1 Security in Oracle Fusion Middleware
This chapter provides a survey of security capabilities in Oracle Fusion Middleware and a road map for system administrators and application developers. It contains these topics:
1.1 Terminology
We start by defining some common terms that are used in this document and throughout the related documents mentioned in the preface.
An application can be provided by Oracle or by a third-party vendor, or it can be developed in-house. In all cases, applications are designed to run in an application server environment and take advantage of Oracle Fusion Middleware features and capabilities.
The typical life cycle of an application includes these phases:
-
development
-
deployment
-
ongoing maintenance in a production environment.
Security is an integral part of the application life cycle, although the scope and implementation details may vary.
For example, at development time user credentials can simply be stored in a file, whereas a deployed application is generally secured with an identity management solution using an LDAP directory at the back-end.
Auditing is a process that measures accountability. In the Identity and Access Management space, auditing provides reports and the data you need to determine who accessed what resources and when.
Authentication verifies that the user is who she claims to be. A user's identity is verified through the credentials presented by that user, such as:
-
something one has, for example, credentials issued by a trusted authority such as a passport (real world) or a smart card (IT world),
-
something one knows, for example a shared secret such as a password,
-
something one is, for example, biometric information
A combination of several types of credentials is referred to as "strong" authentication; an example is the use of an ATM card (something one has) with a PIN or password (something one knows).
Also known as access control, authorization is designed to grant access to specific resources based on an authenticated user's entitlements. Entitlements are defined by one or several attributes. An attribute is the property, characteristic, or role of a user; for example, if "Raj" is the user, "software engineer" is the attribute (or role).
Authorization is based on the enforcement of access policies; for example, if Raj is assigned the software engineer role, he can access specific application code.
A credential store is a service that you can use to store passwords to external applications and systems such as databases or LDAP directories.
In Oracle Fusion Middleware 11g Release 1 (11.1.1), the credential store is either file-based (Oracle wallet) or an LDAP-based repository for storing credentials such as passwords.
The deployment phase is the second stage in the life cycle of an application. During this phase, administrators package the application and deploy it to the target environment (for example, an application server) to enable end user access.
In the deployment phase, administrators typically perform application role-to-enterprise group mappings. For more information, see
The development phase is the first stage in the life cycle of an application. During this phase, developers code the application logic and presentation layers.
Using Oracle Application Development Framework (Oracle ADF), developers can make use of Oracle ADF's built-in support for a range of security features.
For details, see:
-
Enabling ADF Security in a Fusion Web Application in the Oracle Fusion Middleware Fusion Developer's Guide for Oracle Application Development Framework
Oracle Enterprise Manager Fusion Middleware Control
Fusion Middleware Control is a JMX-based GUI management tool provided as part of Oracle Enterprise Manager.
An identity store is a trusted store where user identities (users and groups) are kept.
In Oracle Fusion Middleware 11g Release 1 (11.1.1), the default identity store is an embedded LDAP store maintained in the Oracle WebLogic Server process suitable for testing and small-scale deployments only. Enterprise LDAP servers (Oracle Internet Directory and third-party LDAP directories) are also supported.
See Section 2.3.1, "Authentication" for related information.
The infrastructure refers to the full range of system software required to deploy an application. Infrastructure hardening is the process of applying security to each component of the infrastructure, including web servers, application servers, identity and access management solutions, and database systems. Infrastructure hardening is the basis for end-to-end security across the multiple infrastructure components involved in a transaction.
Note:
In the context of securing Oracle WebLogic Server, this task is referred to as "lockdown." However, in the broader context of Oracle Fusion Middleware, it is referred to as infrastructure hardening.See Also:
The WebLogic Security Service provides a powerful and flexible set of software tools for securing the subsystems and applications that run on a server instance. For details, see Oracle Fusion Middleware Developing Web Applications, Servlets, and JSPs for Oracle WebLogic ServerJava Authentication and Authorization Service (JAAS)
JAAS can be used for two purposes:
-
for authentication of users, to reliably and securely determine who is currently executing Java code, regardless of whether the code is running as an application, an applet, a bean, or a servlet; and
-
for authorization of users to ensure they have the access control rights (permissions) required to do the actions performed.
For details, see the Java Authentication and Authorization Service (JAAS) Reference Guide at:
http://java.sun.com/javase/6/docs/technotes/guides/security//jaas/JAASRefGuide.html
A Java component is a peer of a system component, and is managed by the application server container. Examples include Oracle SOA Suite and Oracle Identity Federation.
Objects necessary for SSL communication, including private keys, digital certificates, and trusted CA certificates are stored in keystores.
Oracle Fusion Middleware provides two types of keystores for keys and certificates:
-
JKS-based keystore and truststore, the default JDK implementation of Java keystores provided by Sun Microsystems. JKS keystores are used for Oracle Virtual Directory and other products.
-
Oracle wallet, a container for PKCS#12-based credentials. Oracle wallets are used for Oracle Internet Directory and other products.
For more information, see Section 4.2, "Keystores".
Oracle Application Development Framework (ADF)
Oracle Application Development Framework (Oracle ADF) is an innovative, comprehensive Java EE development framework that is directly supported and enabled by the Oracle JDeveloper 11g development environment.
Oracle ADF simplifies Java EE development by minimizing the need to write code that implements the application's infrastructure, allowing the users to focus on the features of the actual application. Oracle ADF provides these infrastructure implementations as part of the framework. To recognize a set of runtime services is not enough, Oracle ADF is also focused on the development experience to provide a visual and declarative approach to Java EE development through the Oracle JDeveloper 11g development tool.
Oracle ADF is based upon Oracle Platform Security Services.
Oracle Access Manager provides a full range of identity administration and security functions that include Web single sign-on; user self-service and self-registration; sophisticated workflow functionality; auditing and access reporting; policy management; dynamic group management; and delegated administration.
Oracle Adaptive Access Manager
Rapid growth in online commerce has brought increasing sophistication of internet fraud. Threats from Phishing, Pharming, Trojans, Key Logging, and Proxy Attacks, combined with regulations and mandates (such as FFIEC, HIPAA, PCI) governing online data privacy, place online security at a premium.
Oracle Adaptive Access Manager provides superior protection for businesses and their customers through strong yet easy-to-deploy multifactor authentication and proactive, real-time fraud prevention.
Oracle Entitlements Server is a fine-grained entitlements management solution that externalizes and centralizes administration of enterprise entitlements, simplifies authorization policies, and enforces security decisions in distributed, heterogeneous applications.
Oracle Entitlements Server secures access to application resources and software components (such as URLs, EJBs, and JSPs) as well as arbitrary business objects (such as customer accounts or patient records). Oracle Entitlements Server policies specify which users, groups, and/or roles can access application resources, allowing those roles to be dynamically resolved at runtime.
Through a unique, flexible architecture, Oracle Entitlements Server can also evaluate specialized attributes to make further, more granular access control decisions. Oracle Entitlements Server's stand-alone administration service manages and distributes complex entitlements policies to policy decision and enforcement points.
These decision points may run in a centralized mode or they can be embedded within an application - an approach that ensures maximum flexibility and high performance authorizations for business critical applications.
Oracle Identity Federation is an industry-leading federation solution providing a self-contained and flexible multi-protocol federation server that can be rapidly deployed with your existing identity and access management systems. Support for leading standards-based protocols ensures interoperability to share identities across vendors, customers, and business partners without the increased costs of managing, maintaining, and administering additional identities and credentials.
Oracle Identity Manager is a best-in-class user provisioning and administration solution that automates the process of adding, updating, and deleting user accounts from applications and directories; and improves regulatory compliance by providing granular reports and attestation support to report and certify user access.
Oracle Platform Security Services (OPSS)
Oracle Platform Security Services (OPSS) provides enterprise product development teams, systems integrators (SIs), and independent software vendors (ISVs) with a standards-based, portable, integrated, enterprise-grade security framework for Java Standard Edition (Java SE) and Java Enterprise Edition (Java EE) applications.
OPSS provides an abstraction layer in the form of standards-based application programming interfaces (APIs) that insulate developers from security and identity management implementation details. In-house developed applications, third-party applications, and integrated applications all benefit from the same uniform security, identity management, and audit services across the enterprise.
When they leverage OPSS, developers do not need to know the details of cryptographic key management or interfaces with user repositories and other identity management infrastructures.
Oracle Web Services Manager is a comprehensive solution for adding policy-driven best practices to all your existing or new Web services and provides the key security and management capabilities necessary to deploy Service-Oriented Architectures across your line-of-business applications.
Oracle Web Services Manager allows IT management to centrally define policies that govern Web services operations (such as access policy, logging policy, and load balancing), then wrap these policies around Web services without needing to modify those services.
Oracle Web Services Manager collects monitoring statistics to ensure quality of service, uptime, and security threats and displays them in a Web dashboard.
An Oracle wallet is a container that stores credentials such as certificates, trusted certificates, certificate requests, and private keys. You can store Oracle wallets on the file system or in LDAP directories such as Oracle Internet Directory. Oracle wallets can be auto-login or password-protected wallets.
You use an Oracle wallet for the following components:
-
Oracle HTTP Server
-
Oracle Web Cache
-
Oracle Internet Directory
A partner application is an Oracle Application Server-based application or a non-Oracle application that delegates the authentication function to the Oracle Single Sign-On server. A partner application is responsible for determining whether a user authenticated by Oracle Single Sign-On is authorized to use the application. Examples of partner applications include Oracle Portal, Oracle Discoverer, and Oracle Delegated Administration Services.
Security Assertions Markup Language (SAML)
Single sign-on enables a user to authenticate once and gain access to several applications without the need to re-authenticate.
A system component is a manageable process that is not Oracle WebLogic Server. Examples include Oracle HTTP Server and Oracle Internet Directory.
Web services security includes authentication and authorization (described above) as well as confidentiality and privacy (keeping information secret), and integrity / non repudiation (making sure that a message remains unaltered during transit by having an authority digitally sign that message; a digital signature also validates the sender and provides a time stamp ensuring that a transaction can't be later repudiated by either the sender or the receiver). Web services security requirements are supported by industry standards both at the transport level (Secure Socket Layer) and at the application level relying on XML frameworks, for example XML encryption, XML signature, and Security Assertion Markup Language (SAML).
eXtensible Access Control Markup Language (XACML)
XACML is a declarative standard for languages that specify both access control policy and access control request/response requirements.
1.2 Scope of Security in Oracle Fusion Middleware
By Oracle Fusion Middleware security, we mean the full range of security options available to applications throughout their life cycle in 11g Release 1 (11.1.1). At the outset it is important to note that, beginning with this release, Oracle WebLogic Server is the application server for Oracle Fusion Middleware. Existing users can continue to use the security facilities provided by Oracle WebLogic Server, using the same configuration tools as before.
Oracle WebLogic Server security is unchanged in 11g Release 1 (11.1.1) and customers can use existing Oracle WebLogic Server tools for managing base container/JavaEE security.
See Also:
Chapter 5, "Common Security Scenarios and Tasks" for more information about the different security options in Oracle Fusion Middleware.1.2.1 About Authentication and Single Sign-On
Oracle Fusion Middleware supports a range of authentication and single sign-on (SSO) options, including:
-
Authentication Providers
An authentication provider allows Oracle WebLogic Server to establish trust by validating a user.
-
An identity assertion provider is a type of authentication provider that handles perimeter-based authentication and multiple security protocols and token types.
-
Identity Stores
See "Identity Store" for information.
-
Support for 10g Oracle Single Sign-On and 10g Oracle Access Manager.
Note:
Oracle Access Manager is the preferred solution. For more information, see Section 5.1, "Single Sign-On".Oracle WebLogic Server contains authentication providers for both of these products.
1.2.2 About Oracle Platform Security Services
As noted earlier (see Section 1.1, "Terminology"), Oracle Platform Security Services (OPSS) provides a standards-based, portable, integrated, enterprise-grade security framework for Java Standard Edition (Java SE) and Java Enterprise Edition (Java EE) applications.
OPSS provides security services to both Oracle WebLogic Server and such Oracle components as:
-
Oracle SOA Suite
-
Oracle WebCenter
-
Oracle Entitlement Server
-
Oracle Web Services Manager
OPSS incorporates the Security Service Provider Interfaces for Oracle WebLogic Server, and Oracle's 10g security framework, referred to as Java Platform Security (JPS).
For details, see Chapter 2, "About Oracle Platform Security Services".
1.2.3 About Security for Oracle SOA Suite
Oracle SOA Suite relies primarily on the security features of Oracle WebLogic Server and Oracle Fusion Middleware. For example, you enable Secure Socket Layer (SSL) on Oracle SOA Suite connections into Oracle WebLogic Server by using the Oracle WebLogic Server Administration Console to configure listeners.
In addition, here are some suite-specific aspects of security:
-
-
Two-way SSL
-
SSL between Oracle SOA Suite and Oracle HTTP Server
-
automatic authentication when accessing a second Oracle BPM Worklist from a first Oracle BPM Worklist in Security Assertion Markup Language (SAML) SSO environments
-
automatic authentication of Oracle BPM Worklist users in Windows native authentication environment through Kerberos
-
-
Securing Oracle Business Activity Monitoring
-
Credential Mapping
-
Oracle BAM User Permissions
-
Oracle Internet Directory with Oracle BAM
-
-
Securing Oracle User Messaging Service
-
Secure storage of sensitive driver properties like passwords in the credential store
-
transport-level security using SSL
-
For details, see the Oracle Fusion Middleware Administrator's Guide for Oracle SOA Suite.
1.2.4 About Security for Oracle WebCenter
Besides the application layer, Oracle WebCenter supports four security layers:
-
The WebCenter Spaces application supports:
-
Application role management and privilege mapping
-
Self-registration
-
Group Space security management
-
Account and password management
-
-
The WebCenter Security Framework supports:
-
Service Security Extension Framework
-
Permission- and Role-mapping-based authorization
-
External applications and credential mapping
-
-
ADF Security supports:
-
Page and task flow authorization
-
Secure connection management
-
Credential mapping APIs
-
-
Oracle Platform Security Services (OPSS) supports:
-
Anonymous-role and Authenticated-role support
-
Identity store, policy store, and credential store
-
Identity Management Services
-
Oracle Web Services Manager Security
-
For details, see Managing Security in the Oracle Fusion Middleware Administrator's Guide for Oracle WebCenter.
1.3 Oracle Fusion Middleware and the Three-Tier Architecture
Security can be defined as controlled access to the Oracle Fusion Middleware infrastructure and/or to enterprise applications built upon that infrastructure.
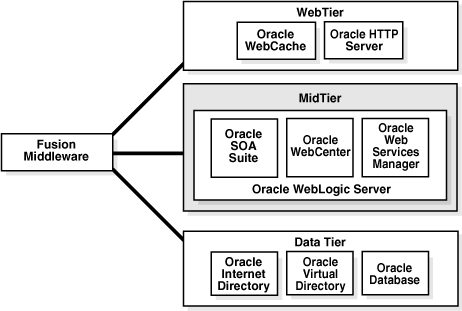
Figure 1-1 shows how Oracle Fusion Middleware supports the classic three-tier enterprise environment:
In this model:
-
The Web tier consists of components like WebCache and Oracle HTTP Server, which protect resources and control access to applications.
-
The Middle tier runs Oracle WebLogic Server, which hosts the security Service Provider Interfaces (SPIs) and APIs. Oracle Fusion Middleware components such as Oracle SOA Suite, Oracle WebCenter, and Oracle Web Services Manager operate in the middle tier.
See Also :
Section 2.1.2, "How Applications Can Use Oracle Platform Security Services" for a description of the SPI model. -
The data tier is the repository for LDAP directories and databases, such as Oracle Internet Directory, Oracle Virtual Directory, and Oracle Database.
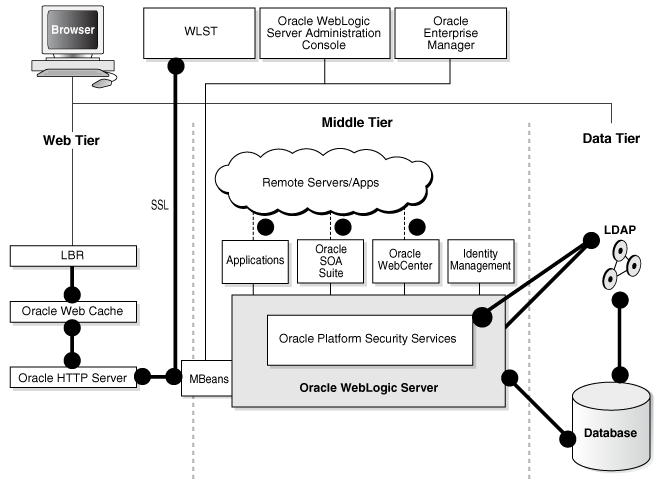
The following diagram is a high-level overview of the major elements of security in Oracle Fusion Middleware:
This figure shows the elements of security in Oracle Fusion Middleware: the Web tier on the left contains load balancers and other components outside the firewall; the middle tier hosts Oracle WebLogic Server and its applications; and on the right, the Data tier contains databases and directories. Different administration tools are shown at the top of the figure.
Key elements of this architecture are as follows:
-
Fusion Middleware Control, GUI-based administration tool for Oracle Fusion Middleware. You use Fusion Middleware Control to configure, manage and monitor components and applications, and to implement security for these components:
-
Oracle HTTP Server
-
Oracle Web Cache
-
Oracle Internet Directory
-
Oracle Virtual Directory
-
-
Oracle WebLogic Server is the application server for Oracle Fusion Middleware components such as Oracle SOA Suite, Oracle Identity Management, Oracle WebCenter, and applications developed by customers, system integrators, and third-party vendors.
-
The circles represents listeners that can be SSL-enabled for secure communication
For details, see Chapter 4, "Infrastructure Hardening".
1.3.1 Tools for Managing Oracle Fusion Middleware
Oracle Fusion Middleware contains these graphical and command-line runtime tools:
-
Oracle WebLogic Server Administration Console enables you to configure Oracle WebLogic Server domains and JavaEE applications running on the server
-
Fusion Middleware Control enables you to configure Oracle applications running on the server, and to leverage security features that rely on the OPSS APIs.
-
The Oracle WebLogic Scripting Tool (
WLST) is a command-line scripting environment that you can use to create, manage, and monitor WebLogic Server domains, and administer Oracle Fusion Middleware security features -
Oracle Business Intelligence Publisher enables you to view audit reports