| Oracle® Identity and Access Management Introduction 10g (10.1.4.0.1) Part Number B31291-01 |
|
|
View PDF |
| Oracle® Identity and Access Management Introduction 10g (10.1.4.0.1) Part Number B31291-01 |
|
|
View PDF |
Oracle Access Manager (formerly known as Oblix NetPoint and Oracle COREid) provides a full range of identity administration and security functions. These functions include Web single sign-on, user self-service and self-registration, workflow, auditing and access reporting, policy management, dynamic group management, and delegated administration.
Oracle Access Manager consists of two systems:
Access System—You use the Access System to configure single- and multi-domain single sign-on to Web- and non-Web-based applications, Web pages, and other resources. You can configure user authentication schemes that require a user name and password, a certificate, or you can design a custom login form. Users are authorized based on schemes that you define. The authorization schemes are based on criteria such as header variables, the time, or data retrieved from external sources. You can use external authorization plug-ins in an authorization scheme. You can configure audits and reports of authentication and authorization activity. Third-party integrations enable use of smart cards and other technologies.
Identity System—You use the Identity System to enable users to manage their profiles, perform self-registration, subscribe to and manage group memberships, and manage other organizational assets. The Identity System contains functionality for creating and managing password policies including self-service for lost password retrieval. You can configure delegated administration to enable management of millions of users. Workflow functionality enables Identity System functions to be routed for additional information and approval, and workflow steps can send calls to external applications.
This chapter provides an overview of Oracle Access Manager 10g (10.1.4.0.1) and includes the following topics:
Oracle Access Manager enables you to change from a perimeter defense model, in which you unilaterally block outside access to your resources, to a security model based on business rules. You can securely provide business systems and data to employees, customers, and suppliers.
Oracle Access Manager helps your enterprise facilitate delivery of corporate functions to extended groups of employees, customers, partners, and suppliers; maintain a high level of security across applications; enable users and business partners to access the information they need.
For example, suppose that your internal users, your suppliers, and your customers require access to unique data sets. In addition, suppose that you also have common data that everyone should see. Using Oracle Access Manager, your identity-based policies can provide the right levels of access to each group while ensuring that everyone can securely access only the data that they need and that they have the right to access.
Using Oracle Access Manager, you can manage a corporate portal that is open to external business partners. For instance, for a portal that allows customers to order manufacturing materials and equipment, all applications exposed through the portal are protected with one platform (Oracle Access Manager) which grants access rights. Administration of the access policies protecting these resources can be delegated throughout the corporation so that business units, rather than the IT department, make decisions about the customers, suppliers, and partners who are to be given access rights. This is possible even if you need to manage millions of people, including your customers, employees, and suppliers.
Using Oracle Access Manager, you can also grant different types of privileges to different classes of users. For instance, a health-care organization can manage its data so that different groups can view different kinds of data, as follows:
Health-care plan members can view their health-care information.
Companies providing health-care services to their employees can manage their health-care plans.
Doctors and hospitals can view patient information.
An organization can use Oracle Access Manager to aggregate application accounts. For example, financial institutions can configure self-service portals to allow their customers to access different accounts from a single login, including online banking, mortgage information, and insurance.
The Access System enables you to centralize access policy creation while decentralizing policy management and enforcement. The following types of resources can be protected using the Access System:
HTTP resources including directories, pages, Web-based applications, query strings, and so forth
J2EE application server resources, including Java server pages (JSPs), servlets, and enterprise Java beans (EJBs)
Other resources, including standalone programs (Java, C, C++), ERP applications, CRM applications, and the like
This section outlines key access-control features.
Authentication Services—Provide a generalized means to authenticate users and systems attempting to access resources protected by Oracle Access Manager. Authentication services support both the basic username and password authentication method as well as stronger methods such as digital certificates or SecurID cards.
You can either use standard authentication plug-ins or create your own custom plug-ins using the Authentication Plug-In API. Each custom plug-in implements the authentication interface to pass relevant information between the Access Server and the plug-in. Methods within the interface parse the data.
Once a user is authenticated, Oracle Access Manager creates a single-sign-on (SSO) session for the client that frees the user from having to sign on again to access other resources or applications.
Authorization Services—Deliver centralized, consistent management of policies across applications, while providing users granular access to Web-based content and resources. You can secure sensitive information while helping ensure that users and systems have the easy access they need.
Authorization is governed by a policy domain that includes an authorization expression among a set of default rules that specify how resources for this domain are protected. You can use the authorization scheme provided by the Access System or configure one or more custom schemes that include custom plug-ins created using the Authorization Plug-In API. See also Oracle Access Manager Developer Guide.
Once authorization is confirmed, the user is granted access to the resource.
Auditing Services—Provide flexible and detailed reporting, auditing, and logging of events in Oracle Access Manager with out-of-the-box reports for Crystal Reports. The auditing and log files enable you to perform threat and intrusion detection, security monitoring, and business-level reporting by integrating with third-party products.
Personalization Services—Enable personalization for other applications through HTTP header variables and redirection URLs. When Oracle Access Manager authenticates or authorizes user requests, the URL it returns can contain HTTP header variables which in turn can contain any user data stored under the authenticated user's ID in the directory.
The downstream application can decode this information and use it to personalize the user experience. You can include a redirection URL in the URL returned by Oracle Access Manager, which may take the user to another Web page tailored to the identity of the user.
Single Sign-On—Enables users and groups of users to access multiple applications after a single login and authentication, which improves the user experience by eliminating multiple logins. Users needing access to single-domain servers store a generated cookie for subsequent requests to the Web site. Users needing access to multi-domain servers store a cookie generated by a central Web login server; this occurs transparently for each accessed server within the associated Web system.
Delegated Access Administration—Enables distribution of administrative tasks. When the responsibility for managing the Access System falls on a few people, you may want these people to appoint others to share the work. For example, you can delegate the ability to modify the revoked user list and to add, modify, or delete configuration details and schemes.
For more information and a sample Access System installation, see "How the Oracle Access Manager Access System Works".
This section includes the following topics:
Figure 6-1 shows the basic components of the Access System. The WebGate communicates with the Access Server; the Access Server communicates with the directory server; the Policy Manager communicates with the directory server through a WebPass.
The Oracle Access Protocol (formerly known as the NetPoint or COREid Access Protocol) enables communication between Access System components during user authentication and authorization. Transport security between Web clients (Policy Manager and WebPass; Access Server and WebGate) can be Open, Simple (Oracle-provided), and Cert (third-party CA). In both Simple and Cert mode, Oracle Access Manager components use X.509 digital certificates only.
Transport security between Access Servers and the directory server (and Policy Managers and directory server) may be either open or SSL-enabled. The same mode must be used between all Policy Managers and the directory server.
During Policy Manager installation and setup, the LDAP directory server is updated to include policy data (access policy data). All access policy definitions defined in the Policy Manager are stored in the directory server.
This discussion introduces the Policy Manager, Access System Console, and functions available with each.
Policy Manager—The Policy Manager provides the login interface for the Access System, communicates with the directory server to write policy data, and communicates with the Access Server over the OAP to update the Access Server when you make certain policy modifications.
Master Access Administrators and Delegated Access Administrators use the Policy Manager to:
Create and manage policy domains that consist of:
Resource types to protect
Authentication, authorization, and audit rules
Policies (exceptions)
Administrative rights
Add resources to policy domains
Test access policy enforcement
The Policy Manager must be installed on a machine hosting a Web server instance with a WebPass (installed at the same directory level as the Policy Manager). Oracle recommends that you install multiple Policy Managers for fault tolerance. For details about installing the Policy Manager, see the Oracle Access Manager Installation Guide.
Access System Console—Included with the Policy Manager. Provides a login interface to the Access System Console and the functions that allow any Master Administrator, Master Access Administrator, and Delegated Access Administrator to use the following functional options:
System Configuration—Enables a Master Oracle Access Manager Administrator to assign users to be a Master Access Administrator, as well as add or remove Delegated Access Administrators and their rights. Responsibilities of a Master Access Administrator include defining resource types, policy domains, and authentication and authorization schemes.
From the System Configuration tab, administrators can also view and change server settings from this tab. For example, you can specify email addresses for bug reports, user feedback, and the company Web master. You can change the default logout URL for single sign-on, configure directory server settings, and view cache settings.
System Management—Enables a Master Administrator to manage:
Diagnostics—Show Access Server details, including connection information.
Manage Reports—Create, view, or modify user access privilege reports.
Manage Sync Records—Archive or purge synchronization records generated by the Policy Manager before a given date. To help you manage the space these records consume on the directory server, it is a good idea to periodically archive or purge all the records before a specified date.
Access System Configuration—Enables a Master Access Administrator or Delegated Access Administrators to complete the following tasks:
View, add, modify, and delete AccessGates, Access Servers, Access Server clusters, Host Identifiers
View and modify authentication and authorization parameters; Web resource user rights; and common information
Configure common information, including:
Shared Secret: Generate a cryptographic key that encrypts cookies sent from an AccessGate or WebGate to a browser.
Master Audit Rule: Create the default Master Audit Rule for this installation.
Resource type Definitions: Define and manage resource types.Flush Password Policy Cache: Select a password policy and flush all associated caches or select a Lost Password Management policy and flush all associated caches.Duplicate Actions: Select a policy for handling Duplicate Action Headers
The Access Server plays a key role in authentication and authorization:
Authentication involves determining what authentication method is required for a resource and gathering credentials from the directory server, then returning an HTTP response based on the results of credential validation to the access client (WebGate or AccessGate).
Authorization involves gathering access information and granting access based on a policy domain stored in the directory and the identity established during authentication.
To perform these operations, you may have one or more standalone Access Server instances that communicate with both the directory server and WebGate. Before you can install an Access Server instance, you must define it in the Access System Console.
|
Note: Oracle recommends that you install multiple Access Servers for failover and load balancing. |
Process overview: Access Server functions
Receives requests from an access client (WebGate or AccessGate)
Queries authentication, authorization, and auditing rules in the directory server to determine whether:
The resource is protected (and if so, how)
The user is already authenticated (if the user is not yet authenticated, a challenge is provided)
The user credentials are valid
The user is authorized for the requested resource, and under what conditions
Responds to the access client as follows:
Sends the authentication scheme
Validates credentials
Authorizes the user
Audits
Manages the session, by:
Helping the WebGate terminate user sessions
Re-authenticating when there is a time out
Tracking user activity during a session
Setting session timeouts for users
Throughout Oracle Access Manager manuals, the terms AccessGate and WebGate may be used interchangeably. However, there are differences worth noting:
A WebGate is a Web server plug-in access client that intercepts HTTP requests for Web resources and forwards them to the Access Server for authentication and authorization. A WebGate is shipped out-of-the-box with Oracle Access Manager.
An AccessGate is a custom access client that is specifically developed using the Software Developer Kit (SDK) and Access Manager APIs, either by you or by Oracle. An AccessGate is a form of access client that processes requests for Web and non-Web resources (non-HTTP) from users or applications.
A WebGate intercepts requests for resources from users or applications and forwards requests to the Access Server for authentication and authorization. See "Access System Operation" for more information.
Before you can install a WebGate, you must define it in the Access System Console and associate it with an Access Server or cluster of Access Servers. For details, see Oracle Access Manager Installation Guide.
The following description explains how Access System components work in concert during authentication and authorization. See also Figure 6-2.
Process overview: When a user requests access
The WebGate intercepts the request.
Servers that can be protected include Web servers, application servers, and FTP servers (using the Access Manager SDK), among others.
The WebGate forwards the request to the Access Server to determine whether the resource is protected, how, and if the user is authenticated (if not, there is a challenge).
The Access Server checks the directory server for credentials such as a user ID and password, sends the information back to WebGate, and generates an encrypted cookie to authenticate the user.
The Access Server authenticates the user with a customer-specified authentication method to determine the identity, leveraging information stored in the directory server. Oracle Access Manager authentication supports any third-party authentication method as well as different authentication levels. Resources with varying degrees of sensitivity can be protected by requiring higher levels of authentication that correspond to more stringent authentication methods.
Following authentication, the WebGate prompts the Access Server to look up the appropriate security policies, compare them to the user's identity, and determine the user's level of authorization.
If the access policy is valid, the user is allowed to access the desired content or applications.
If the policy is false, the user is denied access and redirected to another URL determined by the organization's administrator.
Figure 6-2 Basic Access System Operations
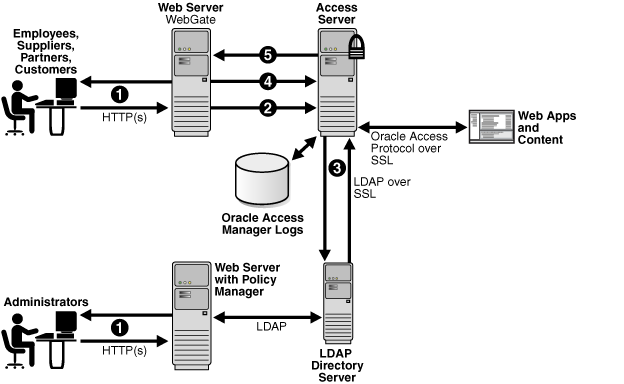
As mentioned earlier, the Policy Manager provides the login interface for the Access System, communicates with the directory server to write policy data, and communicates with the Access Server over the OAP to update the Access Server when you make certain policy modifications. The WebPass intercepts and forwards administrator requests for the Policy Manager and Access System Console.
Administrators can build password management and other functions on top of the Oracle Access Manager identity management system. You can integrate other applications with the primary Identity System components using a single identity management system so that access cards, computer accounts, and payroll functions can all be modified from one identity change function when an employee leaves an organization. Customization and XML-based integration features are included.
End users can search for and view other users and groups, depending on the rights granted to them by an administrator; modify personal information such as phone numbers and passwords; and display organizational information such as floor plans and asset lists.
Identity System administration features include:
Centralized User, Group, and Organization (object) Management—Enables you to provide different access policies for different people and groups and to manage organizational entities, such as assets and maps. Information in the Oracle Access Manager Identity System can then be leveraged by the Oracle Access Manager Access System to manage access privileges based on user attributes, group membership, or association with an organizational entity.
Dynamic Role-Based Identity Administration—Provides security guided by user identity-based access privileges. For example, a role may include all users or all managers or direct-reports only, and so on.
A Customizable Multi-Step Identity Workflow Engine—Enables you to map and automate business processes, policies, and approvals relating to identity data. For example, you can model your business processes in the Identity System using workflows to:
Create, delete, and modify users, groups, and organizations
Implement self-registration of users and organizations
Subscribe and unsubscribe to groups
Multi-Level Delegation of Identity Administration—Enables you to scale up to millions of users by delegating identity administration activities. Administrators can delegate all or some of the rights they have been granted, and they can choose whether or not to allow their delegates to pass these rights on to others. The tasks that are delegated are specific to the right, the target, and the tree path.
Self-Service—Enables you to implement a secure self-service model for organizational functions such as password change. Users with self-service permissions can manage their own information without the use of a workflow.
Self-Registration—Provides limited access to your system through the initiation and processing of a self-registration workflow.
For example, you can set up a self-registration workflow such that when a user self-registers, the registration request is forwarded to appropriate people for approval. Upon approval, the user is immediately and automatically granted access to all appropriate resources based on his or her identity attributes.
Data Management Layer—Supports multiple LDAP environments, RDBMS databases, and split-directory profiles. This feature is also known as Data Anywhere and is available with Oracle Virtual Directory. Data Anywhere aggregates and consolidates data from RDBMS and LDAP directories into a virtual LDAP tree. The tree can be managed by the Oracle Access Manager Identity System and used to support authentication and authorization with the Oracle Access Manager Access System. For complete details, see the Oracle Access Manager Identity and Common Administration Guide.
Password Management Services—Enables you to specify multiple password policies, constraints on password composition, a configurable password validity period and notification, forced password change, lost password management setup, and password creation/change rules.
User Interface Customization—Provides several methods you can use to change the appearance of Oracle Access Manager applications and control operations, and connect CGI files or JavaScripts to Oracle Access Manager screens. For details, see the Oracle Access Manager Customization Guide.
Extensive APIs for Identity Integration—Enables you to gain access and interact with Oracle Access Manager without using a browser, and implement functions and executables triggered by events within Oracle Access Manager. For details, see the Oracle Access Manager Customization Guide.
Unless otherwise indicated, you can find more information about these features and how to configure them in the Oracle Access Manager Identity and Common Administration Guide. For a simple installation diagram, see the next discussion: "How the Oracle Access Manager Identity System Works".
The Oracle Access Manager Identity System provides the infrastructure needed for other applications and systems to leverage user identity and policy information across the enterprise. This eliminates the need to create and manage separate user identity repositories for each application.
This section contains the following topics:
Figure 6-3 illustrates the basic Identity System components in a simple environment, as well as transport security between components over the Oracle Identity Protocol (formerly known as the NetPoint or COREid Identity Protocol). The end users and Administrators are separated from components by a firewall. The Web server with WebPass installed resides in the DMZ. The Identity Server and directory server reside behind the second firewall.
The Oracle Identity Protocol facilitates communication between Identity Servers and associated WebPass instances. Transport security between Oracle Access Manager Web clients (WebPass and Identity Server) may be specified as Open, Simple (Oracle-provided), or Cert (third-party CA). In both Simple and Cert mode, Oracle Access Manager components use X.509 digital certificates only. Transport security between Identity Servers and the directory server may be either open or SSL-enabled.
During Oracle Access Manager installation and setup, the LDAP directory server is updated to include the Oracle Access Manager schema with object classes and attributes for the entire system. Oracle Access Manager enables you to store various types of data on the same directory server type, or separate directory server types. Data types include:
User Data—User directory entries managed by Oracle Access Manager
Configuration Data—Oracle Access Manager configuration details stored in the directory and managed by the Identity System
Policy Data—Access policy definitions defined in the Policy Manager are stored in the directory server
During Oracle Access Manager installation and setup, the Master Oracle Access Manager Administrator (Master Administrator) is assigned. The Master Administrator is a super user who is empowered to configure the deployment and assign administrative tasks. Using the System Console, the Master Administrator can create additional Master Administrators, as well as Master Identity Administrators and Master Access Administrators. For example, a Master Identity Administrator can delegate authority to other administrators, which enables management of millions of users.
In addition to managing identity information, you can use the Identity System to manage access privileges for a user based on a specific user attribute, membership in a group, or association with an organization. Administrators can link privileges together into a workflow so that, for example, when a user self-registers, the registration request is forwarded to appropriate people for signoff.
Your Oracle Access Manager installation must include at least one Identity Server. You use the Identity Server to manage identity information about users, groups, organizations, and other objects. Your installation may include one or more Identity Server instances. The Identity Server performs three main functions:
Reads and writes to your LDAP directory server across a network connection
Stores user information on a directory server and keeps the directory current
Processes all requests related to user, group, and organization identification
Each instance of the Identity Server communicates with a Web server through a WebPass plug-in, as discussed in "WebPass".
The Identity Server provides the following Identity applications, which are accessed through a Web-based interface. All have a reporting capability:
User Manager—Enables complete management of all identity information related to individual network users.
The User Manager enables administrators to add, modify, deactivate, and delete user identities. In addition, the User Manager enables administrators to provide users with access privileges based on their directory profiles (and substitute rights), as well as view and monitor requests.
Typically, end users can view other users and modify their own identity information. The users that a person can view and the identity information that someone can modify depends on the privileges granted by the Master Administrator.
Group Manager—Enables authorized personnel to create, manage and delete static, dynamic, or nested groups or to delegate group administration.
Administrators can create or delete groups, and enable users to subscribe or unsubscribe from groups.
End users can view groups and subscribe to membership in a group. The groups that a person can view, and subscription rights, are granted by a Master Administrator.
Organization Manager—Helps you manage system rules, access privileges, and workflows to manage ongoing changes for entire organizations.
Administrators can create and delete organizations and other objects (such as floor plans and assets) that do not belong in the User Manager or Group Manager.
End users can view organizational entities. The organizational entities that a person can view depend upon the rights granted by a Master Administrator.
Identity System Console—Provides Web-based administration and configuration that is used to create administrators and assign the right to delegate administrative tasks. Tabs in the Identity System Console provide access to specific identity administration functions.
A WebPass is an Oracle Access Manager Web server plug-in that passes information back and forth between a Web server and the Identity Server. Depending upon its configuration, the Identity Server processes the request either as an XML or HTML file.
A WebPass can communicate with multiple Identity Servers. Each Web server instance that communicates with the Identity Server must be configured with a WebPass. In a Oracle Access Manager installation:
At least one WebPass must be installed on a Web server and configured to communicate with at least one Identity Server.
A WebPass is required on each machine hosting an Oracle Access Manager Policy Manager.
After installing an Identity Server and a WebPass, you must complete an initial Identity System setup process so the Identity Server and WebPass can communicate.
Process overview: WebPass functions
The WebPass receives the user request and maps the URL to a message format.
The WebPass forwards the request to an Identity Server.
The WebPass receives information from the Identity Server and returns it to the user's browser.