| Oracle® Fusion Middleware Security Guide for Oracle Business Intelligence Enterprise Edition 11g Release 1 (11.1.1) Part Number E10543-04 |
|
|
View PDF |
| Oracle® Fusion Middleware Security Guide for Oracle Business Intelligence Enterprise Edition 11g Release 1 (11.1.1) Part Number E10543-04 |
|
|
View PDF |
This chapter describes how to configure Oracle BI components to communicate over the Secure Socket Layer (SSL).
Note:
For a detailed list of security setup steps, see Section 1.8, "Detailed List of Steps for Setting Up Security In Oracle Business Intelligence".The SSL Everywhere feature of Oracle Business Intelligence enables secure communications between the components. You can configure SSL communication between the Oracle Business Intelligence components and between Oracle WebLogic Server for secure HTTP communication across your deployment. This section does not cover configuring secure communications to external services, such as databases and Web servers. For information about how to configure SSL for Oracle WebLogic Server, see "SSL Configuration in Oracle Fusion Middleware" in Oracle Fusion Middleware Administrator's Guide.
This chapter contains the following sections:
Section 5.1, "Common SSL Configuration Tasks for Oracle Business Intelligence"
Section 5.3, "Configuring the Web Server to Use the HTTPS Protocol"
Section 5.4, "Configuring SSL Communication Between Components"
Table 5-1 contains common SSL configuration tasks and provides links for obtaining more information.
Table 5-1 Task Map: Configuring SSL Communication for Oracle Business Intelligence
| Task | Description | Information |
|---|---|---|
|
Understand SSL communication in Oracle Business Intelligence. |
Understand how SSL communication between components and the application server works. |
|
|
Configure SSL communication between the Oracle WebLogic Server Managed servers. |
The Web server must be configured to use HTTPS before enabling SSL communication for Oracle Business Intelligence. |
Section 5.3, "Configuring the Web Server to Use the HTTPS Protocol" "SSL Configuration in Oracle Fusion Middleware" in Oracle Fusion Middleware Administrator's Guide |
|
Configure SSL communication between components. |
Configure SSL communication between Oracle Business Intelligence components. |
Section 5.4, "Configuring SSL Communication Between Components" |
SSL is a cryptographic protocol that enables secure communication between applications across a network. Enabling SSL communication provides several benefits, including message encryption, data integrity, and authentication. An encrypted message ensures confidentiality in that only authorized users have access to it. Data integrity ensures that a message is received intact without any tampering. Authentication guarantees that the person sending the message is who they claim to be.
For more information about SSL concepts and public key cryptography, see "How SSL Works" in Oracle Fusion Middleware Administrator's Guide.
By default, Oracle Business Intelligence components communicate with each other using TCP/IP. Configuring SSL between the Oracle Business Intelligence components enables secured network communication.
Oracle Business Intelligence components can communicate only through one protocol at a time. It is not possible to use SSL between some components, while using simple TCP/IP communications between others. To enable secure communication, all instances of the following Oracle Business Intelligence components must be configured to communicate over SSL:
Oracle BI Server
Oracle BI Presentation Services
Oracle BI JavaHost
Oracle BI Scheduler
Oracle BI Job Manager
Oracle BI Cluster Controller
Oracle BI Server Clients, such as Oracle BI ODBC Client
SSL requires that the server possess a public key and a private key for session negotiation. The public key is made available through a server certificate. The certificate also contains information that identifies the server. The private key is protected by the server.
The SSL Everywhere central configuration feature configures SSL throughout the Oracle Business Intelligence installation from a single centralized point. Certificates are created for you and every Oracle Business Intelligence component is configured to use SSL. The following default security level is configured by the SSL Everywhere feature:
SSL encryption is enabled.
Mutual SSL authentication is not enabled. Since mutual SSL authentication is not enabled, clients do not need their own private SSL keys. All security sensitive inter-component communication links are authenticated by the BISystemUser credentials, or a user's credential.
The default cipher suites are used. For information about how to use a non-default cipher suite, see Section 5.6, "Advanced SSL Configuration Options".
When scaling out, the centrally managed SSL configuration is automatically propagated to any new components that are added.
If a higher level of security is required, manual configuration might be used to augment or replace the SSL Everywhere central configuration. This is considerably more complex. For more information about how to configure SSL manually, contact Oracle Support. For more information, see Access to Oracle Support.
Secure communication over SSL requires certificates signed by a certificate authority (CA). For internal communication, the SSL Everywhere feature creates both a private certificate authority and the certificates for you. The internal certificates cannot be used for the outward facing Web server because user Web browsers are not aware of the private certificate authority. The Web server must therefore be provided with a Web server certificate signed by an externally recognized certificate authority. The central SSL configuration must be given the external certificate authority's root certificate so that the Oracle Business Intelligence components can recognize the Web server certificate.
The Oracle Business Intelligence credential store is used to store the SSL credentials, such as certificates, trusted certificates, certificate requests, and private keys. SSL-related credentials are stored in the oracle.bi.enterprise credential map. The supported certificate file formats are .der and .pem.
The Web server must be configured to use HTTPS before enabling SSL communication for Oracle Business Intelligence. For information about how to configure SSL for Oracle WebLogic Server, see "SSL Configuration in Oracle Fusion Middleware" in Oracle Fusion Middleware Administrator's Guide.
Some Oracle Business Intelligence Java components running in Oracle WebLogic Server invoke other Web services running in Oracle WebLogic Server. Therefore, Oracle WebLogic Server must be configured to trust itself by setting the following Java properties:
javax.net.ssl.trustStore
javax.net.ssl.trustStorePassword
These properties are set by editing the following files:
For Linux:
MW_HOME/user/projects/domains/bifoundation_domain/bin/setDomainEnv.sh
For Windows:
MW_HOME\user\projects\domains\bifoundation_domain\bin\setDomainEnv.bat
and adding the properties to the end of the JAVA_OPTIONS value. Note that any \ character in a path must be escaped with another \ character.
For example, the following edits are made if using the demonstration Oracle WebLogic Server certificate:
For Linux (all on one line):
JAVA_OPTIONS="${JAVA_OPTIONS} -Djavax.net.ssl.trustStore=MW_Home/wlsserver_10.3/server/lib/DemoTrust.jks -Djavax.net.ssl.trustStorePassword="
For Windows (all on one line):
set JAVA_OPTIONS=%JAVA_OPTIONS% -Djavax.net.ssl.trustStore="MW_Home/wlserver_10.3/server/lib/DemoTrust.jks" -Djavax.net.ssl.trustStorePassword=""
If this step is omitted then login will fail.
Best practice is to disable the HTTP listener and leave only the HTTPS listener. After disabling the HTTP listener you must restart Oracle WebLogic Server. If Oracle WebLogic Server is not restarted, then any attempts to login to Oracle Business Intelligence fail.
If the trust store location is given incorrectly, then Web Services for SOA display an error message similar to the following:
java.security.InvalidAlgorithmParameterException: the trustAnchors parameter must be non-empty
Table 5-2 contains the tasks for setting up SSL communication between components and provides links for obtaining more information.
Note:
You must configure SSL for the Web server before enabling SSL for Oracle Business Intelligence. For more information, see Section 5.3, "Configuring the Web Server to Use the HTTPS Protocol".Table 5-2 Task Map: Configuring SSL Communication Between Components
| Task | Description | For Information |
|---|---|---|
|
Lock the configuration. |
Use the BIDomain MBean to lock the domain configuration before making changes. |
|
|
Generate the SSL certificate. |
Use the BIDomain.BIInstance.SecurityConfiguration MBean to generate the SSL certificate. |
|
|
Commit the SSL configuration changes. |
Use the BIDomain MBean to commit the SSL configuration changes. |
|
|
Verify SSL certificates in credential store. |
Verify that the SSL certificates are saved in the credential store. |
Section 5.4.4, "Verifying the SSL Credentials in the Credential Store" |
|
Enable the SSL configuration and restart Oracle Business Intelligence components. |
Use the BIDomain.BIInstance.SecurityConfiguration MBean to enable the SSL configuration between components, then restart the components so the changes take effect. |
|
|
Confirm that SSL communication is enabled between components. |
Run the SSL report to confirm status. |
|
|
Configure SSL communication for the mail server. |
Configure SSL communication for the mail server. |
|
|
Update expired SSL certificates. |
Update expired SSL certificates and replace with new ones. |
Internal SSL communication between components is configured using Oracle Business Intelligence managed beans (MBeans). An MBean is a Java object that represents a JMX manageable resource in a distributed environment, such as an application.
Use the Fusion Middleware Control System MBean Browser to configure SSL communication between Oracle Business Intelligence components. The System MBean Browser is accessed from the Oracle WebLogic Server domain where Oracle Business Intelligence is installed in Fusion Middleware Control. For example, bifoundation_domain.
For more information about using and navigating within Fusion Middleware Control, see "Navigating Within Fusion Middleware Control" in Oracle Fusion Middleware Administrator's Guide.
Configuring SSL between components requires that you lock the configuration before making changes. The BIDomain MBean is used to lock the configuration.
In Fusion Middleware Control target navigation pane, go to the Oracle WebLogic Server domain in which Oracle Business Intelligence is installed. Select this domain. For example, bifoundation_domain.
From the WebLogic Domain menu, select System MBean Browser.
Expand the Application Defined MBeans node in the MBean navigation tree, then expand the oracle.biee.admin node, then expand the bifoundation_domain node.
Locate and expand the BIDomain node to display two BIDomain MBeans. Then either hover your cursor over each MBean or click Show MBean Information to display their full names:
oracle.biee.admin:type=BIDomain, group=Service
oracle.biee.admin:type=BIDomain, group=Config
Select the BIDomain MBean having the full name oracle.biee.admin:type=BIDomain, group=Service from the MBean navigation tree.
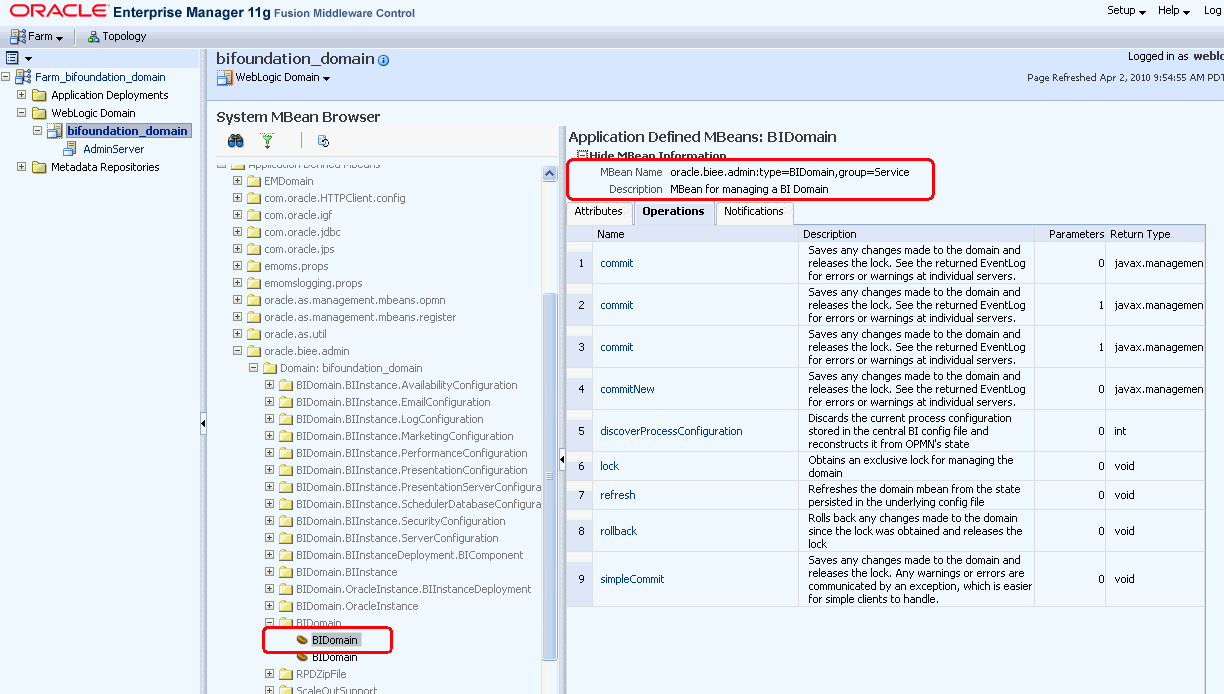
Select the Operations tab, then Lock.
Click Invoke.
A confirmation displays to indicate that the configuration is locked. The next step is to generate the SSL certificates. For more information, see Section 5.4.2, "Generating the SSL Certificates".
Internal SSL communication requires that server certificates, a server public key, and a private key be generated. Oracle Business Intelligence acts as a private CA (certificate authority) for internal communication only. The BIDomain.BIInstance.SecurityConfiguration MBean is used to generate the SSL certificates.
Note:
If you have existing certificates, best practice is to discard them and generate new certificates by following these steps. To use your existing certificates you must manually configure SSL.To generate the SSL certificate:
Lock the configuration.
For information, see Section 5.4.1, "Locking the Configuration".
In Fusion Middleware Control target navigation pane, expand the farm, then expand WebLogic Domain, and select bifoundation_domain.
Display the WebLogic Domain menu, and select System MBean Browser.
The System MBean Browser page is displayed.
Expand the Application Defined MBeans node in the MBean navigation tree, then expand the oracle.biee.admin node, then expand the bifoundation_domain node.
Locate and expand the BIDomain.BIInstance.SecurityConfiguration node.
The BIDomain.BIInstance.SecurityConfiguration MBean is displayed.
Select the BIDomain.BIInstance.SecurityConfiguration MBean.
Configuration options for the MBean display in the right pane.
Select the Attributes tab, then locate the SSLCertificatesGenerated attribute. A value of false indicates that SSL certificates have not been generated. If certificates have been previously generated, you can continue to replace them with new certificates.
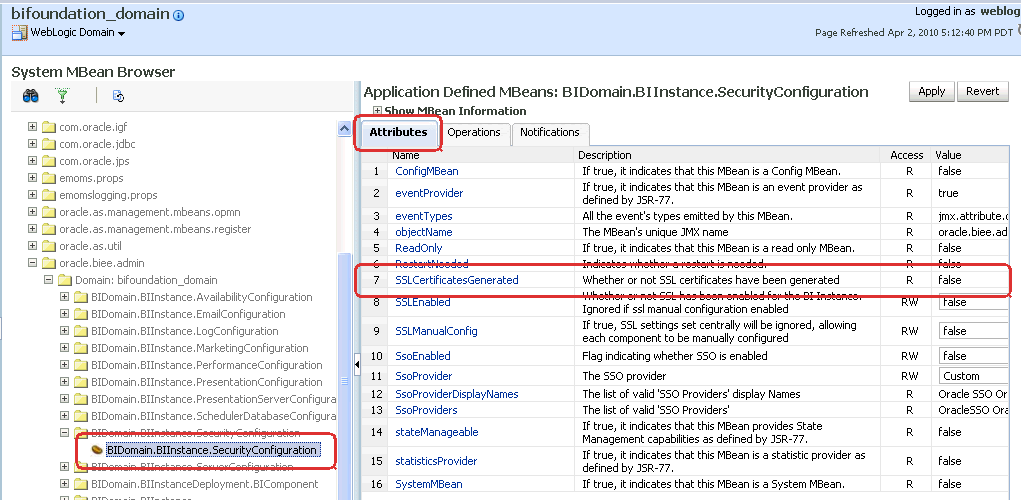
Select the Operations tab, then select generateSSLCertificates operation.
The parameters for the generateSSLCertificates attribute for the BIDomain.BIInstance.SecurityConfiguration MBean displays.
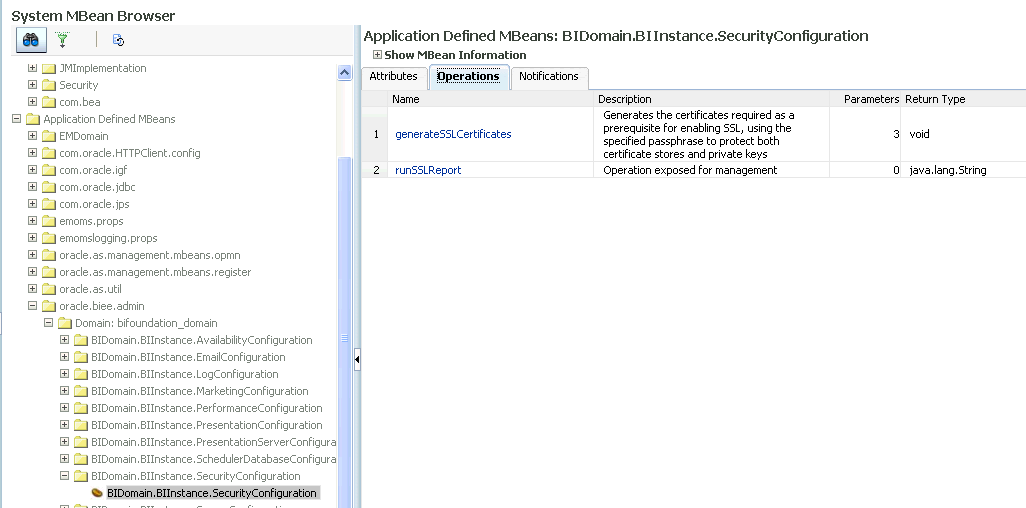
Provide values for the following parameters:
passphrase: Must be more than six characters. The SSL passphrase protects the various certificates and, most importantly, the private key. Remember this passphrase. For example, you need to use it to connect to a BI Server using command line tools that require the tool to verify the BI Server certificate.
webServerCACertificatePath: Enter the path for the Certificate Authority (CA) root certificate for the CA used to sign the web server's certificate. Do not enter the individual web server certificate. Supported types are .der. and .pem. For Oracle WebLogic Server default demonstration certificate authority, enter <MW_HOME>/wlserver_10.3/server/lib/CertGenCA.der.
Note:
The recommended practice is to install a non-demonstration certificate in Oracle WebLogic Server, signed either by a recognized public certificate authority or your organization's certificate authority. You can obtain the CA root certificate direct from the certificate authority or by exporting it from your Web browser.certificateEncoding: Supported types are .der. and .pem. For Oracle WebLogic Server default, enter der
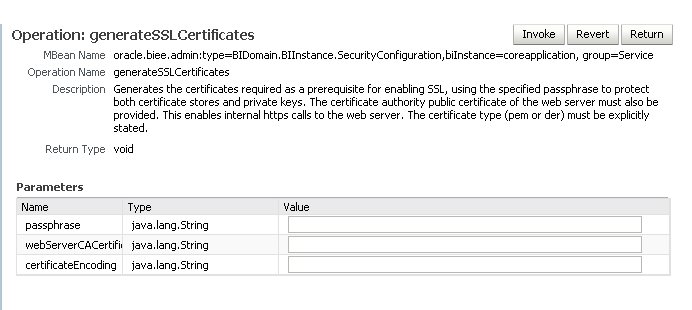
Click Invoke.
A confirmation displays if the operation executed successfully. If successful, the input CA certificate has been validated and the certificate generation request is queued. The next step is to commit the changes, which completes certificate creation and distribution throughout the domain. For more information, see Section 5.4.3, "Commit the SSL Configuration Changes".
You commit the SSL configuration changes using the BIDomain MBean.
Note:
You must configure SSL for the Web server before enabling SSL for Oracle Business Intelligence. For more information, see Section 5.3, "Configuring the Web Server to Use the HTTPS Protocol".To commit the SSL configuration:
From the System MBean Browser, navigate to the BIDomain MBean. You want the MBean with the complete name of oracle.biee.admin:type=BIDomain, group=Service.
For more information about navigating to the BIDomain MBean, follow Steps 1 through 5 in Section 5.4.1, "Locking the Configuration".
Select the BIDomain MBean having the complete name oracle.biee.admin:type=BIDomain, group=Service.
Select the Operations tab, then simpleCommit.
Click Invoke.
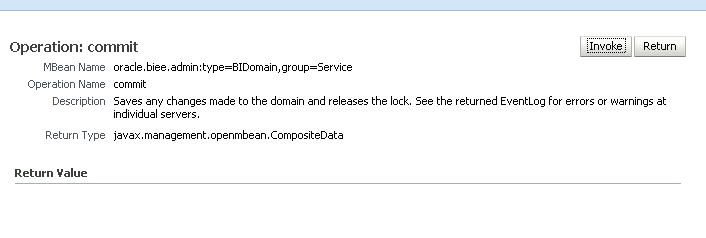
A confirmation displays to indicate if the commit operation was successful.
The next step is to verify the SSL credentials are in the credential store. For more information, see Section 5.4.4, "Verifying the SSL Credentials in the Credential Store".
If the commit operation fails you might see the following error message:
SEVERE: Element Type: DOMAIN, Element Id: null, Operation Result: VALIDATION_FAILED, Detail Message: SSL must be enabled on AdminServer before enabling on BI system; not set on server: AdminServer
This message indicates that SSL has not been enabled on the Oracle WebLogic Server Managed Servers, which is a pre-requisite step. For more information, see Section 5.3, "Configuring the Web Server to Use the HTTPS Protocol". After this pre-requisite is completed you can repeat the commit operation.
The SSL credentials are stored in the credential store for Oracle Business Intelligence.
To verify the SSL credentials in the credential store:
If necessary, from Fusion Middleware Control target navigation pane, expand the farm, then expand WebLogic Domain, and select bifoundation_domain.
From the WebLogic Domain menu, select Security, then Credentials.
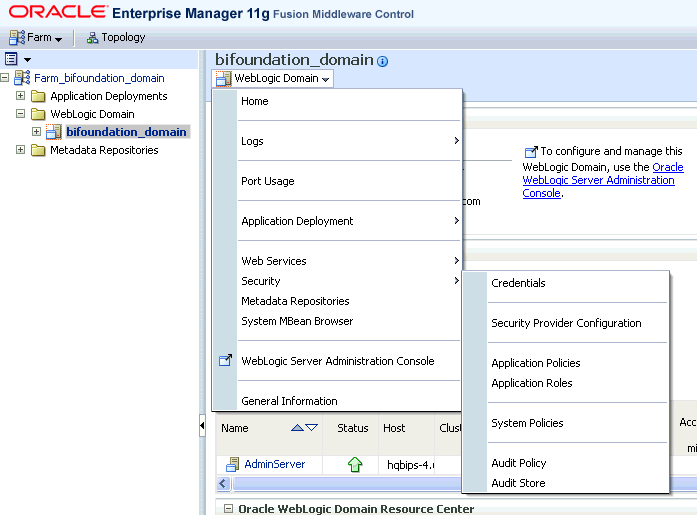
Open oracle.bi.enterprise credential map and verify the SSL credentials have been saved to the credential store. If successful, the following SSL credentials display in the oracle.bi.enterprise credential map:
ssl.java.private.key
ssl.java.public.certificate
config.version
In addition, the certificates are also copied into each MW Home at MW_HOME\user_projects\domains\bifoundation_domain\config\fmwconfig\biinstances\coreapplication\ssl. The certificate files are:
cacert.pem: The certificate of the private CA. Command line tools that want to verify the BI Server certificates point to this file.
webservercacert.pem: The certificate of the public CA that signed the Web server certificate. This is a copy of the CA certificate registered in the generateSSLCertificate operation, in .pem format.
javaserver.keystore: Contains all the certificates in a format suitable for use by Java clients. Contents include:
| Alias | Certificate |
|---|---|
| javaservercert | Server |
| javaserverkey | Key |
| internalcacertificate | Private Key |
| webservercacertificate | Web server CA |
server-key.pem: Private key for the openssl servers.
The next step is to enable the SSL configuration changes. For more information, see Section 5.4.5, "Enabling the SSL Configuration".
The configuration must be locked before you can enable SSL.
Note:
After the SSL configuration is enabled the Oracle Business Intelligence components must be restarted.Verify that the Web server is configured to use HTTPS before enabling the SSL configuration. If necessary, configure the Web server before proceeding.
For information about how to configure SSL for Oracle WebLogic Server, see Section 5.3, "Configuring the Web Server to Use the HTTPS Protocol".
Lock the configuration.
For information, see Section 5.4.1, "Locking the Configuration".
From the System MBean Browser, select the BIDomain.BIInstanceSecurityConfiguration MBean.
For information about how to navigate to the MBean, see Section 5.4.2, "Generating the SSL Certificates".
Select the Attributes tab, then for the SSLEnabled attribute select true from the Value list, then click Apply. You must have the SSL listen port on for the Admin Server and Manager Servers. For more information, see Section 5.3, "Configuring the Web Server to Use the HTTPS Protocol".
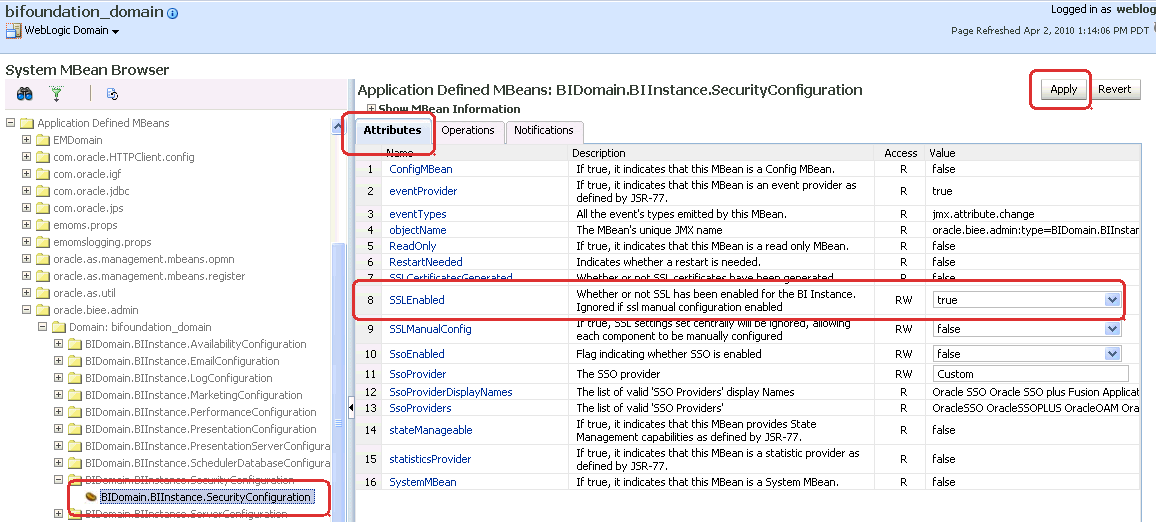
Navigate to the BIDomain MBean and commit the changes.
For information, see Section 5.4.3, "Commit the SSL Configuration Changes".
SSL communication is now enabled between the components. You must restart the Oracle Business Intelligence components for the changes to take effect.
Restart the Oracle Business Intelligence components from the Oracle Business Intelligence Overview page in Fusion Middleware Control.
For more information, see "Starting and Stopping Oracle Business Intelligence System Components" in Oracle Fusion Middleware System Administrator's Guide for Oracle Business Intelligence Enterprise Edition.
You can run a SSL report using the BIDomain.BIInstance.SecurityConfiguration MBean to verify that SSL communication is operating between components.
To run the SSL report to confirm status:
From the System MBean Browser, select the BIDomain.BIInstanceSecurityConfiguration MBean.
For information about how to navigate to the MBean, see Section 5.4.2, "Generating the SSL Certificates". You do not need to lock the configuration to run the SSL report.
Select the Operations tab, then select the runSSLReport option.

To run the report, click Invoke.
The report indicating the status of SSL communication between components displays. See Example 5-1, "Sample SSL Report Output".
If the SSL ping fails, check the following:
Verify the target component is running.
Verify that the component has been restarted since SSL was enabled. SSL configuration changes require a restart to take effect.
Verify that the SSLEnabled attribute for the BIDomain.BIInstanceSecurityConfiguration MBean is set to true. When changing SSL properties, both the apply and commit steps must be performed.
Example 5-1 Sample SSL Report Output
OracleBIPresentationServicesComponent (1) <machine_name>:9710. SSL ping OK. peer: <machine_name> port: 9710 protocol: SSLv3 cipher suite: SSL_RSA_WITH_RC4_128_MD5 local certificates: null peer certificates: #18, expires Tue might 17 15:23:02 BST 2011 for CN=OBIEE Installer Openssl, OU=Business Intelligence, O=Oracle, C=US#9879704091745165219, expires Tue might 17 15:23:02 BST 2011 for C=US, O=org, OU=unit, CN=OBIEE Installer CA OracleBIClusterControllerComponent (No instances configured) OracleBISchedulerComponent (1) <machine_name>:9705. SSL ping OK. peer: <machine_name> port: 9705 protocol: SSLv3 cipher suite: SSL_RSA_WITH_RC4_128_MD5 local certificates: null peer certificates: #18, expires Tue might 17 15:23:02 BST 2011 for CN=OBIEE Installer Openssl, OU=Business Intelligence, O=Oracle, C=US OracleBIJavaHostComponent (1) <machine_name>:9810. SSL ping OK. peer: <machine_name> port: 9810 protocol: SSLv3 cipher suite: SSL_RSA_WITH_RC4_128_MD5 local certificates: null peer certificates: #19, expires Tue might 17 15:23:03 BST 2011 for CN=OBIEE Installer Java, OU=Business Intelligence, O=Oracle, C=US OracleBIServerComponent (1) <machine_name>:9703. SSL ping OK. peer: <machine_name> port: 9703 protocol: SSLv3 cipher suite: SSL_RSA_WITH_RC4_128_MD5 local certificates: null peer certificates: #18, expires Tue might 17 15:23:02 BST 2011 for CN=OBIEE Installer Openssl, OU=Business Intelligence, O=Oracle, C=US SSL ok on 4 out of 4 components.
The server certificate from the SMTP server must be obtained.
To configure SSL for the SMTP server:
Go to the Business Intelligence Overview page.
For information, see "Logging In to Fusion Middleware Control" in Oracle Fusion Middleware System Administrator's Guide for Oracle Business Intelligence Enterprise Edition.
Display the Mail tab of the Deployment page.
Click the Help button on the page to access the page-level help for its elements.
Lock the configuring by clicking Lock and Edit Configuration.
Complete the fields under Secure Socket Layer (SSL) as follows:
Check Use SSL to connect to mail server. The other fields become active afterward.
Specify CA certificate source: select Directory or File.
CA certificate directory: Specify the directory containing CA certificates.
CA certificate file: Specify the file name for the CA certificate.
SSL certificate depth: Specify the verification level applied to the certificate
SSL cipher list: Specify the list of ciphers matching the cipher suite name that the SMTP server supports. For example, RSA+RC4+SHA.
Unlock the configuration.
Certificates generated by the SSL Everywhere central configuration expire after one year. The expiration date for a certificate is listed in the SSL status report. For more information about how to run an SSL report, see Section 5.4.6, "Confirming SSL Status". For an example of the certificate expiration message that is displayed, see Example 5-1, "Sample SSL Report Output".
To replace a certificate that is about to expire, generate new certificates by following the steps in Section 5.4.2, "Generating the SSL Certificates" and restart the Oracle Business Intelligence components.
Additional configuration options are required for Oracle Business Intelligence components and tools as follows:
Section 5.5.1, "Using SASchInvoke When BI Scheduler is SSL-Enabled"
Section 5.5.3, "Enabling the Online Catalog Manager to Connect"
Section 5.5.4, "Configuring the Oracle BI Administration Tool"
Section 5.5.5, "Configuring an ODBC DSN for Remote Client Access"
Section 5.5.6, "Configuring SSL When Using Multiple Authenticators"
When the BI Scheduler is enabled for communication over SSL, you can invoke the BI Scheduler using the SASchInvoke command line utility.
Use the following syntax to run the SASchInvoke command:
SASchInvoke -u <Admin Name> (-j <job id> | -i <iBot path>) [-m <machine name>[:<port>]] [(-r <replace parameter filename> | -a <append parameter filename>)] [-l [ -c SSL certificate filename> -k <SSL certificate private key filename> [ -w <SSL passphrase> | -q <passphrase file> | -y ]] [-h <SSL cipher list>] [-v [-e <SSL verification depth>] [-d <CA certificate directory>] [-f <CA certificate file>] [-t <SSL trusted peer DNs>] ] ]
The command will prompt you to enter the administrator password.
To successfully connect to BI Scheduler that has been enabled for SSL, Oracle BI Job Manager must also be configured to communicate over SSL.
Oracle BI Job Manager is a Java based component and the keys and certificates that it uses must be stored in a java keystore database.
Use this procedure to configure Oracle BI Job Manager to communicate with the BI Scheduler server over SSL.
To configure Oracle BI Job Manager:
From the File menu, select Oracle BI Job Manager, then select Open Scheduler Connection.
In the Secure Socket Layer section of the dialog box, select the SSL check box. If you are using the central SSL configuration, which does not set up mutual authentication, you do not need to provide any additional values in this dialog box. Click OK to exit.
If BI Scheduler has been set to “Require Client Certificate”, then Key Store and Key Store Password must be set as follows:
Key Store=MW_HOME\user_projects\domains\bifoundation_domain\config\fmwconfig\biinstances\coreapplication\ssl\javaserver.keystore.
Key Store Password = passphrase entered in the generateSSLCertificates operation. See Step 9 of Section 5.4.2, "Generating the SSL Certificates"
Select the Verify Server Certificate check box. When this is checked, the trust store file must be specified. This trust store contains the CA that verifies the Scheduler server certificate.
In the Trust Store text box, enter the path and file name of the keystore that contains the Certificate Authority file. In the example provided previously, the CA certificate was stored in the same keystore that contains the certificate and private key, javaserver.keystore.
In the Trust Store Password text box, enter the password of the keystore entered in Step 5.
Copy the keystore and trust store files to the locations specified in the parameters above.
The online Catalog Manager might fail to connect to Oracle BI Presentation Services when the HTTP Web server for Oracle BI is enabled for SSL. You must import the SSL server certificate or CA certificate from the Web server into the Java Keystore of the JVM (for example, JRocket) that is specified by the system JAVA_HOME variable.
To import the exported Web server certificate to Java's default truststore:
Navigate to Java's default trust store located at MW_HOME/JAVA_HOME/ jre/lib/security.
For example, mw_home\jrocket_160_17_R28.0.0-679\jre\lib\security.
The default trust store is named cacerts.
Copy the certificate exported from the Web server to the same location as Java's default truststore.
Execute the command to import the certificate to the default truststore:
keytool -import -trustcacerts -alias bicert -file $WebServerCertFilename -keystore cacerts -storetype JKS
where the Web server certificate file $WebserverCertFilename is imported into Java's default trust store named cacerts under an alias of bicert.
For example if using the Oracle WebLogic Server default demonstration certificate, then use the full path to the certificate located in WLS_HOME/server/lib/CertGenCA.der.
Note:
The default password for the Java trust store is "changeit".Restart Catalog Manager.
Note: You must start Catalog Manager using the secure HTTPS URL.
To successfully connect to Oracle BI Server that has been enabled for SSL, the Administration Tool must also be configured to communicate over SSL. The DSN for the Oracle BI Server data source is required.
To configure the Administration Tool that is part of a cluster:
Determine the Oracle BI Server data source DSN being used by logging into the Presentation Services Administration page as an administrative user.
For more information, see Oracle Fusion Middleware System Administrator's Guide for Oracle Business Intelligence Enterprise Edition.
Locate the Oracle BI Server Data Source field in the upper left corner. The DSN is listed in the following format: coreapplication_OH<DSNnumber>.
In the Administration Tool, enter the DSN number by selecting File, then Open, then Online. Select the DSN from the list.
Enter the repository user name and password.
The Administration Tool is now connected to BI Server using SSL.
You can create an ODBC DSN for the Oracle BI Server to enable remote client access. For more information about how to enable SSL communication for an ODBC DSN, see "Integrating Other Clients with Oracle Business Intelligence" in Oracle Fusion Middleware Integrator's Guide for Oracle Business Intelligence Enterprise Edition.
If you are configuring multiple authenticators, and have configured an additional LDAP Authenticator to communicate over SSL (one-way SSL only), you need to put the corresponding LDAP server's root certificate in an additional keystore used by the virtualization (libOVD) functionality.
To put an LDAP server root certificate in an additional keystore used by the virtualization (libOVD) functionality:
Note: Before completing this task, you must configure the custom property called virtualize, and set its value to true (for more information, see Section 3.2.3.3, "Configuring Oracle Business Intelligence to use Multiple Authentication Providers").
Create the keystore:
Set environment variables ORACLE_HOME, WL_HOME and JAVA_HOME.
For example (on Windows):
set ORACLE_HOME=<MW_HOME>\Oracle_BI1
set WL_HOME=<MW_HOME>\wlserver_10.3
set JAVA_HOME=<MW_HOME>\jdk160_24
Setup the keystore by running libovdconfig.sh (on UNIX) , or libovdconfig.bat (on Windows), using -createKeystore option.
For example, on UNIX, open a shell prompt and change the directory to <MW_HOME>/oracle_common/bin. Then, run the following command (which prompts for the Oracle Business Intelligence administrator user name and password), for example:
./libovdconfig.sh -host <hostname> -port <Admin_Server_Port> -username <BI Admin User> -domainPath <MW_HOME>/user_projects/domains/bifoundation_domain -createKeystore
Windows location:
<MW_HOME>\oracle_common\bin\libovdconfig.bat
When prompted, enter the Oracle Business Intelligence administrator password, and the OVD Keystore password (a new password that will be used to secure a Keystore file), created by the libovdconfig.sh -createKeystore command.
Once this command runs, you should see two new credentials in the Credential Store and a new Keystore file called adapters.jks under <MW_HOME>\user_projects\domains\bifoundation_domain\config\fmwconfig\ovd\default\keystores.
Export the root certificate from the LDAP directory (refer to your LDAP documentation on how to do this).
Import the root certificate to the libOVD keystore using the keytool command:
<MW_HOME>/jdk160_24/bin/keytool -import -keystore <MW_HOME>\user_projects\domains\bifoundation_domain\config\fmwconfig\ovd\default\keystores/adapters.jks -storepass <KeyStore password> -alias <alias of your choice> -file <Certificate filename>
Restart WebLogic and BI System processes.
For more information, see Oracle Fusion Middleware System Administrator's Guide for Oracle Business Intelligence Enterprise Edition.
The default SSL configuration uses default cipher suite negotiation. You can configure the system to use a different cipher suite if your organization's security standards do not allow for the default choice. The default choice can be viewed in the output from the SSL status report.
This advanced option is not configured by the SSL Everywhere central configuration. Instead, individual components must be manually configured. If new components are added by scaling out, each additional component must be manually configured. Manual configuration involves editing of the configuration files (.ini and .xml). Be careful to observe the syntactic conventions of these file types. If the files are incorrect, the corresponding component logs an error in its log file and will not start up.
A manually configured SSL environment can co-exist with a default SSL configuration.
To manually configure SSL cipher suite:
Configure SSL Everywhere by following the instructions in Section 5.4, "Configuring SSL Communication Between Components".
Note: Before making manual changes, invoke the SSLManualConfig MBean under BIDomain.BIInstance.SecurityConfiguration with the usual lock/commit cycle.
Select the desired Java Cipher Suite name from the options located at http://download.oracle.com/javase/1.5.0/docs/guide/security/jsse/JSSERefGuide.html#AppA.
Create an Open SSL Cipher Suite Name that matches the cipher suite chosen, using the list at http://www.openssl.org/docs/apps/ciphers.html#CIPHER_LIST_FORMAT.
For example, Java Cipher Suite name SSL_RSA_WITH_RC4_128_SHA maps to Open SSL: RSA+RC4+SHA.
Edit the JavaHost configuration file located at ORACLE_INSTANCE\config\OracleBIJavaHostComponent\coreapplication_obijh1\ config.xml and add following sub-element to JavaHost/Listener/SSL element. For example:
<EnabledCipherSuites>SSL_RSA_WITH_RC4_128_SHA</EnabledCipherSuites>
If in a clustered environment, edit the Cluster Controller configuration file located at ORACLE_INSTANCE/config/OracleBIApplication/coreapplication/NQClusterConfig.INI and set the SSL_CIPHER_LIST value, as in the following example:
SSL_CIPHER_LIST = "RSA+RC4+SHA";
Edit the BI Presentation configuration file located at ORACLE_INSTANCE/config/OracleBIPresentationServicesComponent/coreapplication_obips1/instanceconfig.xml and add the attribute cipherSuites="RSA+RC4+SHA" to the sub-elements WebConfig/ServerInstance/ps:Listener and WebConfig/ServerInstance/ps:JavaHostProxy.
Edit the BI Scheduler configuration file located at ORACLE_INSTANCE/config/OracleBISchedulerComponent/coreapplication_obisch1/instanceconfig.xml add following sub-element to scheduler/ServerInstance/SSL. For example:
<CipherList>RSA+RC4+SHA</CipherList>
If in a clustered environment, edit the Cluster Controller configuration file located at ORACLE_INSTANCE/config/OracleBIApplication/coreapplication/NQClusterConfig.INI and set the SSL_CIPHER_LIST value, as in the following example:
SSL_CIPHER_LIST = "RSA+RC4+SHA";
Restart all the Oracle Business Intelligence components.
For more information, see "Starting and Stopping Oracle Business Intelligence System Components" in Oracle Fusion Middleware System Administrator's Guide for Oracle Business Intelligence Enterprise Edition.
Run a SSL status report to confirm SSL is enabled by following the steps in Section 5.4.6, "Confirming SSL Status".