4 Server Administration
This chapter describes tasks related to day-to-day administration of Oracle Identity Federation, and additional tasks that the administrator may need to perform on occasion. It contains these topics:
4.1 Basic Administration
This section describes basic administration of Oracle Identity Federation. It contains these topics:
4.1.1 About the Federation Server Administrator
The Oracle Identity Federation administrator performs two major tasks, which can be characterized as:
-
Basic runtime administration of the server, including starting, stopping, and monitoring the server
-
Federated identity administration, which involves user administration (user creation, deletion, and federation), and maintaining information about trusted providers and the users affiliated with those providers
This section contains these topics:
4.1.1.1 About Roles
Oracle WebLogic Server defines certain global roles in the security realm that it installs, including:
-
Admin (includes the Administrators group by default)
-
Operator (includes the Operators group by default)
-
Monitor (includes the Monitors group by default)
See Also:
Users, Groups, And Security Roles in Oracle Fusion Middleware Securing Resources Using Roles and Policies for Oracle WebLogic Server.The domain administrator can create the FederationAdmin role to grant Oracle Identity Federation administrator access to non-Admin/Operator/Monitor users.
Note:
The FederationAdmin role is recognized only byWLST commands and other JMX MBean clients, not by Fusion Middleware Control. This means that users with the FederationAdmin role will only be able to configure Oracle Identity Federation through WLST or other JMX clients, not through Fusion Middleware Control.4.1.1.2 Deployment Planning
When deploying Oracle Identity Federation in a network of trusted sources and destinations, you will need to exchange information with other site administrators, and configure identity providers and service providers accordingly.
See Also:
-
Chapter 5, "Configuring Oracle Identity Federation" for details about server properties
-
Section 4.3, "Managing Identity Federations" for details about trusted provider information
In a federated environment, at the simplest level the service provider acts as a consumer of identity information, while the identity provider (where the user request originated) acts as the supplier of identity information. The identity provider may, in turn, adopt a consumer role as it communicates with an authentication and authorization mechanism (an AAA system) to obtain the necessary credentials. Service providers may also want to map users to identities at the destination, although this is not a requirement. Identity suppliers and consumers must be able to achieve a runtime exchange of data, which results in the source asserting some identity information about the principal which the destination can trust as a means of uniquely identifying the principal.
As an identity provider, you may wish to work with partner site administrators to provide the relevant lists of users from your domain. This is an optional information exchange.
Oracle Identity Federation can produce and consume provider metadata that conforms to the Liberty metadata specifications and to the SAML 2.0 metadata specifications. Additionally, Oracle Identity Federation supports the ability to import provider metadata that uses the metadata extensions for SAML 2.0 query requesters.
You will need to establish cross-domain trust by setting up authentication and exchanging keys or certificates among the network of trusted sources and destinations.
For initial setup and testing, identity providers and service providers can both use default self-signed certificates. When going into production, however, consider the usage type when deciding whether self-signed certificates are sufficient: CA-issued certificates are most useful when there is no prior trust relation between entities, for example, when you use SSL to access a web site over the Internet. But given that the trust relationship between federation peers requires the exchange of metadata or the equivalent, which can and usually does include the peer certificates, self-signed certificates should be sufficient for production deployment so long as you can trust how you obtained the peer certificates. Note that CA-issued certificates might be used in the metadata exchange, for example signed e-mail or a download from a web server over SSL.
The process of setting up cross-domain trust can be simplified by the use of metadata. Oracle Identity Federation enables you to store provider-specific metadata which overrides global IdP and SP settings with data specific to communication with each peer provider.
Oracle Identity Federation provides secure communication using X.509 certificate authentication.
Oracle Identity Federation provides encryption for data integrity using public key cryptography, a technique that uses a public and private key pair. Data is signed with a sending party's private key and the signature is verified by the recipient using the sender's public key.
Oracle Identity Federation uses documents known as certificates to enable peer providers to establish trust. A Certificate Authority (CA) issues a certificate to vouch for a user's identity, including the party's public key in the certificate for use by the receiving party.
You configure key pairs and certificates using a local keystore. The identity provider configures a public and private key pair and a certificate - providing validation of the public key from a Certificate Authority (CA) - when using the POST profile. The presentation of the public key by the IdP, and certificate import by the SP, are critical aspects in managing the trust relationship between partners.
You can also implement SSL connections. For details on how to configure SSL connections and client certificates, see Section 8.2, "Configuring SSL for Oracle Identity Federation".
Note:
SSL functionality is external to Oracle Identity Federation.4.1.1.3 Other Planning Tasks
Besides exchanging identities and securing communications involving those identities, parties that plan to engage in a federated network must agree on a range of additional topics, such as:
-
federation protocols
-
services
-
profiles
You will need to work with others in your network to ensure that the various IdPs and SPs understand their business partners' setups in order for federation to work properly.
4.1.2 Administering Oracle Identity Federation
You administer the Oracle Identity Federation server using the management tools in Oracle Fusion Middleware. See the following sections of the Oracle Fusion Middleware Administrator's Guide for details:
-
Getting Started Using Oracle Enterprise Manager Fusion Middleware Control
-
Getting Started Using Command-Line Tools
-
Using the Fusion Middleware Control MBean Browsers
4.1.3 Oracle Identity Federation Log Files
Oracle Identity Federation log files are maintained in the $DOMAIN_HOME/servers/servername/logs directory and provide useful information for managing and monitoring server instances. The log files include:
Table 4-1 Oracle Identity Federation Log Files
| Log File Name | Description |
|---|---|
|
servername |
Contains the runtime log records for the Oracle Identity Federation server. |
Note:
In prior releases, SAML messages exchanged between providers were maintained infederation-msg.log. This log file no longer exists; these messages are now audited and available in the Fusion Middleware Audit Framework.4.1.4 Backups
You should back up your configurations/systems with the tools that you normally employ to back up your systems on a daily basis.
For more information about this topic, see Advanced Administration: Backup and Recovery in the Oracle Fusion Middleware Administrator's Guide.
Use this backup regimen:
-
Use the backup/restore system tools on window platforms.
-
Back up everything on all components in the Oracle Identity Federation configuration.
Use this backup regimen:
-
Shut down all Oracle WebLogic Server and Oracle Identity Federation components.
-
Run the
tarcommand on all components, including the Oracle Identity Federation folder under the managed server, and the RDBMS data files that Oracle Identity Federation is using.For example:
tar cvzf oif11_backup oif_folder
4.2 Common Tasks
This section describes common services provided by Oracle Identity Federation for administrators and peer users. It explains these tasks:
4.2.1 Obtain Server Metadata
The Oracle Identity Federation metadata can either be retrieved from Oracle Enterprise Manager Fusion Middleware Control or by directly accessing a URL.
To retrieve the metadata from Fusion Middleware Control:
-
Navigate to Oracle Identity Federation, then Administration, then Security and Trust, then Provider Metadata.
-
Select the provider type and the version of the Oracle Identity Federation metadata to be created.
-
Click Generate.
To get the Oracle Identity Federation IdP metadata, go to a URL of the form:
http://host:port/fed/idp/metadata
To get the Oracle Identity Federation SP metadata, go to a URL of the form:
http://host:port/fed/sp/metadata
The following is a sample of metadata for a server that has SSO Identity Provider, Attribute Authority, Authentication Query and Assertion ID Responder features enabled:
<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" ID="id-PmHsOU3mD8zEyjDo0QbyelE5oxY-" entityID="https://sta00534.us.oracle.com:7002/fed/idp" validUntil="2009-05-24T15:48:15Z">
<md:IDPSSODescriptor WantAuthnRequestsSigned="false" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<md:KeyDescriptor use="signing">
<dsig:KeyInfo xmlns:dsig="http://www.w3.org/2000/09/xmldsig#">
<dsig:X509Data>
<dsig:X509Certificate>MIICIzCCAYygAwIBAgIBJTANBgkqhkiG9w0BAQQFADA1MTMwMQYDVQQDEypzdGEwMDUzNC51cy5vcmFjbGUuY29tIFNpZ25pbmcgQ2VydGlmaWNhdGUwHhcNMDkwMTEzMjMwMTE2WhcNMTAwMTEzMjMwMTE2WjA1MTMwMQYDVQQDEypzdGEwMDUzNC51cy5vcmFjbGUuY29tIFNpZ25pbmcgQ2VydGlmaWNhdGUwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAI7X7J6A057NEBgTnCYussaz6E3IY6JsgAYOiXHfwunEv6zRZnpdVlZIRUyT+NNULSfk+PLbQU/NCg8yQdJeSNYkQ4BId+yyUDcYC447nhHa37uLKM7aWyAXc6AeffC6CSEs0yZltgU2nIxJh9tLhPe5hzf0QjSImyXR/vjS/6nDAgMBAAGjQzBBMA8GA1UdEwEB/wQFMAMBAf8wDwYDVR0PAQH/BAUDAwfwADAdBgNVHQ4EFgQUmZ8T7GkFv2VZB+FogX99DIvodTswDQYJKoZIhvcNAQEEBQADgYEAbMGoZzjo9Bfaua3wiRh3LyMeahdoHv5S67JPAWNXrvQUxKjvYH0QR2oTnD+Rf3hIhi6Tjwy4oP9YrcADiChp8tqckrBnR3L1aEErLXGau6r++a/PwslasuysNfbEoHrGJ1m+3K9DXGYYkGKdKgW9Dgg8MObZshDxd7xUm557QO8=
</dsig:X509Certificate>
<dsig:X509IssuerSerial>
<dsig:X509IssuerName>CN=sta00534.us.oracle.com Signing Certificate</dsig:X509IssuerName>
<dsig:X509SerialNumber>37</dsig:X509SerialNumber>
</dsig:X509IssuerSerial>
<dsig:X509SubjectName>CN=sta00534.us.oracle.com Signing Certificate</dsig:X509SubjectName>
</dsig:X509Data>
</dsig:KeyInfo>
</md:KeyDescriptor>
<md:KeyDescriptor use="encryption">
<dsig:KeyInfo xmlns:dsig="http://www.w3.org/2000/09/xmldsig#">
<dsig:X509Data>
<dsig:X509Certificate>MIICPDCCAeYCEC5V26OFPaoDxzAazNs8UBwwDQYJKoZIhvcNAQEEBQAweTELMAkGA1UEBhMCVVMxEDAOBgNVBAgTB015U3RhdGUxDzANBgNVBAcTBk15VG93bjEXMBUG
A1UEChMOTXlPcmdhbml6YXRpb24xGTAXBgNVBAsTEEZPUiBURVNUSU5HIE9OTFkxEzARBgNVBAMTCkNlcnRHZW5DQUIwHhcNMDgxMTE4MjAwNzE4WhcNMjMxMTE5MjAwNzE4WjCBhTELMAkGA1UEBhMCVVMxEDAOBgNVBAgWB015U3RhdGUxDzANBgNVBAcWBk15VG93bjEXMBUGA1UEChYOTXlPcmdhbml6YXRpb24xGTAXBgNVBAsWEEZPUiBURVNUSU5HIE9OTFkxHzAdBgNVBAMWFnN0YTAwNTM0LnVzLm9yYWNsZS5jb20wgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAMJCDgD00LDSUdWT0SznaU35ZkeQD2Ql6hvtoGcs8MfQpOM/yzM3C9GDlK9+0JpN+7EFGQsCCezFVEX6lMzWdkvdGhbTUJ8/FI32QZ6FPkFItZrnfOS6eDpxcPsnv33rPVQ+ccRvj7BK+sn24PEeV5rt3xF1cGuHGr57t/LtUa01AgMBAAEwDQYJKoZIhvcNAQEEBQADQQAChW8nbopN0FTyZRcVOTZKUlklHXf5X8Xi4gh2OIkkr7q9kjFlfI60SQZoD/nThn1sGZPPbtPGEwRevpqv7cI/
</dsig:X509Certificate>
<dsig:X509IssuerSerial>
<dsig:X509IssuerName>CN=CertGenCAB, OU=FOR TESTING ONLY, O=MyOrganization, L=MyTown, ST=MyState, C=US</dsig:X509IssuerName>
<dsig:X509SerialNumber>61590287842211333696140797217026625564</dsig:X509SerialNumber>
</dsig:X509IssuerSerial>
<dsig:X509SubjectName>CN=sta00534.us.oracle.com, OU=FOR TESTING ONLY, O=MyOrganization, L=MyTown, ST=MyState, C=US</dsig:X509SubjectName>
</dsig:X509Data>
</dsig:KeyInfo>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#rsa-1_5"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes128-cbc"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes192-cbc"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes256-cbc"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#tripledes-cbc"/>
</md:KeyDescriptor>
<md:ArtifactResolutionService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://sta00534.us.oracle.com:7002/fed/idp/soap" index="1" isDefault="true"/>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://sta00534.us.oracle.com:7002/fed/idp/samlv20" ResponseLocation="https://sta00534.us.oracle.com:7002/fed/idp/samlv20"/>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://sta00534.us.oracle.com:7002/fed/idp/samlv20" ResponseLocation="https://sta00534.us.oracle.com:7002/fed/idp/samlv20"/>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST-SimpleSign" Location="https://sta00534.us.oracle.com:7002/fed/idp/samlv20ss" ResponseLocation="https://sta00534.us.oracle.com:7002/fed/idp/samlv20ss"/>
<md:ManageNameIDService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://sta00534.us.oracle.com:7002/fed/idp/samlv20" ResponseLocation="https://sta00534.us.oracle.com:7002/fed/idp/samlv20"/>
<md:ManageNameIDService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://sta00534.us.oracle.com:7002/fed/idp/samlv20" ResponseLocation="https://sta00534.us.oracle.com:7002/fed/idp/samlv20"/>
<md:ManageNameIDService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST-SimpleSign" Location="https://sta00534.us.oracle.com:7002/fed/idp/samlv20ss" ResponseLocation="https://sta00534.us.oracle.com:7002/fed/idp/samlv20ss"/>
<md:ManageNameIDService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://sta00534.us.oracle.com:7002/fed/idp/soap"/>
<md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:persistent</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:transient</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:X509SubjectName</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat>
<md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://sta00534.us.oracle.com:7002/fed/idp/samlv20"/>
<md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://sta00534.us.oracle.com:7002/fed/idp/samlv20"/>
<md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST-SimpleSign" Location="https://sta00534.us.oracle.com:7002/fed/idp/samlv20ss"/>
<md:AssertionIDRequestService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://sta00534.us.oracle.com:7002/fed/idp/soap"/>
<md:AssertionIDRequestService Binding="urn:oasis:names:tc:SAML:2.0:bindings:URI" Location="https://sta00534.us.oracle.com:7002/fed/idp/assertionid"/>
</md:IDPSSODescriptor>
<md:AuthnAuthorityDescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<md:KeyDescriptor use="signing">
<dsig:KeyInfo xmlns:dsig="http://www.w3.org/2000/09/xmldsig#">
<dsig:X509Data>
<dsig:X509Certificate>MIICIzCCAYygAwIBAgIBJTANBgkqhkiG9w0BAQQFADA1MTMwMQYDVQQDEypzdGEwMDUzNC51cy5vcmFjbGUuY29tIFNpZ25pbmcgQ2VydGlmaWNhdGUwHhcNMDkwMTEzMjMwMTE2WhcNMTAwMTEzMjMwMTE2WjA1MTMwMQYDVQQDEypzdGEwMDUzNC51cy5vcmFjbGUuY29tIFNpZ25pbmcgQ2VydGlmaWNhdGUwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAI7X7J6A057NEBgTnCYussaz6E3IY6JsgAYOiXHfwunEv6zRZnpdVlZIRUyT+NNULSfk+PLbQU/NCg8yQdJeSNYkQ4BId+yyUDcYC447nhHa37uLKM7aWyAXc6AeffC6CSEs0yZltgU2nIxJh9tLhPe5hzf0QjSImyXR/vjS/6nDAgMBAAGjQzBBMA8GA1UdEwEB/wQFMAMBAf8wDwYDVR0PAQH/BAUDAwfwADAdBgNVHQ4EFgQUmZ8T7GkFv2VZB+FogX99DIvodTswDQYJKoZIhvcNAQEEBQADgYEAbMGoZzjo9Bfaua3wiRh3LyMeahdoHv5S67JPAWNXrvQUxKjvYH0QR2oTnD+Rf3hIhi6Tjwy4oP9YrcADiChp8tqckrBnR3L1aEErLXGau6r++a/PwslasuysNfbEoHrGJ1m+3K9DXGYYkGKdKgW9Dgg8MObZshDxd7xUm557QO8=
</dsig:X509Certificate>
<dsig:X509IssuerSerial>
<dsig:X509IssuerName>CN=sta00534.us.oracle.com Signing Certificate</dsig:X509IssuerName>
<dsig:X509SerialNumber>37</dsig:X509SerialNumber>
</dsig:X509IssuerSerial>
<dsig:X509SubjectName>CN=sta00534.us.oracle.com Signing Certificate</dsig:X509SubjectName>
</dsig:X509Data>
</dsig:KeyInfo>
</md:KeyDescriptor>
<md:KeyDescriptor use="encryption">
<dsig:KeyInfo xmlns:dsig="http://www.w3.org/2000/09/xmldsig#">
<dsig:X509Data>
<dsig:X509Certificate>MIICPDCCAeYCEC5V26OFPaoDxzAazNs8UBwwDQYJKoZIhvcNAQEEBQAweTELMAkGA1UEBhMCVVMxEDAOBgNVBAgTB015U3RhdGUxDzANBgNVBAcTBk15VG93bjEXMBUG
A1UEChMOTXlPcmdhbml6YXRpb24xGTAXBgNVBAsTEEZPUiBURVNUSU5HIE9OTFkxEzARBgNVBAMTCkNlcnRHZW5DQUIwHhcNMDgxMTE4MjAwNzE4WhcNMjMxMTE5MjAwNzE4WjCBhTELMAkGA1UEBhMCVVMxEDAOBgNVBAgWB015U3RhdGUxDzANBgNVBAcWBk15VG93bjEXMBUGA1UEChYOTXlPcmdhbml6YXRpb24xGTAXBgNVBAsWEEZPUiBURVNUSU5HIE9OTFkxHzAdBgNVBAMWFnN0YTAwNTM0LnVzLm9yYWNsZS5jb20wgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAMJCDgD00LDSUdWT0SznaU35ZkeQD2Ql6hvtoGcs8MfQpOM/yzM3C9GDlK9+0JpN+7EFGQsCCezFVEX6lMzWdkvdGhbTUJ8/FI32QZ6FPkFItZrnfOS6eDpxcPsnv33rPVQ+ccRvj7BK+sn24PEeV5rt3xF1cGuHGr57t/LtUa01AgMBAAEwDQYJKoZIhvcNAQEEBQADQQAChW8nbopN0FTyZRcVOTZKUlklHXf5X8Xi4gh2OIkkr7q9kjFlfI60SQZoD/nThn1sGZPPbtPGEwRevpqv7cI/
</dsig:X509Certificate>
<dsig:X509IssuerSerial>
<dsig:X509IssuerName>CN=CertGenCAB, OU=FOR TESTING ONLY, O=MyOrganization, L=MyTown, ST=MyState, C=US</dsig:X509IssuerName>
<dsig:X509SerialNumber>61590287842211333696140797217026625564</dsig:X509SerialNumber>
</dsig:X509IssuerSerial>
<dsig:X509SubjectName>CN=sta00534.us.oracle.com, OU=FOR TESTING ONLY, O=MyOrganization, L=MyTown, ST=MyState, C=US</dsig:X509SubjectName>
</dsig:X509Data>
</dsig:KeyInfo>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#rsa-1_5"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes128-cbc"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes192-cbc"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes256-cbc"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#tripledes-cbc"/>
</md:KeyDescriptor>
<md:AuthnQueryService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://sta00534.us.oracle.com:7002/fed/authnauth/soap"/>
<md:AssertionIDRequestService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://sta00534.us.oracle.com:7002/fed/authnauth/soap"/>
<md:AssertionIDRequestService Binding="urn:oasis:names:tc:SAML:2.0:bindings:URI" Location="https://sta00534.us.oracle.com:7002/fed/authnauth/assertionid"/>
<md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:persistent</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:X509SubjectName</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat>
</md:AuthnAuthorityDescriptor>
<md:AttributeAuthorityDescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<md:KeyDescriptor use="signing">
<dsig:KeyInfo xmlns:dsig="http://www.w3.org/2000/09/xmldsig#">
<dsig:X509Data>
<dsig:X509Certificate>MIICIzCCAYygAwIBAgIBJTANBgkqhkiG9w0BAQQFADA1MTMwMQYDVQQDEypzdGEwMDUzNC51cy5vcmFjbGUuY29tIFNpZ25pbmcgQ2VydGlmaWNhdGUwHhcNMDkwMTEzMjMwMTE2WhcNMTAwMTEzMjMwMTE2WjA1MTMwMQYDVQQDEypzdGEwMDUzNC51cy5vcmFjbGUuY29tIFNpZ25pbmcgQ2VydGlmaWNhdGUwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAI7X7J6A057NEBgTnCYussaz6E3IY6JsgAYOiXHfwunEv6zRZnpdVlZIRUyT+NNULSfk+PLbQU/NCg8yQdJeSNYkQ4BId+yyUDcYC447nhHa37uLKM7aWyAXc6AeffC6CSEs0yZltgU2nIxJh9tLhPe5hzf0QjSImyXR/vjS/6nDAgMBAAGjQzBBMA8GA1UdEwEB/wQFMAMBAf8wDwYDVR0PAQH/BAUDAwfwADAdBgNVHQ4EFgQUmZ8T7GkFv2VZB+FogX99DIvodTswDQYJKoZIhvcNAQEEBQADgYEAbMGoZzjo9Bfaua3wiRh3LyMeahdoHv5S67JPAWNXrvQUxKjvYH0QR2oTnD+Rf3hIhi6Tjwy4oP9YrcADiChp8tqckrBnR3L1aEErLXGau6r++a/PwslasuysNfbEoHrGJ1m+3K9DXGYYkGKdKgW9Dgg8MObZshDxd7xUm557QO8=
</dsig:X509Certificate>
<dsig:X509IssuerSerial>
<dsig:X509IssuerName>CN=sta00534.us.oracle.com Signing Certificate</dsig:X509IssuerName>
<dsig:X509SerialNumber>37</dsig:X509SerialNumber>
</dsig:X509IssuerSerial>
<dsig:X509SubjectName>CN=sta00534.us.oracle.com Signing Certificate</dsig:X509SubjectName>
</dsig:X509Data>
</dsig:KeyInfo>
</md:KeyDescriptor>
<md:KeyDescriptor use="encryption">
<dsig:KeyInfo xmlns:dsig="http://www.w3.org/2000/09/xmldsig#">
<dsig:X509Data>
<dsig:X509Certificate>MIICPDCCAeYCEC5V26OFPaoDxzAazNs8UBwwDQYJKoZIhvcNAQEEBQAweTELMAkGA1UEBhMCVVMxEDAOBgNVBAgTB015U3RhdGUxDzANBgNVBAcTBk15VG93bjEXMBUG
A1UEChMOTXlPcmdhbml6YXRpb24xGTAXBgNVBAsTEEZPUiBURVNUSU5HIE9OTFkxEzARBgNVBAMTCkNlcnRHZW5DQUIwHhcNMDgxMTE4MjAwNzE4WhcNMjMxMTE5MjAwNzE4WjCBhTELMAkGA1UEBhMCVVMxEDAOBgNVBAgWB015U3RhdGUxDzANBgNVBAcWBk15VG93bjEXMBUGA1UEChYOTXlPcmdhbml6YXRpb24xGTAXBgNVBAsWEEZPUiBURVNUSU5HIE9OTFkxHzAdBgNVBAMWFnN0YTAwNTM0LnVzLm9yYWNsZS5jb20wgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAMJCDgD00LDSUdWT0SznaU35ZkeQD2Ql6hvtoGcs8MfQpOM/yzM3C9GDlK9+0JpN+7EFGQsCCezFVEX6lMzWdkvdGhbTUJ8/FI32QZ6FPkFItZrnfOS6eDpxcPsnv33rPVQ+ccRvj7BK+sn24PEeV5rt3xF1cGuHGr57t/LtUa01AgMBAAEwDQYJKoZIhvcNAQEEBQADQQAChW8nbopN0FTyZRcVOTZKUlklHXf5X8Xi4gh2OIkkr7q9kjFlfI60SQZoD/nThn1sGZPPbtPGEwRevpqv7cI/
</dsig:X509Certificate>
<dsig:X509IssuerSerial>
<dsig:X509IssuerName>CN=CertGenCAB, OU=FOR TESTING ONLY, O=MyOrganization, L=MyTown, ST=MyState, C=US</dsig:X509IssuerName>
<dsig:X509SerialNumber>61590287842211333696140797217026625564</dsig:X509SerialNumber>
</dsig:X509IssuerSerial>
<dsig:X509SubjectName>CN=sta00534.us.oracle.com, OU=FOR TESTING ONLY, O=MyOrganization, L=MyTown, ST=MyState, C=US</dsig:X509SubjectName>
</dsig:X509Data>
</dsig:KeyInfo>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#rsa-1_5"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes128-cbc"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes192-cbc"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes256-cbc"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#tripledes-cbc"/>
</md:KeyDescriptor>
<md:AttributeService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://sta00534.us.oracle.com:7002/fed/aa/soap"/>
<md:AssertionIDRequestService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://sta00534.us.oracle.com:7002/fed/aa/soap"/>
<md:AssertionIDRequestService Binding="urn:oasis:names:tc:SAML:2.0:bindings:URI" Location="https://sta00534.us.oracle.com:7002/fed/aa/assertionid"/>
<md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:persistent</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:X509SubjectName</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat>
<md:AttributeProfile>urn:oasis:names:tc:SAML:2.0:profiles:attribute:basic</md:AttributeProfile>
</md:AttributeAuthorityDescriptor>
</md:EntityDescriptor>
The following is a sample of metadata for a server that has SSO Service Provider and Attribute Requestor features enabled:
<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" ID="id-f4-F2z4ncIOsHw5w6CkMjneSE7I-" entityID="http://sta00534.us.oracle.com:7499/fed/sp" validUntil="2009-05-24T15:39:48Z">
<md:RoleDescriptor xmlns:query="urn:oasis:names:tc:SAML:metadata:ext:query" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" WantAssertionsSigned="false" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol" xsi:type="query:AttributeQueryDescriptorType">
<md:KeyDescriptor use="signing">
<dsig:KeyInfo xmlns:dsig="http://www.w3.org/2000/09/xmldsig#">
<dsig:X509Data>
<dsig:X509Certificate>MIICIzCCAYygAwIBAgIBJTANBgkqhkiG9w0BAQQFADA1MTMwMQYDVQQDEypzdGEwMDUzNC51cy5vcmFjbGUuY29tIFNpZ25pbmcgQ2VydGlmaWNhdGUwHhcNMDkwMTEzMjMwMTE2WhcNMTAwMTEzMjMwMTE2WjA1MTMwMQYDVQQDEypzdGEwMDUzNC51cy5vcmFjbGUuY29tIFNpZ25pbmcgQ2VydGlmaWNhdGUwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAI7X7J6A057NEBgTnCYussaz6E3IY6JsgAYOiXHfwunEv6zRZnpdVlZIRUyT+NNULSfk+PLbQU/NCg8yQdJeSNYkQ4BId+yyUDcYC447nhHa37uLKM7aWyAXc6AeffC6CSEs0yZltgU2nIxJh9tLhPe5hzf0QjSImyXR/vjS/6nDAgMBAAGjQzBBMA8GA1UdEwEB/wQFMAMBAf8wDwYDVR0PAQH/BAUDAwfwADAdBgNVHQ4EFgQUmZ8T7GkFv2VZB+FogX99DIvodTswDQYJKoZIhvcNAQEEBQADgYEAbMGoZzjo9Bfaua3wiRh3LyMeahdoHv5S67JPAWNXrvQUxKjvYH0QR2oTnD+Rf3hIhi6Tjwy4oP9YrcADiChp8tqckrBnR3L1aEErLXGau6r++a/PwslasuysNfbEoHrGJ1m+3K9DXGYYkGKdKgW9Dgg8MObZshDxd7xUm557QO8=
</dsig:X509Certificate>
<dsig:X509IssuerSerial>
<dsig:X509IssuerName>CN=sta00534.us.oracle.com Signing Certificate</dsig:X509IssuerName>
<dsig:X509SerialNumber>37</dsig:X509SerialNumber>
</dsig:X509IssuerSerial>
<dsig:X509SubjectName>CN=sta00534.us.oracle.com Signing Certificate</dsig:X509SubjectName>
</dsig:X509Data>
</dsig:KeyInfo>
</md:KeyDescriptor>
<md:KeyDescriptor use="encryption">
<dsig:KeyInfo xmlns:dsig="http://www.w3.org/2000/09/xmldsig#">
<dsig:X509Data>
<dsig:X509Certificate>MIICPDCCAeYCEC5V26OFPaoDxzAazNs8UBwwDQYJKoZIhvcNAQEEBQAweTELMAkGA1UEBhMCVVMxEDAOBgNVBAgTB015U3RhdGUxDzANBgNVBAcTBk15VG93bjEXMBUG
A1UEChMOTXlPcmdhbml6YXRpb24xGTAXBgNVBAsTEEZPUiBURVNUSU5HIE9OTFkxEzARBgNVBAMTCkNlcnRHZW5DQUIwHhcNMDgxMTE4MjAwNzE4WhcNMjMxMTE5MjAwNzE4WjCBhTELMAkGA1UEBhMCVVMxEDAOBgNVBAgWB015U3RhdGUxDzANBgNVBAcWBk15VG93bjEXMBUGA1UEChYOTXlPcmdhbml6YXRpb24xGTAXBgNVBAsWEEZPUiBURVNUSU5HIE9OTFkxHzAdBgNVBAMWFnN0YTAwNTM0LnVzLm9yYWNsZS5jb20wgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAMJCDgD00LDSUdWT0SznaU35ZkeQD2Ql6hvtoGcs8MfQpOM/yzM3C9GDlK9+0JpN+7EFGQsCCezFVEX6lMzWdkvdGhbTUJ8/FI32QZ6FPkFItZrnfOS6eDpxcPsnv33rPVQ+ccRvj7BK+sn24PEeV5rt3xF1cGuHGr57t/LtUa01AgMBAAEwDQYJKoZIhvcNAQEEBQADQQAChW8nbopN0FTyZRcVOTZKUlklHXf5X8Xi4gh2OIkkr7q9kjFlfI60SQZoD/nThn1sGZPPbtPGEwRevpqv7cI/
</dsig:X509Certificate>
<dsig:X509IssuerSerial>
<dsig:X509IssuerName>CN=CertGenCAB, OU=FOR TESTING ONLY, O=MyOrganization, L=MyTown, ST=MyState, C=US</dsig:X509IssuerName>
<dsig:X509SerialNumber>61590287842211333696140797217026625564</dsig:X509SerialNumber>
</dsig:X509IssuerSerial>
<dsig:X509SubjectName>CN=sta00534.us.oracle.com, OU=FOR TESTING ONLY, O=MyOrganization, L=MyTown, ST=MyState, C=US</dsig:X509SubjectName>
</dsig:X509Data>
</dsig:KeyInfo>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#rsa-1_5"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes128-cbc"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes192-cbc"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes256-cbc"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#tripledes-cbc"/>
</md:KeyDescriptor>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:X509SubjectName</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat>
<md:NameIDFormat>lastname</md:NameIDFormat>
</md:RoleDescriptor>
<md:SPSSODescriptor AuthnRequestsSigned="true" WantAssertionsSigned="false" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<md:KeyDescriptor use="signing">
<dsig:KeyInfo xmlns:dsig="http://www.w3.org/2000/09/xmldsig#">
<dsig:X509Data>
<dsig:X509Certificate>MIICIzCCAYygAwIBAgIBJTANBgkqhkiG9w0BAQQFADA1MTMwMQYDVQQDEypzdGEwMDUzNC51cy5vcmFjbGUuY29tIFNpZ25pbmcgQ2VydGlmaWNhdGUwHhcNMDkwMTEzMjMwMTE2WhcNMTAwMTEzMjMwMTE2WjA1MTMwMQYDVQQDEypzdGEwMDUzNC51cy5vcmFjbGUuY29tIFNpZ25pbmcgQ2VydGlmaWNhdGUwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAI7X7J6A057NEBgTnCYussaz6E3IY6JsgAYOiXHfwunEv6zRZnpdVlZIRUyT+NNULSfk+PLbQU/NCg8yQdJeSNYkQ4BId+yyUDcYC447nhHa37uLKM7aWyAXc6AeffC6CSEs0yZltgU2nIxJh9tLhPe5hzf0QjSImyXR/vjS/6nDAgMBAAGjQzBBMA8GA1UdEwEB/wQFMAMBAf8wDwYDVR0PAQH/BAUDAwfwADAdBgNVHQ4EFgQUmZ8T7GkFv2VZB+FogX99DIvodTswDQYJKoZIhvcNAQEEBQADgYEAbMGoZzjo9Bfaua3wiRh3LyMeahdoHv5S67JPAWNXrvQUxKjvYH0QR2oTnD+Rf3hIhi6Tjwy4oP9YrcADiChp8tqckrBnR3L1aEErLXGau6r++a/PwslasuysNfbEoHrGJ1m+3K9DXGYYkGKdKgW9Dgg8MObZshDxd7xUm557QO8=
</dsig:X509Certificate>
<dsig:X509IssuerSerial>
<dsig:X509IssuerName>CN=sta00534.us.oracle.com Signing Certificate</dsig:X509IssuerName>
<dsig:X509SerialNumber>37</dsig:X509SerialNumber>
</dsig:X509IssuerSerial>
<dsig:X509SubjectName>CN=sta00534.us.oracle.com Signing Certificate</dsig:X509SubjectName>
</dsig:X509Data>
</dsig:KeyInfo>
</md:KeyDescriptor>
<md:KeyDescriptor use="encryption">
<dsig:KeyInfo xmlns:dsig="http://www.w3.org/2000/09/xmldsig#">
<dsig:X509Data>
<dsig:X509Certificate>MIICPDCCAeYCEC5V26OFPaoDxzAazNs8UBwwDQYJKoZIhvcNAQEEBQAweTELMAkGA1UEBhMCVVMxEDAOBgNVBAgTB015U3RhdGUxDzANBgNVBAcTBk15VG93bjEXMBUG
A1UEChMOTXlPcmdhbml6YXRpb24xGTAXBgNVBAsTEEZPUiBURVNUSU5HIE9OTFkxEzARBgNVBAMTCkNlcnRHZW5DQUIwHhcNMDgxMTE4MjAwNzE4WhcNMjMxMTE5MjAwNzE4WjCBhTELMAkGA1UEBhMCVVMxEDAOBgNVBAgWB015U3RhdGUxDzANBgNVBAcWBk15VG93bjEXMBUGA1UEChYOTXlPcmdhbml6YXRpb24xGTAXBgNVBAsWEEZPUiBURVNUSU5HIE9OTFkxHzAdBgNVBAMWFnN0YTAwNTM0LnVzLm9yYWNsZS5jb20wgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAMJCDgD00LDSUdWT0SznaU35ZkeQD2Ql6hvtoGcs8MfQpOM/yzM3C9GDlK9+0JpN+7EFGQsCCezFVEX6lMzWdkvdGhbTUJ8/FI32QZ6FPkFItZrnfOS6eDpxcPsnv33rPVQ+ccRvj7BK+sn24PEeV5rt3xF1cGuHGr57t/LtUa01AgMBAAEwDQYJKoZIhvcNAQEEBQADQQAChW8nbopN0FTyZRcVOTZKUlklHXf5X8Xi4gh2OIkkr7q9kjFlfI60SQZoD/nThn1sGZPPbtPGEwRevpqv7cI/
</dsig:X509Certificate>
<dsig:X509IssuerSerial>
<dsig:X509IssuerName>CN=CertGenCAB, OU=FOR TESTING ONLY, O=MyOrganization, L=MyTown, ST=MyState, C=US</dsig:X509IssuerName>
<dsig:X509SerialNumber>61590287842211333696140797217026625564</dsig:X509SerialNumber>
</dsig:X509IssuerSerial>
<dsig:X509SubjectName>CN=sta00534.us.oracle.com, OU=FOR TESTING ONLY, O=MyOrganization, L=MyTown, ST=MyState, C=US</dsig:X509SubjectName>
</dsig:X509Data>
</dsig:KeyInfo>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#rsa-1_5"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes128-cbc"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes192-cbc"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes256-cbc"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#tripledes-cbc"/>
</md:KeyDescriptor>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://sta00534.us.oracle.com:7002/fed/sp/samlv20" ResponseLocation="https://sta00534.us.oracle.com:7002/fed/sp/samlv20"/>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://sta00534.us.oracle.com:7002/fed/sp/samlv20" ResponseLocation="https://sta00534.us.oracle.com:7002/fed/sp/samlv20"/>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST-SimpleSign" Location="https://sta00534.us.oracle.com:7002/fed/sp/samlv20ss" ResponseLocation="https://sta00534.us.oracle.com:7002/fed/sp/samlv20ss"/>
<md:ManageNameIDService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://sta00534.us.oracle.com:7002/fed/sp/samlv20" ResponseLocation="https://sta00534.us.oracle.com:7002/fed/sp/samlv20"/>
<md:ManageNameIDService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://sta00534.us.oracle.com:7002/fed/sp/samlv20" ResponseLocation="https://sta00534.us.oracle.com:7002/fed/sp/samlv20"/>
<md:ManageNameIDService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST-SimpleSign" Location="https://sta00534.us.oracle.com:7002/fed/sp/samlv20ss" ResponseLocation="https://sta00534.us.oracle.com:7002/fed/sp/samlv20ss"/>
<md:ManageNameIDService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://sta00534.us.oracle.com:7002/fed/sp/soap"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Artifact" Location="https://sta00534.us.oracle.com:7002/fed/sp/art20" index="0" isDefault="true"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://sta00534.us.oracle.com:7002/fed/sp/authnResponse20" index="1"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST-SimpleSign" Location="https://sta00534.us.oracle.com:7002/fed/sp/authnResponse20ss" index="2"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:PAOS" Location="https://sta00534.us.oracle.com:7002/fed/sp/authnResponse20" index="4"/>
</md:SPSSODescriptor>
</md:EntityDescriptor>
Sub-topics include:
4.2.1.1 Versions
When issuing a metadata request for both the IdP and SP operations, you can specify the version of the metadata by specifying the version query parameter.
The query parameter must take one of these values:
-
saml10- SAML 1.0 Metadata -
saml11- SAML 1.1 Metadata -
saml20- SAML 2.0 Metadata -
lib11- Liberty 1.1 -
lib12- Liberty 1.2
This example query requests IdP metadata for SAML 2.0 version:
http://host:port/fed/idp/metadata?version=saml20
Note:
If the version parameter is missing, the version is assumed to besaml20.4.2.1.2 Provider-specific Metadata
Oracle Identity Federation allows you to define global configuration parameters, and provides a way to override these global parameters when interacting with a specific remote provider. Some overridden parameters will result in a change of metadata.
For interoperability, Oracle Identity Federation supports metadata generation based on either the configuration of a specific provider, or by using the global settings.
If you choose to override the global configuration for a specific provider, you would typically generate the Oracle Identity Federation metadata based on the provider-specific configuration and provide it to the remote provider.
To generate the Oracle Identity Federation metadata for a specific remote provider, append the providerid query parameter to the URL, setting it to the ProviderID. For example:
http://host:port/fed/idp/metadata?providerid=idp.com
Note:
If theproviderid parameter is missing, Oracle Identity Federation generates its metadata based on the global configuration.4.2.2 Obtain Server Certificates
To get Oracle Identity Federation's IdP certificate, go to a URL in the following format:
http://host:port/fed/idp/cert
To get Oracle Identity Federation's SP certificate, go to a URL in the following format:
http://host:port/fed/sp/cert
Additional topics include:
4.2.2.1 Specifying Certificate Usage
You can specify the use (signing or encryption) of the certificate to be returned by including the use parameter with one of these values:
-
enc- encryption certificate -
sign- signing certificate
For example:
http://host:port/fed/idp/cert?use=enc
This request format returns the Oracle Identity Federation IdP's new encryption certificate.
Note:
If you do not specify theuse parameter, the signing certificate is returned by default.4.2.2.2 Specifying Certificate Type
You can specify the type (new or old) of the certificate to be returned by including the type parameter with one of these values:
-
new- new certificate -
old- old certificate
For example:
http://host:port/fed/idp/cert?type=old&use=enc
This request format returns the Oracle Identity Federation IdP's old encryption certificate.
Note:
If you do not specify the type parameter, the new certificate is returned by default.4.2.3 Perform SP-initiated Single Sign-On
It is possible to initiate a Federation SSO operation by directly requesting a service at the Oracle Identity Federation/SP instance
The URL to be requested on Oracle Identity Federation is of the form: http://host:port/fed/sp/initiatesso
The following query parameters can be specified when requesting the URL:
-
providerid- This is the identifier of the IdP to use to perform the SSO operation (optional). If missing, the default SSO provider is used. -
federationid- This is the identifier of the affiliation to use for the SSO (optional). See Section 6.2, "Working with Affiliations" for more information. -
returnurl- This is the URL to which the user is sent after a successful SSO operation. It is required if the Unsolicited Relay State property is empty.
An example of the URL format is:
http://host:port/fed/sp/initiatesso?providerid=http%3A%2F%2Fidp.com&returnurl=ProtectedAppURL
Note:
Check that the query parameter values are correctly URL-encoded.4.2.4 Perform IdP-initiated Single Sign-On
Oracle Identity Federation provides the ability to initiate an SSO operation by directly requesting a URL at the Oracle Identity Federation instance acting as an IdP; this is called an SSO IdP-initiated operation.
The url to be requested on Oracle Identity Federation is of the form: http://host:port/fed/idp/initiatesso.
The following query parameters can be specified:
-
providerid- This is the identifier of the SAML 2.0 SP to use to perform the SSO operation (optional). -
federationid- This is the identifier of the affiliation to use for the SSO (optional). See Section 6.2, "Working with Affiliations" for more information. -
returnurl- This is the URL to which the user is sent after a successful SSO operation.
An example of this type of URL is:
http://host:port/fed/idp/initiatesso?providerid=http%3A%2F%2Fsp.com&returnurl=ProtectedAppURL
Note:
Check that the query parameter values are correctly URL-encoded.4.2.5 Launch the Logout Process
Launch the logout process by accessing a URL of the form:
http://hostname:port/fed/user/logout?returnurl=http%3A%2F%2Fanotherhostname%2Fpath
The logout service takes a returnurl parameter, which is necessary for correct operation; the user will be redirected to this URL after the logout process completes.
If no returnurl parameter is specified when invoking the Oracle Identity Federation logout URL, the sign-off operation is performed, and the server will display the built-in logout result page.
The logout is performed for all peer providers for the following protocols:
-
SAML 2.0
-
WS-Federation
-
Liberty 1.1
-
Liberty 1.2
For the SAML 1.x protocols, only the local Oracle Identity Federation session will be deleted. The SAML 1.x remote providers will not be notified of the user terminating the session.
4.2.6 Set Signature Verification Certificate Property (SAML 1.x)
If you did not upload XML metadata for a SAML 1.x provider, and that provider is configured to send signed messages, you need to do the following:
-
If the provider is an IdP, you must set the
IdP Signature Verification Certificateproperty. -
If the provider is an SP, you must set the
SP Signature Verification Certificateproperty.
See Also:
Section 4.2.2, "Obtain Server Certificates" for information on how to obtain these certificates.4.2.7 Perform SP-initiated Single Sign-On (SAML 1.x)
Certain properties have to be set before you can perform SP Initiated SSO.
After adding the SP metadata to the IdP, select it and click Edit. Set the following property in the Trusted Provider Settings section:
SP Assertion Consumer Service URL: http://host:port/fed/sp/samlv11sso
After adding the IdP metadata to the SP, select it and click Edit. Set the following properties in the Trusted Provider Settings section:
-
IdP Initiated SSO URL --
http://host:port/fed/idp/samlv11sso(for SAML 1.1) orhttp://host:port/fed/idp/samlv10sso(for SAML 1.0) -
IdP Initiated SSO Target Parameter -- any 'reasonable' string; used by the peer provider to identify the desired resource ("TARGET" in the case of Oracle Identity Federation).
-
IdP Initiated SSO ProviderID Parameter - providerid
-
IdP SOAP Artifact Resolution Endpoint -
http://host:port/fed/idp/soapv11
4.2.8 Send Attribute Requests and Queries (SAML 1.x)
SAML 1.x defines a protocol for retrieving users' attributes. You can either send an attribute request to an Oracle Identity Federation instance acting as an SP, or send a SAML 1.x attribute query to an Oracle Identity Federation instance acting as an IdP.
Section 5.6, "Configuring Attribute Sharing with the Oracle Access Manager AuthZ Plug-in" shows how to configure an SP and IdP for attribute sharing for SAML.
To send an attribute request (in a SOAP envelope) to the SP, use the following url: http://sphost:port/fed/ar/soap.
To send a SAML 1.x attribute query (in a SOAP envelope) to the IdP, use the following url: http://idphost:port/fed/aa/soapv11
For details, see:
-
Section 5.6, "Configuring Attribute Sharing with the Oracle Access Manager AuthZ Plug-in"
-
Section 4.3.5, "Set Up Single Sign-On for SAML 1.x and WS-Federation"
You can also configure attribute name and value mapping, and attribute filtering. See Section 5.9, "Configuring Attribute Mapping and Filtering" for details.
When Oracle Identity Federation, acting as an identity provider, receives a SAML 1.x attribute query, it will need to identify the requester. Oracle Identity Federation provides two ways in which a requester can be identified: by providing an SSL client certificate, or by authenticating via HTTP Basic Authentication.
If the requester authenticates via an SSL client certificate, the cn of the certificate subject must be the provider ID with which Oracle Identity Federation identifies the requester. In the case when the requester authenticates via HTTP Basic Authentication, the username used by the requester must be the provider ID with which Oracle Identity Federation identifies the requester.
For details on how to set up SSL with client authentication or HTTP basic authentication, see Section 6.9, "Protecting the SOAP Endpoint".
4.2.8.1 NameID Format Strings when Using the Attribute Requester Service
The strings to be used for the NameID format when using the Attribute Requester service are:
Table 4-2 NameID Formats for Attribute Requester Service
| Format | String |
|---|---|
|
x509 |
oracle:security:nameid:format:x509 |
|
|
oracle:security:nameid:format:emailaddress |
|
windows |
oracle:security:nameid:format:windowsdomainqualifiedname |
|
kerberos |
oracle:security:nameid:format:kerberos |
|
persistent |
oracle:security:nameid:format:persistent |
|
transient |
oracle:security:nameid:format:transient |
|
unspecified |
oracle:security:nameid:format:unspecified |
|
custom |
oracle:security:nameid:format:custom |
|
userid |
oracle:security:nameid:format:userid |
4.2.9 Send Authentication Queries (SAML 1.x)
To send SAML 1.x authentication queries to an Oracle Identity Federation instance acting as an IdP, use a URL of the form:
http://host:port/fed/authnauth/soapv11
When Oracle Identity Federation, acting as an identity provider, receives a SAML 1.x authentication query, it must identify the requester. Oracle Identity Federation provides two ways in which a requester can be identified: by providing an SSL client certificate, or by authenticating through HTTP basic authentication.
If the requester authenticates using an SSL client certificate, the cn of the certificate subject must be the provider ID with which Oracle Identity Federation identifies the requester. If the requester authenticates through HTTP basic authentication, the username used by the requester must be the provider ID with which Oracle Identity Federation identifies the requester.
For details on how to set up SSL with client authentication or HTTP basic authentication, see Section 6.9, "Protecting the SOAP Endpoint".
4.3 Managing Identity Federations
You use Oracle Identity Federation server's Federations page in Fusion Middleware Control to view and manage the server's trusted providers.
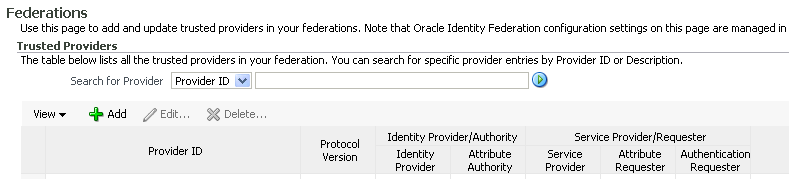
To view the page in Fusion Middleware Control, select the instance of interest, and navigate to Oracle Identity Federation, then Administration, then Federations.
Topics in this section include:
4.3.1 Search for a Provider
Use this feature to locate a provider from your trusted providers.
In the text box, enter the Provider ID, or the provider description. Click the search icon.
You can enter a partial Provider ID or description. For example, enter a port number to display only servers that listen on the specified port.
4.3.2 Add Trusted Providers
To add a trusted provider to your server's trusted providers:
-
In Fusion Middleware Control, select the server instance in the topology panel at left.
-
Navigate to Oracle Identity Federation, then Administration, then Federations.
-
On the Federations page, click Add.
The Add Trusted Provider dialog appears. You can supply the provider details here or upload from the file system.
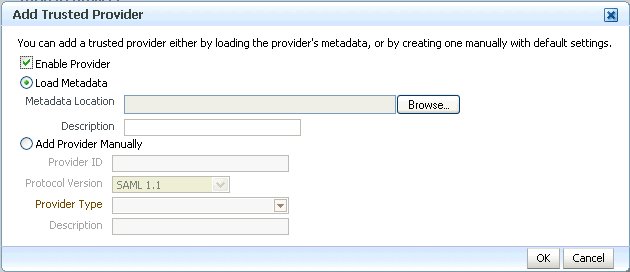
Note the following points:
-
When you upload metadata, there is no validation to check if the related SP or IdP site is using the same protocol. A federated single sign-on may be performed to validate the protocols.
-
After using the Firefox browser to upload provider metadata from the Federations page in Fusion Middleware Control, you cannot modify the provider metadata file that you just uploaded until you restart Firefox.
The reason for this is the
Live HTTP Headeradd-on in Firefox. Once you disable this add-on and restart Firefox, you can modify the provider metadate file after you have uploaded the metadata on the Federations page.
4.3.3 Update Trusted Providers
To update or delete a trusted provider:
-
In Fusion Middleware Control, select the server instance in the topology panel at left.
-
Navigate to Oracle Identity Federation, then Administration, then Federations.
-
Select the provider and click Edit.
4.3.4 Delete Trusted Providers
To update or delete a trusted provider from your server's trusted providers:
-
In Fusion Middleware Control, select the server instance in the topology panel at left.
-
Navigate to Oracle Identity Federation, then Administration, then Federations.
-
Select the provider and click Delete.
4.3.5 Set Up Single Sign-On for SAML 1.x and WS-Federation
To set up SSO for SAML 1.x and WS-Federation protocols, you first add the peer provider to the list of trusted providers, then fill in the required attributes for the protocol.
Add the Peer Provider to the Trusted Providers
Take these steps to achieve this task:
-
In Fusion Middleware Control, select the server instance in the topology panel at the left.
-
Navigate to Oracle Identity Federation, then Administration, then Federations.
-
On the Federations page, click Add.
-
Select the option to Add Provider Manually. Fill in the required attributes, and click OK to add the trusted provider.
Fill in the Required Attributes for SAML 1.x
You can choose to upload SAML1.x metadata, which can then be generated by Oracle Identity Federation. The peer provider's signing certificate and the artifact resolution SOAP endpoint parameters are automatically filled in.
Take these steps to achieve this task:
-
On the Federations page, select the SAML 1.X provider and click Edit.
-
Select the option to Update Manually.
-
Select the Peer Provider Settings tab.
-
If the peer provider is an identity provider:
-
In the Identity Provider / Authority Settings section enter the peer provider's signing certificate, in the New Signature Verification Certificate field.
-
In the Initiate SSO URL field, enter the URL used by the peer provider to initiate the SSO flow.
-
In the Initiate SSO Target Parameter field, enter the parameter used by the peer provider to identify the desired resource (
TARGETin the case of Oracle Identity Federation). -
In the Initiate SSO Provider ID Parameter field, enter the name of the parameter that the peer provider uses to identify the provider ID of the service provider. For an Oracle Identity Federation peer identity provider, the parameter name must be "
providerid". -
In the Artifact Resolution SOAP Endpoint field, enter the URL used by the peer provider to receive SOAP requests to resolve artifacts
For example, an Oracle Identity Federation peer identity provider might have the following Initiate SSO URL, using the configuration entered in steps b, c, and d above:
-
-
If the peer provider is a service provider:
-
In the Service Provider / Requester Settings section enter the peer provider's signing certificate, in the New Signature Verification Certificate field.
-
In the Assertion Consumer Service URL field, enter the URL used by the peer provider to consume the assertion.
-
Fill in the Required Attributes for WS-Federation SSO
Take these steps to achieve this task:
-
On the Federations page, select the WS-Fed 1.1 provider and click Edit.
-
Select the option to Update Manually.
-
Select the Peer Provider Settings tab.
-
If the peer provider is an identity provider:
-
In the Identity Provider / Authority Settings section enter the peer provider's signing certificate, in New Signature Verification Certificate field.
-
In the Identity Realm Secure Token URL field, add the URL of the peer provider to which the authentication request should be sent.
-
-
If the peer provider is a service provider:
-
In the Resource Realm Secure Token URL field, enter the URL of the peer provider to which the assertion should be sent.
-
From the Assertion Type/Version drop-down list, select the version of the assertion that should be sent to this service provider.
-
Required Properties to Send to Peer Provider - WS-Federation
As IdP needs to send to peer provider (SP)
-
ProviderID
http(s)://server_name:server_port/fed/idp -
Signing Certificate
-
Identity Realm Secure Token URL (The URL to which authentication requests should be sent
http(s)://server_name:server_port/fed/idp/wsfed11)
As SP, needs to send to peer provider (IdP)
-
ProviderID
http(s)://server_name:server_port/fed/sp -
Resource Realm Secure Token URL (The URL to which assertions should be sent
http(s)://server_name:server_port/fed/sp/wsfed11) -
Assertion Type/Version (The version of the assertion that wish to be sent; optional)
Required Properties to Send to Peer Provider - SAML 1.x
The IdP needs to send to peer provider (SP)
-
ProviderID
http(s)://server_name:server_port/fed/idp -
Signing Certificate
-
IdP initiate SSO URL (the URL to which authentication requests should be sent)
For SAML 1.1:
http(s)://server_name:server_port/fed/idp/samlv11sso
For SAML 1.0:
http(s)://server_name:server_port/fed/idp/samlv10sso
-
IdP Artifact resolution URL (URL for sending artifact query) http(s)://server_name:server_port/fed/idp/soapv11
-
Target URL query parameter (for Oracle Identity Federation it is TARGET). The parameter would contain the URL the user would land on, after a successful SSO
-
ProviderID URL query parameter (for Oracle Identity Federation it is providerid). The parameter would contain the SP providerID when SP initiates a SAML1.x SSO
-
SourceID required for the artifact profile. The value is got from the IdP metadata, from tag <saml1md:SourceID>
As SP, needs to send to peer provider (IdP)
-
ProviderID
http(s)://server_name:server_port/fed/sp -
Signing Certificate (if we sign SOAP requests)
-
Assertion Consumer URL (The URL to which assertions should be sent
http(s)://server_name:server_port/fed/sp/samlv11sso)
4.4 Configuring Identities
Use this page to locate and manage user and federated identities, and to maintain search options.
4.4.1 About Federated Identities
When a user performs SSO for the first time, and Oracle Identity Federation is configured with a federation data store, it will create a federation record for the user, containing information about the federated identity. This includes:
-
the Username – the User ID with which Oracle Identity Federation identifies the user.
-
the User description – the user description
-
the IdP Provided Name ID – the Name ID provided by the identity provider
when SSO was performed
-
the IdP Provided Name ID Format – the format of the Name ID provided by the identity provider. This field will be empty if the format is "persisent".
-
the IdP Provided Name ID Qualifier - the Name ID qualifier, optionally provided by the identity provider.
-
the Protocol Version – the protocol version used when performing SSO.
-
the SP Provided Name ID – the Name ID provided by the service provider. This will be blank when the federation is created.
-
the SP Provided Name ID Format – the format of the Name ID provided by the service provider. This field will be empty if the format is "persisent".
-
the SP Provided Name ID Qualifier – the Name ID qualifier, optionally provided by the service provider.
-
the SP Provided Name ID Version - the version of the SP Name ID.
-
the Provider ID – the provider ID of the peer provider with which SSO was performed.
-
the Federation Type – the type of federation that was created. It can have one of these values:
-
1 - federation between this server as an IdP and an SP
-
2 - federation between this server as an IdP and an Affiliation
-
3 - federation between this server as an SP and an IdP
-
4 - federation between Oracle Internet Directory server as an Affiliation and an IdP.
-
When the identity provider updates a federation by performing a Manage Name ID (MNI) operation, the value of the following fields is be updated:
-
the IdP Provided Name ID
-
the IdP Provided Name ID Format
-
the IdP Provided Name ID Qualifier
-
the Protocol Version
When the service provider updates a federation by performing a Manage Name ID (MNI) operation, the value of the following fields is updated.
-
the SP Provided Name ID
-
the SP Provided Name ID Format
-
the SP Provided Name ID Qualifier
-
the SP Provided Name ID Version
The following fields will be empty when the federation record is created:
-
the SP Provided Name ID Format.
-
the SP Provided Name ID Qualifier.
-
the SP Provided Name ID Version.
4.4.2 Identities - Federations
Use this page to locate and maintain federated identity records.
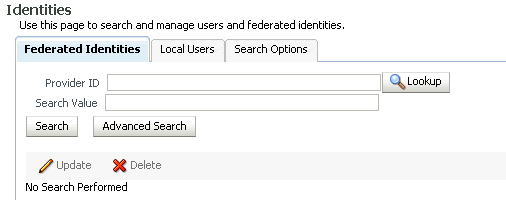
The following search fields are provided:
-
Provider ID: Enter a Provider ID and click Lookup to choose the correct ID from a list of trusted providers. Entering a Provider ID in this field will limit the search to only those federated identities created with the provider specified. If no Provider ID is specified, the search will be performed over the federated identities created with all trusted providers.
-
Search Value: Enter the value you wish to search for. If no value is specified, all federated identity records will be returned.
The search returns a table of federation records. The table columns appearing in the table depend on the default display attributes configured in the search options configuration.
Take these steps to perform an advanced search:
-
Enter a Provider ID, or part of one and click Lookup to choose the correct ID from a list of trusted providers. Entering a provider ID in this field will limit the search to only those federated identities created with the provider specified. If no Provider ID is specified, the search will be performed over the federated identities created with all trusted providers.
-
Check Include New and Old Name IDs in Search to include the new and old NameID values in the search for federation records.
Note:
The new and old NameID fields are populated only if an update operation was previously performed on a federation record, and if the protocol is enabled.If NameID registration is disabled or if no update operation was ever performed, there is no need to include those fields during a search operation.
-
Use the Operator radio buttons to specify whether the returned records must satisfy all conditions (
And) or records satisfying any conditions (Or). -
Add attribute search conditions by following these steps:
-
Click Add Attribute.
-
A pop-up box appears. Use the drop-down list to select a federated identity attribute, and click OK.
-
The attribute appears as a search option. Select the comparator to use and the value to search for.
-
-
Click Search.
To manage a displayed record, select the corresponding row. Buttons on the page provide these actions:
-
Update - Updates the Name ID of the federated identity by performing a Manage Name ID (MNI) operation. See Section 4.4.1, "About Federated Identities" for more details.
-
Delete - Terminates the federated identity by performing a Manage Name ID (MNI) operation with the "Terminate" flag set to true, and deletes the record.
The functions are available for the SAML 2.0 and Liberty 1.x protocols.
4.4.3 Identities - Users
Use this page to locate and maintain user records.
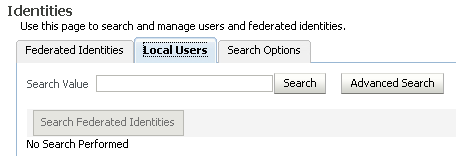
Enter the search value for which you wish to search in the local user entries, and click Search. If no value is specified, all users will be returned..
The search returns a table of user records. The table columns appearing in the table depend on the default display attributes configured in the search option configuration.
Take these steps to perform an advanced search:
-
Use the Operator radio buttons to specify whether the returned records must satisfy all conditions (
And) or records satisfying any conditions (Or). -
Add attribute search conditions by following these steps:
-
Click Add Attributes.
-
A pop-up box appears. Select a user attribute from the list, and click OK.
Note:
The attributes that appear in this list are those configured in the search options configuration Section 4.4.4, "Identities - Search Options". -
The attribute appears as a search condition. Select the comparator to use and the value to search for.
-
Click Search.
-
4.4.4 Identities - Search Options
Use this page to configure the attributes used to search for users and federation records.
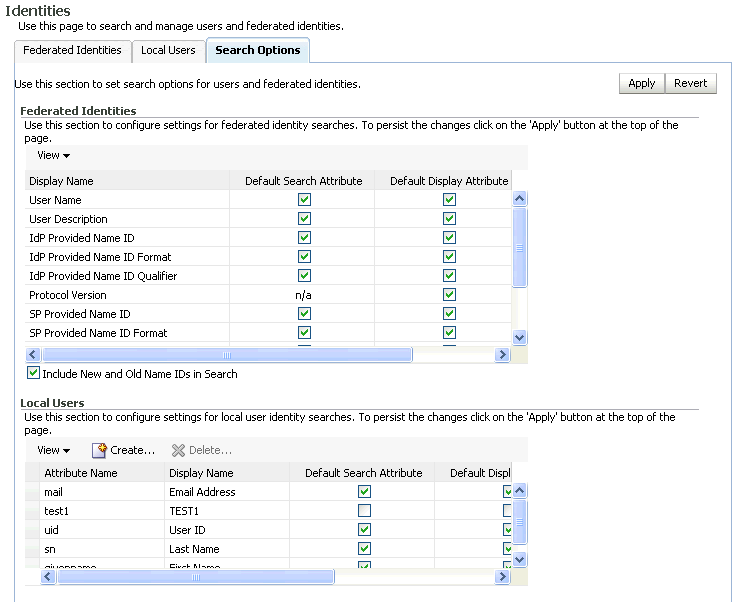
The page displays two tables:
-
The Federations table shows the attributes available on the "Identities - Federation Records" tab of the Identities page. It shows:
-
the attribute's display name
-
whether this attribute is a default search attribute in simple searches; in other words, whether a simple search will be performed over this attribute.
-
whether this attribute is displayed by default in the results from simple and advanced searches.
Use the checkboxes to specify which attributes should be available by default for search and display, respectively. Click Apply to save your changes.
-
-
The Local Users table shows the attributes available on the Identities - Users tab of the Identities page. It shows:
-
the attribute's name in the user data store
-
the attribute's display name
-
whether this attribute is a default search attribute in simple searches; in other words, whether a simple search will be performed over this attribute
-
whether this attribute is displayed by default in the results from simple and advanced searches.
Use the checkboxes to specify which attributes should be available by default for search and display, respectively. Click Apply to save your changes.
Click Create to add another attribute to the list. Enter the following values:
-
Attribute Name - The attribute name in the user data store
-
Display Name – The name that will be displayed when referencing this attribute
-
Default Search Attribute – Check if this attribute should be searched over in simple searches.
-
Default Display Attribute – Check if this attribute should be displayed in the search results.
-
Sort On – Check this if search results should be sorted based on the value of this attribute.
Select an attribute and click Delete to remove it from the list of attributes available for display and searches. Once you delete an attribute, it is no longer available, but you can add it back to the list using Create.
-
Attributes for Federated Identities
The available attributes are:
-
User Name
-
User Description
-
IdP ID
-
IdP Format
-
IdP Qualifier
-
Protocol Version
-
SP Provider ID
-
SP Provider ID Format
-
SP Provider ID Version
-
Provider ID
-
Federation Type
The federation type can have these values:
-
1 - federation between this server as an IdP and an SP
-
2 - federation between this server as an IdP and an Affiliation
-
3 - federation between this server as an SP and an IdP
-
4 - federation between Oracle Internet Directory server as an Affiliation and an IdP
-
Check Include New and Old Name IDs in Search to include the new and old NameID values in the search operation for federation records.
The new and old NameID fields are populated only if an update operation was performed on a federation record, and if the NameID registration protocol is enabled.
If the protocol is disabled or if no update operation was ever performed, there is no need to include those fields during a search operation.
Attributes for users need to be added in the Local Users table in the Search Options tab before searches for local users can be performed. However, if the User data store is of type LDAP, the following attributes have already been added:
-
Email Address
-
User ID
-
Last Name
-
First Name
4.5 Managing Credentials for Oracle Identity Federation
Several properties used by Oracle Identity Federation are stored in the credential store. Table 4-3 provides the list of properties:
Note:
Quoted values are the literal values stored.Table 4-3 Oracle Identity Federation Properties Stored in Credential Store
| Key | Description | Username | Password | Alias |
|---|---|---|---|---|
|
jcepwdsign |
PKCS#12/JCE signing password |
"UniqueUserNameCredential" |
|
|
|
oldjcepwdsign |
Old PKCS#12/JCE signing password |
"UniqueUserNameCredential" |
|
|
|
jcepwdenc |
PKCS#12/JCE encryption password |
"UniqueUserNameCredential" |
|
|
|
oldjcepwdenc |
Old PKCS#12/JCE encryption password |
"UniqueUserNameCredential" |
|
|
|
userldappassword |
LDAP credentials for user data store |
User Store Bind DN (userldapusername) |
|
|
|
fedldappassword |
LDAP credentials for fed data store |
Fed Store Bind DN (fedldapusername) |
|
|
|
ldappassword |
LDAP credentials for LDAP Authn Engine |
Auth Engine Bind DN (ldapbinddn) |
|
|
|
ossopartnerkey |
Oracle SSO partner key |
"UniqueUserNameCredential" |
|
|
|
ossooldpartnerkey |
Old Oracle SSO partner key |
"UniqueUserNameCredential" |
|
|
|
proxypassword |
Proxy password in Server Properties page of Fusion Middleware Control |
Proxy User Name (proxyuser) |
|
|
|
PROVIDER_ID |
Password for HTTP Basic Authn in the Peer Provider specific page |
HTTP Basic Authn Username (authnbasicusername) |
|
|
Note that:
-
the password is entered by the user during configuration
-
ApplicationNameis the name with which Oracle Identity Federation is deployed; by default this isOIF. -
Authn Engine Bind DNis the Bind DN specified by user for the LDAP authentication Engine -
Fed Store Bind DNis Bind DN specified by user for the LDAP federation store -
User Store Bind DNis the Bind DN specified by user for the user identity store.
Note:
When executing theseWLST commands, connect to the administration server instead of the managed server where Oracle Identity Federation is running.Credentials are automatically stored in the credential store when you configure Oracle Identity Federation through Fusion Middleware Control.
If needed, you can update these credentials manually using WLST commands or using Fusion Middleware Control.
See Also:
Configuring the Credential Store in the Oracle Fusion Middleware Security Guide for configuration details using both these tools.As an example of using the interactive WLST mode, you can issue the following commands to store userldappassword in the credential store so that it is accessible to Oracle Identity Federation.
This example assumes that the LDAP bind dn is cn=orcladmin, the correct password is substituted for password, and Oracle Identity Federation is deployed with application name OIF:
Create the userldappassword credential:
createCred(map="OIF", key="userldappassword",
user="cn=orcladmin", password="password", desc="user ldap password")
Update the userldappassword credential:
updateCred(map="OIF", key="userldappassword",
user="cn=orcladmin", password="password", desc="User ldap password")
Delete the userldappassword credential:
deleteCred(map="OIF", key="userldappassword")