| Oracle® Real User Experience Insight User's Guide Release 6.0.1 for Linux x86-64 Part Number E16359-02 |
|
|
View PDF |
| Oracle® Real User Experience Insight User's Guide Release 6.0.1 for Linux x86-64 Part Number E16359-02 |
|
|
View PDF |
This chapter introduces you to RUEI. It explains how RUEI can provide you with powerful analysis of your network and business infrastructure. The roles used within RUEI, the appearance of the Reporter interface, and how you can customize it, are also highlighted.
RUEI should already have been successfully installed within your organization's network, and the Initial Setup Wizard run to provide information about the network infrastructure. The procedure to do this is described in the Oracle Real User Experience Insight Installation Guide.
While organizations are increasingly looking to explore Internet opportunities, they require accurate and up-to-date information regarding their Web traffic to assess the effectiveness of their Internet operations. What is required is a solution that records every user session, and translates complex Web data into meaningful and understandable statistics which can then be the basis of effective business and operational decisions.
RUEI is a powerful Web-based utility to report on real-user traffic requested by, and generated from, your network. It measures the response times of pages and transactions at the most critical points in your network infrastructure. Powerful session diagnostics allow Application Managers and IT technical staff to perform root-cause analysis.
It enables you to view server and network times based on the real-user experience, monitor your Key Performance Indicators (KPIs) and Service Level Agreements (SLAs), and trigger alert notifications on incidents that violate their defined targets.
You can implement checks on page content, site errors, and the functional requirements of your transactions. Based on this information, you can verify your business and technical operations. You can set custom alerts on the availability, throughput, and traffic of everything identified in RUEI.
RUEI comes with a library of powerful reports that provide both business-orientated and technical-orientated users with the information they need to make effective decisions. In addition, authorized users can quickly create their own reports or modify existing reports. Using these reports, they can directly interact with the Web data to gain a deep understanding of online usage behavior, as well as the overall status of Web applications. They can view these reports interactively, or receive them by e-mail.
Using RUEI's dynamic drill-down capabilities, you can quickly focus on any desired level of Web results.You can sort, filter, and export information. In addition, you can correlate any data across a wide variety of criteria, including time, client location, transaction, and user name.
The session diagnostics facility enables you to perform root-cause analysis of operational problems. It offers you the ability to assess any individual session, and review all the user's activity within that session.
The workstations that will access the RUEI user interface must have one of the following browsers installed:
Mozilla Firefox 3.0.
Internet Explorer 6 SP2.
Internet Explorer 7.
Note that JavaScript must be enabled. No other plug-ins are required.
In addition, the workstation should have a screen resolution of 1024 * 768 (or higher).
Note:
Ensure that any pop-up blocker within the browser has been disabled.In order for RUEI to start data monitoring and reporting, it must be configured with some information about your network infrastructure. Once completed, user traffic reporting is available. The following actions should have been performed before you start to use RUEI:
If the monitored traffic includes SSL-based sessions, the Collector will not be able to decrypt the SSL traffic unless the SSL keys are made available to the system. This is described in Section 8.3, "Managing SSL Keys". Of course, non-SSL traffic is unaffected by this requirement.
It is recommended that you specify the cookie structures used within your Web environment. Otherwise, session tracking is based on IP address and browser. This is described in Section 7.1, "Specifying Cookie Technology".
Within RUEI, user identification is first based on the HTTP Authorization field. After that, it is derived from the supplied POST argument specified in the application's definition. When this is not configured, the SSL client certificate is used (when available). The common name (CN) portion of it is used. Therefore, if you are using arguments within URLs, the item within these used for user identification must be specified in order to provide reliable results. This is described in Section 6.2.9, "Defining User Identification".
Page identification within RUEI is based on applications. Essentially, an application is a collection of Web pages. Note that information about any pages that could not be identified using application and page definitions is discarded and, therefore, not available through reports and the Data Browser. This is described in Section 6.1, "Naming Pages" and Section 6.2, "Defining Applications".
Transactions give you greater insight into how visitors experience your Web pages. This facility is described in Section 6.5, "Building Transactions".
Check the status of the Collector(s) by selecting System, then Status, and then Collector status. This is described in Section 9.2, "Viewing the Status of the Collectors". In addition, you can obtain an overview of the monitored network traffic by selecting System, then Status, and then Data processing. This is described in Section 9.7, "Viewing a Traffic Summary".
RUEI uses predefined roles and permissions to determine the actions that users can perform. For each of these roles, RUEI provides a set of reports and analyze tools to help them quickly and effectively meet their information requirements. These roles are explained in Table 1-1:
Table 1-1 Roles
| Role | Description |
|---|---|
|
Administrator |
This user performs the initial configuration of RUEI, and maintains the basic network-related configuration (such as mail settings and Collector attachments) used by the system. In addition, users assigned Administrator privileges act as first-level support for the system, and are responsible for such things as performing backups of the current configuration, the configuration of advanced system settings, and the administration of the other users authorized to work with the system. |
|
Security Officer |
This user is responsible for managing all system settings that are affected by the organization's network security policy. In particular, they:
|
|
Business users |
These users are concerned with evaluating visitor behavior according to business goals. As such, they use the business intelligence that the system offers them to monitor a wide variety of issues, such as identifying the most popular paths taken to your Web site, or how engaged visitors are on particular pages or sections. They may be concerned with improving customer satisfaction, retention, and loyalty, increasing conversion rates, or monitoring the effectiveness of Web site-based marketing activities. Based on assigned permissions, they use the dashboard functionality, as well as on-demand and mailed reports, to maintain an overview of the organization's operations. They can also use these reports and data exports as the basis for further analysis by IT specialists. |
|
IT users |
These users are concerned with supporting the IT and other technical information the system needs to monitor the Web environment. Typically, they are responsible for deeper analysis of failed SLAs or KPIs. They use the reporting and Data Browser facilities to their fullest to locate the reported anomaly or failure. For example, they might identify that failed user sessions are only occurring for users from a particular network domain. |
Depending on the configuration required by your organization, users can be authorized to perform combinations of these roles. There is no limit to the number of users who can be defined.
Super Administrator Versus Authorized Administrators
Be aware that there is one predefined RUEI user: the Super Administrator. Unlike all other users, their initial password is set using the set-admin-password.sh script, and is always locally authenticated. Depending on your operational requirements, other users can be assigned Administrator privileges. However, these users remain under the control of the Super Administrator. For clarity, when it is necessary to distinguish the Super Administrator from other users assigned Administrator privileges, the Super Administrator is referred to as the admin user.
Within RUEI, report categories and views within the Data Browser have a status assigned to them. This status can be Business-related, IT-related, or both. In this way, business and IT users can immediately locate the information that is relevant to them. For example, on entry to the Report library, the list of displayed reports for a business users is filtered to reflect the reports with which they will want to work.
For each user, other than Administrators, their Business and IT access permissions define the level of access they have to these items. These permissions are incremental. That is, each level contains all access permissions beneath it, as well as new ones. These are described in Table 1-2:
Table 1-2 Business and IT Access Permissions
| Access Level | Business User | IT User |
|---|---|---|
|
None |
The user has no access. |
The user has no access. |
|
OverviewFoot 1 |
The user can view their dashboards, the KPI overview, and alert history. |
The user can view their dashboards, the KPI overview, and alert history. |
|
Inquiry |
The user has read-only access to reports, and can create PDF downloads. |
The user has read-only access to reports, and can create PDF downloads. |
|
Analytical |
|
|
|
Full |
|
|
Footnote 1 A user who is not authorized to at least Overview level as either a Business or IT user cannot log on.
The creation and management of user roles and permissions is described in Section 9.15, "Managing Users and Permissions".
Each view within the Data Browser is either Business or IT-related (or both). Access to a view is only available for users with the relevant Analytical level permission. These are shown in Table 1-3.
Table 1-3 Analytical Level Permissions for Data Browser Views
| Category | View | Business | IT |
|---|---|---|---|
|
Applications |
Overall |
||
|
All pages |
X |
X |
|
|
All sessions |
X |
X |
|
|
All transactions |
X |
X |
|
|
Key pages |
X |
X |
|
|
URL diagnostics |
X |
||
|
Problem analysis |
|||
|
Failed URLs |
X |
||
|
Failed pages |
X |
X |
|
|
Slow URLs |
X |
||
|
Suites |
|||
|
E-Business SuiteFoot 1 |
X |
X |
|
|
E-Business Suite URL diagnosticsFootref 1 |
X |
||
|
JD EdwardsFootref 1 |
X |
X |
|
|
JD Edwards URL diagnosticsFootref 1 |
X |
||
|
Oracle ADF |
X |
X |
|
|
Oracle ADF diagnostics |
X |
||
|
PeopleSoftFootref 1 |
X |
X |
|
|
PeopleSoft URL diagnosticsFootref 1 |
X |
||
|
SiebelFootref 1 |
X |
X |
|
|
Siebel URL diagnosticsFootref 1 |
X |
||
|
WebLogic Portal |
X |
X |
|
|
WebLogic Portal URL diagnostics |
X |
||
|
Services |
Overall |
||
|
All functions |
X |
||
|
Problem analysis |
|||
|
Failed functions |
X |
Footnote 1 The group's associated accelerator package must be installed for it to be available. In addition, at least one suite for the group must have been defined.
To start your RUEI session, point your browser at the following URL:
https://Reporter/ruei
Note:
If you have not already received this information, contact your Administrator for the required IP address or host name part of the URL.The Logon dialog box shown in Figure 1-1 appears:
Enter your user name and password, and click Login. If you have not already been assigned a user name, contact the Administrator.
Note:
If you experience problems logging on, ensure that any pop-up blocking facility within your browser has been disabled.From the System menu, select Preferences (shown in Figure 1-2) to customize your personal settings:
The following options are available:
User: allows you to specify the settings that will be used for your sessions. You can control the national language used during your sessions, whether the reports you receive are sent in multiple e-mails or bundled into a single e-mail, and the module in which you want to start your sessions (for example, reports, favorites, or user management). These settings are explained in Section 9.15.3, "Modifying a User's Settings".
Formatting: allows you to specify how numeric values will be formatted in reports. You can specify the decimal point indicator, the character used as the thousand separator, and the date format (05 Feb 2008 or Feb 05, 2008).
Change password: allows you to change your system password. You are required to enter your current password, and to confirm the new password that you want to use.
Note:
According to your organization's security policies (described in Section 9.15.4, "Enforcing Password Security Policies"), you are required to regularly change your password. You will receive a warning each time you logon seven days prior to password expiration. If, during this time, you have not reset your password, your account will be locked. If you will be out of the office for more than seven days prior to your password expiring, it is strongly recommended that you reset your password prior to your absence.RUEI allows you to create a set of your own customized dashboards. A dashboard is a visual display of the most important information required to achieve an objective, consolidated and arranged on a single screen so that the information can be monitored at a glance. An example is shown in Figure 1-3.
Each of your currently defined dashboards is available via tabs at the top of the screen. The last tab (») provides an overview of the templates available to you to use as the basis for creating new dashboards.
Designing Effective Dashboards
When designing your dashboards, it is recommended you carefully consider the dashboard's appropriate content in terms of which data to report, and what visualizations to use. In particular, it is recommended you carefully consider the following points:
Is the dashboard's information content overloaded? Ideally, it should help you visually identify trends, patterns, and anomalies.
Which visualizations provide the clearest, most meaningful presentation of the data in the least amount of space?
Does the displayed information need to be refreshed in real-time and, if so, how often? Do the objectives it serves require real-time information?
Does the dashboard quickly point out something that deserves your attention, and might require action?
Dashboards and Templates
Dashboards are created based on templates. There are two types of templates: system and public. System templates are provided with the product installation, and cannot be modified. Public templates, on the other hand, are dashboard templates created and maintained by Administrators. They cannot be modified by any other user.
To create a new dashboard, do the following:
Click the Dashboard tab, and then click the last (») tab. The templates currently available to you are listed. An example is shown in Figure 1-4.
Figure 1-4 Example of Available Templates
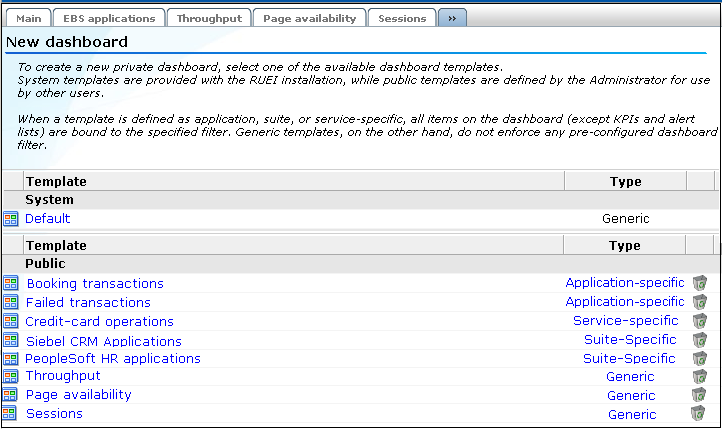
Click the template you want to use as the basis for the new template. A dialog similar to the one shown in Figure 1-5 appears.
Specify a name for the new dashboard. This must be unique across your dashboards, and is limited to a maximum length of 30 characters.
Select the template upon which the dashboard should be based. Alternatively, select the option "(none)" for the dashboard to be created from scratch. Note there is no link between the newly created dashboard and the template upon which it is based. That is, any future changes to the template are not applied to any dashboards created from it.
Select the dashboard's format. This can be based on one, two, or three columns. The percentages indicate the amount of available screen space allocated to each dashboard column.
Select the refresh interval. This can either be manual (that is, the dashboard is only refreshed when you click the Reload icon on the taskbar), or automatic (every 5, 10, or 15 minutes).
Within the Options tab, the Type menu specifies if the dashboard will be bound to a specific application, suite or Web service, or if it will be generic. The options within these menus depends on your assigned access permissions. The use of dashboard filters is described in Section 1.7.3, "Using Template Filters".
When ready, click Save.
Note:
You can have a maximum of 10 dashboards at any one time.Viewing Dashboards
Each of your currently defined dashboards is available by clicking its associated tab within the Dashboard tab. You can also click the Open in a new window icon on the taskbar. This is useful for viewing dashboards in a full-screen display, or for viewing several dashboards at the same time through resized and aligned windows.
Modifying Dashboards
You can modify a dashboard's properties by clicking the Edit icon within the dashboard taskbar. A dialog similar to the one shown in Figure 1-5 appears. Use this dialog to modify the dashboard's underlying template, name, layout, and refresh interval. The dashboard's layout and filter (described in Section 1.7.3, "Using Template Filters") are also reported.
You can also add or remove items to and from a dashboard, as well as modify existing items. This is described in the following section.
To add an item to a dashboard, do the following:
Select the required dashboard, and click the Add item icon on the taskbar. A dialog similar to the one shown in Figure 1-6 appears.
Specify a name for the new item. This must be unique to items within the selected dashboard.
Select the dashboard upon which the new item will appear. By default, this is the currently selected dashboard.
Optionally, you can specify the item's height in pixels. If you leave this field blank, the item is automatically sized within the available dashboard space.
Select the widget type to be shown. This can be one of the following:
Alert log: specifies the item represents a rolling list of the latest generated alerts. If this option is selected, you can use fields within the Options tab to specify how you want the alerts sorted, the order in which they should appear, and the maximum number of alerts that should be reported within the list. You can use the fields within the Filters tab to specify the category of KPI alerts listed, their status, and severity.
Data browser: specifies the item represents a data source within the Data Browser. If this option is selected, you can use the fields within the Options tab to specify the group from which the item should be derived (for example, All sessions or Failed pages), as well as its category and dimension level. The visualization (for example, values list or pie chart) and view level (for example, 5-minutes or year) can also be specified. In the case of a graphical visualization, you can use the Show legend check box to specify if In the case of a value list, you can specify the maximum number of listed values. The available options depend on the selected data source.
You can use the fields within the Filters tab to specify filters (based on selected dimensions) that should be applied to the selected data source. This widget is only available if you have been granted Analytical or Full access permissions (see Table 1-2).
Map: specifies the item should appear as a map highlighting the location of the selected data item (for example, client sessions). This is shown with a color coding scheme to represent the locations from where the selected data source originates. Hence, a bright red color indicates a country with a high level, while one with a white color indicates no selected data source activity originating from there. More detailed views are also available for Europe, USA, and Asia.
You can use the fields within the Filters tab to specify filters (based on selected dimensions) that should be applied to the reported data source. This item is only available if you have IT Analytical or Full access permissions (see Table 1-2).
Single KPI: specifies the item should report the current status of a specific KPI. If this option is selected, you can use the fields within the Options tab to specify the required KPI and a visualization for the item (gauge or graph).
Multiple KPIs: specifies the item should report the status of a selected number of defined KPIs. If you select this option, you can use the fields within the Options tab to specify the number and order of the reported KPIs, and the Filters tab to specify the KPI categories and statuses that should be reported.
Multiple SLAs: specifies the item should report whether selected categories of SLAs have achieved their yearly, monthly, weekly, and daily defined percentage levels. If you select this option, you can use the Options tab to specify how you want the reported SLAs sorted, and the Filters tab to specify the categories that should be reported. Note that if the Category field is left empty, all categories are reported.
If the new item is a single KPI with a graph visualization, an alert list, a Data Browser item, or a map, you can use the Time period menu to specify the period for which the reported data should refer. This can be the last five minutes, or the last 1, 6, 12, 24, or 36 hours. For all other item types, (a single KPI with a gauge visualization, or a multiple KPIs item) this menu is disabled, and the period reported for the item is derived from the KPI's defined sampling interval. This is described in Section 5.2, "Defining KPIs and SLAs".
When ready, click Save. The defined item is added to the top left-hand corner of the selected dashboard. You can drag and drop the item to finalize its position within the dashboard.
Note:
You can define a maximum of 35 items for a dashboard.Drilling-Down Into The Data Browser
In the case of Data Browser dashboard items, you can click the Browse icon located in the top right-hand corner of the item to obtain a complete view of the data from which the item is derived. The use of the Data Browser is described in Chapter 3, "Working With the Data Browser". Note this icon is only available if you have IT Analytical or Full access permissions (see Table 1-2).
Modifying Dashboard Items
You can click a dashboard item's title to edit it. A dialog similar to the shown in Figure 1-6 allows you to modify its properties. Depending on whether an item is derived from an application, service, or suite-specific template, and your access permissions, some of the fields within the dialog may be disabled. Note an item can be deleted by clicking the Remove icon within its title area.
Templates can either be defined as generic, or as application, service, or suite-specific. In the case of the later, all items on the dashboard (except KPIs and alert logs) are bound to a specified source. Generic dashboards do not have this restriction.
If a source-specific template is defined, each item on the dashboard is filtered on the specified source. If this filter cannot be applied for some reason (for example, because a specified application has since been deleted), or because the user does not have the necessary access level permissions, the item is replaced with a warning that the requested data could not be displayed.
The use of template filters has a number of advantages:
It minimizes template maintenance. For example, imagine that a dashboard template contains 20 items, all of which refer to the same application. Instead of having to modify all 20 items when you want to create the same template for another application, you only have to modify the template filter.
System users can be authorized to view data within a dashboard that they would not normally be able to view. For example, imagine that a user has only Business and IT Overview access level permissions. In this case, they do not have access to the Data Browser. However, through their user account definitions (described in Section 9.15, "Managing Users and Permissions"), they can be authorized to view selected data items for a specific application, service, or suite. However, they would be prevented from being able to view information derived other data sources.
Detection of Template Filters
Note that after an application, service, or suite has been configured, it must still be detected at least once in the monitored traffic before it can be used as a template filter.
You can add the current view within the Data Browser or the currently viewed KPI within the KPI overview facility to a dashboard by clicking the Add to dashboard icon. A dialog similar to the one shown in Figure 1-6 appears. You can use this dialog to finalize how the data source should be reported within the dashboard.
As explained earlier, public templates are created by Administrators for use by others users as the basis for their dashboards. To create a public template, do the following:
Click the Dashboard tab, then click an existing dashboard tab, and then click the Save as template icon on the taskbar. Note this option is only available to Administrators. The dialog shown in Figure 1-7 appears.
Figure 1-7 Create Dashboard Template Dialog
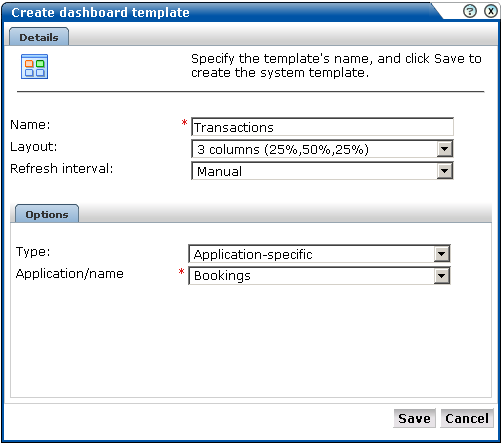
Specify a name for the new template. This must be unique across system templates.
Specify the template's format and refresh interval.
Within the Options tab, use the Type menu to specify whether the template should be bound to a specific application, service, or suite. The use of filters is described in Section 1.7.3, "Using Template Filters".
In the case of an application or service-specific template, specify the application or service to which it should be bound. In the case of a suite-specific template, specify the suite type (for example, PeopleSoft), and the configured suite. Note the options available within the Suite type menu depends on the accelerator packages installed on your system.
Note that users with Business and IT access permissions below Inquiry level need to be authorized to view information about specific applications, services, and suites. This is described in Section 9.15, "Managing Users and Permissions".
When ready, click Save. The newly created template immediately appears within the list of public templates. Access to the items on the template depends on the user's individual access permissions.
Modifying System Templates
System templates cannot be edited directly. If you need to modify a system template, it is recommended that you select the Disable option from the system template's context menu to make it unavailable to other users. You should then modify an existing dashboard (or create a new one) with your required modifications, save this as a public template, and then advice users to use the public template as an alternative to the system template.
After creating public templates for use by other system users, you can edit their properties by doing the following:
Click the Dashboard tab, and then click the last (») tab. The currently available public templates are listed. Select the Edit option from the required template's context menu. A dialog similar to the one shown in Figure 1-7 appears.
Use the fields available within the dialog to modify the templates name, layout, refresh interval, and data source as described Section 1.7.5, "Creating Public Templates". When ready, click Save.
As explained earlier, there is no direct link between a template and the dashboards created based upon it. Hence, any changes you make to a template are not reflected in existing dashboards created from it.