| Oracle® Access Manager Access Administration Guide 10g (10.1.4.0.1) Part Number B25990-01 |
|
|
View PDF |
| Oracle® Access Manager Access Administration Guide 10g (10.1.4.0.1) Part Number B25990-01 |
|
|
View PDF |
This chapter discusses several additional Access System configuration and management functions available within the Access System Console. Topics include:
For more information about managing the Access System, see:
Oracle Access Manager should be installed and set up, as described in the Oracle Access Manager Installation Guide. Read the Oracle Access Manager Introduction, which provides an overview of Oracle Access Manager not found in other manuals. Also, familiarize yourself with the Oracle Access Manager Identity and Common Administration Guide, which provides a brief review of Access System applications and installation; introduces Access System configuration and administration; and includes common functions, configuration, and administration.
Earlier chapters in this manual describe configuring administrators and viewing server settings through the Access System Console, System Configuration functions. That information is not repeated here.
The rest of this section discusses the following topics:
Numerous functions are available in the Access System Console, Access System Configuration tab, as shown in the following list. Unless indicated, other chapters in this manual describe Access System Configuration functions:
Access Server Clusters: View existing Access Server Clusters, add new and modify existing Access Server Clusters, configure and delete Access Server Clusters.
AccessGate Configuration: View existing AccessGates, add new and modify existing AccessGates, configure and delete AccessGates.
Access Server Configuration: View existing Access Servers, add new and modify existing Access Servers, configure cache and audit settings.
Authentication Management: Configure Authentication Rules.
Authorization Management: Configure Authorization Rules.
User Access Configuration: List revoked users, flush the user cache, as described in this chapter under"Configuring User Access" .
Common Information Configuration: Generate a cryptographic key to encrypt cookies (covered here), configure a master auditing rule, manage resource type definitions, flush the Password Policy Cache (covered here), handle duplicate action headers. For more information on items covered here, see:
Host Identifiers: Configure host identifiers.
There are a number of options available in the Access System Console to perform system management operations, which are described in this chapter:
Diagnostics: Show Access Server details, including connection information, as described in "Running Diagnostics".
Manage Reports: Create, view, modify, and execute User Access Privilege Reports, as described in "Managing User Access Privilege Reports".
Manage Sync Records: Archive or purge Sync Records, as described in "Managing Sync Records".
For information about diagnostics, auditing, reports, and logging, see the Oracle Access Manager Identity and Common Administration Guide.
You use the User Access Configuration function available through the Access System Console, Access System Configuration tab, to manage revoked users and flush user data from the cache. This section covers the following topics:
|
Note: You must be a Master Access Administrator or a Delegated Access Administrator with appropriate permissions to configure user access. |
For more information on caches, see "Automatic Access System Cache Flush". See also the Oracle Access Manager Deployment Guide.
You can create and modify a list of users who are prohibited from accessing any of your resources. This list supersedes any other policies controlling user access to your resources. Once a user has been revoked, if the user tries to refresh the browser, or go to another protected resource, they are denied access. If a revoked user tries to log in, he or she is presented with the following error:
The user corresponding to the credentials credentials used in the login has been revoked. . .
To create the revoked user list
In the Access System Console, click Access System Configuration, then click User Access Configuration.
The User Access Configuration screen appears.
Click Revoked Users.
The Modify User Revocation List screen appears, displaying the names of revoked users. If no revoked users exist, the Configure User Revocation List screen appears. If any exist, their names appear beneath the Revoked Users link.
Click Select User, then use the Selector feature (Select User button) to add or remove revoked users.
See the Oracle Access Manager Identity and Common Administration Guide for instructions on using the Selector.
Click Save to save your changes (or click Cancel to exit without saving.
This feature lets you delete information about certain users from the AccessGate and Access Server caches. For example, you might want to flush a user's information after that user's rights to view or modify an attribute have changed.
To flush user information from the cache
With any screen within the User Access Configuration feature displayed, click the Flush User Cache tab.
For example:
Access System Console, select Access System Configuration, select User Access Configuration, then click Flush User Cache
The Flush all cached information for specified users screen appears.
Use the Selector feature (Select User button) to create a list of users whose information is flushed from all caches.
See the Oracle Access Manager Identity and Common Administration Guide for instructions on using the Selector.
The names of people that you have selected appear.
Click Flush Cache.
You are prompted to confirm your decision. If you click OK the names are cleared from the screen, and information about these users is flushed from AccessGate and Access Server caches.
You use the Shared Secret function available through the Access System Configuration, Common Information Configuration tab, to generate a key that encrypts single sign-on cookies sent from an AccessGate to a browser.
|
Note: You must be a Master Access Administrator to create a shared secret key. You should generate a cryptographic key as soon as possible after installing Oracle Access Manager, otherwise a less secure default is used. |
AES is a new encryption scheme introduced in Oracle Access Manager 7.0. If you have a new installation of Oracle Access Manager 10.1.4, AES is the default encryption scheme. RC6 encryption is deprecated in Oracle Access Manager 10.1.4, and its support will be removed in future releases.
If you have upgraded to Oracle Access Manager 10.1.4 from an older version, the older encryption scheme will be retained. Older WebGates may co-exist with newer WebGates as described in the:
Use RC4 as the encryption scheme if you have version 5.x and version 7.x WebGates co-existing together.
Use RC6 as the encryption scheme if you have version 6.x and version 7.x WebGates co-existing together.
You should use AES encryption only when all the WebGates and Access Servers are upgraded to Oracle Access Manager version 7.0 and higher.
|
Note: If the shared secret is generated more frequently than the session timeout, then the user may have a cookie that was encrypted using a shared secret that is more than two generations old. In this case, the cookie is rejected and the user is forced to re-authenticate. |
To generate a cryptographic key
In the Access System Console, click Access System Configuration, click Common Information Configuration.
The Common Information Configuration screen appears.
Click the Shared Secret tab at the top of the screen.
The Generate shared secret screen appears.
Click Modify.
The Generate shared secret page now includes various ciphers from which to choose.
Select the appropriate cipher option for the shared secret (Oracle recommends using the AES cipher).
Click Generate Secret only once.
Oracle Access Manager generates a new cryptographic key and distributes it to each Access Server on your system. The new key replaces the existing key without disrupting service to end users. Re-authentication only happens when the session times out. This process is called grandfathering. Clicking Generate Secret multiple times can put the shared secret key in Identity out of synch with the key in the Policy Manager.
A message informs you the operation was successful.
If you change the shared secret during a user session, the user does not need to re-authenticate. If a cookie is being decrypted with the old shared secret and the cookie is refreshed, it is encrypted with the new shared secret.
If the shared secret is changed more frequently than one-fourth the setting of the idle session timeout parameter, users may have to re-authenticate during a session. Otherwise, user are not required to re-authenticate during a session if the shared secret is changed.
You use Flush Password Policy Cache function, available through the Access System Configuration, select Common Information Configuration tab, to flush all password policies from the Access Server cache. Flushing the password policy cache removes existing password policies and adds newly configured policies.
|
Note: You must be a Master Access Administrator to flush password policy caches. You can also automatically update this cache. For more information about updates to the Access Server cache, see the Oracle Access Manager Identity and Common Administration Guide. |
Click Access System Console, select Access System Configuration, select Common Information Configuration, then click Flush Password Policy Cache.
In the next screen, select the name of the policy you want to flush from the cache.
Click Flush Cache, and click OK to confirm your decision.
Click Flush Redirect URL, if you have configured redirect URLs, and click OK.
You use the Diagnostics on Access System Console, System Management page to run diagnostics on all the Access Servers in your Oracle Access Manager system or selected servers.
To run diagnostics for Access Servers
From the Access System Console, select System Management, then click Diagnostics.
You are asked to select the Access Servers on which you would like to run diagnostics
Select the option you want:
All Access Servers: Select All Access Servers, then click the Go button.
Specific Access: Servers Hold down the Control key, then click the names of the servers whose details you want, then click the Go button.
You use the Manage Reports function on the Access System Console, System Management page to manage user access privilege reports.
Each Access Server can collect audit information about the resource requests it handles. The list of existing reports is visible from the Manage Reports page. In addition, you can perform the following operations:
For more information on auditing and reports, see the Oracle Access Manager Identity and Common Administration Guide.
You can create user access privilege reports that verify whether specific users have access to specific resources at specific times. Explanations to help you complete these fields appear in the following procedure.
To add a user access privilege report
From the Access System Console, select System Management, then click Manage Reports.
On the Manage User Access Privilege Reports page, click the Add button.
Complete the information as follows:
Report Name: Choose a self-explanatory name for the audit report.
Description: If you wish, you may describe the report.
Access Server: Name of the Access Server that will collect the information for the report.
Results Storage: Indicate whether the audit data should go to a disk file or a database.
Store in File: Check the box beside this option, then specify the fully-qualified path and file name in the Name of File field.
Store in Database: See the Oracle Access Manager Identity and Common Administration Guide for specific Oracle Access Manager configuration details and the Oracle Access Manager Installation Guide for information on database support.
List of Resources: Click the Add button beside this option to display the Add Resource Rule page, as shown in the following screen shot.
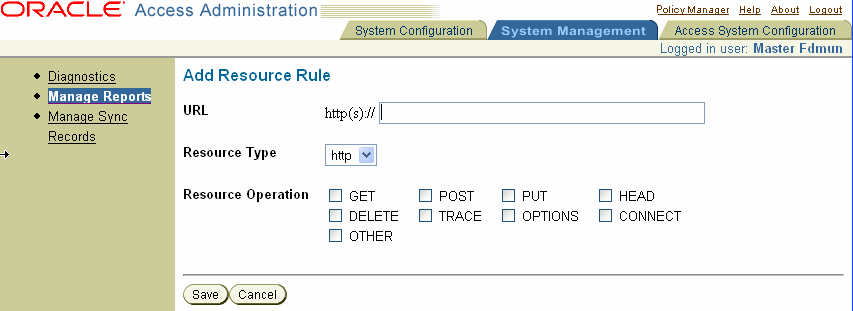
|
Note: You may add multiple resources to a report. Access information on each resource will be returned in the report. |
On the Add Resource Rule page, complete the rule by specifying the following, then click Save to return to the Add New Report page:
URL: The URL of a target resource you want to add to the report.
Resource Type: Supported choices are HTTP and EJB.
Resource Operation: Check boxes appear beside operations you can include in the report. Oracle Access Manager will determine which are permitted against the specified resources. for the specified users. at the specified time.
On the Add New Report page, continue specifying the following information:
From this IP Address: Optional. The IP address of the machine hosting the client browser whose access you want to test. This parameter is optional.
Date/Time of Access: Select a button to determine when a specific resource will be available to the users specified by the current report:
Any: Oracle Access Manager will determine if there is at least some point in time when the resource is available.
Specific date and time: Indicates you want to identify a specific point in time so that Oracle Access Manager can determine if access is permitted at that particular moment.
Check Access for the following users: Specify whether to check the access for all users in the directory or only those you designate.
selected users: Enables you to use the Selector page to locate and add specific users. Choose selected users, click the Select User button, specify your search criteria, then add specific users.
all users: Indicates you want to check the access of all users in the directory.
Click Save on the Add Reports page to save the specifications for the report and display the name you specified as a link on the Manage User Access Privilege Reports page.
From the Manage User Access Privilege Reports page (Access System Console, select System Management, then click Manage Reports), you can perform a number of operations:
Add: Create a new report as described in "Adding a Report".
Delete: Check the box beside the report name on the Manage User Access Privilege Reports page, then click the Delete button to remove the report. Confirm that you want to delete the report when asked.
|
Note: To delete or execute multiple reports simultaneously, check all the boxes on which to operate, then click the appropriate button. |
Execute: Check the box beside the report name on the Manage User Access Privilege Reports page, then click the Execute button. Confirm that you want to execute the report when asked.
Refresh: Update the list of reports on the Manage User Access Privilege Reports page by clicking the Refresh button.
Modify: Click a link on the Manage User Access Privilege Reports page to display the Manage Existing Report page, then change the parameters for the existing static audit report. See "Adding a Report" for details about each option.
The Policy Manager creates synchronization records, which are stored on the directory server. Over time, these records accumulate. You can manage the space these records consume on the directory server by periodically archiving or purging all the records prior to a specified date.
The archive file is typically named nnn.ldif, where nnn is a string of numbers representing both the moment at which the file was created and the cut-off time for archiving or purging records. All records created prior to the cut-off time will be archived or purged.
By default, the archived file is stored in:
PolicyManager_install_dir\access\oblix\data\common
where PolicyManager_install_dir represents the directory where you installed the Policy Manager.
From the Access System Console, click System Management, then click Manage Sync Records.
On the Manage Sync Records page, use the drop down lists to specify the Date of sync records generated.
Click the Archive Sync Records button.
When asked if you really want to archive the records, click OK to execute the action (or Cancel to revoke the operation).
Record the location when you are presented with a message like the following:
Successfully archived 210 sync records generated before the selected date to file /export/home/COREid1014/webcomponent/access/oblix/data/common/syncrecords109099 8000.20040729.040844.ldif.
From the Access System Console, click System Management, then click Manage Sync Records.
On the Manage Sync Records page, use the drop down lists to specify the Date of sync records generated.
Click the Purge Sync Records button.
When asked if you really want to purge the records, click OK to execute the action (or Cancel to revoke the operation).
For more information about reports, see the Oracle Access Manager Identity and Common Administration Guide.