| Oracle® Adaptive Access Manager Reference Guide Release 10g (10.1.4.5) Part Number E12054-03 |
|
|
View PDF |
| Oracle® Adaptive Access Manager Reference Guide Release 10g (10.1.4.5) Part Number E12054-03 |
|
|
View PDF |
This chapter provides an in-depth understanding of Oracle Adaptive Access Manager's device fingerprinting technology. Oracle Adaptive Access Manager identifies devices based on combinations of the device ID tentacles; secure cookie, flash object, user agent string, browser characteristics, device hardware configuration, network characteristics, geo-location and historical context. The intelligent identification does not rely on any single tentacle so it can function on user devices not following strict specifications. This is especially important in consumer facing deployments.
The device is identified using proprietary logic and a configurable set of nested models. This document lists some of the conditions that are used to identify the device. These conditions evaluate historical user behavior and cases where some tentacles are not available such as cookies, Flash. As well, the specialized models detect high-risk situations such as out-of-sync or manipulated cookies.
Oracle Adaptive Access Manager device fingerprinting is a mechanism to recognize the devices a customer uses to login – whether it is a desktop computer, laptop computer or other web enabled device. Oracle Adaptive Access Manager uses dozens of attributes, including proprietary OTS (One Time Secure) cookies, flash objects and advanced "Auto-Learning" device identification logic, to "fingerprint" the device. Oracle Adaptive Access Manager's patent-pending fingerprinting process produces a fingerprint that is not vulnerable to "replay attacks" and does not have any logic on the client side where it's vulnerable to exploit. The device identification is not merely a static list off attributes but a dynamic capture and evaluation of the specific combinations of attributes.
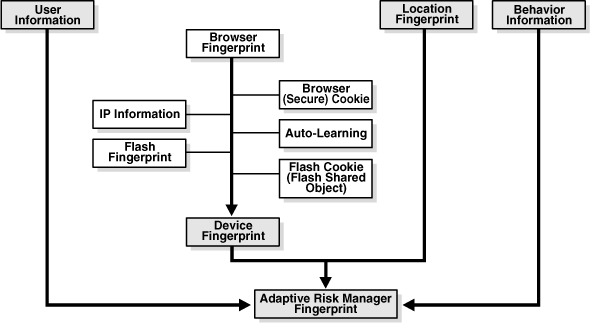
A device is fingerprinted as soon as it hits the system, prior to any authentication attempt. This way the device identification information is available for risk evaluation at any runtime. Some common runtimes are pre-authentication, post-authentication and in-session/transaction.
Generally the login page is embedded with a few lines of static html snippet code. The html snippet also has code to include a flash object and image tags to collect advanced device characteristics. The flash code internally makes a call to the application server thereby uploading the device characteristics.
Oracle Adaptive Access Manager generates a unique Secure Cookie for each session and looks for the same cookie the next time any user logs in from the device. The cookie is only valid for that session on that particular device. The cookies are retrieved or set using the following mechanisms:
Image tags - An image tag might be introduced in the login page, which makes a call to the server to get the image. This request sends the cookies from the browser, which is used for finger printing the device. The image tags could also be used to compute the network bandwidth and the processing speed of the device. These additional data points could also be used by Oracle Adaptive Access Manager to uniquely identify the network/computer device while authenticating the user.
HTTP Requests - In cases where images are blocked, the cookies might be extracted from the login request itself. Oracle Adaptive Access Manager uses these different modes of collecting the cookies to overcome some technical difficulties imposed by browser or the security settings on the device.
The request from the flash client and image request need to be handled by the application server and passed on to the Oracle Adaptive Access Manager client code. This client code extracts the device characteristics information from the request and calls the Oracle Adaptive Access Manager server.
The Oracle Adaptive Access Manager client library is given with the source code. The customer can use it directly or customize it to suite their environment.
This section provides information about the device fingerprinting attributes including secure browser cookies, Flash Shared Objects, and locations information
As mentioned above, secure browser cookies are one of the mechanisms used to identify the device and create the Oracle Adaptive Access Manager Intelligent Fingerprint. The secure cookies are rotated every time the user logs in. The Secure Cookies are extracted from the HTTP request. Along with the secure cookie, the Oracle Adaptive Access Manager also extracts the Browser characteristics, like user agent, time zone, locale, etc.
For additional characteristics that are used to create a unique fingerprint for the device, refer to the table below.
| OS/Browser | Characteristics |
|---|---|
| Operating System | Operating SystemVersion Patch |
| Browser | Browser Version Patch Support
levelJavaScript Support Image |
Similar to Secure Cookie, Oracle Adaptive Access Manager uses Flash Shared Objects to store rotating digital cookie and update it on each login request. The cookie is sent to the server using an HTTP request. Along with the cookie, the Flash movie also sends the device characteristics, such as does the computer have a microphone, audio, etc., thereby creating an additional fingerprint to the device. For additional characteristics, refer to the table below.
| Hardware/Software | Characteristics |
|---|---|
| Hardware | Screen DPI
Screen color Screen resolution Has audio card Has printer support Has microphone |
| Software | Has audio encoder
Supports Video Has MP3 encoder Can play streaming Audio Can play streaming Video Has Video encoder |
The locations information used by the user is also stored in the Oracle Adaptive Access Manager database and used by the rules engine to identify anomalies in user login patterns and also to validate whether the location is blacklisted and if the user is permitted to login from the location.
Oracle Adaptive Access Manager's method for device fingerprinting generates a one-time fingerprint for each user session which is unique to the individual's device and which is replaced upon each subsequent visit with another unique fingerprint. This ensures that even a stolen fingerprint cannot be reused for fraud.
Some of the attributes collected to generate the location fingerprint are listed below:
IP address
City, State, Country information and confidence factors
Connection type
Connection speed
IP routing type
ISP flag
ASN
Carrier name
Top-level domain
Second-level domain
Registering organization
A list of anonymizing proxies
Hostnames and routers
Oracle Adaptive Access Manager includes robust risk models (containing pre-packaged rules) for security, business, workflow and 3rd party data, which are evaluated by the system in real time. Oracle Adaptive Access Manager's base models include many rules that use device rule templates.
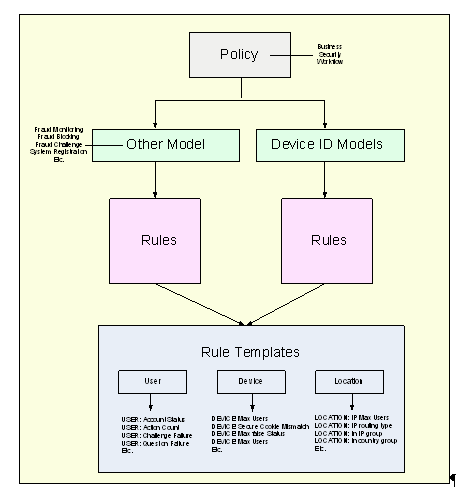
Customizing the rules that come standard with the product and adding new rules require minimal effort on the part of the institution due to the intuitive rule template editor accessible in Oracle Adaptive Access Manager.
To view the list of Device Identification models, choose Models from the Admin menu. Then, from the Models menu, select List Models.
With the Device Identification item selected for the Run Time, click Run Query.
Oracle Adaptive Access Manager's fingerprinting technology does not solely rely on one element. Oracle Adaptive Access Manager uses dozens of attributes to recognize and "fingerprint" the device you typically use to login, providing greater "coverage" for an institution's customer base. For example, in the case where certain elements are unavailable, the system can still provide robust security utilizing other objects (secure cookie, flash cookie, HTTP header, Real Media, QuickTime, etc.). Oracle Adaptive Access Manager's secure device fingerprinting technology allows for a higher non-repudiation in associating device with user and transaction, reducing false positives that other fingerprinting technologies cannot overcome currently.
Oracle Adaptive Access Manager recognizes that institutions need solutions that are non-intrusive for their end users, making device identification increasingly crucial to all rules incorporating device fingerprinting.
Non-repudiation = authentication that with high assurance can be asserted to be genuine, and that can not subsequently be refuted.
These use cases help to define Oracle Adaptive Access Manager's device risk gradient. The device risk gradient specifies the certainty of the device being identified. It is standard in almost all rules as a pre-condition. For example, a device risk gradient of 0 is an exact match whereas a device gradient of 500 is a "similar" device, and a score of 1000 a "different" device.
Are you reading the device characteristics at every logon time and matching them to the previously stored fingerprint in the cookie?
The device characteristics are read at each logon. The fingerprint is not in a cookie. It is in a database.
How does introducing the session factor prevent against a stolen (persistent) cookie scenario? Does the product have to keep the last session id of each device per user on the backend adaptive store?
You could steal the cookie, but it is a "one-time" use cookie. So there are two options; either:
the real user has already used his cookie once and the system has updated (changed, used up) the stale cookie so it is no good, or
the fraudster uses the cookie before the real user. It is certainly possible that the hacker could beat the user to use the one-time cookie but the device fingerprint would be different for the rogue user and they would then have to answer the user's KBA questions
On the possibility that the fraudster does use the cookie first and it succeeds (this might not even be possible), then the real user can receive a warning that their cookie is now stale, and that may tip them off that something is wrong. The real user can then change their password, and so on.
Is it a persistent cookie that stores the device characteristics?
It is not in a cookie. It is stored in a database.
Do you have a database store keeping those fingerprints per user device to match against what you read from device at logon time?
Yes, Oracle Adaptive Access Manager has its own database in which device fingerprints and other operational information are stored. There is a separate fingerprint for each user that has used a machine. The fingerprint is not stored locally on the machine.
What if persistent cookies are disabled?
Oracle Adaptive Access Manager uses different pieces of information about a machine to develop the "device fingerprint". If persistent cookies are disabled, Oracle Adaptive Access Manager still has other information to use in identifying the machine.
Each feature standing on its own is not sufficient to secure the session; it is the combination of device fingerprint, IP, location, time, behavioral analysis, behavioral analysis as it relates to past behavior, etc.
What if secure cookies are deleted?
Oracle Adaptive Access Manager's fingerprinting technology does not solely rely on one element. Oracle Adaptive Access Manager uses dozens of attributes to recognize and "fingerprint" the device you typically use to login, providing greater "coverage" for an institution's customer base. If secure cookies are missing or disabled, Oracle Adaptive Access Manager uses other elements such as flash object and HTTP headers for device identification.
What if flash is not enabled?
Oracle Adaptive Access Manager's fingerprinting technology does not solely rely on one element. Oracle Adaptive Access Manager uses dozens of attributes to recognize and "fingerprint" the device you typically use to login, providing greater "coverage" for an institution's customer base. If flash is not enabled, Oracle Adaptive Access Manager uses other elements such as secure cookie and HTTP headers for device identification.
How are device scores determined
Device scores are determined using Oracle Adaptive Access Manager's proprietary algorithm. A device score is made up of many elements. Each element can have a range of values. These values are used to determine the device score.
When a customer has the appropriate device scoring models deployed they can see these individual rule scores. The session holds the values that make up this score.
Why are there so many device ID models
Our team has created many device ID models to take into account the various use cases that we've learned through our Fraud Intelligence Network. By creating these device ID models, we have created a robust device identification mechanism and reduced false positives as a result.
Are device ID models configurable?
Yes, device ID models are configurable.
Can we add new device ID models? If so, how?
Yes, new device ID models can be added. We recommend that you work with our Professional Services team to create any new device ID models
To view the list of Device Identification models, choose Models from the Admin menu. Then, from the Models menu, select List Models.
With the Device Identification item selected for the Runtime, click Run Query.
The Device Identification Models provided are:
201 Cookie enable check
202 Flash missing
203 Cookie missing
204 Http header mismatch
205 Hdr mismatch No Flash
206 Hdr mismatch No SC
207 Device upgrade
208 Brwsr Device upgrade
209 SecureCookie mismatch
210 Same device DigCookie
211 out of sync cookie
301 First time browser
401 GeoCheck Flash Came
systemDeviceID
To view the list of Device Identification rule templates, choose Rule Templates from the Admin menu. Then, from the Rule Templates menu, select List Rule Templates.
With the Device ID Rules item selected for the Runtype, click Run Query.
The Device ID rule templates provided are:
Cookies Match
Header data match
Header data match percentage
Header data present
Http Header data Browser match
Http Header data Browser upgrade
Http Header data OS match
Http Header data OS upgrade
Is Cookie Valid
Is Cookie empty
Is Cookie from same device
Known header data match percentage