| Oracle® Access Manager Identity and Common Administration Guide 10g (10.1.4.2.0) Part Number B32419-01 |
|
|
View PDF |
| Oracle® Access Manager Identity and Common Administration Guide 10g (10.1.4.2.0) Part Number B32419-01 |
|
|
View PDF |
Oracle Access Manager provides support for .NET features with Windows Server 2003. For details about supported features and their implementation within Oracle Access Manager, see the following topics in this appendix:
Active Directory running on Windows Server 2003 provides support for ambiguous name resolution (ANR).
ANR is a search algorithm associated with LDAP clients that must be enabled on both the LDAP client and the LDAP server. ANR allows objects to be bound without complex search filters and is useful when locating objects and attributes that may or may not be known by the client.
In Oracle Access Manager, ANR is a virtual attribute that does not physically exist in the directory server. Oracle Access Manager provides the virtual ANR attribute through the AD_anr.ldif file, which enables Oracle Access Manager to interpret ANR requests, map ANR requests to Boolean functions And and Or that expand to a directory-server filter to broaden the search, and send the query to Active Directory.
Note:
The AD_anr.ldif file is included in the Oracle Access Manager schema installation and must be imported manually. See "Configuring for ANR" for details.By default, the attributes shown in Table D-1 are set for ANR.
Table D-1 ANR Attributes
| ANR Attributes |
|---|
|
displayName |
|
GivenName |
|
LegacyExchangeDN |
|
msExchMailNickname |
|
name |
|
physicalDeliveryOfficeName |
|
proxyAddress |
|
sAMAccountName |
|
Surname |
For a search filter such as (anr=von), the server would return objects that matched any of the previously listed attributes equal to von*. When a space is embedded in the search string, the search is divided at the space and an Or search is also performed on the attributes. The server attempts to perform first/last name processing. When there is only one space, the search divides only at the first space.
For example, if the search filter was (anr=Rob Al), the filter expansion would look like the following.
(|(givenName=Rob Al*) (sn=Rob Al*) (displayName=Rob Al*) (legacyExchangeDN=Rob Al*) (name=Rob Al*) (physicalDeliveryOfficeName=Rob Al*) (proxyAddresses=Rob Al*) (saMAccountName=Rob Al*) (&(givenName=Rob*)(sn=Al*)) (&(givenName=Al*)(sn=Rob*)) )
The attributes used by ANR are configurable. You can specify other attributes to be included in ANR searches by using the Active Directory Schema Snap-in to check the Ambiguous Name Resolution box for the attribute. You can directly set the searchFlags attribute to 5 in the attributeSchema for the attribute you want to include. To include an attribute to be used for ANR, the attribute must also be indexed.
The following task overview outlines the procedures you must complete to enable ANR within Oracle Access Manager. After you upload the meta-attribute configuration for ANR into the configuration branch in the directory server, the ANR attribute should be configured on the profile page and defined as searchable. Attribute access control can also be configured on the same profile page.
Task overview: Preparing to use ANR during searches
Update Oracle configuration data to include the ANR meta-attribute details in the configuration branch of the schema, as described in "Updating Configuration Data".
Make the ANR attribute available to the Oracle Access Manager search function in the Identity Server, as described in "Configuring ANR in Identity System Panels".
Verify Access Control rights, as described in "Verifying ANR Attribute Access Control".
Use ANR-to-Oracle Access Manager authentication and authorization search filters, as described in "Using ANR in Identity System Searches".
You first need to update configuration data (Oracle Access Manager configuration data) to include the ANR meta-attribute configuration information in the configuration branch. During this procedure, the following AD_anr.ldif is executed.
#File to load ANR meta-attribute configuration to the directory tree. dn: obattr=anr,obclass=user,OU=Oblix,<domain-dn> changetype: add instanceType: 4 distinguishedName: obattr=anr,obclass=user,OU=Oblix,<domain-dn> objectClass: oblixmetaattribute name: anr obattr: anr obcardinality: ob_single obdisplayname: ANR obdisplaytype: ObDTextS obsearchable: true obvisible: true
When this procedure is complete, ANR appears as an attribute you can select when configuring Identity System panels.
To update Oracle configuration data
Locate the AD_anr.ldif file on the machine hosting the Identity Server: \IdentityServer_install_dir\identity\oblix\data.ldap\common\AD_anr.ldif.
Import the AD_anr.ldif file to the configuration directory.
For example:
D:\data>ldifde -i -f AD_anr.ldif -a "cn=administrator,cn=users,dc=name,dc=company,dc=net" password
Restart the Identity Server.
After you update the Oracle configuration data with ANR meta-attributes, you are ready to make the ANR attribute available to the Identity System search function on a Tab (panel) and in the list of searchable attributes in the User Manager Selector.
The following procedure guides you through configuring ANR in Identity System panels. For more information, see "Configuring User, Group, and Organization Manager".
To configure ANR in Identity System Panels
From the Identity System landing page, click the link for the Identity System Console.
If you are already logged in, click the Identity System Console tab.
Click the User Manager Configuration sub-tab, then click the Tabs link in the left navigation pane.
Click the link for the tab, then click View Object Profile.
Click Configure Panels, then click the link for the panel that you want to configure.
A summary appears listing all attributes for the selected panel.
Click the Modify button at the bottom of the summary page.
The Modify Panel page appears.
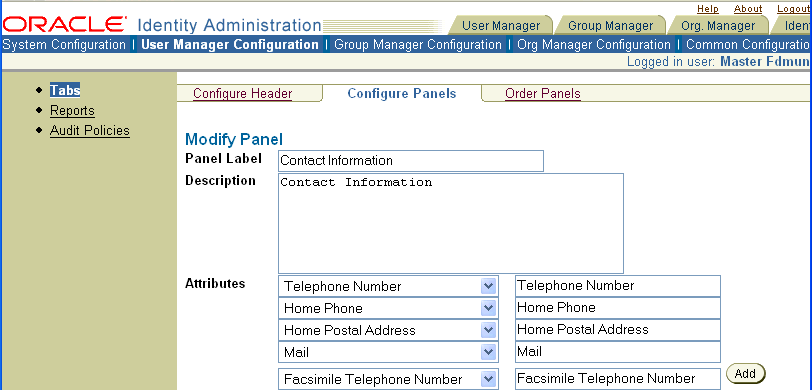
Click the Add button, then select ANR from the list in the Attributes column and click Save.
The summary page appears listing all attributes, which should now include ANR.
Next you need to confirm that ANR is a searchable attribute that will appear in the Query Builder's search criteria list.
From the Identity System Console, click the User Manager Configuration sub-tab, then click the Tabs link in the left navigation pane.
Click the link for the tab.
Click the View Search Attributes button at the bottom of the page.
A list of all search attributes appears.
Confirm that ANR is in the list. For example:
Restart the Identity Server.
By default, the attribute has read rights. The ANR attribute must not have modify rights. The following procedure shows the Access Control rights for the ANR attribute. See "Setting and Modifying LDAP Attribute Permissions" for details.
To verify ANR attribute access control
From the Identity System landing page, click the link for the User Manager.
If you are already logged in to the Identity System, click the tab for the User Manager application.
Click the Configuration sub-tab, then click the link for Attribute Access Control.
Select ANR from the Attribute list, then verify that it has read rights only.
You are ready to use ANR in Identity System searches.
When a user invokes the User Manager, they can choose ANR from the search criteria list to perform a directory search.
From the Identity System landing page, click the link for the User Manager.
If you are already logged in to the Identity System, click the tab for the User Manager application.
Select ANR from the Search list, define other search criteria, then enter your condition.
Click Go and check your results.
A structural object class can stand on its own and contains basic attributes required for use within Identity System applications. Structural object class examples include person and groupOfNames. The person object class may contain attributes such as name, department, employee ID, and email address. A structural object class must be assigned when you create a tab within an Identity System application.
Auxiliary object classes are mix-in classes that can be added to any structural class. You use an auxiliary object class to add a set of related attributes to an entry that already belongs to a structural class. Items such as a billing address, a challenge phrase, a response to a challenge phrase, and so on may be useful for definition in an auxiliary object class.
With Windows Server 2000, Active Directory supported only statically linked auxiliary classes. A statically-linked auxiliary class is one that is included in the auxiliaryClass or systemAuxiliaryClass attribute of an object class's classSchema definition in the schema. It is part of every instance of the class with which it is associated. Using statically-linked auxiliary classes is the default with Oracle Access Manager is installed with Active Directory. All other directories support only dynamically linked auxiliary object classes.
With a Windows 2003 Server, Active Directory and Oracle Access Manager support dynamically linked auxiliary classes. With the schema defined for a particular user, group, or organization, dynamically linked auxiliary classes enable you to store additional attributes with an individual object without the forest-wide impact of extending the schema definition for an entire class. Dynamically linked auxiliary class attributes are mixed in only at runtime.
For example, you can use dynamic linking to attach a sales-specific auxiliary class to the user objects of sales people and other department-specific auxiliary classes to the user objects of employees in other departments. Or you may want to convert a basic group to a mail group by adding specific attributes dynamically.
Task overview: Setting up for dynamic auxiliary classes
Install and set up Oracle Access Manager with dynamic-auxiliary classes enabled, as described in the Oracle Access Manager Installation Guide.
Specify additional structural object classes for the Organization Manager, as described in "About Object Classes".
Configure attributes, as described in "About Object Class Attributes".
Configure User, Group, and Organization application tabs, as described in "Configuring Tabs".
Configure User, Group, and Organization profile pages, as described in "Configuring Tab Profile Pages and Panels".
Define workflows, as described in "Chaining Identity Functions Into Workflows".
Specify additional auxiliary object classes, as described in "Adding Attributes Dynamically".
The following procedure provides an example only and assumes that you have created a Tab and Panel in the User Manager. Here you will add desired auxiliary attributes dynamically.
Note:
This is only an example. You may be working in the Group Manager or Organization Manager. See also, "Adding Attributes for a Group".To specify additional auxiliary object classes in the User Manager
From the Identity System Console, click User Manager Configuration, then click Tabs in the left navigation pane.
Click the link for the tab.
Click the View Object Profile button, then click the Configure Panels link.
Click the link for the panel that you want to modify.
Click the Modify button to display the Modify Panel page.
Click the Add button, select one or more attributes from the list, then click Save.
The View Panel page appears with the attributes you added.
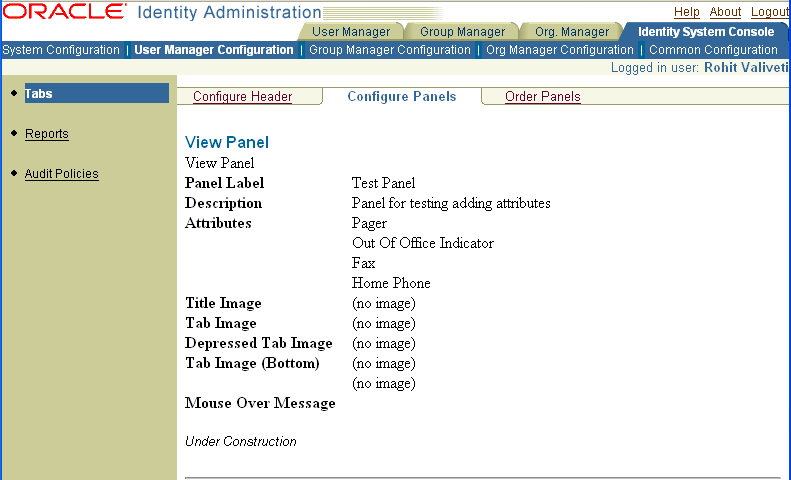
The entry in the directory server has changed, and the new attributes are included.
The example in this procedure dynamically converts a single basic group to a mail group by adding attributes, such as:
| Attribute 1 | Attribute 2 | Attribute 3 |
|---|---|---|
| MailAlternateAddress | Mailhost | MailRoutingAddress |
This example assumes that you have created a Group Panel and a workflow to create a Mail Group. Now you add desired attributes dynamically. This is only an example. You may be working in the User Manager or Organization Manager. See also "Adding Attributes Dynamically".
To add attributes to a Group Profile panel
From the Identity System landing page, click the link for the Identity System Console.
If you are already logged in, click the Identity System Console tab.
Click the Group Manager Configuration sub-tab, then click the Tabs link in the left navigation pane.
Click View Object Profile, Configure Panels, then click the link for the panel that you want to modify.
The View Panel page appears.
Click Modify.
The Modify Panel page appears.
In the Attributes section of the page, click the Add button, select one or more attributes from the list, then click Save and verify that the attributes you added appear in the View Panel page.
Select Group Manager from the Select Application list in the upper right corner.
Enter your search criteria in the Selector and click Go.
The results are returned. When you select a Group to review you will notice that the attributes you added dynamically to one group are available only for that group.
Click Modify, click the + button, then add a specific value, and save, as usual.
The entry in the directory has also changed. For example, the following screen shot shows a sample entry before auxiliary classes were added.
The next screen shows the same entry after auxiliary classes were added.
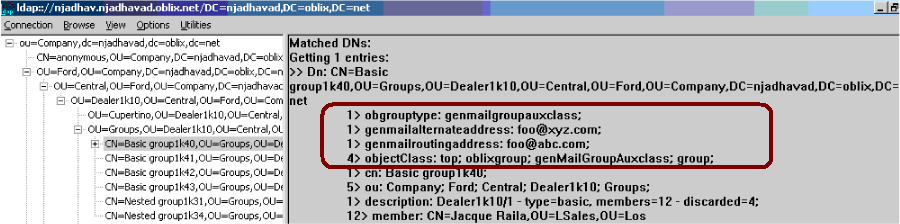
The Active Directory running on Windows Server 2003 provides a concurrent bind (also known as fast bind) feature that allows multiple authentications over the same LDAP connection.
The Access System supports and uses this feature, which provides the following advantages:
Fast bind permits two threads to request a bind over one connection at the same time.
Fast bind provides a faster authentication mechanism because it only validates the password and the account flag and does not build a ticket.
The Fast Bind option must be enabled for each database instance, and is located on individual database profiles in the Access System Console.
To configure the Access System to use a fast bind
From the Access System Console, click the System Configuration tab.
Click the View Server Settings link in the left navigation pane.
The Configure LDAP Directory Server Profile section on this page is where you choose the directory profile to modify.
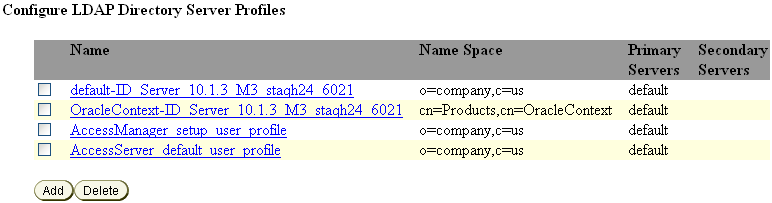
Click the name of the directory server instance on which you want to enable the Fast Bind feature.
The Modify Directory Server Profile page appears, and you can locate the instance of the directory server profile (also called the database instance) to modify near the bottom of the page.
Locate and click the name of the directory server profile instance (database instance) that you want. For example:

Click the link for this instance and check the box beside the Fast Bind option. For example:
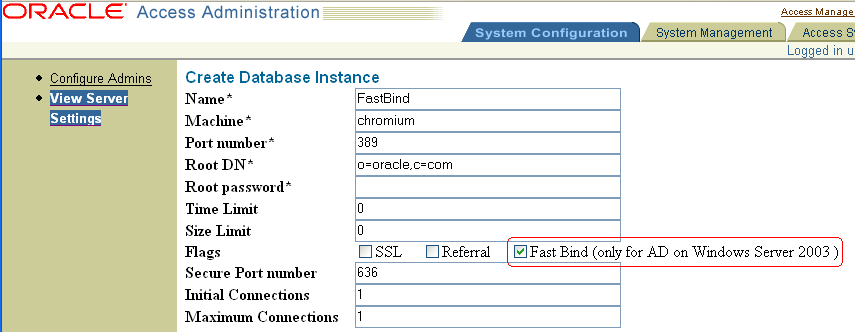
Click Save.
Confirm that the profile is enabled on the Modify Directory Server profile page.
Repeat as needed to enable the Fast Bind option for other database instances.
In a Windows environment, all processes and threads execute in a security context. Impersonation is the ability of a thread to execute in a security context that is different from that of the process that owns the thread. The primary purpose of impersonation is to trigger access checks against a client's identity.
For details about enabling impersonation in Oracle Access Manager, which overrides impersonation enabled with IIS, see Oracle Access Manager Access System Administration Guide.
Oracle Access Manager provides support for integrated Windows authentication (IWA). Your environment may include:
Windows 2000 Server or Windows Server 2003 or Solaris
Internet Information Services (IIS) 5.5 or 6.x
Active Directory or iPlanet directory server
If the user's directory server has, for example, an NT Logon ID, or if the user name is the same everywhere, then a user is able to authenticate into any directory server.
The most common authentication mechanism on Windows 2000 and Windows Server 2003 is Kerberos.
The use of IWA by Oracle Access Manager is seamless. The user won't notice any difference between a typical authentication and IWA when they log on to their desktop, open an Internet Explorer (IE) browser, request a protected web resource, and complete single sign-on.
To see the supported versions and platforms for this integration, refer to Metalink, as follows.
To view information on Metalink
Go to the following URL:
Click the Certify tab.
Click View Certifications by Product.
Select the Application Server option and click Submit.
Choose Oracle Application Server and click Submit.
Process overview: Using IWA authentication
The user logs in to the desktop machine, and local authentication is completed using the Windows Domain Administrator authentication scheme.
The user opens an Internet Explorer (IE) browser and requests an Access System-protected Web resource.
The browser notes the local authentication and sends a token to the IIS Web server.
The IIS Web server uses the token to authenticate the user and set up the REMOTE_USER HTTP header variable that specifies the user name supplied by the client and authenticated by the server.
The WebGate installed on the IIS Web server uses the hidden feature of external authentication to get the REMOTE_USER header variable value and map it to a DN for the ObSSOCookie generation and authorization.
The WebGate creates an ObSSOCookie and sends it back to the browser.
The Access System authorization and other processes proceed as usual.
The maximum session timeout period configured for the WebGate is applicable to the generated ObSSOCookie.
Task overview: Setting Up IWA authentication
Install a WebGate on the same IIS Web server or servers on which you will set up IWA, as described in the Oracle Access Manager Installation Guide.
If you installed the WebGate at the Site level, you should perform the tasks at the Site level.
If you have multiple WebGates installed at different virtual sites, you should perform the tasks for each virtual site.
Enable IWA on the WebGate, as described in "Enabling IWA on the WebGate Web Server".
Configure the WebGate to use IWA, as described in "Configuring the WebGate for IWA" .
Create an authentication scheme for IWA in Oracle Access Manager, as described in "Creating an IWA Authentication Scheme in Oracle Access Manager".
Test the IWA implementation, as described in "Testing IWA Implementation".
The first procedure is to enable IWA on the machine hosting the WebGate.
If you have installed the WebGate at the Site level, you should perform the tasks at the Site level.
If you have multiple WebGates installed at different virtual sites, you should perform the tasks for each virtual site.
To enable IWA on the machine hosting the WebGate
Start the Internet Services Manager on the machine hosting the WebGate: Start, Programs, Administrative Tools, Internet Services Manager
Right-click the Default Web site (or the name of Web server if you changed the name of the Default Web site), then select Properties.
Note:
If you installed WebGate at the Site level, right-click the Site then select Properties.Click the Edit button beside Master Properties.
Click the Directory Security tab, then click Edit beside "Anonymous access and authentication control."
Disable Anonymous Access on the IIS Web Server.
Enable Integrated Windows Authentication.
Click OK, then click OK again.
Restart the IIS Web server.
To configure the WebGate for IWA, you must set the user-defined parameter UseIISBuiltinAuthentication to true in the Access System Console. See the chapter on configuring the Access System in Oracle Access Manager Access System Administration Guide for details.
To modify an AccessGate through the Access System Console
Launch the Access System Console, click the Access System Configuration tab, then click the AccessGate Configuration link in the left navigation pane.
The Search for AccessGates page appears.
Select the search attribute and condition from the lists, or select All to find all AccessGates.
The Search list is a selection list of attributes that can be searched. The remaining fields allow you to specify search criteria that are appropriate for the selected attribute.
Click Go.
The search results are displayed on the page.
Click the name of the AccessGate or WebGate that you want to modify.
The AccessGate Details page appears.
Click Modify.
The Modify AccessGate page appears. You can enter new information on this page
You cannot change an AccessGate or WebGate name. To rename it, you must delete it from the Access System Console and then uninstall it. You then create a new AccessGate or WebGate.
Type new values as needed.
Click Save to save your changes.
You must create an IWA authentication scheme for the Access System to use a specific challenge method, challenge parameter, and plug-in, as described in the following procedure.
To create an IWA authentication scheme in the Access System
Navigate to the Access System Console, as usual. For example:
http://hostname:port/access/oblix
Navigate to the Authentication Management page and click Add: Access System Console, Access System Configuration, Authentication Management, Add.
Create an Integrated Windows Authentication scheme.
For example:
Name: Integrated Windows Authentication
Description: This scheme is Integrated Windows Authentication, using the built-in Windows authentication mechanism.
Level: 1
Challenge Method: Ext
Challenge Parameter: creds: REMOTE_USER
SSL Required: No
Challenge Redirect
Click the Plug-Ins tab, then click Modify.
Select the plug-in name from the list, enter your plug-in parameters and click Add, then save when you are finished.
For example:
Plugin(s)
| Plugin Name | Plugin Parameters |
|---|---|
credential_mapping |
obMappingBase=<"Domain name">,obMappingFilter="(&(objectclass=user) (samaccountname=%REMOTE_USER%))" |
Save the authentication scheme and protect resources using this scheme, as usual.
When using the Access System Password Management feature with an Active Directory forest, note the following:
The Change on Reset, Password Expiration, and Password ExpirationWarning features will work.
The Number of Retrieves feature will not work.
This limitation applies only if you are using the LDAP mode for Password Management in the Access System and only if you are using Active Directory in a forest configuration.
The .NET Framework provides an object-oriented programming environment to guarantee the safe execution of code and to eliminate performance problems in scripted environments. In the .NET Framework, code that targets the runtime is called managed code.
In addition, MANAGEDLIB actions offer the benefits of managed code, including:
Language Choice--You can write your plug-ins in VisualBasic, C#, Managed C++ (MC++), Java, or PERL.
Language Integration--You can combine MIL modules compiled from different source languages into one assembly or plug-in.
This provides the plug-in writer with a wider range of language choices for plug-in development.
Support for Memory Management--The common language runtime (CLR) provides garbage collection, freeing the plug-in writer from most memory management.
The garbage collector returns memory to the heap when that memory is no longer referenced. However, the plug-in writer should ensure that there are no dangling references to objects. If there are dangling references, garbage collection will not occur for the unused memory.
.NET Framework Support--The .NET framework SDK contains a wide range of functionality. This may reduce the need for third-party support in plug-in code.
Oracle Access Manager can use and call APIs in many languages, including managed code and languages such as C, Managed C++ (MC++), and Visual Basic.Net.
For more information about managed code and managed helper classes, see the Oracle Access Manager Developer Guide.
The Access System provides an authorization plug-in that uses the Microsoft Windows Server 2003 Authorization Manager (AzMan) services to make authorization decisions for Access Server clients, including WebGates and callers of the Access Server API.
See the Oracle Access Manager Integration Guide for details about configuring a policy domain for the AzMan plug-in.
Oracle Access Manager supports smart card authentication with Active Directory and IIS Web servers in homogeneous Windows environments. Using a smart card provides a stronger form of authentication than a user name and password alone because it is based on something the user knows and something the user has.
Something the user knows is the user's secret personal identification number (PIN), similar in concept to a personal bank code PIN.
Something the user has is the cryptographically-based identification and proof-of-possession generated by the smart card device that you insert into the smart card reader attached to a computer.
See the Oracle Access Manager Integration Guide for details about configuring integrating with smart card authentication.
Oracle Access Manager supports the ASP.NET component of the Microsoft .NET Framework, which developers can use to build, deploy, and run Web applications and distributed applications. The Oracle Access Manager Security Connector for ASP.NET supports and enhances native .NET role-based security.
See the Oracle Access Manager Integration Guide for details about how to use the Oracle Access Manager Security Connector for ASP.NET to instantiate a new OblixPrincipal object and populate it with roles (Access System authorization rules) and the native WindowsPrincipal object.
For more information on troubleshooting, see "Troubleshooting Oracle Access Manager".
Active Directory Home Page
http://www.microsoft.com/windows2000/technologies/directory/ad/default.asp
ADSI Overview
http://www.microsoft.com/windows2000/techinfo/howitworks/activedirectory/adsilinks.asp
Active Directory Programmers Page
ADSI Programmers Page