-based authentication scheme, ensure that a logout.html page is present on the proxy Web server document root.
You can create a custom logout page using HTML, JSP, or a CGI protocol.
The default logout page, named logout.html, is in the following location:
WebGate_install_dir\access\oblix\apps\common\bin
Where WebGate_install_dir is the directory where the WebGate will be installed. Ensure that the name of the logout page contains the string "logout.".
Ensure that the user ID that is returned by the OB_USER header variable exists in the user management data sources for SAP Enterprise 6.0.
Install a WebGate on the Web server instance that supports the proxy connection to the SAP Enterprise Portal 6.0 instance. See the Oracle Access Manager Installation Guide for details.
The following steps describe enabling external authentication in SAP Enterprise Portal 6.0 using the OB_USER header variable.
For more information on configuring authentication schemes for SAP Enterprise Portal, see the SAP Enterprise Portal 6.0 SP2 Enterprise Postal Security Guide.
To configure SAP Enterprise Portal 6.0 for external authentication
To enable logout from a single sign-on session in both SAP Enterprise Portal 6.0 and Oracle Access Manager, configure a logout URL in SAP Enterprise Portal 6.0 from the administration interface.
The URL for the administration interface is as follows:
http://sap_host:port/irj/
Where sap_host is the name of the machine hosting the SAP Enterprise Portal 6.0 and port is the listen port for the portal.
From the administration interface, click System Administration, then System Configuration, then UM Configuration, then Direct Editing.
Add the following lines to the end of the configuration file:
ume.logoff.redirect.url=http(s)://proxy_host:port/logout.html ume.logoff.redirect.silent=false
Where http(s) is either http or https, proxy_host is the name of the proxy Web server and port is the listen port for the proxy.
Save the changes and log out.
Stop the SAP J2EE dispatcher and server.
Browse to the following directory:
SAP_J2EE_engine_install_dir\ume
Back up the file authschemes.xml.bak to another directory.
Rename authschemes.xml.bak to authschemes.xml.
Open authschemes.xml in an editor and change the reference of the default authentication scheme to the authentication scheme header as follows:
<authscheme-refs>
<authscheme-ref name="default">
<authscheme>header</authscheme>
</authscheme-ref>
</authscheme-refs>
In the authentication scheme header of authschemes.xml, specify the name of the HTTP header variable where the Access System provides the user ID.
As described in "Configure Oracle Access Manager for SAP Enterprise Portal 6.0" on page 12-12, this is the OB_USER header variable. You configure this header variable as follows:
<authscheme name="header">
<loginmodule>
<loginModuleName>
com.sap.security.core.logon.imp.HeaderVariableLoginModule
</loginModuleName>
<controlFlag>REQUISITE</controlFlag>
<options>Header=OB_USER</options>
</loginmodule>
<priority>5</priority>
<frontEndType>2</frontEndType>
<frontEndTarget>com.sap.portal.runtime.logon.header</frontEndTarget>
</authscheme>
The control flag value REQUISITE means the login module must succeed. If login succeeds, authentication continues through the list of login modules. If it fails, control immediately returns to the application and authentication does not continue through the list of login modules.
Restart the portal server and J2EE engine.
The modified authschemes.xml file will be loaded into the Portal Content Directory (PCD). SAP Enterprise Portal 6.0 will rename it as authschemes.xml.bak.
The following are recommended tests for the integration.
Enter the appropriate URL for your proxy in a browser:
http(s)://proxy_host:port/irj
Oracle Access Manager should prompt for user credentials depending on the authentication scheme (form-based or Basic over LDAP).
Enter valid user credentials at the prompt.
These credentials should belong to a user in Oracle Access Manager who is authorized to access /irj. This user ID must also be present in the SAP Enterprise Portal 6.0 User Management System.
The user should be logged into the SAP Enterprise Portal 6.0 having supplied the login credentials to Oracle Access Manager.
If the user have administrative privileges in SAP Enterprise Portal 6.0, ensure that the usual administrative functions are available for this user.
For example, search for other SAP Enterprise Portal users through the user Management System.
Log off from the SAP Enterprise Portal.
You should be redirected to the logout.html page that you configured. Both the SAP Enterprise Portal and the Oracle Access Manager sessions should end.
Access SAP Enterprise Portal login again in the same browser.
Oracle Access Manager should prompt for login credentials again.
Access the SAP Enterprise Portal login page without using the proxy by entering the following in a browser:
https://sap_host:port/irj
You should receive the following error:
Cannot logon user defined in header variable!
The following information is intended to help you troubleshoot issues with this integration.
Problem—The browser has problems displaying the SAP administration interface through the proxy server. You may receive an "object not found" error and related javascript errors.
Solution—See the following SAP document for supported browsers, "SAP NetWeaver '04 SR1 PAM: Browsers for end users and admin functionality." SAP has recommended Internet Explorer 6, and it supports almost all proxy operations. In the case of Internet Explorer, the Microsoft Security patch can sometimes affect the display of the user interface. See SAP Note 785308 for details.