C Advanced Tuning of the Daemon
The daemon configuration is managed using Oracle Studio. Daemon configuration is divided into the following groups:
Control
Using the Control tab for the daemon, you define various daemon control options. The Daemon Control tab is accessed as follows:
-
From the Start menu, select Programs, Oracle, and then select Studio.
-
From the Design perspective Configuration view expand the Machines folder.
-
Right-click the computer and select Open Runtime Perspective.
-
Right-click the required daemon in the Runtime Explorer and select Edit Daemon Configuration. The Control tab for the daemon is displayed in the editor.
-
After making changes to the daemon, right-click the daemon and select Reload Configuration.
Note:
You can also change daemon settings using the Configuration Explorer, by selecting a computer and scrolling the list to the required daemon. Right-click the daemon and select Open.Changes made to the daemon configuration are only implemented after the configuration is reloaded using the Reload Configuration option in the Runtime Manager perspective.
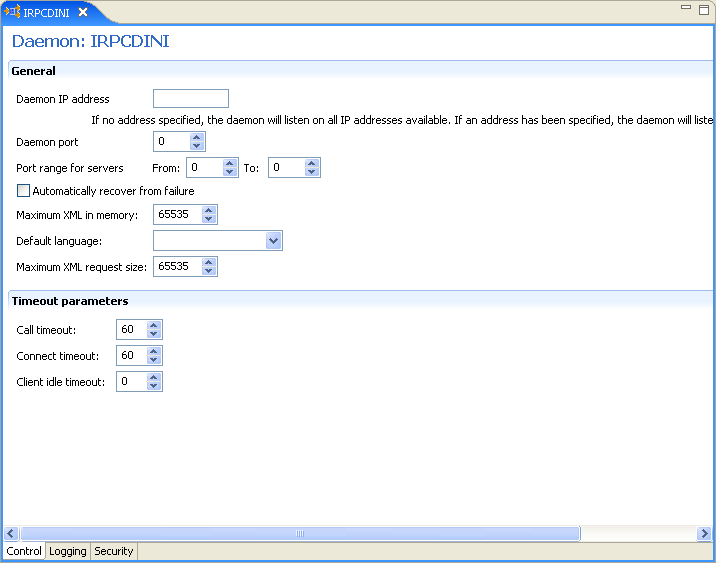
The Control tab is shown in the following figure:
The following table shows the parameters that can be set in the Control tab:
Table C-1 Daemon Control Tab Components
| Field | Description |
|---|---|
|
Daemon IP Address |
Enter the IP address of the computer(s) where the daemon is listening. If no IP address is entered, the daemon listens on all available IP addresses. |
|
Daemon port |
Enter the port where the daemon is listening. If no port is entered, the daemon listens on all available ports. |
|
Automatically recover from failure |
The daemon restarts automatically if it fails for any reason (any error that causes the daemon process to terminate, such as network process lost or the CPU running the daemon crashes and the backup daemon is defined on another CPU). All available and unconnected servers are terminated and any connected servers are marked and terminated on release. Also the backup starts a backup for itself. The backup appends a new log file to the log of the original daemon, adding a line indicating that a backup daemon was started. |
|
Maximum XML request size |
The maximum number of bytes that the daemon handles for an XML document. |
|
Default language |
The language that the daemon supports. This setting is used when working with a client with a code page different from the server code page. |
|
Maximum XML in memory |
The maximum amount of space reserved for the XML in memory. |
|
Call timeout |
The timeout period for short calls for all daemons. The definition of a short call is a call that should be completed in a few seconds. For example, most calls to a database such as DESCRIBE should be completed in a few seconds as opposed to call like a GETROWS call, which can take a long time. In heavily loaded or otherwise slow systems, even short calls such as calls to open a file, may take a significant amount of time. If a short call takes more than the specified time to complete, then the connection is stopped. The default value for this parameter is 60 seconds. Values of less than 60 seconds are considered to be 60 seconds. Specifying the timeout in a workspace overrides the value set in this field for that workspace. |
|
Connect timeout |
The time the client waits for a daemon server to start. If the daemon server does not start within this period, then the client is notified that the server did not respond. The value specified for this parameter serves as the default timeout for all the workspaces listed in the daemon configuration. The default value for this parameter is 60 seconds. Notes:
|
|
Client idle timeout |
The maximum amount of time any daemon client may be idle before the connection with the server is closed. Specifying the timeout in a Workspace overrides this setting for that workspace. |
Logging
Using the Logging tab, you define the daemon log file settings, the log file structure and the location where the log is saved. In addition, use it to define the data that is logged and traced in the file.
The following describes how to open the Logging tab.
-
From the Start menu, select Programs, Oracle, and then select Studio.
-
From the Design perspective Configuration view expand the Machines folder.
-
Right-click a computer and select Open Runtime Perspective.
-
Right-click the daemon in the Runtime Explorer and select Edit Daemon Configuration.
-
Click the Logging tab.
-
After making changes to the daemon, right-click the daemon and select Reload Configuration.
Note:
You can also change daemon settings using the Configuration Explorer, by selecting a computer and scrolling the list to the required daemon. Right-click the daemon and select Open.Changes made to the daemon configuration are only implemented after the configuration is reloaded using the Reload Configuration option in the Runtime Manager perspective.
-
Right-click the daemon and select Recycle Servers. Any servers in the connection pool are closed and new servers start with the new configuration.
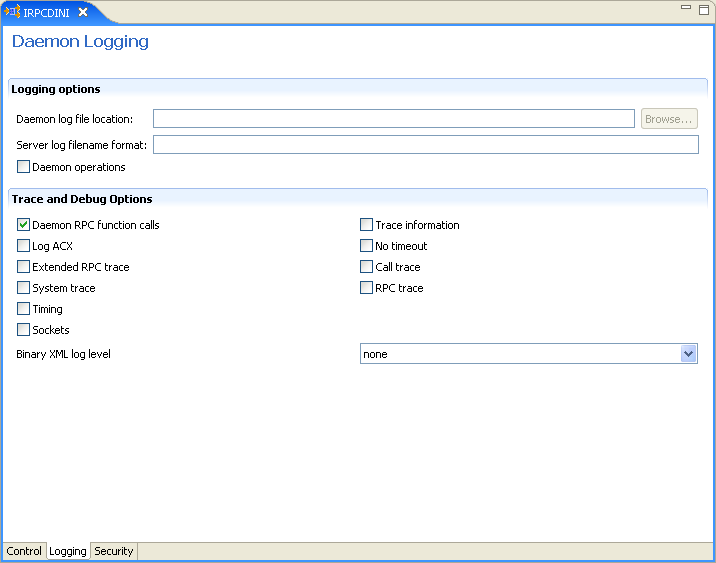
The Logging tab for the daemon is shown in the following figure:
The Daemon Logging tab comprises fields, as listed in the following table:
Table C-2 Daemon Logging Tab Components
| Field | Description |
|---|---|
|
Logging options |
|
|
Daemon log file location |
Specifies the daemon produces its log data. The full path must be specified. |
|
Server log filename format |
Defines the name and location of the server log file. The field must specify the full path name. If no directory information is provided for the log file, then it is located in the login directory of the account running Oracle Connect workstation. |
|
Daemon operations |
Select this to log all of the daemon operations. |
|
Tracing and debug options |
|
|
Daemon RPC function calls |
Select this to log all daemon RPC function calls. |
|
Log ACX |
Select this to log requests and processes. |
|
Extended RPC trace |
Generates a verbose message in the server log file for each low-level RPC function called. This is useful for troubleshooting the server. |
|
System trace |
Generates system-specific tracing of various operations. |
|
Timing |
Generates a time stamp for every entry to the server log file. |
|
Sockets |
Generates a message in the server log file for each socket operation. |
|
Trace information |
Select this to log low-level RPC operations. |
|
No timeout |
Disables the standard RPC timeouts, setting them to a long duration (approximately an hour) to facilitate debugging. |
|
Call trace |
Generates a message in the server log file for each RPC function called. This is useful for troubleshooting the server. |
|
RPC trace |
Enables debugging messages on the server. |
|
Binary XML log level |
Sets the binary XML log level. Your options are:
|
The following tokens can appear in the log file template and is replaced accordingly:
-
%A: workspace name -
%D: date (yymmdd) -
%I: instance number of the given workspace server -
%L: server account login directory -
%P: server process ID -
%T: time (hhmmss) -
%U: server account name (username)
For example, %L/server_%A%I.log may produce a log file such as: /usr/smith/server_sales15.log.
The default log file template is %L/server_%A%I.log.
Security
The following Security tab for the daemon is used to:
-
Grant administration rights for the daemon.
-
Determine access to the computer.
The following shows how to open the Daemon Security tab:
-
From the Start menu, select Programs, Oracle, and then select Studio.
-
From the Design perspective Configuration view expand the Machines folder.
-
Right-click the computer and select Open Runtime Perspective.
-
Right-click the daemon in the Runtime Explorer and select Edit Daemon Configuration.
-
Click the Security tab.
-
After making changes to the daemon, right-click the daemon and select Reload Configuration.
Note:
You can also change daemon settings using the Configuration Explorer, by selecting a computer and scrolling the list to the required daemon. Right-click the daemon and select Open.Changes made to the daemon configuration are not implemented. They are only implemented after the configuration is reloaded using the Reload Configuration option in the Runtime Manager.
-
Right-click the daemon and select Recycle servers. Any servers in the connection pool are closed and new servers start with the new configuration.
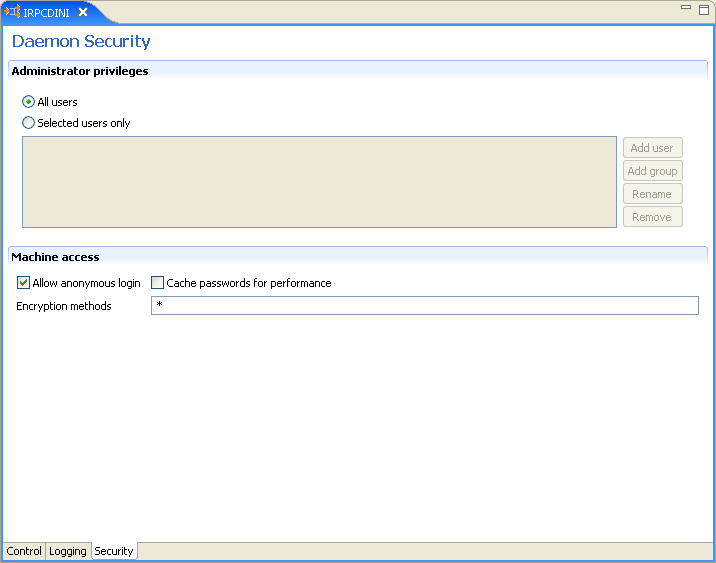
The Daemon Security tab is shown in the following figure:
The Daemon Security tab comprises fields, as listed in the following table:
Table C-3 Daemon Security Tab Components
| Field | Description |
|---|---|
|
Administrators privileges |
Identifies the users (accounts) allowed to perform administrative tasks (tasks that require administrative login). |
|
All users |
Enables all users to access the daemon and change the settings. |
|
Selected users only |
Identifies the names of users (accounts) and groups that can be administrators.Foot 1 If a user is not specified, the account from which the daemon was started is considered the administrator. Note that the daemon does not require the user to log in to the account on the system, but to log in to the daemon using the account name and password. |
|
Machine access |
Manages access to the computer. |
|
Allow anonymous login |
Whether workspaces allow anonymous logins (without user name/password entries). For the optimal level of security, keep this option unchecked and define a user name for the Daemon Administrators parameter. If unchecked, then no workspace can have an anonymous client. If checked, then a particular workspace allows anonymous clients. |
|
Cached password |
Enables login passwords to be cached. This enhances performance by reducing login times for future connections from the same client in a session. |
|
Encryption methods |
Specifies the encryption method used to send information across the network. The default is an asterisk (*), meaning that all methods are acceptable. If an encryption method is specified, it must be used. The RC4 and DES3 protocols are currently supported. |
Footnote 1 The name is prefixed with '@', to use the operating system GROUP feature.
Workspaces
A daemon can include multiple workspaces. A workspace defines the server processes and environment that are used for the communication between the client and the server for the duration of the client request. Each workspace has its own definition. The workspace definition is divided into the following groups:
General
Using the General tab, you enter general information about the features that control the operation of the workspace, such as the server type, the command procedure used to start the workspace and the binding configuration associated with this workspace.
Do the following to open the General tab:
-
From the Start menu, select Programs, Oracle, and then select Studio.
-
From the Design perspective Configuration view, expand the Machines folder.
-
Right-click a computer and select Open Runtime Perspective.
-
Expand the Daemons node to display the workspaces in the Runtime Explorer.
-
Right-click the workspace and select Edit Workspace Configuration. The WS Info. tab opens.
-
After making changes to the workspace, right-click the daemon and select Reload Configuration.
Note:
You can also change daemon settings using the Configuration Explorer, by selecting a computer and scrolling the list to the required daemon. Right-click the daemon and select Open.Changes made to the daemon configuration are not implemented. They are only implemented after the configuration is reloaded using the Reload Configuration option in the Runtime Manager.
-
Right-click the daemon and select Recycle Servers. Any servers in the connection pool are closed and new servers start with the new configuration.
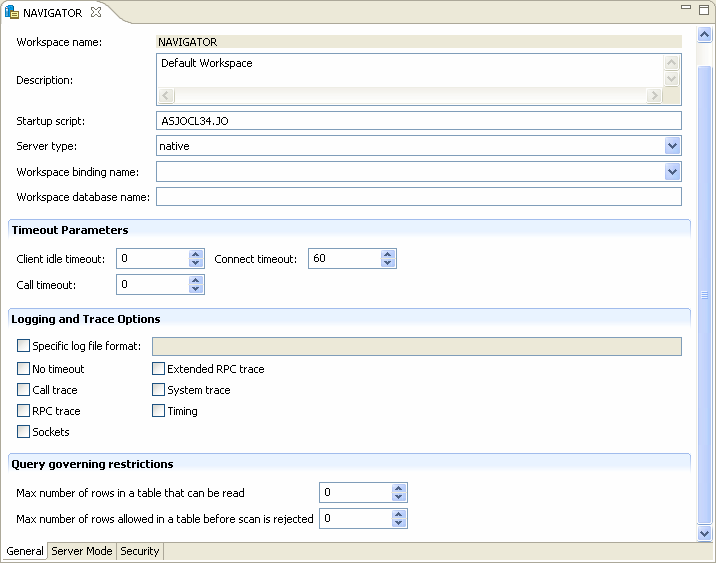
The General tab is shown in the following figure:
The General tab comprises fields, as listed in the following table:
Table C-4 General Tab Components
| Field | Description |
|---|---|
|
Workspace name |
The name used to identify the workspace. Note: The default configuration includes the default Navigator workspace. This workspace is automatically used if a workspace is not specified as part of the connection settings. |
|
Description |
A description of the workspace. |
|
Startup script |
The full path name of the script that starts the workspace server processes. The script specified here must always activate the |
|
Server type |
This field is not applicable for use with OracleAS Adapter for IMS/TM. Do not change the default value. |
|
Workspace binding name |
This field is not applicable for use with OracleAS Adapter for IMS/TM. |
|
Timeout parameters |
The time the client waits for the workspace server to start. If the workspace server does not start within this period, then the client is notified that the server did not respond. Specifying the timeout here overrides the default setting, specified in the Control section. For more information, see Control for details about the Daemon Control section. |
|
Client idle timeout |
The maximum amount of time a workspace client can be idle before the connection with the server is closed. |
|
Connect timeout |
The time the client waits for a workspace server to start. If the workspace server does not start within this period, then the client is notified that the server did not respond. |
|
Call timeout |
The timeout period for short calls for all daemons. The definition of a short call is a call that should be completed in a few seconds. For example, most calls to a database such as Specifying the timeout in a workspace overrides the value set in this field for that workspace. |
|
Logging and Trace Options |
|
|
Specific log file format |
Defines the name and location of the server log file to write the data to a file instead of SYSOUT for the server process. The parameter must specify the name and the high level qualifier. The following tokens can appear in the log file template and are replaced accordingly:
|
|
Trace options |
Specifies the type of tracing to be performed. The following tracing options are available:
|
|
Query governing restrictions |
|
|
Max number of rows in a table that can be read |
Select the maximum number of table rows that are read in a query. When the number of rows read from a table exceeds the number stated the query returns an error. |
|
Max number of rows allowed in a table before scan is rejected |
Select the maximum number of table rows that can be scanned. This parameter has different behavior for query optimization and execution.
|
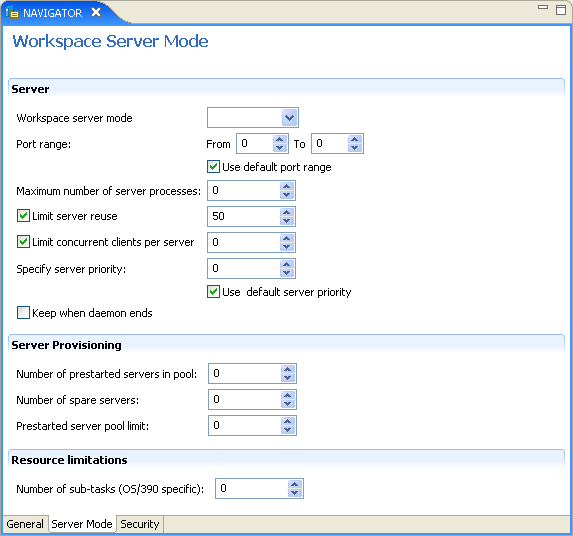
Server Mode
The Server Mode tab lets you configure the features that control the operation of the servers started up by the workspace and allocated to clients.
For example, you can configure the workspace to start multiple servers for future use, before any client request, instead of starting each server when a request is received from a client.
Do the following to open the Server Mode tab:
-
From the Start menu, select Programs, Oracle, and then select Studio.
-
From the Design Perspective Configuration view, expand the Machines folder.
-
Right-click the computer and select Open Runtime Perspective.
-
Expand the Daemons node to display the workspaces in the Runtime Explorer.
-
Right-click the workspace and select Edit Workspace Configuration.
-
Click the Server Mode tab.
-
After making changes to the workspace, right-click the daemon and select Reload Configuration.
Notes:
-
You can also change daemon settings using the Configuration Explorer, by selecting a computer and scrolling the list to the required daemon. Right-click the daemon and select Open.
-
Changes made to the daemon configuration are not implemented. They are only implemented after the configuration is reloaded using the Reload Configuration option in the Runtime Manager.
-
-
Right-click the daemon and select Recycle Servers. Any servers in the connection pool are closed and new servers start with the new configuration.
The Server Mode tab is shown in the following figure:
The Server Mode tab has the following fields:
Table C-5 Server Mode Tab Components
| Field | Description |
|---|---|
|
Specifies the type of new server processes that the daemon starts. The daemon supports the following server modes:
|
|
|
Sets the maximum number of times a particular server can be reused. A one-client server can be reused after its (single) client has disconnected. Reuse of servers enhances startup performance because it avoids the need to repeat initialization. The default for this field is none (0), indicating that server reuse is unlimited. This parameter is disabled only if the server mode value is singleClient. |
|
|
Clients per server limit |
Sets the maximum number of clients a server process for the current workspace accepts. The default for this field is none (0), indicating that the number of clients for each server is unlimited. This field is enabled only if the server mode value is multiClient or multiThreaded. |
|
Server availability |
Specifies the number of servers in a pool of servers, available to be assigned to a client. The following options are available:
|
|
Port range |
Determines the range of ports available for this workspace when starting server processes. Use this option when you want to control the port number, so that Oracle Connect can be accessed through a firewall. Enter the port range in the following fields:
|
|
Use default port range |
Select this to use the port range that is defined in the daemon. This is defined in the Port range for servers field in the daemon Control tab. |
|
Maximum number of server processes |
Enter the maximum number of server processes that can run at the same time. |
|
Limit server reuse |
Select this to limit the number of servers that can be reused. If this is selected, the Reuse limit parameter is available. |
|
If Limit server reuse is selected, in the field next to the check box, enter the maximum number of times a server can be reused. Select the maximum of clients accepted in a server process. A one-client server can be reused after its (single) client has disconnected. Reuse of servers enhances startup performance because it avoids the need to repeat initialization. This parameter is not available if the Limit server reuse parameter is not selected. This parameter is not available if the server mode value is singleClient. |
|
|
Limit concurrent clients per server |
Select this to limit the number of clients that a server can accept for the current workspace process. If this is not selected, the number of clients is unlimited. |
|
If Limit concurrent clients per server is selected, in the field next to the check box, enter the maximum number of clients that a server process for the current workspace accepts. The default for this field is None, indicating that the number of clients for each server is unlimited. This field is available if the server mode value is multiClient or multiThreaded. |
|
|
Set the priority for servers. For example, a workspace for applications with online transaction processing can be assigned a higher priority than a workspace that requires only query processing. The lower the number, the higher the priority. For example, workspaces with a priority of Note: This is unavailable if Use default server priority is selected. |
|
|
Sets the priority to |
|
|
Keep when daemon ends |
Select this to stop all servers started by that daemon when a daemon is shutdown, even if they are active. Select this for the workspace servers to remain active, even after the daemon has been shut down. If selected, it is the responsibility of the system operator or manager to ensure that the servers are eventually stopped. This must be done at the system level. |
|
Server Provisioning |
|
|
Number of prestarted servers in pool |
Initial number of servers: The number of server processes that are prestarted for this workspace when the daemon starts. When the number of available server processes drops lower than the value specified in the Minimum number field, the daemon again starts server processes until this number of available server processes is reached. The default for this field is 0. |
|
Number of spare servers |
The minimum number of server processes in the prestarted pool before the daemon resumes creating new server processes (to the value specified in the Initial number of servers field). If this field is set to a value higher than the Initial number of servers field, the daemon uses the value specified in the Initial number of servers field. The default for this field is 0. |
|
Prestarted server pool limit |
The maximum number of available server processes. Once this number is reached, no new nonactive server processes are created for the particular workspace. For example, if several server processes are released at the same time, so that there are more available server processes than specified by this field, the additional server processes higher than this value are terminated. The default for this field is zero, meaning that there is no maximum. |
|
Resource limitations |
|
|
Number of sub-tasks |
The number of sub-tasks for a server that are prestarted for this workspace when the daemon starts. In addition to setting up a pool of server processes as described earlier, you can set additional server processes as sub-tasks by specifying this parameter. If you set 10 servers and 10 prestarted sub-tasks then 100 tasks are started (10 sub-tasks for each process). |
Security
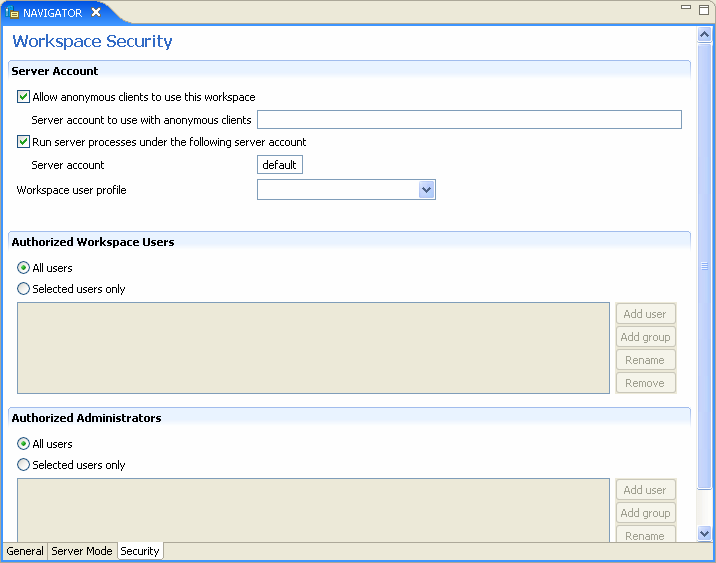
The Security tab lets you configure the security level for a workspace. this lets you set the security options for the workspace only. The Security tab is used to:
-
Grant administration rights for the workspace
-
Determine access to the workspace by a client
Do the following to open the Security tab:
-
From the Start menu, select Programs, Oracle, and then select Studio.
-
From the Design Perspective Configuration view, expand the Machines folder.
-
Right-click the computer and select Open Runtime Perspective.
-
Expand the Daemons node to display the workspaces in the Runtime Explorer.
-
Right-click the workspace and select Edit Workspace Configuration.
-
Click the Security tab.
-
After making changes to the workspace, right-click the daemon and select Reload Configuration.
Notes:
-
You can also change daemon settings using the Configuration Explorer, by selecting a computer and scrolling the list to the required daemon. Right-click the daemon and select Open.
-
Changes made to the daemon configuration are not implemented. They are only implemented after the configuration is reloaded using the Reload Configuration option in the Runtime Manager.
-
-
Right-click the daemon and select Recycle Servers. Any servers in the connection pool are closed and new servers start with the new configuration.
The Security tab is shown in the following figure:
The Security tab has the following fields:
| Field | Description |
|---|---|
|
Server Account |
This section defines the users (accounts) allowed to access the workspace, firewall access ports, workspace account, and anonymous login permissions. |
|
Use specific workspace account |
Select this to define the operating system account used for the workspace. If selected, enter the name of the workspace account in the workspace account field. If not selected, the account name that was provided by the client is used. |
|
Allow anonymous clients to use this workspace |
Select this to allow this workspace to be invoked without authentication. If selected, enter the name of the workspace account in the Server account to use with anonymous clients field. |
|
Authorized Workspace users |
Indicate which users have permission to use the workspace. Select one of the following
|
|
Authorized Administrators |
Identifies the users (accounts) with administrator privileges. Select one of the following:
|