| Oracle® Fusion Middleware Enterprise Deployment Guide for Oracle Identity Management (Oracle Fusion Applications Edition) 11g Release 1 (11.1.1.5.0) Part Number E21032-01 |
|
|
View PDF |
| Oracle® Fusion Middleware Enterprise Deployment Guide for Oracle Identity Management (Oracle Fusion Applications Edition) 11g Release 1 (11.1.1.5.0) Part Number E21032-01 |
|
|
View PDF |
This chapter describes how to install and configure Oracle Access Manager 11.1.1 for use in the Oracle Identity Management enterprise deployment.
This chapter includes the following topics:
Section 12.1, "Introduction to Installing Oracle Access Manager"
Section 12.3, "Configuring Oracle Access Manager on IDMHOST1"
Section 12.4, "Configuring Oracle Access Manager on IDMHOST2"
Section 12.5, "Configuring Oracle Access Manager to work with the Oracle Web Tier"
Section 12.10, "Backing Up the Application Tier Configuration"
Oracle Access Manager enables your users to seamlessly gain access to web applications and other IT resources across your enterprise. It provides a centralized and automated single sign-on (SSO) solution, which includes an extensible set of authentication methods and the ability to define workflows around them. It also contains an authorization engine, which grants or denies access to particular resources based on properties of the user requesting access as well as based on the environment from which the request is made. Comprehensive policy management, auditing, and integration with other components of your IT infrastructure enrich this core functionality.
Oracle Access Manager consists of various components, including Access Server, Access Manager Console, and WebGates. The Access Server, which includes both the Access Server and Identity Server, are the server components necessary to serve user requests for access to enterprise resources. The Access Manager console is the administrative console to the Access Server. WebGates are web server agents that act as the actual enforcement points for Oracle Access Manager. Follow the instructions in this chapter and Chapter 18, "Configuring Single Sign-on for Administration Consoles" to install and configure the Oracle Access Manager components necessary for your enterprise deployment.
This section contains the following topics:
The enterprise deployment described in this guide shows Oracle Access Manager using Oracle Internet Directory as the only LDAP repository. Oracle Access Manager uses a single LDAP for policy and configuration data. It is possible to configure another LDAP as the Identity Store where users, organizations and groups reside. For example, an Oracle Access Manager instance may use Oracle Internet Directory as its policy and configuration store and point to an instance of Microsoft Active Directory for users and groups.
In addition, the Identity Stores can potentially be front-ended by Oracle Virtual Directory to virtualize the data sources.
To learn more about the different types of directory configuration for Oracle Access Manager, consult the 11g Oracle Access Manager documentation at Oracle Technology Network. Customers considering these variations should adjust their directory tier and Oracle Access Manager deployment accordingly.
Before you configure Oracle Access Manager, ensure that the following tasks have been performed on IDMHOST1 and IDMHOST2:
Install Oracle WebLogic Server as described in Section 4.5.3.
Install Identity Management as described in Section 4.5.4.
Install Oracle Identity and Access Management as described in Section 4.5.7.
Install the Identity Store, as described in Chapter 7, "Extending the Domain with Oracle Internet Directory" or Chapter 10, "Preparing Directories Other than Oracle Internet Directory."
Install Oracle Virtual Directory, if required, as described in Chapter 9, "Extending the Domain with Oracle Virtual Directory."
This section contains the following topics:
Section 12.3.1, "Extending Domain with Oracle Access Manager"
Section 12.3.3, "Propagating the Domain Changes to the Managed Server Domain Directory"
Start the configuration wizard by executing the command:
MW_HOME/oracle_common/common/bin/config.sh
Then proceed as follows:
On the Welcome screen, select Extend an Existing WebLogic Domain. Click Next.
On the Select a WebLogic Domain screen, using the navigator, select the domain home of the WebLogic Administration Server, for example: ORACLE_BASE/admin/IDMDomain/aserver/IDMDomain.
Click Next
On the Select Extension Source screen, select Oracle Access Manager with Database Policy Store.
Click Next
The schedulerDS Multi Data Source is shown the Configure RAC Multi Data Sources screen, if you have Oracle Directory Integration Platform configured in your domain. Do not make any changes to this data source.
Click Next.
On the Configure JDBC Component Schema screen select the datasource OAM Infrastructure.
Select Configure selected data sources as RAC multi data sources in the next panel.
Click Next.
On the Configure RAC Multi Data Sources Screen:
Service Name: Service name of the database that contains the Oracle Access Manager repository (oamedg.mycompany.com)
User Name: EDG_OAM
Password: Password for user EDG_OAM
In the top right box, click Add to add the second Oracle RAC node.
Host Name: OIDDBHOST1-VIP
Instance Name: idmdb1
Port: 1521
Click Add again to add the second database host:
Host Name: OIDDBHOST2-VIP
Instance Name: idmdb2
Port: 1521
If you are using Oracle Database 11.2, replace the vip addresses with the 11.2 SCAN address.
Click Next.
On the Test Component Schema screen, the Wizard attempts to validate the data sources. If the data source validation succeeds, click Next. If it fails, click Previous, correct the problem, and try again.
On the Select Optional Configuration screen, select Managed Servers, Clusters and Machines.
Click Next
When you first enter the Configure Managed Servers screen, the configuration wizard creates a default Managed Server for you. AT this point, you must do two things:
Change the values of the default Managed Server.
Add a second Managed Server and supply values for it.
That is, you must change the existing entry and add one new entry.
Do not change the configuration of any Managed Servers which have already been configured as part of previous application deployments.
For the default Oracle Access Manager server (oam_server) entry, change the following values:
Name: WLS_OAM1
Listen Address: IDMHOST1
To add the second Oracle Access Manager Server, click Add and supply the following values:
Name: WLS_OAM2
Listen Address: IDMHOST2
Listen Port: 14100
Leave all the other fields at the default settings.
Click Next.
On the Configure Clusters screen, create a cluster by clicking Add. Supply the following information:
Name: cluster_oam
Cluster Messaging Mode: unicast
Leave all other fields at the default settings and click Next.
On the Assign Servers to Clusters screen, associate the Managed Servers with the cluster. Click the cluster name in the right pane. Click the Managed Server under Servers, then click the arrow to assign it to the cluster.
The cluster_oam has the Managed Servers WLS_OAM1 and WLS_OAM2.
Note:
Do not change the configuration of any clusters which have already been configured as part of previous application deployments.Click Next.
On the Configure Machines screen, create a machine for each host in the topology. Click the tab UNIX if your hosts use Linux or a UNIX-based operating system. Otherwise, click machines. Supply:
Name: The name of the host. Best practice is to use the DNS name. For example: idmhost1.mycompany.com and idmhost2.mycompany.com for the first and second nodes respectively.
Node Manager Listen Address: The DNS name of the machine. For example: idmhost1.mycompany.com and idmhost2.mycompany.com for the first and second nodes respectively.
Node Manager Port: A port for Node Manager to use.
If you have already configured Oracle Directory Integration Platform or ODSM, machines already exist for those hosts.
Click Next.
On the Assign Servers to Machines screen, indicate which Managed Servers to run on each of the machines you created.
Click a machine in the right pane.
Click the Managed Servers you want to run on that machine in the left pane.
Click the arrow to assign the Managed Servers to the machines. Repeat until all Managed Servers are assigned to machines. For example:
IDMHOST1: WLS_OAM1
IDMHOST2: WLS_OAM2
Click Next to continue.
On the Configuration Summary screen, click Extend to extend the domain.
Note:
If you receive a warning that says:CFGFWK: Server listen ports in your domain configuration conflict with ports in use by active processes on this host
Click OK.
This warning appears if Managed Servers have been defined as part of previous installs and can safely be ignored.
On the Installation Complete screen, click Done.
Restart WebLogic Administration Server as described in Section 19.1, "Starting and Stopping Oracle Identity Management Components."
By default, the IDMDomain Agent provides single sign-on capability for administration consoles. In enterprise deployments, WebGate handles single sign-on, so you must remove the IDMDomain agent. Remove the IDMDomain Agent as follows:
Log in to the WebLogic console using the URL: http://admin.mycompany.com/console
Then:
Select Security Realms from the Domain Structure Menu
Click myrealm.
Click the Providers tab.
Click Lock and Edit from the Change Center.
In the list of authentication providers, select IAMSuiteAgent.
Click Delete.
Click Yes to confirm the deletion.
Click Activate Changes from the Change Center.
Restart WebLogic Adminisration Server and ALL running Managed Servers, as described in Section 19.1, "Starting and Stopping Oracle Identity Management Components."
Start the WebLogic Managed Server WLS_OAM1 as described in Section 19.1, "Starting and Stopping Oracle Identity Management Components."
To propagate the start scripts and classpath configuration from the Administration Server's domain directory to the Managed Server domain directory, proceed as follows:
Run the pack command on IDMHOST to create a template pack. Type the following commands:
IDMHOST1> cd MW_HOME/oracle_common/common/bin IDMHOST1> ./pack.sh -managed=true -domain=ORACLE_BASE/admin/IDMDomain/aserver/IDMDomain -template=MW_HOME/templates/IDMDomain.jar -template_name=IDMDomain_Template
Run the unpack command on IDMHOST1 to unpack the propagated template to the domain directory of the Managed Server. Type the following command:
IDMHOST1> ./unpack.sh -domain=ORACLE_BASE/admin/IDMDomain/mserver/IDMDomain/ -template=MW_HOME/templates/IDMDomain.jar -overwrite_domain=true -app_dir=ORACLE_BASE/admin/IDMDomain/mserver/applications
Restart Managed Server WLS_OAM1.
This section contains the following topics:
Section 12.4.1, "Deploying Oracle Access Manager on IDMHOST2"
Section 12.4.2, "Updating Node Manager Properties File on IDMHOST2"
Section 12.4.3, "Starting Oracle Access Manager Server on IDMHOST2"
Once the configuration has succeeded on IDMHOST1, you can propagate the configuration to IDMHOST2. You do this by packing the domain on IDMHOST1, using the pack script, and unpacking it on IDMHOST2 using the unpack script. Both scripts reside in MW_HOME/oracle_common/common/bin.
In Step 1 of Section 12.3.3, "Propagating the Domain Changes to the Managed Server Domain Directory," you created a file called IDMDomain.jar in the MW_HOME/templates directory. Copy this file to IDMHOST2.
Unpack the file on IDMHOST2 by using the unpack utility:
./unpack.sh -domain=ORACLE_BASE/admin/IDMDomain/mserver/IDMDomain -template=MW_HOME/templates/IDMDomain.jar -overwrite_domain=true -app_dir=ORACLE_BASE/admin/IDMDomain/mserver/applications
If the Node Manager is not already started on IDMHOST2, perform the following steps to start it:
Start the Node Manager on IDMHOST2 to create the nodemanager.properties file by using the startNodemanager.sh script located under the MW_HOME/wlserver_10.3/server/bin directory.
Before you can start the Managed Servers by using the console, node manager requires that the property StartScriptEnabled is set to true. You set it by running the setNMProps.sh script located under the MW_HOME/oracle_common/common/bin directory.
prompt> MW_HOME/oracle_common/common/bin
prompt> ./setNMProps.sh
Stop and Start the Node Manager as described in Section 19.1, "Starting and Stopping Oracle Identity Management Components"so that the properties take effect.
Start Oracle Access Manager on IDMHOST2 by following the start procedures in Section 19.1, "Starting and Stopping Oracle Identity Management Components" for:
Node Manager (if it is not already started)
WebLogic Managed Server WLS_OAM2
This section describes how to configure Oracle Access Manager to work with the Oracle Web Tier.
This section contains the following topics:
Section 12.5.2, "Configuring Oracle HTTP Servers to Display Login Page"
Section 12.5.3, "Configuring Oracle HTTP Servers to Access Oracle Access Manager Console"
Before proceeding, ensure that the following tasks have been performed:
Configure Oracle Web Tier on WEBHOST1 and WEBHOST2 as described in Section 5.1, "Configuring the Oracle Web Tier."
Configure Oracle Access Manager on IDMHOST1 and IDMHOST2 as described in Section 12.3, "Configuring Oracle Access Manager on IDMHOST1" and Section 12.4, "Configuring Oracle Access Manager on IDMHOST2."
Configure the load balancer with a virtual host name (sso.mycompany.com) routing traffic to the webservers on WEBHOST1 and WEBHOST2 as described in Section 2.2.2, "Configuring Virtual Server Names and Ports on the Load Balancer."
Configure the load balancer with a virtual host name (admin.mycompany.com) routing traffic to webservers WEBHOST1 and WEBHOST2 Section 2.2.2, "Configuring Virtual Server Names and Ports on the Load Balancer."
On each of the web servers on WEBHOST1 and WEBHOST2 create a file called oam.conf in the directory ORACLE_INSTANCE/config/OHS/component/moduleconf.
This file must contain the following information:
<Location /oam>
SetHandler weblogic-handler
WebLogicCluster idmhost1.mycompany.com:14100,idmhost2.mycompany.com:14100
</Location>
It must also contain:
<Location /fusion_apps>
SetHandler weblogic-handler
WebLogicCluster idmhost1.mycompany.com:14100,idmhost2.mycompany.com:14100
</Location>
if the END user uses the FAAuthScheme to protect its Application Domain, that is, the FusionApplication.
On each of the web servers on WEBHOST1 and WEBHOST2, a file called admin.conf was created in the directory ORACLE_INSTANCE/config/OHS/component/moduleconf. (See Section 6.9, "Configuring Oracle HTTP Server for the WebLogic Administration Server".) Edit this file and add the following lines within the virtual host definition:
<Location /oamconsole> SetHandler weblogic-handler WebLogicHost ADMINVHN WebLogicPort 7001 </Location>
After editing the file should look like:
NameVirtualHost *:80
<VirtualHost *:80>
ServerName admin.mycompany.com:80
ServerAdmin you@your.address
RewriteEngine On
RewriteOptions inherit
RewriteRule ^/console/jsp/common/logout.jsp /oamsso/logout.html [PT]
RewriteRule ^/em/targetauth/emaslogout.jsp /oamsso/logout.html [PT]
# Admin Server and EM
<Location /console>
SetHandler weblogic-handler
WebLogicHost ADMINVHN
WeblogicPort 7001
</Location>
<Location /consolehelp>
SetHandler weblogic-handler
WebLogicHost ADMINVHN
WeblogicPort 7001
</Location>
<Location /em>
SetHandler weblogic-handler
WebLogicHost ADMINVHN
WeblogicPort 7001
</Location>
<Location /oamconsole>
SetHandler weblogic-handler
WebLogicHost ADMINVHN
WebLogicPort 7001
</Location>
</VirtualHost>
Restart the Oracle HTTP Server, as described in Section 19.1, "Starting and Stopping Oracle Identity Management Components."
Attempt to access the Oracle Access Manager application using the URL: https://sso.mycompany.com/oam
The Oracle Access Manager screen is displayed. A message saying Action Failed appears on the screen. You can ignore the message because all you are testing is that the Oracle Access Manager server can be accessed through the Load Balancer.
Attempt to Access the OAM console at: http://admin.mycompany.com/oamconsole
This section contains the following topics:
Section 12.6.1, "Changing Oracle Access Manager Security Model"
Section 12.6.2, "Configuring Oracle Access Manager by Using the IDM Automation Tool"
By default, Oracle Access Manager is configured to use the Open security model. Many applications require a different security model with a higher level of security.
If you want to change the security model, proceed as follows:
Log in to the OAM console at:
http://admin.mycompany.com/oamconsole
as the WebLogic administration user. Then perform the following steps:
Click the System Configuration tab.
Expand Server Instances under the Common Configuration section.
Click an Oracle Access Manager server, for example, WLS_OAM1, then select Open from the Actions menu.
Change the mode to the required security model, for example, Simple.
Click Apply.
The Confirm Edit dialog appears:
OAM Server instance wls_oam1 might be in use, are you sure you want to edit it?
Select Yes.
Repeat for each Oracle Access Manager server.
Click Access Manager Settings located in the Access Manager Settings section.
Select Open from the Actions menu. The access manager settings are displayed.
If you have changed the security mode to Simple, supply a global passphrase.
If you have changed the security mode to Cert Mode Configuration, provide the keystore details.
Click Apply.
Click the System Configuration tab.
Expand Access Manager Settings - SSO Agents.
Click OAM Agents and select Open from the Actions menu.
In the Search window, click Search.
Click IAMSuiteAgent in the search results. The Agent Properties are displayed.
Set the Security value to the new security model.
Click Apply.
Restart the managed servers WLS_OAM1 and WLS_OAM2 as described in Section 19.1, "Starting and Stopping Oracle Identity Management Components."
Note:
The Simple Security model is recommended if you plan to run Oracle Fusion ApplicationsNow that the initial installation is done and the security model set, the following tasks must be performed:
Oracle Access Manager must be configured to use an external LDAP Directory (idstore.mycompany.com).
Oracle Access Manager WebGate Agent must be created.
You perform these tasks by using idmConfigTool.
Perform the following tasks on IDMHOST1:
Set the environment variables MW_HOME, JAVA_HOME, IDM_HOME and ORACLE_HOME.
Set IDM_HOME to IDM_ORACLE_HOME.
Set ORACLE_HOME to IAM_ORACLE_HOME.
Create a properties file called config_oam1.props with the following contents:
WLSHOST: adminvhn.mycompany.com WLSPORT: 7001 WLSADMIN: weblogic IDSTORE_HOST: idstore.mycompany.com IDSTORE_PORT: 389 IDSTORE_BINDDN: cn=orcladmin IDSTORE_USERNAMEATTRIBUTE: cn IDSTORE_LOGINATTRIBUTE: uid IDSTORE_USERSEARCHBASE: cn=Users,dc=mycompany,dc=com IDSTORE_SEARCHBASE: dc=mycompany,dc=com IDSTORE_GROUPSEARCHBASE: cn=Groups,dc=mycompany,dc=com IDSTORE_OAMSOFTWAREUSER: oamLDAP IDSTORE_OAMADMINUSER: oamadmin PRIMARY_OAM_SERVERS: oamhost1.mycompany.com:5575,oamhost2.mycompany.com:5575 WEBGATE_TYPE: ohsWebgate10g ACCESS_GATE_ID: Webgate_IDM OAM11G_IDM_DOMAIN_OHS_HOST:sso.mycompany.com OAM11G_IDM_DOMAIN_OHS_PORT:443 OAM11G_IDM_DOMAIN_OHS_PROTOCOL:https OAM11G_OAM_SERVER_TRANSFER_MODE:simple OAM11G_IDM_DOMAIN_LOGOUT_URLS: /console/jsp/common/logout.jsp,/em/targetauth/emaslogout.jsp OAM11G_WG_DENY_ON_NOT_PROTECTED: false OAM11G_SERVER_LOGIN_ATTRIBUTE: uid OAM_TRANSFER_MODE: simple COOKIE_DOMAIN: .mycompany.com OAM11G_IDSTORE_ROLE_SECURITY_ADMIN: OAMAdministrators OAM11G_SSO_ONLY_FLAG: true OAM11G_OIM_INTEGRATION_REQ: false OAM11G_IMPERSONATION_FLAG:true OAM11G_SERVER_LBR_HOST:sso.mycompany.com OAM11G_SERVER_LBR_PORT:443 OAM11G_SERVER_LBR_PROTOCOL:https OAM11G_OIM_WEBGATE_PASSWD: password to be assigned to WebGate COOKIE_EXPIRY_INTERVAL: 120
Where:
WLSHOST and WLSPORT are, respectively, the host and port of your administration server. This is the virtual name.
WLSADMIN is the WebLogic administrative user you use to log in to the WebLogic console.
IDSTORE_HOST and IDSTORE _PORT are, respectively, the host and port of your Identity Store directory.
IDSTORE_BINDDN is an administrative user in the Identity Store directory.
IDSTORE_USERSEARCHBASE is the location in the directory where Users are stored.
IDSTORE_GROUPSEARCHBASE is the location in the directory where Groups are stored.
IDSTORE_SEARCHBASE is the location in the directory where Users and Groups are stored.
IDSTORE_OAMSOFTWAREUSER is the name of the user you created in Section 11.4.2, "Creating Users and Groups for Oracle Access Manager" to be used to interact with LDAP.
IDSTORE_OAMADMINUSER is the name of the user you created in Section 11.4.2, "Creating Users and Groups for Oracle Access Manager" to access your OAM Console.
PRIMARY_OAM_SERVERS is a comma separated list of your Oracle Access Manager Servers and the proxy ports they use.
Note:
To determine the proxy ports your OAM Servers use:Log in to the OAM console at http://admin.mycompany.com/oamconsole
Click the System Configuration tab.
Expand Server Instances under the Common Configuration section
Click an Oracle Access Manager server, such as WLS_OAM1, and select Open from the Actions menu.
Proxy port is the one shown as Port.
ACCESS_GATE_ID is the name you want to assign to the WebGate.
OAM11G_OIM_WEBGATE_PASSWD is the password to be assign to the WebGate.
OAM11G_IDM_DOMAIN_OHS_HOST is the name of the load balancer which is in front of the OHS's.
OAM11G_IDM_DOMAIN_OHS_PORT is the port that the load balancer listens on.
OAM11G_IDM_DOMAIN_OHS_PROTOCOL is the protocol to use when directing requests at the load balancer.
OAM11G_WG_DENY_ON_NOT_PROTECTED, when set to false, allows login pages to be displayed.
OAM_TRANSFER_MODE is the security model that the Access Servers function in, as defined in Section 12.6.1, "Changing Oracle Access Manager Security Model."
OAM11G_OAM_SERVER_TRANSFER_MODE is the security model that the Access Servers function in, as defined in Section 12.6.1, "Changing Oracle Access Manager Security Model."
OAM11G_IMPERSONATION_FLAG is set to True if you are using Oracle Fusion Applications.
OAM11G_IDM_DOMAIN_LOGOUT_URLS is set to the various logout URLs.
OAM11G_SSO_ONLY_FLAG confgures Oracle Access Manager 11g as authentication only mode or normal mode, which supports authentication and authorization.
If OAM11G_SSO_ONLY_FLAG is true, the Oracle Access Manager 11g server operates in authentication only mode, where all authorizations return true by default without any policy validations. In this mode, the server does not have the overhead of authorization handling. This is recommended for applications which do not depend on authorization policies and need only the authentication feature of the Oracle Access Manager server.
If the value is false, the server runs in default mode, where each authentication is followed by one or more authorization requests to the Oracle Access Manager server. WebGate allows the access to the requested resources or not, based on the responses from the Oracle Access Manager server.
OAM11G_SERVER_LBR_HOST is the name of the load balancer fronting your site. This and the following two parameters are used to construct your login URL.
OAM11G_SERVER_LBR_PORT is the port that the load balancer is listening on.
OAM11G_SERVER_LBR_PROTOCOL is the URL prefix to use.
COOKIE_DOMAIN is the domain in which the WebGate functions.
WEBGATE_TYPE is the type of WebGate agent you want to create.
OAM11G_IDSTORE_NAME is the Identity Store name. If you already have an Identity Store in place which you wish to reuse (rather than allowing the tool to create a new one for you), then set the value of this parameter to the name of the Identity Store you wish to reuse.
Configure Oracle Access Manager using the command idmConfigTool which is located at:
IAM_ORACLE_HOME/idmtools/bin
Note:
When you run theidmConfigTool, it creates or appends to the file idmDomainConfig.param. This file is generated in the same directory that the idmConfigTool is run from. To ensure that each time the tool is run, the same file is appended to, always run the idmConfigTool from the directory:
IAM_ORACLE_HOME/idmtools/bin
The syntax of the command on Linux is:
idmConfigTool.sh -configOAM input_file=configfile
The syntax on Windows is:
idmConfigTool.bat -configOAM input_file=configfile
For example:
idmConfigTool.sh -configOAM input_file=config_oam1.props
When the command runs you are prompted to enter the password of the account you are connecting to the Identity Store with. You are also asked to specify the passwords you want to assign to these accounts:
IDSTORE_PWD_OAMSOFTWAREUSER
IDSTORE_PWD_OAMADMINUSER
Sample command output:
Enter ID Store Bind DN password : Enter User Password for WLSPASSWD: Confirm User Password for WLSPASSWD: Enter User Password for OAM11G_IDM_DOMAIN_WEBGATE_PASSWD: Confirm User Password for OAM11G_IDM_DOMAIN_WEBGATE_PASSWD: Enter User Password for IDSTORE_PWD_OAMSOFTWAREUSER: Confirm User Password for IDSTORE_PWD_OAMSOFTWAREUSER: Enter User Password for IDSTORE_PWD_OAMADMINUSER: Confirm User Password for IDSTORE_PWD_OAMADMINUSER: The tool has completed its operation. Details have been logged to automation.log
Check the log file for any errors or warnings and correct them. A file named automation.log is created in the directory where you run the tool.
Restart WebLogic Administration Server as described in Section 19.1, "Starting and Stopping Oracle Identity Management Components."
Note:
After you runidmConfigTool, several files are created that you need for subsequent tasks. Keep these in a safe location.
The following files exist in the directory DOMAIN_HOME/output/Webgate_IDM. You need these when you install the WebGate software.
ObAccessClient.xml
logout.html
To Validate that this has completed correctly.
Access the OAM console at:
http://admin.mycompany.com/oamconsole
Log in as the Oracle Access Manager Admin User you created in Section 11.4.2, "Creating Users and Groups for Oracle Access Manager."
Click the System Configuration tab
Expand Access Manager Settings - SSO Agents - OAM Agents.
Click the open folder icon, then click Search.
You should see the webgate agent Webgate_IDM, which you created in Section 12.6.2, "Configuring Oracle Access Manager by Using the IDM Automation Tool."
After generating the initial configuration, you must edit the configuration and add advanced configuration entries.
Select System Configuration Tab
Select Access Manager Settings - SSO Agents - OAM Agent from the directory tree. Double-click or select the open folder icon.
On the displayed search page click Search to perform an empty search.
Click the Agent Webgate_IDM.
Select Open from the Actions menu.
Update the following information:
Deny if not Protected: Deselect.
Set Max Connections to 4 for all of the Oracle Access Manager servers listed in the primary servers list.
Click Apply.
Click Policy Configuration tab.
Double Click IAMSuiteAgent under Host Identifiers.
Click + in the operations box.
Enter the following information:
Host Name: admin.mycompany.com
Port: 80
Click Apply.
You can validate Oracle Access Manager by using the oamtest tool. To do this, perform the following steps:
Ensure that JAVA_HOME is set in your environment.
Add JAVA_HOME/bin to your PATH, for example:
export PATH=$JAVA_HOME/bin:$PATH
Change directory to:
IAM_HOME/oam/server/tester
Start the test tool in a terminal window using the command:
java -jar oamtest.jar
When the OAM test tool starts, enter the following information in the Server Connection section of the page:
Primary IP Address: idmhost1.mycompany.com
Port: 5575
Agent ID: Webgate_IDM
Agent Password: webgate password
Note:
if you configured simple mode, you must select Simple and provide the global passphrase.Click Connect.
In the status window you see:
[reponse] Connected to primary access server
In the Protected Resource URI section enter:
Scheme: http
Host: admin.mycompany.com
Port: 80
Resource: /oamconsole
Click Validate.
In the status widow you see:
[request][validate] yes
In the User Identity window, enter:
Username : oamadmin
Password: oamadmin password
Click Authenticate.
In the status window, you see:
[response][authenticate] yes
Click Authorize.
In the status window you see.
[response][authenticate] yes
The following is an example of a test:
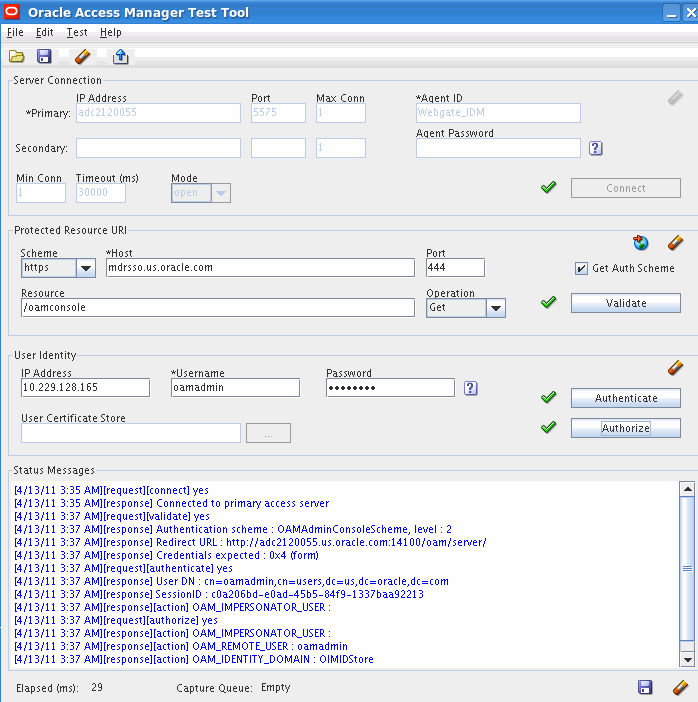
Repeat this test for each access server in the topology, remembering to change the connection details for each server.
If you are integrating other components, such as Oracle Identity Manager and Oracle Adaptive Access Manager, with Oracle Access Manager and Oracle Access Manager is using the simple security transport model, you must generate a keystore that can be used with those components. The procedure to do this is outlined in this section. Run it on IDMHOST1.
This section contains the following topics:
Section 12.9.1, "Creating an Empty Trust Store File Named oamclient-truststore.jks"
Section 12.9.2, "Importing the CA Certificate into the Trust Store"
To create this file, you use a tool called keytool that comes with the JDK (Java Development Kit). Before running any of the following commands, ensure that the JDK is in your path. For example
export JAVA_HOME=MW_HOME/jrockit_160_24_D1.1.2-4 export PATH=$JAVA_HOME/bin:$PATH
First, execute the command:
keytool -genkey -alias alias_name -keystore PathName_to_Keystore -storetype JKS
The command prompts you for a keystore password. This password MUST be same as the global pass phrase used in the Oracle Access Manager server. The command also prompts for information about the user and organization. Enter relevant information.
Example:
keytool -genkey -alias oam -keystore oamclient-truststore.jks -storetype JKS
Sample output:
Enter keystore password: Re-enter new password: What is your first and last name? [Unknown]: John Doe What is the name of your organizational unit? [Unknown]: MAA What is the name of your organization? [Unknown]: Oracle What is the name of your City or Locality? [Unknown]: Redwood Shores What is the name of your State or Province? [Unknown]: CA What is the two-letter country code for this unit? [Unknown]: US Is CN=John Doe, OU=MAA, O=Oracle, L=Redwood Shores, ST=CA, C=US correct? [no]: yes Enter key password for <oam> (RETURN if same as keystore password): Re-enter new password:
Then execute the command:
keytool -delete -alias alias_name -keystore oamclient-truststore.jks -storetype JKS
For example:
keytool -delete -alias oam -keystore oamclient-truststore.jks -storetype JKS
The command prompts for the keystore password you entered previously.
Oracle Access Manager 11g comes with a self-signed Certificate Authority that is used in Simple mode to issue certificates for the Access Client. This certificate must be added to the keystore you just created.
The certificate resides in the file cacert.der, which is located in the directory IAM_ORACLE_HOME/oam/server/config. Execute the following command to import a PEM/DER format CA certificate into the trust store. On Linux and UNIX-based systems, type:
keytool -importcert -file IAM_ORACLE_HOME/oam/server/config/cacert.der -trustcacerts -keystore PathName_to_keystore -storetype JKS
On Windows, type:
keytool -import -file IAM_ORACLE_HOME\oam\server\config\cacert.der -trustcacerts -keystore PathName_to_keystore -storetype JKS
Enter keystore password when prompted.
Example:
keytool -importcert -file /IAM_ORACLE_HOME/oam/server/config/cacert.der -trustcacerts -keystore oamclient-truststore.jks -storetype JKS
Sample output:
Enter keystore password: Owner: CN=NetPoint Simple Security CA - Not for General Use, OU=NetPoint, O="Oblix, Inc.", L=Cupertino, ST=California, C=US Issuer: CN=NetPoint Simple Security CA - Not for General Use, OU=NetPoint, O="Oblix, Inc.", L=Cupertino, ST=California, C=US Serial number: 0 Valid from: Wed Apr 01 05:57:22 PDT 2009 until: Thu Mar 28 05:57:22 PDT 2024 Certificate fingerprints: MD5: 05:F4:8C:84:85:37:DB:E3:66:87:EF:39:E0:E6:B2:3F SHA1: 97:B0:F8:19:7D:0E:22:6B:40:2A:73:73:1B:27:B2:7B:8D:64:82:21 Signature algorithm name: MD5withRSA Version: 1 Trust this certificate? [no]: yes Certificate was added to keystore
An SSL certificate and private key were generated when you ran the idmConfigTool command in Section 12.6.2, "Configuring Oracle Access Manager by Using the IDM Automation Tool." The SSL certificate and key are required for clients to communicate with Oracle Access Manager in Simple mode. The names of these files are, respectively, aaa_cert.pem and aaa_key.pem. They are located in the directory DOMAIN_HOME/output/Webgate_IDM on IDMHOST1, where DOMAIN_HOME is the Administration Server Domain home.
Execute the following commands to import the certificate and key file into the keystore oamclient-keystore.jsk.
Unzip the file importcert.zip, which is located in the directory:
IAM_ORACLE_HOME/oam/server/tools/importcert
For example:
cd IAM_ORACLE_HOME/oam/server/tools/importcert
unzip importcert.zip
Execute the command:
openssl pkcs8 -topk8 -nocrypt -in DOMAIN_HOME/output/Webgate_IDM/aaa_key.pem -inform PEM -out aaa_key.der -outform DER
The command prompts for a passphrase. Enter the password, which must be the global passphrase. This command creates the aaa_key.der file in the directory where the command is run
Example:
openssl pkcs8 -topk8 -nocrypt -in /u01/app/oracle/admin/IDMDomain/aserver/IDMDomain/output/Webgate_IDM/aaa_key.pem -inform PEM -out aaa_key.der -outform DER Enter pass phrase for oamclient-truststore.jks:
Then execute:
openssl x509 -in /u01/app/oracle/admin/IDMDomain/aserver/IDMDomain/output/Webgate_IDM/aaa_cert.pem -inform PEM -out aaa_cert.der -outform DER
This command creates the aaa_cert.der file in the directory where the command is run. This command does not generate any output.
Execute the command:
java -cp IAM_ORACLE_HOME/oam/server/tools/importcert/importcert.jar oracle.security.am.common.tools.importcerts.CertificateImport -keystore ssoKeystore.jks -privatekeyfile aaa_key.der -signedcertfile aaa_cert.der -storetype jks -genkeystore yes
This command creates the ssoKeystore.jks file in the directory where the command is run.
In this command, aaa_key.der and aaa_cert.der are, respectively, the private key and certificate pair in DER format.
Sample output:
Enter keystore password as prompted. This MUST be same as global pass phrase. The files ssoKeystore.jks and oamclient-truststore.jks can now be used to allow clients to connect to OAM.
Note:
The filesssoKeystore.jks and oamclient-truststore.jks are required when you integrate Oracle Access Manager running in Simple mode with Oracle Identity Management or Oracle Access Manager. When you integrate these components, you are asked to copy these files to the DOMAIN_HOME/config/fmwconfig directory. If you subsequently extend the domain on machines where these files have been placed using pack/unpack, you must recopy ssoKeystore.jks and oamclient-truststore.jks after unpacking.It is an Oracle best practices recommendation to create a backup after successfully completing the installation and configuration of each tier, or at another logical point. Create a backup after verifying that the installation so far is successful. This is a quick backup for the express purpose of immediate restoration in case of problems in later steps. The backup destination is the local disk. You can discard this backup when the enterprise deployment setup is complete. After the enterprise deployment setup is complete, you can initiate the regular deployment-specific Backup and Recovery process. For more details, see the Oracle Fusion Middleware Administrator's Guide.
For information on database backups, refer to the Oracle Database Backup and Recovery User's Guide.
To back up the installation to this point, follow these steps:
Back up the web tier as described in Section 5.5, "Backing up the Web Tier Configuration."
Back up the Oracle Access Manager database. This is a full database backup, either hot or cold. The recommended tool is Oracle Recovery Manager.
Back up the Administration Server domain directory as described in Section 6.15, "Backing Up the WebLogic Domain."
Back up the Oracle Internet Directory as described in Section 7.7, "Backing up the Oracle Internet Directory Configuration."
Back up the Oracle Virtual Directory as described in Section 9.10, "Backing Up the Oracle Virtual Directory Configuration."
For information about backing up the application tier configuration, see Section 19.4, "Performing Backups and Recoveries."