|
Oracle® Business Intelligence Applications Installation and Configuration Guide > Integrated Security for Oracle BI Applications > Implementing Security With Oracle EBS >
About Unit-Based Security With Oracle EBS
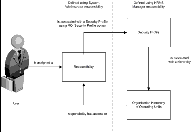
Operating Units are secured by attaching a security profile to a user ID or responsibility. In turn, a security profile is associated with an organization hierarchy (see figure below). Figure 35. Unit-based security against Oracle EBSOperating Unit Dimension is decided by looking at the profiles set at User/Responsibility/Application/Site Levels (in order). In other words, if a value is set in the profile at User Level and at Site Level, the value set at user level takes precedence. The profiles used are: - MO: Security Profile.
Depending on the Security Profile assigned, the Operating Units which are associated with that Security Profile become accessible to the User.
- MO: Operating Unit.
If (1) is set to NULL (not set at any of the 4 levels), then we look at the profile, MO: Operating Unit. The only difference is that while MO: Operating Unit can be assigned only 1 OU, MO: Security Profile basically contains a Security Profile, which has access to 1 or more Operating Units.
Operating Unit Dimension is essentially a User secured dimension, which does the following: - It looks at the context of the user accessing a report.
- It determines which Operating Units the user can access.
- It displays the content.
From Oracle EBS R12 onwards, one Operating Unit is not fixed to just one responsibility. Users can still login as "Purchasing, Vision Operations (USA)" and create a PO for "Vision Germany", as OU is now shown as a LOV in the PO screen and the LOV values that show up depend on the 2 profiles. Implementation Steps For Unit-Based Security With Oracle EBS
The implementation steps are as follows: - Oracle BI Applications uses LDAP authentication, and the following session variable is set automatically.
- System variable: USER -->
- Oracle BI Applications gets the operating unit set corresponding to the USER, from FND_USER_RESP_GROUPS. The following session variable is set automatically:
- The security group hosts the collection of all related data access permissions. During implementation, customers have to decide which users or other groups to apply this security and add the users or other groups as members of the group.
- Security group: Operating Unit Org-based Security -->
- The permissions enforce the data security on the logical tables that have a relationship with operating units (for a list of logical tables, see Table 117 below).
- When users creates ad-hoc reports, they will see the data that is assigned with these permissions. For reports involved with the logical tables (for a list of logical tables, see Table 117 below), users are restricted to data pertaining to their visibility in the organization structure of the operating unit.
Table 117. Logical tables secured
|
"Core"."Fact - Sales - Backlog Lines" |
"Core"."Fact - Sales - Booking Lines" |
"Core"."Fact - Sales - Invoice Line" |
"Core"."Fact - Sales - Backlog History" |
"Core"."Fact - Sales - Pick Line" |
"Core"."Fact - Sales - Order Line" |
"Core"."Fact - Sales - Schedule Line" |
"Core"."Fact - Sales - Cycle Line" |
"Core"."Fact - Purchasing - Cost" |
"Core"."Fact - Purchasing - Cycle Line" |
"Core"."Fact - Purchasing - Order Item" |
"Core"."Fact - Purchasing - Receipt" |
"Core"."Fact - Purchasing - Requisition" |
"Core"."Fact - Purchasing - Request Status" |
"Core"."Fact - Purchasing - Schedule" |
"Core"."Fact - Fins - AP Employee Expense" |
"Core"."Fact - Sales - Customer Status History" |
"Core"."Dim - Operating Unit Org" |
"Core"."Fact - Fins - AR Transaction" |
"Core"."Fact - Fins - AP Transaction" |
"Core"."Fact - Fins - (Internal) AP Current Closing Balance" |
"Core"."Fact - Fins - (Internal) AP Balance Delta" |
"Core"."Fact - Fins - (Internal) AR Current Closing Balance" |
"Core"."Fact - Fins - (Internal) AR Balance Delta" |
"Core"."Fact - Fins - AP Posted Transaction" |
"Core"."Fact - Fins - AR Posted Transaction" |
"Core"."Fact - Fins - AR Aging" |
"Core"."Fact - Fins - AP Aging" |
About Inventory Organization-Based Security With Oracle EBS Ideally, Inventory organization security is applied on the basis of the currently logged-in responsibility, rather than a current user. In EBS however, if an Inventory Org V1 has been associated with Responsibility R1 and R2, then V1 is accessible only to those 2 responsibilities. If another Inventory Org V2 has not been defined at all in that screen, then all responsibilities have access to V2. Each record entry into this form inserts a row into ORG_ACCESS table. This is the reason for a UNION based query of BIS_ORGANIZATIONS_V, and ideally, the Inventory Org secured view definition should have been: SELECT 'INV_ORG', BIS_ORGANIZATIONS_V.ID FROM BIS_ORGANIZATIONS_V WHERE RESPONSIBILITY_ID = :RESPONSIBILITY_ID
This would give us a list of Inventory Organizations that are accessible to the "logged in" responsibility. In case security is set as user level in BI EE, the BI query is secure because it simply checks all the responsibilities accessible to the user, and then queries the ORG_ACCESS to check all the Inventory Organizations accessible to those responsibilities and all those Inventory Organizations that are not specifically allocated to any responsibility (in other words, accessible to everyone). This combined list of Inventory Orgs would be applied in the query. Therefore, it is possible that certain inventory organizations have been explicitly granted to certain responsibilities (using the ORG ACCESS form), and if the responsibility is not assigned to the logged-in user, then those inventory orgs would not be displayed to the user. Implementation Steps For Inventory Organization-Based Security With Oracle EBS
The implementation steps are as follows: - Oracle BI Applications uses LDAP authentication, and the following session variable is set automatically.
- System variable: USER -->
- Oracle BI Applications gets the operating unit set corresponding to the USER, from FND_USER_RESP_GROUPS. The following session variable is set automatically:
- The security group hosts the collection of all related data access permissions. During implementation, customers have to decide which users or other groups to apply this security and add the users or other groups as members of the group.
- Security group: Inventory Org-based Security -->
- The permissions enforce the data security on the logical tables that have a relationship with operating units (for a list of logical tables, see Table 118 below).
When users creates ad-hoc reports, they will see the data that is assigned with these permissions. For reports involved with the logical tables (for a list of logical tables, see Table 118 below), users are restricted to data pertaining to their visibility in the organization structure of the operating unit.
Table 118. Logical tables secured
|
"Core"."Fact - Sales - Backlog Lines" |
"Core"."Fact - Sales - Booking Lines" |
"Core"."Fact - Sales - Invoice Line" |
"Core"."Fact - Sales - Backlog History" |
"Core"."Fact - Sales - Pick Line" |
"Core"."Fact - Sales - Order Line" |
"Core"."Fact - Sales - Schedule Line" |
"Core"."Fact - Sales - Cycle Line" |
"Core"."Fact - Purchasing - Cost" |
"Core"."Fact - Purchasing - Cycle Line" |
"Core"."Fact - Purchasing - Order Item" |
"Core"."Fact - Purchasing - Receipt" |
"Core"."Fact - Purchasing - Requisition" |
"Core"."Fact - Purchasing - Request Status" |
"Core"."Fact - Purchasing - Schedule" |
"Core"."Fact - Supply Chain - Inventory Balance" |
"Core"."Fact - Supply Chain - Inventory Transaction" |
"Core"."Fact - Sales - Customer Status History" |
"Core"."Fact - Supply Chain - Compound Inventory" |
"Core"."Dim - Inventory Org" |
|