


|

|
|
|
|
This chapter describes the task of administering services across multiple Domains by using the BEA TUXEDO Domains feature. For information about configuring WebLogic Enterprise domains, refer to Configuring Multiple Domains (WLE Systems).
This chapter discusses the following topics:
Using Domains provides the following benefits:
Benefits of Using BEA TUXEDO System Domains
All domain configuration information is stored in a binary file, called the BDMCONFIG
file. You can create and edit the domain gateway configuration file (DMCONFIG
file), with any UNIX text editor. You can update the compiled BDMCONFIG
file while the system is running by using the dmadmin
(1) command when using Domains. There must be one BDMCONFIG
file per BEA TUXEDO application.
A BEA TUXEDO system domain gateway is a server supplied by the BEA TUXEDO system that enables access to and from remote domains. Domains provides a gateway administrative server (GWADM
) that enables run-time administration of the Domains gateway group, and a Domains administrative server (DMADM
) that enables run-time administration of the Domains configuration information (BDMCONFIG
). You enable remote domain access by specifying a gateway group and a domain administration group in the GROUPS
section of the TUXCONFIG
file, and by adding entries for the gateway and the two administrative servers in the SERVERS
section.
In Figure 10-1, DGW
is the domain gateway; GWADM
is the gateway administrative server; DMADM
is the Domains administrative server; and BDMCONFIG
is the Domains gateway configuration file.
The following table describes the sections of the DMCONFIG
file.
What is the domains gateway configuration file?
Figure 10-1 BEA TUXEDO Domains Gateway

Components of the DMCONFIG File
To configure a local domain and a remote domain, perform the following tasks:
Configuring Local and Remote Domains
You need to set the following environment variables for the application to be configured successfully:
Setting Environment Variables
On AIX, LIBPATH
must be set instead of LD_LIBRARY_PATH
. On HP UX, SHLIB_PATH
must be set instead of LD_LIBRARY_PATH
. On NT, no variable for shared libraries is required.
$ TUXDIR=/opt/tuxedo $ PATH=$TUXDIR/bin:$PATH $ LD_LIBRARY_PATH=$TUXDIR/lib:$LD_LIBRARY_PATH $ export TUXDIR PATH LD_LIBRARY_PATH Build a local application configuration file using tmloadcf
(1), and a local domain gateway configuration file using dmloadcf
(1). The local application configuration file (lapp.ubb
) contains the information necessary to boot the local application. This file is compiled into a binary data file (lapp.tux
), using tmloadcf
(1).
The local domain gateway configuration file (lapp.dom
) contains the information used by domain gateways for communications with other domains. This file is compiled into a binary data file (lapp.bdm
), using dmloadcf
(1).
$ cd /home/lapp $ TUXCONFIG=/home/lapp/lapp.tux; export TUXCONFIG $ tmloadcf -y lapp.ubb $ BDMCONFIG=/home/lapp/lapp_bdm; export BDMCONFIG $ dmloadcf -y lapp.dom $ tmboot -y Build a remote application configuration file and a remote domain gateway configuration file. The remote application configuration file (rapp.ubb
) contains the information used by domain gateways for communication with other domains. This file is compiled into a binary data file (rapp.tux
).
The remote domain gateway configuration file (rapp.dom
) contains the information used by domain gateways to initialize the context required for communications with other domains. This configuration file is similar to the local domain gateway configuration file. The difference is in which services are exported and imported. This file is compiled into a binary data file (rapp.bdm
).
$ cd /home/rapp $ TUXCONFIG=/home/rapp/rapp.tux; export TUXCONFIG $ tmloadcf -y rapp.ubb $ BDMCONFIG=/home/rapp/rapp_bdm; export BDMCONFIG $ dmloadcf -y rapp.dom $ tmboot -y Once you create both the local and remote domains, you can then boot the application using tmboot
(1). The order in which the two domains are booted does not matter. Monitor the applications with dmadmin
(1).
Once both applications are booted, a client in the local application can call the TOUPPER
service residing in the remote application.
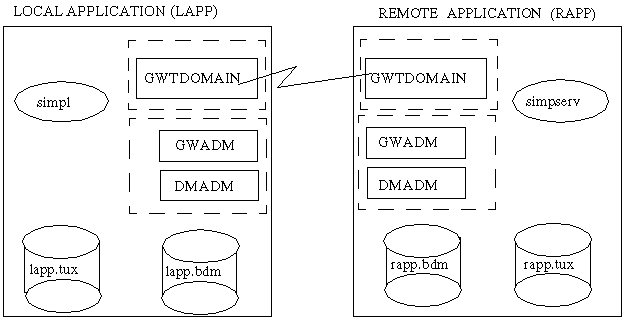
The Domains example illustrated in the following figure and throughout this chapter consists of two applications, both of which are based on the Simpapp
example provided with the BEA TUXEDO system. The first application is called lapp
for "local application;" the second application is called rapp
for "remote application." lapp
is configured to allow its clients to access a service called TOUPPER
, which is advertised in rapp
.A Local and a Remote Application (simpapp)
For the sample local application configuration file (lapp.ubb
) shown in Listing 10-1, only the required parameters are defined. Default settings are used for the other parameters.
The following two server groups are defined:
Example
Building a Local Application Configuration File and a Local Domains Gateway Configuration File
Building a Remote Application Configuration File and a Remote Domains Gateway Configuration File
Example of a Domains-based Configuration
Defining the Local Domains Environment
The following three servers are defined:
Listing 10-1 Example of a Local Application Configuration File
# lapp.ubb
#
*RESOURCES
IPCKEY 111111
MASTER LAPP
MODEL SHM
*MACHINES
giselle
LMID=LAPP
TUXDIR="/opt/tuxedo"
APPDIR="/home/lapp"
TUXCONFIG="/home/lapp/lapp.tux"
*GROUPS
LDMGRP GRPNO=1 LMID=LAPP
LGWGRP GRPNO=2 LMID=LAPP
*SERVERS
DMADM SRVGRP=LDMGRP SRVID=1
GWADM SRVGRP=LGWGRP SRVID=1
GWTDOMAIN SRVGRP=LGWGRP SRVID=2 REPLYQ=N
*SERVICES
For the sample local domain gateway configuration file (lapp.dom
), shown in Listing 10-2, only the required parameters are defined. Default settings are used for the other parameters.
The DM_LOCAL_DOMAIN
section identifies the local domains and their associated gateway groups. This section has one entry (LAPP
) and specifies the parameters required for the domain gateway processes in that group, as follows:
Defining the Local and Remote Domains, Addressing, and Imported and Exported Services
The DM_REMOTE_DOMAINS
section identifies the known set of remote Domains and their characteristics. This section has one entry (RAPP
). TYPE
is used to classify the type of Domains. DomainsID
is a unique domain identifier.
The DM_TDOMAIN
section defines the addressing information required by the BEA TUXEDO Domains feature. Following are entries in the section for each local and remote domain specified in this configuration file:
The DM_LOCAL_SERVICES
section provides information about the services that are exported. This section has no entries because no services are being exported.
The DM_REMOTE_SERVICES
section provides information about the services that are imported. The TOUPPER
service is imported so that it can be accessed by clients in the local domains.
Listing 10-2
Example of a Local Domains Gateway Configuration File
# LAPP GWGRP=LGWGRP *DM_REMOTE_DOMAINS RAPP TYPE=TDOMAIN *DM_TDOMAIN LAPP NWADDR="//mach1:5000" RAPP NWADDR="//mach2:5000" *DM_LOCAL_SERVICES *DM_REMOTE_SERVICES TOUPPER
# lapp.dom
#
*DM_LOCAL_DOMAINS
TYPE=TDOMAIN
DOMAINID="111111"
DOMAINID="222222"
For the sample remote application configuration file (rapp.ubb ), shown in Listing 10-3, only the required parameters are defined. Default settings are used for the other parameters.
The following three server groups are defined:
The following four servers are defined:
Listing 10-3 Example of a Remote Application Configuration File
# rapp.ubb
#
*RESOURCES
IPCKEY 222222
MASTER RAPP
MODEL SHM
*MACHINES
juliet
LMID=RAPP
TUXDIR="/opt/tuxedo"
APPDIR="/home/rapp"
TUXCONFIG="/home/rapp/rapp.tux"
*GROUPS
RDMGRP GRPNO=1 LMID=RAPP
RGWGRP GRPNO=2 LMID=RAPP
APPGRP GRPNO=3 LMID=RAPP
*SERVERS
DMADM SRVGRP=RDMGRP SRVID=1
GWADM SRVGRP=RGWGRP SRVID=1
GWTDOMAIN SRVGRP=RGWGRP SRVID=2 REPLYQ=N
simpserv SRVGRP=APPGRP SRVID=1
*SERVICES
TOUPPER
For the sample remote domain gateway configuration file (rapp.dom
), shown in Listing 10-4, only the required parameters are defined. Default settings are used for the other parameters.
This configuration file is similar to the local domain gateway configuration file. The difference is in which services are exported and imported.
The DM_LOCAL_SERVICES
section provides information about the services exported by each local domain. In this example, the TOUPPER
service is exported and included in the DM_LOCAL_SERVICES
section. No service is imported so there are no entries in the DM_REMOTE_SERVICES
section.
Listing 10-4
Example of a Remote Domains Gateway Configuration File
# rapp.dom *DM_LOCAL_DOMAINS RAPP GWGRP=RGWGRP *DM_REMOTE_DOMAINS LAPP TYPE=TDOMAIN *DM_TDOMAIN RAPP NWADDR="//mach2:5000" LAPP NWADDR="//mach1:5000" *DM_LOCAL_SERVICES Defining the Exported Services
#
TYPE=TDOMAIN
DOMAINID="222222"
DOMAINID="111111"
TOUPPER
*DM_REMOTE_SERVICES
Data compression is useful in most applications and vital to supporting large configurations. When data is sent between Domains, you can elect to compress it for faster performance. This is configured by setting the CMPLIMIT parameter in the dmconfig (5). See Building Networked Applications, for more information on data compression.
Because Domains can exist under diverse ownership, multiple ways are offered to enable you to provide sufficient security:
To create a domain ACL, you must specify the name of the domain ACL and a list of the remote domains that are part of the list (the Domain Import List) in the DM_ACCESS_CONTROL
section of the DMCONFIG
file. The following chart describes these two fields.
Creating a Domain Access Control List (ACL)
Information for data-dependent routing used by gateways to route service requests (to specific remote domains) is provided in the DM_ROUTING
section of the DMCONFIG
file. The FML32
, VIEW32
, FML
, VIEW
, X_C_TYPE
, and X_COMMON
typed buffers are supported. To create a routing table for a domain, you must specify the buffer type for which the routing entry is valid, the name of the routing entry and field, and the ranges and associated remote domain names of the routing field. The following table describes these fields.
Routing Service Requests to Remote Domains

|
|
|
Copyright © 1999 BEA Systems, Inc. All rights reserved.
|