2 About Oracle Platform Security Services
Oracle Platform Security Services comprises Oracle WebLogic Server's internal security framework and Oracle's security framework (referred to as Oracle Platform Security). OPSS delivers security as a service within a comprehensive, standards-based security framework.
This chapter contains these topics:
After reading this chapter, you will understand:
-
what role OPSS plays in Oracle Fusion Middleware architecture
-
the components of OPSS
-
where to use different OPSS features
-
where to obtain more details about OPSS
For details, see Introduction to Oracle Platform Security Services in the Oracle Fusion Middleware Security Guide.
2.1 Overview of Oracle Platform Security Services (OPSS)
Oracle Platform Security Services (OPSS) provides enterprise product development teams, systems integrators (SIs), and independent software vendors (ISVs) with a standards-based, portable, integrated, enterprise-grade security framework for Java Standard Edition (Java SE) and Java Enterprise Edition (Java EE) applications.
OPSS provides an abstraction layer in the form of standards-based application programming interfaces (APIs) that insulate developers from security and identity management implementation details. With OPSS, developers do not need to know the details of cryptographic key management or interfaces with user repositories and other identity management infrastructures. By leveraging OPSS, in-house developed applications, third-party applications, and integrated applications all benefit from the same uniform security, identity management, and audit services across the enterprise.
2.1.1 Oracle Platform Security Services in Oracle Fusion Middleware
Here is a list of Oracle Fusion Middleware components that use Oracle Platform Security Services:
-
Oracle WebLogic Server
-
Oracle Entitlements Server
-
Oracle WebCenter
-
Oracle SOA Suite
-
Oracle Identity Management, including:
-
Oracle Internet Directory
-
Oracle Virtual Directory
-
Oracle Identity Federation
-
-
Oracle Web Services Manager
-
Oracle Application Development Framework (ADF)
2.1.2 How Applications Can Use Oracle Platform Security Services
By leveraging Oracle Platform Security Services systems integrators (SIs), and independent software vendors (ISVs) can build their applications and products using the same security building blocks that are used by Oracle products.
Key features of OPSS include:
-
Extensive security services:
-
Authentication
-
Authorization
-
Credential Store Framework
-
User and Role APIs
-
Policy Management APIs
-
Single Sign-On
-
Identity Assertion
-
Auditing
-
Oracle Security Developer Tools, a comprehensive security API library
More information about each service is available in Section 2.3, "Overview of Services".
-
-
Service provider model
Unlike other application servers, OPSS not only provides security services for the application server, but also allows applications to leverage the same services to seamlessly implement authentication, authorization, and other security features available to Oracle system components.
-
Support for Enterprise Standards
The framework supports key standards including:
-
Java EE
-
SAML
-
XACML
-
JACC
-
JAAS
See Also:
Section 1.1, "Terminology" for information about these standards. -
-
Support for Windows Native Authentication
-
Support for SPNEGO
-
Portability
OPSS is a portable framework:
-
you can build enterprise JavaEE and standalone JavaSE applications in a consistent security framework and ensure a consistent security implementation
-
the service provider interface (SPI) model allows you to implement custom security providers relying on a standards-based security platform
-
the security framework is not tied to a specific application server
-
-
Ease of development
-
Available on both JavaEE and JavaSE platforms
-
Integrated with various back-end data stores (LDAP, RDBMS, custom)
Since OPSS provides the building blocks for securing applications, it simplifies development and allows application developers to focus on solving business problems while relying on OPSS to provide security consistently, in a portable manner, across the enterprise.
2.2 Oracle Platform Security Services Architecture
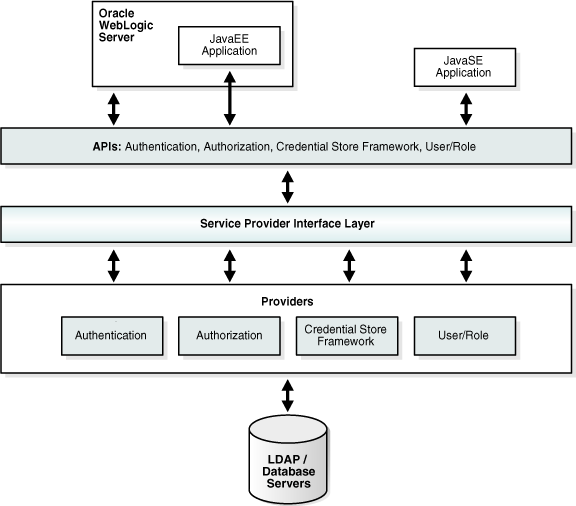
Figure 2-1 shows the environment and building blocks of OPSS and the roles they play in providing security services.
This figure depicts the various security components as layers. The uppermost layer consists of Oracle WebLogic Server and the components and Java applications running on the server; below this is the API layer consisting of Authentication, Authorization, CSF, and User and Role APIs, followed by the Service Provider Interface (SPI) layer and the service providers for authentication, authorization, and others. The final and bottom layer consists of repositories including LDAP and database servers.
Oracle Platform Security Services
Oracle Platform Security Services (OPSS) is both a security framework exposing security services and APIs, and a platform offering concrete implementation of security services. It includes these five elements:
-
Common Security Services (CSS), the internal security framework on which Oracle WebLogic Server is based
This framework provides security to Oracle WebLogic Server, Oracle Entitlements Server, and many other products that previously ran on the application server, and continue to do so in 11g Release 1 (11.1.1)
-
Oracle Platform Services
This framework provides security to Oracle applications, for example, Oracle Application Development Framework (ADF), Oracle WebCenter, Oracle SOA Suite, Oracle Web Services Manager (OWSM) and other products that previously ran on Oracle Application Server, and continues to support these products in 11g Release 1 (11.1.1)
-
User and Role APIs
-
Oracle Fusion Middleware Audit Framework
This framework provides auditing capabilities for components.
-
Oracle Security Developer Tools
For details, see OPSS Architecture Overview in the Oracle Fusion Middleware Security Guide.
Oracle Platform Security Services APIs
OPSS APIs provide a full range of security capabilities:
-
authentication,
authorization,
-
fine-grained authorization,
-
auditing
and other services.
For more information, see:
2.3 Overview of Services
Table 2-1 lists the different services available in this release.
Table 2-1 Oracle Fusion Middleware Security Services
The remainder of this section provides a survey of each service.
See Also:
For more information about securing Oracle WebLogic Server, see:2.3.1 Authentication
In Oracle Fusion Middleware, users are authenticated against an identity store, which is a trusted source of user identities. The authentication process can make use of username-password combinations, tickets, and public key certificates. Credentials supplied by a user are verified against the store during authentication and used to grant the user access to application functions.
The identity store is implemented through Oracle WebLogic Server LDAP authenticators.
Out-of-the-box, Oracle WebLogic Server stores user identities in an embedded LDAP repository. In a deployed production environment, Oracle recommends using an LDAP directory as the identity store. Oracle Fusion Middleware 11gR1 supports a wide array of LDAP servers as identity store including:
-
Oracle Internet Directory
-
Oracle Virtual Directory
-
Sun Java System Directory Server
-
Microsoft Active Directory
-
Open LDAP
-
Novell eDirectory
-
generic
OPSS employs WebLogic authentication providers, components that validate user credentials or system processes based on a user name-password combination or a digital certificate. Oracle WebLogic Server supports the aggregation of authentication providers, so that multiple stores can be used during verification.
For details, see:
-
Authentication Basics in the Oracle Fusion Middleware Security Guide.
-
Oracle Fusion Middleware Securing Oracle WebLogic Server.
2.3.1.1 Authentication Recommendations
A site's authentication needs depend on the phases of the application life cycle:
-
Development Phase – when an application is being developed
-
Staging Phase - where the application is validated for production readiness, and
-
Production Phase - when the application is ultimately deployed and utilized by end-users.
Authentication during the application development phase typically involves using a login module as well as the native testing of user identity and policies. Additionally, some developers may also package application policies as part of the application archive (WAR) before handing it off for deployment in staging and production environments.
Authentication in the Development Phase
Oracle JDeveloper 11gR1, a component of Oracle Fusion Middleware, provides a unified application development environment.
Any application developed with JDeveloper can be tested against Oracle WebLogic Server's embedded LDAP server. The embedded LDAP server is the default security provider store for WebLogic authentication, authorization, credential mapping, and role mapping providers.
Oracle recommends using the embedded LDAP server to test application authentication during development.
See Also:
Managing the Embedded LDAP Server in Oracle Fusion Middleware Securing Oracle WebLogic Server.Single Sign-On Solutions in Staging and Production Phases
Once an application is deployed, the choice of an authentication mechanism depends on the configuration of the Oracle Weblogic Server domain in the staging or production environments. The configuration can take the following forms:
-
Using Oracle Single Sign-On for all or specific applications that are deployed across multiple domains
-
Using Oracle Access Manager for all applications or specific applications that are deployed across multiple domains
-
Using a third-party SSO solution for all applications or specific applications that are deployed across multiple domains
-
Using Windows Native Authentication for applications deployed on Windows platforms
See Also:
-
Configuring Single Sign-On in Oracle Fusion Middleware in the Oracle Fusion Middleware Security Guide
-
Oracle Fusion Middleware Administrator's Guide for Oracle Identity Federation
-
Oracle Access Manager Identity and Common Administration Guide
2.3.2 Authorization
Authorization refers to access control by the use of policies. The authorization process enforces policies, determines what types of activities one can do, or what types of services one can access. Oracle Platform Security Services supports two authorization models for JavaEE and ADF applications.
-
JavaEE Role-based Access Control
-
Oracle ADF Security
Authorization based on JavaEE Role-based Access Control
For Java EE applications, Oracle Fusion Middleware supports JavaEE's role-based access control (RBAC) model, which has logical roles and physical roles. Logical roles are role names used in application code. Physical roles exist in an identity store. During application deployment, the administrator maps the logical role to a physical role.
Authorization based on Oracle ADF
Oracle Platform Security Services supports a fine-grained, permission-based authorization model which protects a resource by means of JAAS-based checkPermission calls.
See Using the method checkPermission in the Oracle Fusion Middleware Security Guide for details.
Leveraged by Oracle Application Development Framework and Oracle WebCenter applications, this model provides a fine-grained authorization capability; for example, you can apply authorization checks separately to individual ADF regions of the application.
Authorization in the Development Phase
Oracle JDeveloper enables you to choose between the Java EE and ADF authorization models.
The ADF authorization model provides an easy-to-use wizard.
Oracle recommends using representative data from the production environment as much as possible during these tests.
Documented procedures address the following Java EE authorization topics:
-
How to configure the Java EE security model in Oracle Jdeveloper using embedded LDAP
-
How to configure security in deployment descriptors by granting resource (URL or EJB method) to a logical role in the
web.xmlandejb-jar.xmlfiles
Documented procedures address the following ADF authorization topics:.
-
How to configure the ADF security model using the ADF security wizard in Oracle JDeveloper
-
How to configure fine-grained security for each region of the ADF page
-
How to grant selective page elements and define the actions for those elements corresponding to a logical role
For details, see:
-
Oracle Fusion Middleware Fusion Developer's Guide for Oracle Application Development Framework
-
Policy Store Basics in the Oracle Fusion Middleware Security Guide.
Authorization in the Staging/Deployment Phases
As a rule, developers are not aware of the enterprise roles (groups) that exist in an identity store and are thus unaware of the authorization policies to apply. Authorization policies are typically implemented during deployment into a production environment.
The following documented procedures help the domain administrator during application deployments:
-
How to map the logical roles used in an application to the enterprise groups that exist in an identity store using the management tools that ship with Oracle Fusion Middleware
-
How to choose application-specific policies that need to migrate to the domain policy store
-
Over time, as the application's security needs evolve, how to use management tools like Oracle Fusion Middleware Control and WLST to make appropriate changes to the application's policies
-
In an environment that uses Oracle Single Sign-On with LDAP, how to configure these SSO environments to use the same user population for both authorization and authentication
The following sections of the Oracle Fusion Middleware Security Guide provide details about implementing post-development authorization:
-
Configuring Single Sign-On in the Oracle Fusion Middleware Security Guide.
-
Mapping of Logical Roles to WebLogic Roles in the Oracle Fusion Middleware Security Guide.
-
Migrating Application Policies Automatically in the Oracle Fusion Middleware Security Guide.
-
Managing the Domain Policy Store in the Oracle Fusion Middleware Security Guide.
2.3.3 Credential Store Framework
A credential store is a repository to store user name/password or generic credentials (a certificate). The value of using a credential store is that the application does not store passwords in clear text and does not need to invent its own solutions for protecting passwords, allowing administrators and developers alike to work with a consistent credential repository.
OPSS provides the Credential Store Framework for Create, Read, Update, and Delete operations on credentials stored in a credential store.
OPSS supports two types of credential stores:
-
file-based
-
LDAP
Domain-level identity and credential stores are supported for applications. You can configure credentials for automatic migration to the domain credential store when the application is deployed.
2.3.4 User and Role API
The User and Role API framework allows applications to access identity information (users and groups) in a uniform and portable manner regardless of the particular underlying identity repository. Supported operations include creating, updating, or deleting identities, or searching identities for attributes or information of interest.
The repository could be an LDAP directory server such as Oracle Internet Directory, Microsoft Active Directory, or Sun Java System Directory Server, or could be a database, flat file, or some other custom repository.
The User and Role API framework provides a convenient way to access repositories programmatically in a portable way, freeing the application developer from the potentially difficult task of accounting for the intricacies of particular identity sources. The framework allows an application to work against different repositories seamlessly. An application can switch between various identity repositories without any code changes being required.
For details, refer to "Developing with the User and Role API" in the Oracle Fusion Middleware Security Guide.
2.3.5 Policy Store and the Policy API
The policy store holds the policies that are used to evaluate authorization decisions. It is a repository of system and application-specific policies and roles. Application roles can include:
-
enterprise users and groups
-
application roles, such as administrative roles
A policy can use any of these roles or users as principals.
The policy store can be shared by multiple applications in the same Oracle WebLogic Server domain and managed at the domain level.
In Oracle Fusion Middleware 11g Release 1 (11.1.1), policy stores can be:
-
XML files, which are the out-of-the-box policy store provider
-
LDAP directories
-
Oracle Internet Directory
-
Oracle Virtual Directory
-
The Policy Store API defines:
-
A management interface to grant and revoke permissions to or from grantees
-
A delegation architecture where authorization decisions can be delegated to custom policy providers based on configured criteria such as permission types and application names
-
Application-based logical roles (or application roles) combined with application-specific fine-grained policies for portable representation of sophisticated application policies
For details, see "Understanding Identities, Policies, and Credentials" in the Oracle Fusion Middleware Security Guide.
2.3.6 Single Sign-On
Single sign-on (SSO) enables a user to authenticate once and gain access to several applications without the need to re-authenticate.
Oracle WebLogic Server offers these SSO choices:
-
Oracle Single Sign-On,
-
Oracle Access Manager.
Oracle WebLogic Server includes two new identity assertion providers (one for each solution) that can be configured with the Oracle WebLogic Administration Console. Applications running on Oracle WebLogic Server can choose either single sign-on solution (or both).
Additionally, Oracle Fusion Middleware provides a framework allowing any third-party SSO solution to be integrated with the environment.
For details about configuring your application to use single sign-on, see Configuring Single Sign-On in the Oracle Fusion Middleware Security Guide.
2.3.7 SSL Support
Oracle Fusion Middleware offers SSL configuration features to provide SSL configuration across the enterprise stack:
-
Web Tier
-
Oracle HTTP Server
-
Oracle Web Cache
-
-
Middle Tier
-
Oracle SOA Suite
Oracle WebCenter
Oracle Identity Federation
-
-
Data Tier
-
Oracle Internet Directory
-
Oracle Virtual Directory
-
Oracle Database
-
third-party LDAP directories and databases
-
-
Oracle WebLogic Server, including SSL inbound from Oracle HTTP Server to Oracle WebLogic Server
The Oracle Enterprise Manager Fusion Middleware Control GUI tool and the WLST command-line tool provide consistent, uniform functions for configuring Oracle wallets and JKS keystores, and configuring SSL. These tools also provide the key functionality of existing tools such as orapki.
Appropriate tools, such as the Oracle WebLogic Server Administration Console, are available for SSL-enabling other endpoints.
For details, see these chapters in the Oracle Fusion Middleware Administrator's Guide:
-
Managing Keystores, Wallets, and Certificates
-
SSL Configuration in Oracle Fusion Middleware
-
Oracle Wallet Manager and orapki
2.3.8 Auditing
Audit is a new service in Oracle Fusion Middleware 11g Release 1 (11.1.1), providing a central audit facility for the middleware family of products. The audit feature:
-
is usable across Oracle Fusion Middleware 11g components and services such as Oracle Web Services Manager, Oracle Internet Directory (OID), Oracle Virtual Directory, and Oracle Directory Integration and Provisioning (DIP)
-
integrates with Oracle Enterprise Manager Fusion Middleware Control for UI-based configuration and management
-
integrates with
WLSTfor command-line, script-based configuration -
integrates with Oracle Platform Security Services
Key features of auditing for robust support of compliance and analytics needs include:
-
A uniform system for administering audits across a range of system components, Java EE and non-JavaEE applications
-
Capturing authentication history/failures, authorization history, user management, and other common transaction data
-
Analytics on fraud and intrusion detection
-
Flexible audit policies, including pre-seeded audit policies, capturing customers' most common audit events
-
Prebuilt compliance reporting features using out-of-the-box analytical reporting capabilities within Oracle BI Publisher; data can be analyzed on multiple dimensions across multiple components. These reports can also be customized according to your preferences.
-
Common audit repository
-
Common audit record format
See the following topics in the Oracle Fusion Middleware Security Guide for more information:
-
Introduction to Common Audit Framework
-
Configuring and Managing Auditing
2.3.9 Oracle Security Developer Toolkit
Oracle Security Developer Tools provide you with the cryptographic building blocks necessary for developing robust security applications, ranging from basic tasks like secure messaging to more complex projects such as securely implementing a service-oriented architecture. The tools build upon the core foundations of cryptography, public key infrastructure, web services security, and federated identity management, and are widely used in building Oracle's own security offerings.
Oracle Products using Oracle Security Developer Tools
Products using the toolkit include, but are not limited to:
-
Oracle Applications
-
Global Mapping; GI (Image Process Management); Payment; XDO (XML Publisher); Workflow, BPEL
-
Oracle Collaboration Suite (Email)
-
-
Application Server
-
Available on WebLogic Server (10.3 and later)
-
-
Platform Security
-
Oracle Platform Security Services
-
SSL Configuration
-
Oracle Wallet (used by Oracle Identity Management products, Oracle EM and the Oracle Database Server)
-
-
Oracle Products
-
Oracle Web Services Manager (OWSM)
-
Business Integration (B2B)
-
Oracle Portal
-
Oracle Identity Federation (OIF)
-
What's in the Oracle Security Developer Tools
The toolkit includes:
-
Oracle Crypto - supports Public key cryptography algorithms, Digital signature algorithms, Key exchange algorithms, Symmetric cryptography algorithms, Message digest algorithms, MAC algorithms, and methods for building and parsing ASN.1 objects
-
Oracle Security Engine - The Oracle Security Engine toolkit supports X.509 Version 3 Certificates, PKCS#12, PKCS#10 for certificate requests, CRLs, Signed Public Key And Challenge (SPKAC), PKCS#7 for wrapping X.509 certificates and CRLs, and other features.
-
Oracle CMS - provides an extensive set of tools for reading and writing CMS objects, and supporting tools for developing secure message envelopes.
-
Oracle S/MIME - provides full support for X.509 Version 3 certificates with extensions, including certificate parsing and verification; support for X.509 certificate chains in PKCS#7 and PKCS#12 formats; private key encryption using PKCS#5, PKCS#8, and PKCS#12; and an integrated ASN.1 library for input and output of data in ASN.1 DER/BER format.
-
Oracle PKI - contains a set of tools for working with digital certificates, including access to LDAP directories, date stamping of digital messages, certificate validation, and certificate management.
-
Oracle JCE - is a cryptographic provider that fits into the Sun Microsystems JCA provider framework. Oracle JCE implements the standard JCE APIs. The Oracle JCE Provider package contains a number of cryptographic algorithms and services including ciphers, key agreement, key factory and secret key factory, key pair generation, and others.
The standard API enables the developer to conveniently switch from one provider to another.
-
Oracle XML Security - supports the XML Digital Signature specification (JSR105), the Decryption Transform proposed standard, the XML Canonicalization standard, the Exclusive XML Canonicalization standard, and compatibility with a wide range of JAXP 1.1 compliant XML parsers and XSLT engines.
-
Oracle SAML - provides tools and documentation to assist developers of SAML-compliant Java security services. You can integrate Oracle SAML into existing Java solutions, including applets, applications, EJBs, servlets, and JSPs. The API supports:
-
the SAML 1.0/1.1 and 2.0 specifications
-
SAML-based single sign-on (SSO), Attribute, Metadata, Enhanced Client Proxy, and federated identity profiles
-
-
Oracle Web Services Security - provides an authentication and authorization framework based on OASIS specifications, and supports the SOAP Message Security standard, the Username Token Profile standard, the X.509 Certificate Token Profile standard, and the WSS SAML Token Profile.
-
Oracle Liberty - allows Java developers to design and develop single sign-on (SSO) and federated identity solutions based on the Liberty Alliance specifications.
-
Oracle XKMS - provides a convenient way to handle public key infrastructures by allowing developers to write XML transactions for digital signature processing. Oracle XKMS implements the W3C XKMS standard.
For details, see the Oracle Fusion Middleware Reference Guide for Oracle Security Developer Tools.