| Oracle® Identity Management Integration Guide 10g (10.1.4.2) Part Number E10528-01 |
|
|
View PDF |
| Oracle® Identity Management Integration Guide 10g (10.1.4.2) Part Number E10528-01 |
|
|
View PDF |
As of 10g (10.1.4.2), Oracle offers two complementary provisioning products, optimized for different use cases:
Oracle Identity Manager, formerly known as Oracle Xellerate Identity Provisioning, is an enterprise provisioning platform designed to manage complex environments with highly heterogeneous technologies that can include directories, databases, mainframes, proprietary technologies, and flat files. Oracle Identity Manager offers full-functioned workflow and policy capabilities along with a rich set of audit and compliance features.
Oracle Directory Integration Platform, a component of the Identity Management infrastructure, is a meta-directory technology designed to perform directory synchronization as well as provisioning tasks in a directory-centric environment. Oracle Directory Integration Platform is designed to manage a more homogeneous environment consisting of directories and compatible Oracle products. Oracle Directory Integration Platform performs provisioning tasks by using data synchronization and offers a small deployment footprint when workflow and a full feature policy engine are not required.
This chapter discusses Oracle Directory Integration Platform Provisioning. It contains these sections:
See Also:
The chapter on developing provisioning-integrated applications in Oracle Identity Management Application Developer's Guide
Provisioning refers to the process of providing users, groups, and other objects with access to applications and other resources that may be available in an enterprise environment. A provisioning-integrated application refers to an application that has registered for provisioning events and registered a provisioning-integration profile in Oracle Internet Directory. At times, you may want to synchronize all user entries in an application-specific directory with those in Oracle Internet Directory, but provision a particular application to receive notification about only some of them. For example, the directory for Oracle Human Resources typically contains data for all employees in an enterprise, and you would probably want to synchronize all of that data with Oracle Internet Directory. However, you might want to provision another application, such as Oracle Email, to be notified only when members join or leave a particular group.
Before a user account can be provisioned for applications in an Oracle Identity Management deployment, it must first be created in Oracle Internet Directory. User accounts can be created in Oracle Internet Directory with any of the following tools or methods:
Oracle Internet Directory Provisioning Console
Directory Integration Assistant's bulkprov operation
Synchronization with third-party directories
Command-line LDAP tools
The Oracle Directory Integration Platform Service can be invoked for any user entries, regardless of how they were created in Oracle Internet Directory. However, creating a user entry in Oracle Internet Directory does not necessarily mean that the user entry will have access to all applications in the Oracle Identity Management environment. The user account must be manually provisioned by an administrator or automatically provisioned according to an application's provisioning policies. The default provisioning policy of an application can be one of the following:
Provision all users
Do not provision users
Provision users after evaluating a provisioning policy
Provisioning policies are entirely dependent on the needs and requirements within each enterprise environment. For example, an organization may choose to provision all users with access to an e-mail application, but may restrict the users that are provisioned to access a human resources application.
The Oracle Directory Integration Platform Service consists of the following components:
The Oracle directory integration server.
The Oracle Internet Directory Provisioning Console, a ready-to-use, standalone application created by using Oracle Delegated Administration Services. The Provisioning Console works closely with the Oracle Directory Integration Platform Administration tools.
A provisioning integration profile for each provisioning-integrated application in which you want to provision users. You create a provisioning-integration profile by using the Provisioning Subscription Tool.
See Also:
Theoidprovtool section in the Oracle Directory Integration Platform tools chapter of the Oracle Identity Management User Reference for information about the Provisioning Subscription ToolThis section explains how applications are provisioned with Oracle Directory Integration Platform Provisioning. It contains these topics:
A provisioning-integrated application can maintain user information in Oracle Internet Directory or a third-party repository. Applications that maintain user information in Oracle Internet Directory can use the Data Access Java plug-in to create, modify, and delete user entries whenever the change occurs in Oracle Internet Directory.
See Also:
Oracle Identity Management Application Developer's Guide for more information about the Data Access Java plug-inThe Data Access Java plug-in can be invoked directly from Oracle Identity Management, including the Provisioning Console, bulk provisioning with the Directory Integration Assistant (dipassistant), and command-line LDAP tools. For this reason, applications that can be provisioned with the Data Access Java plug-in are provisioned synchronously; no separate provisioning event needs to be sent to the application from the Oracle directory integration server. The Data Access Java plug-in returns either SUCCESS or FAILURE to the Oracle directory integration server. If an execution status of SUCCESS is returned for the Data Access Java plug-in, then a provisioning status is also returned, which is recorded in the user's provisioning status attribute in Oracle Internet Directory for the specific provisioning-integrated application. If the status of FAILURE is returned for new user provisioning requests, then the user's provisioning status is assigned a value of PROVISIONING_FAILURE. See "Provisioning Status in Oracle Internet Directory" for a list of provisioning statuses.
Figure 12-1 illustrates the process of how an application is synchronously provisioned from the Provisioning Console, bulk provisioning with the Directory Integration Assistant (dipassistant), and from third-party directories.
Figure 12-1 Synchronous Provisioning Process
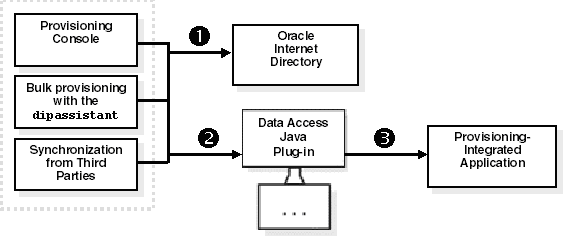
As illustrated in Figure 12-1, synchronous provisioning with the Oracle Directory Integration Platform Service from the Provisioning Console, bulk provisioning with the Directory Integration Assistant (dipassistant), and from third-party directories follows this process:
A new user entry is created in Oracle Internet Directory from one of the following sources:
Oracle Internet Directory Provisioning Console
Bulk provisioning with the Directory Integration Assistant
Synchronization with third-party directories
The Oracle Identity Management component that created the new user entry invokes the Data Access Java plug-in.
The Data Access Java plug-in provisions the new user account in the application.
Figure 12-2 illustrates the process of how an application is synchronously provisioned using command-line LDAP tools.
Figure 12-2 Synchronous Provisioning from Command-Line LDAP Tools
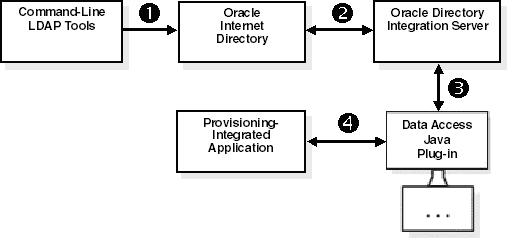
As illustrated in Figure 12-2, synchronous provisioning from command-line LDAP tools follows this process:
A command-line LDAP tool creates a new user entry in Oracle Internet Directory.
At the next scheduled synchronization interval, the Oracle directory integration server identifies new user entries in Oracle Internet Directory that require provisioning.
The Oracle directory integration server invokes the Data Access Java plug-in.
The Data Access Java plug-in provisions the new user accounts in the application.
The Oracle directory integration server propagates PL/SQL events to a provisioning-integrated application, which then executes a PL/SQL plug-in to process the events. Execution of a PL/SQL plug-in occurs within the application repository and not within the address space of any Oracle Identity Management component. Because, provisioning is handled by a PL/SQL plug-in and not by any component of Oracle Identity Management, provisioning-integrated applications that implement a PL/SQL plug-in are provisioned asynchronously. The PL/SQL plug-in returns the status of SUCCESS or FAILURE to the Oracle directory integration server. If the status of SUCCESS is returned for the PL/SQL plug-in, then a provisioning status is also returned, which is recorded in the user's provisioning status attribute in Oracle Internet Directory for the specific provisioning-integrated application. If the status of FAILURE is returned for new user provisioning requests, then the user's provisioning status is assigned a value of PROVISIONING_FAILURE. See "Provisioning Status in Oracle Internet Directory" for a list of provisioning statuses.
Figure 12-3 illustrates the process of how an application is asynchronously provisioned from the Provisioning Console, by using bulk provisioning with the Directory Integration Assistant (dipassistant), or from third-party directories.
Figure 12-3 Asynchronous Provisioning Process
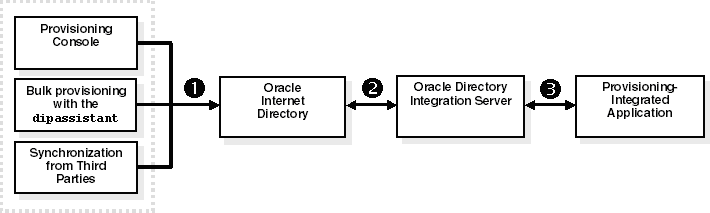
As illustrated in Figure 12-3, asynchronous provisioning from the Provisioning Console, bulk provisioning with the Directory Integration Assistant (dipassistant), and third-party directories follows this process:
A new user entry and an associated entry containing application-specific user preferences are created in Oracle Internet Directory from one of the following sources:
Oracle Internet Directory Provisioning Console
Bulk provisioning with the Directory Integration Assistant
Synchronization with third-party directories
At the next scheduled synchronization interval, the Oracle directory integration server identifies new user entries in Oracle Internet Directory that require provisioning.
Provisioning events are sent from the Oracle directory integration server to the PL/SQL plug-in.
Figure 12-4 illustrates the process of how an application is asynchronously provisioned using command-line LDAP tools.
Figure 12-4 Asynchronous Provisioning using Command-Line LDAP Tools
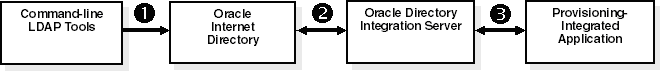
As illustrated in Figure 12-4, asynchronous provisioning using command-line LDAP tools follows this process:
A new user entry is created in Oracle Internet Directory using a command-line LDAP tool.
At the next scheduled synchronization interval, the Oracle directory integration server identifies new users entries in Oracle Internet Directory that require provisioning, and creates an associated entry containing application-specific user preferences.
Provisioning events are sent from the Oracle directory integration server to the PL/SQL plug-in.
Regardless of whether it is provisioned synchronously or asynchronously, an application can invoke the Pre-Data Entry and Post-Data Entry plug-ins to enhance provisioning intelligence and implement business policies. Both plug-ins are invoked by Oracle Identity Management components such as the Oracle Internet Directory Provisioning Console and bulk provisioning with the Directory Integration Assistant (dipassistant).
The Pre-Data Entry plug-in populates fields according to provisioning policies. The primary purpose of this plug-in is to determine whether a user should be provisioned in an application. For example, if an organization has a a policy where only managers are provisioned for a financial application, the Pre-Data Entry plug-in can be used to identify which user entries to provision. Common user attributes are already populated when this plug-in is invoked, so it should have adequate information to make provisioning decisions.
The Post-Data Entry plug-in primarily validates data entered by users for common attributes and application-specific attributes. The validation for the plug-in must be successful for provisioning to continue.
Figure 12-5 illustrates the provisioning data flow using the Pre-Data Entry and Post-Data Entry plug-ins.
As illustrated in Figure 12-5, the provisioning data flow follows this process:
Base user information is created.
The Pre-Data Entry plug-in is invoked, which populates fields according to policies.
The Post-Data Entry plug-in is invoked, which validates data entered by the user.
Depending on the provisioning approach, either asynchronous or synchronous provisioning procedures are invoked.
If provisioning is performed with the Provisioning Console, then after the Pre-Data Entry Plug-in is invoked, but before the Post-Data Entry plug-in is invoked, an administrator can modify the application attributes.
This section describes the procedures for provisioning users in Oracle Identity Management. It contains these topics:
You can use the Provisioning Console to centrally manage user provisioning and deprovisioning of one or more users simultaneously. The console includes a wizard-based interface for creating, modifying, and deleting individual users, and for selectively provision and deprovision users for any provisioning-integrated applications. The Provisioning Console also supports bulk user creation, modification, and deletion of users from an LDIF file. See "Bulk Provisioning" for more information.
When Oracle Internet Directory is used as a central repository and enterprise user entries are synchronized from third-party directories to Oracle Internet Directory, each user identity is automatically provisioned according to the default provisioning policy of each provisioning-integrated application.
Any tools developed by Oracle or third-party vendors that use standard command-line LDAP syntax can create user entries in Oracle Internet Directory. As with user entries that are synchronized from external sources, any user entries created with command-line LDAP tools or any other means are provisioned according to the default provisioning policies for each provisioning-integrated application.
You can use the Provisioning Console or the Directory Integration Assistant (dipassistant) to create and provision user entries by providing an LDAP Data Interchange Format (LDIF) file containing user data. The LDIF file should contain only LDAP-specific attributes. When user entries in an LDIF file are created in Oracle Internet Directory, each entry is provisioned according to the default provisioning policy of each provisioning-integrated application.
On-demand provisioning occurs when a user accesses an application and the application has no knowledge of the user in its repository. The application determines whether to provision a user account based on its default provisioning policies. After provisioning a user account in its repository, an application will update the provisioning status of the user entry in Oracle Internet Directory.
This section discusses the organization of user profiles in Oracle Internet Directory. It contains these topics:
The Oracle Directory Integration Platform Provisioning relies on user profiles in the directory information tree (DIT) that consist of attributes containing personal information and preferences for the various applications in which the user is provisioned. These user attributes for the Oracle Directory Integration Platform Service can be categorized as follows:
Base attributes that are available for every user entry
Application-specific attributes that are only available if a user is provisioned in an application
Base user attributes primarily belong to standard LDAP object classes such as organizationalPerson and inetOrgPerson, and consist of personal details that include first name, last name, given name, e-mail address, and telephone numbers. Base user attributes also consist of Oracle application-specific attributes that belong to the orclUserV2 auxilliary class.
Oracle Internet Directory is the primary repository for both base attributes and application-specific attributes. Both types of attributes are stored in each user's profile. However, an application can cache user attributes that are updated with the provisioning event notification service.As shown in Figure 12-6, user attributes are stored in two locations within the DIT. Base user entries, which include attributes belonging to inetorgperson and orcluserv2, are stored under cn=users,Realm DN. The provisioning status of each user entry is also stored in the base user entry. Application-specific attributes reside in separate entries in the application container. The LDAP schema relating to the application-specific attribute definitions and the object classes are created during the installation or upgrade process. Application-specific attributes are qualified by an auxiliary object class, which will enable searching for the application-specific user properties of the entry. By default, application-specific entries are stored as orclOwnerGUID=GUID of the Base User under the cn=User Properties, cn=Application Type, cn=Products,cn=OracleContext, Realm DN container.Some applications manage their own application attributes and implement the Data Access Java plug-in, which is described in "Understanding Provisioning Concepts". The Oracle Directory Integration Platform Service invokes this plug-in whenever the base user attributes or application-specific attributes are modified.
Figure 12-6 Base User and Application-Specific Attributes
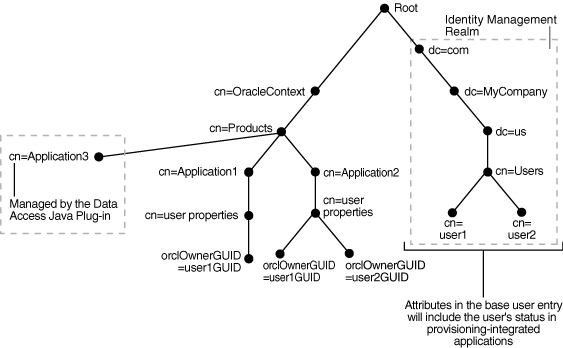
This section discusses the user provisioning statuses in Oracle Internet Directory. It contains these topics:
The Oracle Provisioning Service records a user's provisioning status in Oracle Internet Directory for each provisioning-integrated application. Provisioning status can be set by the Oracle directory integration server, with bulk provisioning using the Directory Integration Assistant (dipassistant), or by a provisioning-integrated application. Table 12-1 lists the provisioning statuses.
Table 12-1 Provisioning Statuses in Oracle Internet Directory
| Internal Status | GUI Status | Description |
|---|---|---|
|
Provisioning Statuses |
||
|
|
Pending |
Provisioning required. This status is selected by an administrator or set according to an application's provisioning policies. Note that this status determines whether a user has been provisioned. |
|
|
In Progress |
Provisioning in progress. The user can access the application when this is the current status if the application performs provisioning at scheduled intervals. The application can also provision the user on-demand. |
|
|
Successful |
Provisioning successful. This status is updated automatically by the Oracle directory integration server, with bulk provisioning using the Directory Integration Assistant ( |
|
|
Not Requested |
Provisioning not required. This status is selected by an administrator or set according to an application's provisioning policies. Note that this status determines whether a user will be provisioned. |
|
|
Failed |
Provisioning failed. This status is updated automatically by the Oracle directory integration server, with bulk provisioning using the Directory Integration Assistant ( |
|
Deprovisioning Statuses |
||
|
|
Pending de-provisioning |
Deprovisioning required. The user is still provisioned when this is the current status. |
|
|
De-provisioning In Progress |
Deprovisioning in progress. |
|
|
Successfully de-provisioned |
Deprovisioning successful. The user cannot access the application when this is the current status. |
|
|
Failed de-provisioning |
Deprovisioning failed. The user is still provisioned when this is the current status. |
|
Upgrade Statuses |
||
|
|
Pending Upgrade |
Provisioning upgrade pending. |
|
|
Upgrade In Progress |
Provisioning upgrade in progress. |
|
|
Upgrade Failed |
Provisioning upgrade failed. |
The provisioning status for each application is stored in the orclUserApplnProvStatus attribute in a user entry. This attribute is indexed in Oracle Internet Directory and is searchable. A subtyped orclUserApplnProvStatus attribute is created for each provisioning-integrated application. For example, the following statements store a user's provisioning statuses for an e-mail application and a scheduling application. The user's provisioning status for the e-mail application is PROVISIONING_SUCCESS while his or her provisioning status for the scheduling application is PROVISIONING_FAILURE.
orclUserApplnProvStatus;CORP-MAIL_E-MAIL:PROVISIONING_SUCCESS orclUserApplnProvStatus;CORP-SCHEDULE_CALENDAR:PROVISIONING_FAILURE
Additional information about a user's provisioning status in an application is stored in the orclUserApplnProvStatusDesc attribute and the provisioning failure account for each application is stored in the orclUserApplnProvFailureCount attribute. As with the orclUserApplnProvStatus attribute, separate orclUserApplnProvStatusDesc and orclUserApplnProvFailureCount attributes are created for each provisioning-integrated application. The format for the orclUserApplnProvStatusDesc attribute is the same as the orclUserApplnProvStatus attribute, except that a timestamp and descriptive information are appended to the application name and type, as follows:
orclUserApplnProvStatusDesc;CORP-MAIL_E-MAIL:20040101010101^Missing employee ID
The orclUserApplnProvStatus, orclUserApplnProvStatusDesc, and orclUserApplnProvFailureCount attributes are contained in the orclUserProvStatus object class as optional attributes.
Table 12-2 lists the valid provisioning status transitions.
Table 12-2 Valid Provisioning Status Transitions in Oracle Internet Directory
| Internal Status | GUI Status | Valid Transition From |
|---|---|---|
|
Provisioning Statuses |
||
|
|
Pending |
Initial missing state
|
|
|
In Progress |
|
|
|
Successful |
|
|
|
Not Requested |
Initial missing state |
|
|
Failed |
|
|
Deprovisioning Statuses |
||
|
|
Pending de-provisioning |
|
|
|
De-provisioning In Progress |
|
|
|
Successfully de-provisioned |
|
|
|
Failed de-provisioning |
|
Figure 12-7 illustrates the valid provisioning status transitions.
Figure 12-7 Valid Provisioning Status Transitions
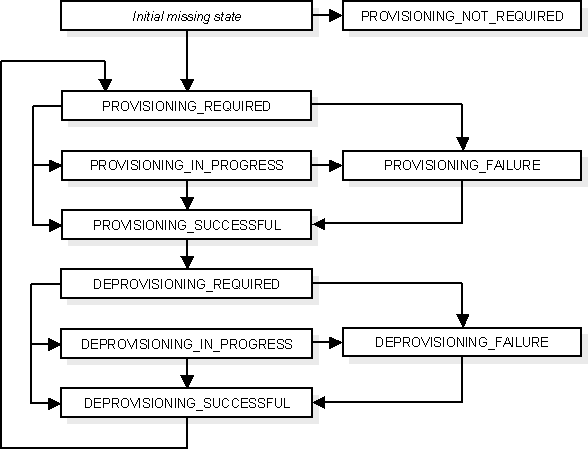
In Oracle Identity Management 10g (10.1.4.2), a user entry can be physically represented in Oracle Internet Directory by multiple LDAP entries. In addition to the base user entry, separate LDAP entries can exist for each provisioning-integrated application.
In a typical upgrade of Oracle Identity Management, multiple middle tiers are not upgraded simultaneously. This means that following an Oracle Identity Management upgrade, middle tiers from a previous version may need to run in parallel with middle tiers from the upgraded version. When a middle tier is upgraded, all of a user's application-specific data that was previously stored in the application metadata repository, will be migrated on-demand. For each user entry that is present in Oracle Internet Directory prior to the upgrade, the Oracle directory integration server will initiate a new user event and assign a provisioning status of PENDING_UPGRADE to the user entry. If a new user entry is created from an older middle tier or some unsupported route, such as an existing application using the standard LDAP SDK, the provisioning status attribute will be missing. In this case, the Oracle directory integration server also initiates a new user event and assign a provisioning status of PENDING_UPGRADE to the user entry.
Once a provisioning-integrated application receives the event, it will return a response to the Oracle directory integration platform indicating whether or not the user is provisioned. The Oracle directory integration platform then updates the provisioning status in the user entry accordingly.
If a new user entry created with the Provisioning Console or through synchronization with an external data source does not contain enough information to provision the user in a particular application, provisioning may fail. Provisioning can also fail for a variety of other reasons. The Oracle Directory Integration Platform Service identifies user provisioning failures as exceptions. Whenever an application responds to a USER_ADD event with a failure status, the Oracle directory integration server will change the user's provisioning status to PROVISIONING_FAILURE. The Oracle directory integration server will then send notifications to the applications of the failed cases also just like a new user case. This will serve as a retry for the provisioning request. The provisioning status of a user displays in the Provisioning Console. The administrator can make the necessary changes to fix the problem, and the provisioning would get retried automatically. This will result in invocation of the data access plug-in if the provisioning is synchronous. However, an event will be propagated if the provisioning is asynchronous.This sequence of steps will be retried as long as the user is not provisioned successfully.
This section discusses the flow of information and control in various provisioning scenarios. It contains these topics:
You can use the Provisioning Console to create and provision new user entries in Oracle Internet Directory. The console uses a wizard-based interface to perform the following steps:
The initial user creation screen shows a list of required base user attributes. The base user attributes are populated after the Provisioning Console invokes the Pre-Data Entry plug-in. For user creation, the plug-in processes the base user attributes and generates the application's default provisioning policy and attributes. For user modification, the Provisioning Console retrieves user information from Oracle Internet Directory, and the plug-in retrieves application information.
The next step in the wizard displays how a user will be provisioned in each application, based on the application's default provisioning policy. For user modification, this step displays one list with applications for which the user is currently provisioned and another list in which the user can be provisioned. You can select one of the following values for an application in which the user is not yet provisioned:
User Policy. The selected value for this field is based on each application's default provisioning policy. This field can display one of two values: Provision or Do Not Provision.
Override Policy to perform Provision. Selecting this option overrides the application's default policy and provisions the user.
Override Policy NOT to perform Provision. Selecting this option override the application's default policy and does not provision the user.
For applications in which the user is currently provisioned, there will be an option for deprovisioning the user.
For applications in which the user is not provisioned, the next step in the wizard displays attributes for the applications to be provisioned, with the default values returned by the Pre-Data Entry plug-in. For applications in which the user is provisioned, current application information is listed. You can make any necessary changes to the attributes in this step before clicking Next. When you click Next, the Post-Data Entry plug-in is invoked, which validates the data you entered.
The final step in the wizard enables you to review application attributes and values. Click Finish. After you click Finish, the Provisioning Console creates or updates the user information in Oracle Internet Directory, and then invokes the Data Access Java plug-in for applications that are provisioned synchronously to create or update the application
Before a user is deleted, the Provisioning Console displays a read-only page listing the base user and the application attributes. After the user confirms the deletion, the Provisioning Console deletes the base user information and any application-specific information, or invokes the Data Access Java plug-in for applications that are provisioned synchronously. For asynchronous applications, a USER_DELETE event is propagated.
The majority of deployments are expected to provision users from an external source, such a third-party enterprise user repository. In these types of deployments, the third-party repository bootstraps Oracle Internet Directory. Oracle Directory Integration Platform will provide ongoing synchronization between Oracle Internet Directory and the third-party repository. Example of third-party user repositories include Oracle Human Resources and LDAP directories such as Microsoft Active Directory and Sun Java System Directory, Novell eDirectory, and OpenLDAP.
The Oracle Directory Synchronization Service will create the user entry in Oracle Internet Directory. Because the information coming from the external source may not be sufficient to provision the user in various applications, the application defaults will be used to create the application information. User creation by the Oracle Directory Synchronization Service occurs as follows:
The Oracle Directory Synchronization Service evaluates the provisioning policies specified by the applications to determine whether the user should be provisioned in the application.
The Oracle Directory Synchronization Service evaluates any other plug-ins that the application has registered.
The Oracle Directory Integration Platform Service invokes the PL/SQL plug-in or the Data Access Java plug-in to deliver the user information to the application.
The provisioning status of the user is returned by the application using the event interfaces.
The Oracle Directory Integration Platform Service updates the provisioning status of the user for the application.
Administrative rights in Oracle Delegated Administration Services vary according to the privileges delegated to each administrator. An administrator can be granted rights to manage and provision users, manage applications, or any combination of these privileges, as described in the following scenarios:
Oracle Delegated Administration Services and Provisioning Administration Privileges
Application Administration and Oracle Delegated Administration Services Privileges
Oracle Delegated Administration Services, Provisioning, and Application Administration Privileges
The following types of provisioning information is managed in Oracle Internet Directory:
Base user information.
Application-specific information.
User provisioning status in each provisioning-integrated application; this information is stored in the base user entry but is administered separately.
Administrators and users each require the following types of privileges:
Administrators require privileges for managing base user attributes and application-specific information.
Users require privileges for managing their own base attributes and application-specific information.
User accounts with administrative privileges are represented by the group entry "cn=User Provisioning Admins,cn=Groups,cn=OracleContext". To manage application-specific information, the application must grant privileges to the "cn=User Provisioning Admins,cn=Groups,cn=OracleContext" group. If an application already defines a group with administrative privileges, then the application needs to add this group as a member of the group.
For administrators with privileges for Oracle Delegated Administration Services administration, Create, Delete, and Edit buttons are available in the Provisioning Console for performing user creation, deletion, and modification. When an administrator who only has administrative rights for Oracle Delegated Administration Services clicks one of these buttons, single-step procedures are used for performing the function.
For administrators with provisioning privileges, Create, Delete, and Edit buttons are available in the Provisioning Console for performing user creation, deletion, and modification. However, unlike the single-step procedures that occur for administrators with Oracle Delegated Administration Services privileges, wizard-based procedures perform creation and modification for administrators with provisioning privileges. User deletion is performed with the same single-step procedure that is available with Oracle Delegated Administration Services privileges, as described in "Oracle Delegated Administration Services Privileges".
For administrators with application administration privileges, but not Oracle Delegated Administration Services privileges or provisioning privileges, Create and Delete buttons are not available in the Provisioning Console. However, there is an Edit button that launches the same wizard that is available with provisioning administration privileges, as described in "Provisioning Administration Privileges". If the application administrator does not have provisioning privileges, then the first page in the wizard, which is used for general user provisioning, is read-only. Yet, the application administrator can modify the application provisioning attributes that are available on other pages in the wizard.
Administrators with Oracle Delegated Administration Services privileges and provisioning privileges have the same rights that are available with provisioning administration privileges, as described in "Provisioning Administration Privileges".
This section explains how privileges are delegated if an administrator is assigned various Oracle Delegated Administration Services privileges and also has administrative privileges.
For application administrators with user creation privileges in Oracle Delegated Administration Services, but not user editing or deletion privileges, the Create and Edit buttons are available in the Provisioning Console, but not the Delete button. User creation is performed with the same wizard-based procedure that is available with provisioning administration privileges, as described in "Provisioning Administration Privileges". User editing privileges are the same as those available with application administration privileges, as described in "Application Administration Privileges".
For application administrators with user editing privileges in Oracle Delegated Administration Services, but not user creation or deletion privileges, the Edit button is available in the Provisioning Console, but not the Create or Delete buttons. User editing is performed with the same wizard-based procedure that is available with provisioning administration privileges, as described in "Provisioning Administration Privileges".
For application administrators with user deletion privileges in Oracle Delegated Administration Services, but not user creation or modification privileges, the Delete and Edit buttons are available in the Provisioning Console, but not the Create button. User deletion is performed with the same single-step procedure that is available with Oracle Delegated Administration Services privileges, as described in "Oracle Delegated Administration Services Privileges". User editing is performed with the same wizard-based procedure that is available with provisioning administration privileges, as described in "Provisioning Administration Privileges".
Administrators with provisioning privileges and application administration privileges have the same rights that are available with provisioning administration privileges, as described in "Provisioning Administration Privileges".
Administrators with Oracle Delegated Administration Services privileges and application administration privileges have the same rights that are available with provisioning administration privileges, as described in "Application Administration Privileges".