6 Managing Security Realms with JMX
A security realm comprises mechanisms for protecting WebLogic resources. Each security realm consists of a set of configured security providers, which are modular components that handle specific aspects of security. You can create a JMX client that uses the providers in a realm to add or remove security data such as users and groups. You can also create a client that adds or removes providers and makes other changes to the realm configuration.
The following sections describe managing security realms with JMX:
For more information about WebLogic Security, see Understanding Security for Oracle WebLogic Server.
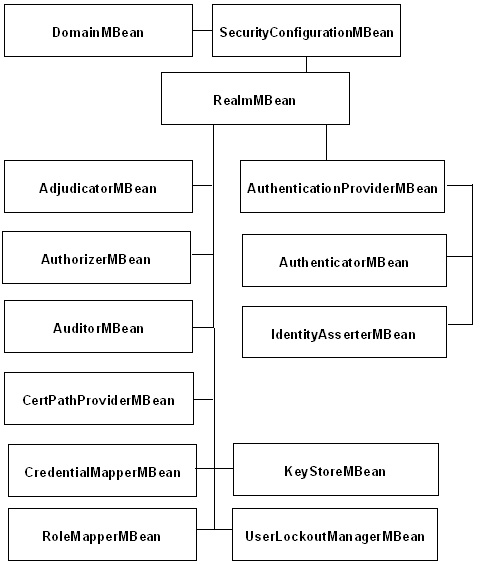
Understanding the Hierarchy of Security MBeans
Like other subsystems, the WebLogic Server security framework organizes its MBeans in a hierarchy that JMX clients can navigate without constructing JMX object names. However, the set of MBean types that are available in a security realm depends on which security providers you have installed in the realm, and the set of services that each security provider enables depends on how the provider was created.
The root of the security realm hierarchy is the RealmMBean. It contains all of the providers that have been configured for the realm. For example, its Authorizers attribute contains all authorization providers that have been configured for the realm. WebLogic Server installs a default set of security providers; therefore, by default the RealmMBean Authorizers attribute contains a DefaultAuthorizerMBean. However, you can uninstall these default providers and replace them with any number of your own providers or third-party providers. For information about the default security providers, see "Configuring WebLogic Security Providers" and "Configuring Authorization Providers" in Securing Oracle WebLogic Server.
Base Provider Types and Mix-In Interfaces
Each security provider must extend a base provider type. For example, DefaultAuthorizerMBean extends AuthorizerMBean, and any custom or third-party authorization provider also extends AuthorizerMBean. If a JMX client gets the value of the RealmMBean Authorizers attribute, the MBean server returns all MBeans in the realm that extend AuthorizerMBean. The JMX client can iterate through the list of providers and select one based on the value of its Name attribute or other criteria.
Base provider types can be enhanced by extending a set of optional mix-in interfaces. For example, if an authentication provider extends the UserEditorMBean, then the provider can add users to the realm.
Security MBeans
WebLogic Server's Security MBeans configure security providers in a security realm. The following tables describe the MBeans that configure different types of security providers.
-
Table 6-1 describes the MBeans that configure Authentication security providers, as well as the abstract MBean classes that Authentication providers must extend. In addition to the MBeans in this table, WebLogic Server includes configuration MBeans for each out-of-the-box Authentication provider.
-
Table 6-2 describes the MBeans that configure security providers, other than Authentication security providers.
-
Table 6-3 describes optional MBean mixin interfaces that security providers can support for management and utility purposes.
For more information about configuring WebLogic security providers, see "Configuring WebLogic Security Providers" and "Configuring Authorization Providers" in Securing Oracle WebLogic Server. Figure 6-1 illustrates where the MBeans are located in the configuration MBean hierarchy.
Table 6-1 MBeans for Authentication Security Providers
| This MBean... | Configures... |
|---|---|
AuthenticationProviderMBean |
The base MBean for all MBean implementations that manage Authentication providers. If your Authentication provider uses the WebLogic Security SSPI to provide login services, then your MBean must extend See "AuthenticationProviderMBean" in the Oracle WebLogic Server MBean ReferenceWebLogic Server MBean Reference. |
AuthenticatorMBean |
The SSPI MBean that all Authentication providers with login services must extend. This MBean provides a See "AuthenticatorMBean" in the Oracle WebLogic Server MBean Reference. |
IdentityAsserterMBean |
The SSPI MBean that all Identity Assertion providers must extend. This MBean enables an Identity Assertion provider to specify the token types for which it is capable of asserting identity. See "IdentityAsserterMBean" in the Oracle WebLogic Server MBean Reference. |
ServletAuthenticationFilterMBean |
The SSPI MBean that all Servlet Authentication Filter providers must extend. This MBean is just a marker interface. It has no methods on it. See "ServletAuthenticationFilterMBean" in the Oracle WebLogic Server MBean Reference. |
Table 6-2 MBeans for Other Security Providers
| This MBean... | Configures... |
|---|---|
AdjudicatorMBean |
The SSPI MBean that all Adjudication providers must extend. See "AdjudicatorMBean" in the Oracle WebLogic Server MBean Reference. |
DefaultAdjudicatorMBean |
Configuration attributes for the WebLogic Adjudication provider. See "DefaultAdjudicatorMBean" in the Oracle WebLogic Server MBean Reference. |
AuditorMBean |
The SSPI MBean that all Auditing providers must extend. See "AuditorMBean" in the Oracle WebLogic Server MBean Reference. |
DefaultAuditorMBean |
Configuration attributes for the WebLogic Auditing provider. See "DefaultAuditorMBean" in the Oracle WebLogic Server MBean Reference. |
AuthorizerMBean |
The SSPI MBean that all Authorization providers must extend. See "AuthorizerMBean" in the Oracle WebLogic Server MBean Reference. |
DeployableAuthorizerMBean |
The SSPI MBean that must be extended by all Authorization providers that can store policies created while deploying a Web application or EJB. See "DeployableAuthorizerMBean" in the Oracle WebLogic Server MBean Reference. |
DefaultAuthorizerMBean |
Configuration attributes for the WebLogic Authorization provider. See "DefaultAuthorizerMBean" in the Oracle WebLogic Server MBean Reference. |
CredentialMapperMBean |
The SSPI MBean that all Credential Mapping providers must extend. See "CredentialMapperMBean" in the Oracle WebLogic Server MBean Reference. |
DeployableCredentialMapperMBean |
The SSPI MBean that must be extended by all Credential Mapper providers that can store credential maps created while deploying a component. See "DeployableCredentialMapperMBean" in the Oracle WebLogic Server MBean Reference. |
DefaultCredentialMapperMBean |
Configuration attributes for the WebLogic Credential Mapping provider, a username/password Credential Mapping provider. See "DefaultCredentialMapperMBean" in the Oracle WebLogic Server MBean Reference. |
PKICredentialMapperMBean |
Configuration attributes for the PKI Credential Mapping provider, a key pair Credential Mapping provider. See "PKICredentialMapperMBean" in the Oracle WebLogic Server MBean Reference. |
SAMLCredentialMapperMBean |
Configuration attributes for the SAML Credential Mapping provider, a Security Assertion Markup Language Credential Mapping provider. See "SAMLCredentialMapperMBean" in the Oracle WebLogic Server MBean Reference. |
CertPathProviderMBean |
The base MBean for all certification path providers. See "CertPathProviderMBean" in the Oracle WebLogic Server MBean Reference. |
CertPathBuilderMBean |
The SSPI MBean that all certification path providers with CertPathBuilder services must extend. See "CertPathBuilderMBean" in the Oracle WebLogic Server MBean Reference. |
CertPathValidatorMBean |
The SSPI MBean that all certification path providers with CertPathValidator services must extend. See "CertPathValidatorMBean" in the Oracle WebLogic Server MBean Reference. |
CertificateRegistryMBean |
Configures and manages the certificate registry. It is both a builder and a validator. It supports building from the end certificate, the end certificate's subject DN, the end certificate's issuer DN and serial number, and the end certificate's subject key identifier. See "CertificateRegistryMBean" in the Oracle WebLogic Server MBean Reference. |
WebLogicCertPathProviderMBean |
The SSPI MBean that all certification path providers with CertPathBuilder services must extend. See "WebLogicCertPathProviderMBean" in the Oracle WebLogic Server MBean Reference. |
RoleMapperMBean |
The base MBean for Role Mapping providers. A Role Mapping provider for a non-deployable module must extend this MBean directly. A Role Mapping provider for a deployable module must extend the See "RoleMapperMBean" in the Oracle WebLogic Server MBean Reference. |
DeployableRoleMapperMBean |
The SSPI MBean that must be extended by Role Mapping providers that can store roles created while deploying a Web application or EJB. See "DeployableRoleMapperMBean" in the Oracle WebLogic Server MBean Reference. |
DefaultRoleMapperMBean |
Configuration attributes for the WebLogic Role Mapping provider. See "DefaultRoleMapperMBean" in the Oracle WebLogic Server MBean Reference. |
Table 6-3 MBean Mixin Interfaces for Security Providers
| This MBean... | Configures... |
|---|---|
ContextHandlerMBean |
Provides a set of attributes for ContextHandler support. An Auditor provider MBean can optionally implement this MBean. See "ContextHandlerMBean" in the Oracle WebLogic Server MBean Reference. |
GroupEditorMBean |
Provides a set of methods for creating, editing, and removing groups. An Authentication provider MBean can optionally implement this MBean. See "GroupEditorMBean" in the Oracle WebLogic Server MBean Reference. |
GroupMemberListerMBean |
Provides a method for listing a group's members. An Authentication provider MBean can optionally implement this MBean. See "GroupMemberListerMBean" in the Oracle WebLogic Server MBean Reference. |
GroupMembershipHierarchyCacheMBean |
Provides configuration attributes that are required to support the Group Membership Hierarchy Cache. An Authentication provider MBean can optionally implement this MBean. See "GroupMembershipHierarchyCacheMBean" in the Oracle WebLogic Server MBean Reference. |
GroupReaderMBean |
Provides a set of methods for reading data about groups. An Authentication provider MBean can optionally implement this MBean. See "GroupReaderMBean" in the Oracle WebLogic Server MBean Reference. |
MemberGroupListerMBean |
Provides a method for listing the groups that contain a member. An Authentication provider MBean can optionally implement this MBean. See "MemberGroupListerMBean" in the Oracle WebLogic Server MBean Reference. |
UserEditorMBean |
Provides a set of methods for creating, editing, and removing users. An Authentication provider MBean can optionally implement this MBean. See "UserEditorMBean" in the Oracle WebLogic Server MBean Reference. |
UserLockoutManagerMBean |
Lists and manages lockouts on user accounts. An Authentication provider MBean can optionally implement this MBean. See "UserLockoutManagerMBean" in the Oracle WebLogic Server MBean Reference. |
UserPasswordEditorMBean |
Provides two methods for changing a user's password. An Authentication provider MBean can optionally implement this MBean. See "UserPasswordEditorMBean" in the Oracle WebLogic Server MBean Reference. |
UserReaderMBean |
Provides a set of methods for reading data about users. An Authentication provider MBean can optionally implement this MBean. See "UserReaderMBean" in the Oracle WebLogic Server MBean Reference. |
UserRemoverMBean |
Provides a method for removing users. An Authentication provider MBean can optionally implement this MBean. See "UserRemoverMBean" in the Oracle WebLogic Server MBean Reference. |
RoleEditorMBean |
Provides a set of methods for creating, editing, and removing roles. A Role Mapping provider MBean can optionally implement this MBean. See "RoleEditorMBean" in the Oracle WebLogic Server MBean Reference. |
RoleListerMBean |
Provides a set of methods for listing data about roles. A Role Mapping provider MBean can optionally implement this MBean. See "RoleListerMBean" in the Oracle WebLogic Server MBean Reference. |
RoleReaderMBean |
Provides a set of methods for reading roles. A Role Mapping provider MBean can optionally implement this MBean. See "RoleReaderMBean" in the Oracle WebLogic Server MBean Reference. |
PolicyEditorMBean |
Provides a set of methods for creating, editing, and removing policies. An Authorization provider MBean can optionally implement this MBean. See "PolicyEditorMBean" in the Oracle WebLogic Server MBean Reference. |
PolicyListerMBean |
Provides a set of methods for listing data about policies. An Authorization provider MBean can optionally implement this MBean. See "PolicyListerMBean" in the Oracle WebLogic Server MBean Reference. |
PolicyReaderMBean |
Provides a set of methods for reading policies. An Authorization provider MBean can optionally implement this MBean. See "PolicyReaderMBean" in the Oracle WebLogic Server MBean Reference. |
PKICredentialMapEditorMBean |
Provides a set of methods for creating, editing, and removing a credential map that matches users, resources and credential action to keystore aliases and the corresponding passwords. A PKICredentialMapping provider MBean can optionally implement this MBean. See "PKICredentialMapEditorMBean" in the Oracle WebLogic Server MBean Reference. |
PKICredentialMapReaderMBean |
Provides a set of methods for reading a credential map that matches users and resources to keystore aliases and their corresponding passwords that can then be used to retrieve key information or public certificate information from the configured keystores. A PKICredentialMapping provider MBean can optionally implement this MBean. See "PKICredentialMapReaderMBean" in the Oracle WebLogic Server MBean Reference. |
UserPasswordCredentialMapEditorMBean |
Provides a set of methods for creating, editing, and removing a credential map that matches WebLogic users to remote usernames and their corresponding passwords. A Credential Mapping provider MBean can optionally extend this MBean. See "UserPasswordCredentialMapEditorMBean" in the Oracle WebLogic Server MBean Reference. |
UserPasswordCredentialMapExtendedReaderMBean |
Provides a set of methods for reading credentials and credential mappings. Credential mappings match WebLogic users to remote usernames and passwords. A Credential Mapping provider MBean can optionally extend this MBean. See "UserPasswordCredentialMapExtendedReaderMBean" in the Oracle WebLogic Server MBean Reference. |
UserPasswordCredentialMapReaderMBean |
Provides a set of methods for reading credentials and credential mappings. Credential mappings match WebLogic users to remote usernames and passwords. A Credential Mapping provider MBean can optionally extend this MBean. See "UserPasswordCredentialMapReaderMBean" in the Oracle WebLogic Server MBean Reference. |
ImportMBean |
Provides a set of methods for importing provider specific data. An optional mixin interface that any security provider may extend. See "ImportMBean" in the Oracle WebLogic Server MBean Reference |
ExportMBean |
Provides a set of methods for exporting provider specific data. An optional mixin interface that any security provider may extend. See "ExportMBean" in the Oracle WebLogic Server MBean Reference |
ListerMBean |
Provides a general mechanism for returning lists. Derived MBeans extend this interface to add methods that access the data of the current object in the list. An optional mixin interface that any security provider may extend. See "ListerMBean" in the Oracle WebLogic Server MBean Reference |
NameListerMBean |
Defines a method used to return lists of names. An optional mixin interface that any security provider may extend. See "NameListerMBean" in the Oracle WebLogic Server MBean Reference |
LDAPServerMBean |
Provides methods to get configuration parameters needed for connecting to an external LDAP server. An optional mixin interface that any security provider may extend. See "LDAPServerMBean" in the Oracle WebLogic Server MBean Reference |
ApplicationVersionerMBean |
The SSPI MBean that security providers extend to indicate that the provider supports versionable applications. An optional mixin interface that a RoleMapper, Authorizer, or CredentialMapper provider MBean may extend. See "ApplicationerVersionMBean" in the Oracle WebLogic Server MBean Reference |
Choosing an MBean Server to Manage Security Realms
When using JMX to manage security realms, you must use two different MBean servers depending on your task:
-
To set the value of a security MBean attribute, you must use the Edit MBean Server.
-
To add users, groups, roles, and policies, or to invoke other operations in a security provider MBean, you must use a Runtime MBean Server or the Domain Runtime MBean Server.
In addition, to prevent the possibility of incompatible changes, you cannot invoke operations in security provider MBeans if your client or another JMX client has an edit session currently active.
For example, the value of the MinimumPasswordLength attribute in DefaultAuthenticatorMBean is stored in the domain's configuration document. Because all modifications to this document are controlled by WebLogic Server, to change the value of this attribute you must use the Edit MBean Server and acquire a lock on the domain's configuration. The createUser operation in DefaultAuthenticatorMBean adds data to an LDAP server, which is not controlled by WebLogic Server. To prevent incompatible changes between the DefaultAuthenticatorMBean's configuration and the data that it uses in the LDAP server, you cannot invoke the createUser operation if you or other users are in the process of modifying the MinimumPasswordLength attribute. In addition, because changing this attribute requires you to restart WebLogic Server, you cannot invoke the createUser operation until you have restarted the server.
Working with Existing Security Providers
Because security providers can extend optional mix-in interfaces, not all security providers can perform all tasks. This flexibility enables your organization's security architect to design a realm for your security needs. The flexibility also makes the design of your JMX clients dependent upon the design and configuration of each realm.
For example, some realms might contain three types of Authentication providers:
-
One that extends
UserEditorMBeanto save administrative users to an LDAP server -
One that extends
UserEditorMBeanto save customers to a database management system -
One that does not extend
UserEditorMBeanand is used only to authenticate existing users
To work with the Authentication providers in this realm, your JMX client must be able to determine which one can add users to the appropriate repository.
Table 6-4 discusses techniques for finding a security provider that is appropriate for your task.
Table 6-4 Finding a Provider in the Realm
| Technique | Description |
|---|---|
|
Find by name |
Each security provider instance is assigned a short name when an administrator configures it for the realm. Your JMX client can look up all providers of a specific type (such as all Authentication providers) and choose the one that matches a name. For an example of such a JMX client, start the WebLogic Server Examples Server. From the Examples Server home page, click on "Extending a Realm Using JMX." The source for this JMX client is installed as
WL_HOME/samples/server/medrec/src/medrecEar/
adminWebApp/WEB-INF/src/com/bea/medrec/
actions/CreateNewAdminAction.java
where If you use this technique, consider saving the name of the security provider in a configuration file instead of hard-coding it in your JMX client. The configuration file enables system administrators to change the providers in the realm and update the properties file instead of requiring you to update and recompile the JMX client. |
|
Find by MBean type |
If the system administrator always wants to use the same type of provider for a task, then your JMX client can find the provider MBean that is of the specified type. For example, if the system administrator always wants to use a While this technique requires no user input, it assumes:
|
|
Use any provider that extends the mix-in interface you need |
You can create a JMX client that learns about the class hierarchy for each provider MBean instance and chooses an instance that extends the mix-in interface you need for your task. For example, your client can discover which Authentication provider extends Use this technique if you know that your security realm will contain only one MBean that extends the needed mix-in interface, or if it does not matter which one you use. |
Discovering Available Services
To create a JMX client that finds MBeans by type or mix-in interface:
-
Connect to a WebLogic Server Runtime MBean Server. See Make Remote Connections to an MBean Server.
All WebLogic Server instances maintain their own Runtime MBean Server, and you can connect to any server's Runtime MBean Server.
-
Get all security provider MBeans of a specific type in the realm (for example, get all Authentication provider MBeans):
-
Use either the
RuntimeServiceMBeanorDomainRuntimeServiceMBeanto navigate the following path through the WebLogic Server MBean hierarchy: -
DomainMBeantoSecurityConfigurationMBeantoRealmMBean. -
Get the value of the
RealmMBeanattribute that contains instances of the security provider type.For example, to get all Authentication providers, get the value of the
RealmMBeanAuthenticationProvidersattribute.
-
-
For each security provider MBean in the
RealmMBeanattribute, get the name of the MBean's class (see Example 6-1):-
Get the provider MBean's
javax.management.ModelMBeanInfoobject.Use
MBeanServerConnection.getMBeanInfo(Provider-MBean)where
Provider-MBeanis a provider MBean that you retrieved fromRealmMBean. -
Get the MBean info's
javax.management.Descriptorobject, and then get the value of the Descriptor'sinterfaceClassNamefield.
-
-
Use the WebLogic Server MBean type service to find all security provider MBean classes that extend a particular base type or mix-in interface (see Example 6-1):
-
Determine the fully-qualified interface name of the base type or mix-in interface.
Each entry in the WebLogic Server MBean Reference lists the fully-qualified interface name of WebLogic Server provider MBeans. If you use a third-party provider, refer to the third-party documentation for this information.
For example, the fully-qualified interface name of the
UserEditorMBeanmix-in interface isweblogic.management.security.authentication.UserEditorMBean. (See "UserEditorMBean" in the Oracle WebLogic Server MBean Reference.) -
Construct the
MBeanTypeServiceMBean's object name.The
MBeanTypeServiceMBean is always registered under the followingjavax.management.ObjectName:com.bea:Name=MBeanTypeService,Type=weblogic.management.mbeanservers.MBeanTypeService
-
Invoke the
MBeanTypeServiceMBean'sgetSubtypes( java.lang.StringbeanInterface)operation, where:beanInterfaceis the fully-qualified interface name that you determined in Step 1.The operation returns an array of
java.lang.Stringobjects.
-
-
Compare the output of the MBean type service with the class name of each provider MBean instance (see Example 6-1).
-
If the provider MBean's class implements or extends the interface from step 4a, invoke operations on the provider MBean.
Example 6-1 Example: Determine If a Provider MBean Instance Extends UserEditorMBean Mix-In Interface
ObjectName MBTservice = new ObjectName(
"com.bea:Name=MBeanTypeService,Type=weblogic.management.mbeanservers.
MBeanTypeService");
for (int p = 0; atnProviders != null && p < atnProviders.length; p++) {
ModelMBeanInfo info = (ModelMBeanInfo)
mBeanServerConnection.getMBeanInfo(atnProviders[p]);
Descriptor desc = info.getMBeanDescriptor();
String className = (String)desc.getFieldValue("interfaceClassName");
String[] mba = (String[]) mBeanServerConnection.invoke( MBTservice,
"getSubtypes", new Object[] {
"weblogic.management.security.authentication.UserEditorMBean" },
new String[] { "java.lang.String" });
boolean isEditor = false;
for (int i = 0; i < mba.length; i++) {
if (mba[i].equals(className)){
userEditor = atnProviders[p];
isEditor = true;
break;
}
if (isEditor = true) break;
}
}
Example: Adding Users to a Realm
The code example in Example 6-2 adds a user to a security realm and adds the user to the Administrators group by searching through all of the authentication providers in the realm and using the first one that extends UserEditorMBean.
Note the following about the code example:
-
Similar to the code in the MedRec example domain, the user name and password come from a JavaBean that was created from an Apache Struts action.
To see the MedRec code:
-
Start the WebLogic Server Examples Server.
-
From the Examples Server home page, click on "Extending a Realm Using JMX."
-
-
The code does not need to lock the domain's configuration because it is not modifying the configuration of the security MBean itself. Instead, it is invoking an operation in the default Authorization provider which saves security data in an LDAP server.
Example 6-2 Example: Adding Users to a Realm
public ActionForward createNewAdmin(ActionMapping mapping,
ActionForm form,
HttpServletRequest request,
HttpServletResponse response)
throws ClientException, Exception {
logger.info("Create New Admin");
CreateAdminBean user = (CreateAdminBean) form;
logger.debug(user.toString());
MBeanServerConnection mBeanServerConnection =
this.getDomainMBeanServerConnection(request);
ObjectName service = new
ObjectName("com.bea:Name=DomainRuntimeService,"+
"Type=weblogic.management.mbeanservers.domainruntime.
DomainRuntimeServiceMBean");
ObjectName domainMBean =
(ObjectName) mBeanServerConnection.getAttribute(service,
"DomainConfiguration");
ObjectName securityConfiguration =
(ObjectName) mBeanServerConnection.getAttribute(domainMBean,
"SecurityConfiguration");
ObjectName defaultRealm =
(ObjectName) mBeanServerConnection.
getAttribute(securityConfiguration, "DefaultRealm");
ObjectName[] atnProviders =
(ObjectName[]) mBeanServerConnection.getAttribute(defaultRealm,
"AuthenticationProviders");
ObjectName userEditor = null;
ObjectName MBTservice = new ObjectName(
"com.bea:Name=MBeanTypeService,Type=weblogic.management.mbeanservers.
MBeanTypeService");
for (int p = 0; atnProviders != null && p < atnProviders.length; p++) {
ModelMBeanInfo info = (ModelMBeanInfo)
mBeanServerConnection.getMBeanInfo(atnProviders[p]);
Descriptor desc = info.getMBeanDescriptor();
String className = (String)desc.getFieldValue("interfaceClassName");
String[] mba = (String[]) mBeanServerConnection.invoke( MBTservice,
"getSubtypes", new Object[] {
"weblogic.management.security.authentication.UserEditorMBean" },
new String[] { "java.lang.String" });
boolean isEditor = false;
for (int i = 0; i < mba.length; i++) {
if (mba[i].equals(className)){
userEditor = atnProviders[p];
isEditor = true;
break;
}
if (isEditor = true) break;
}
}
try {
mBeanServerConnection.invoke(
userEditor, "createUser",
new Object[] {user.getUsername(), user.getPassword(),
"MedRec Admininistator"},
new String[] {"java.lang.String", "java.lang.String",
"java.lang.String"}
);
} catch (MBeanException ex) {
Exception e = ex.getTargetException();
if (e instanceof AlreadyExistsException) {
logger.info("User, " + user.getUsername() + ", already exists.");
ActionErrors errors = new ActionErrors();
errors.add("invalidUserName",
new ActionError("invalid.username.already.exists"));
saveErrors(request, errors);
return mapping.findForward("create.new.admin");
} else {
logger.debug(e);
return mapping.findForward("create.new.admin");
}
}
try {
mBeanServerConnection.invoke(
userEditor, "addMemberToGroup",
new Object[] {"Administrators", user.getUsername()},
new String [] {"java.lang.String", "java.lang.String"}
);
mBeanServerConnection.invoke(
userEditor, "addMemberToGroup",
new Object[] {"MedRecAdmins", user.getUsername()},
new String [] {"java.lang.String", "java.lang.String"}
);
} catch (MBeanException ex) {
Exception e = ex.getTargetException();
if (e instanceof NameNotFoundException) {
logger.info("Invalid Group Name.");
ex.printStackTrace();
return mapping.findForward("create.new.admin");
} else {
logger.debug(e);
return mapping.findForward("create.new.admin");
}
}
logger.info("MedRec Administrator successfully created.");
return mapping.findForward("create.new.admin.successful");
}
Modifying the Realm Configuration
While security provider MBeans handle specific aspects of security, such as authentication and authorization, two other MBeans handle general, realm-wide and domain-wide aspects of security:
-
RealmMBeanrepresents a security realm. JMX clients can use it to add or remove security providers and to specify such behaviors as whether Web and EJB containers call the security framework on every access or only when security is set in the deployment descriptors. -
SecurityConfigurationMBeanspecifies domain-wide security settings such as connection filters and URL-pattern matching behavior for security constraints, servlets, filters, and virtual-hosts in the WebApp container and external security policies.
These two MBeans persist their data in WebLogic Server configuration files. Therefore, to modify attribute values in RealmMBean or SecurityConfigurationMBean, you must use the Edit MBean Server and ConfigurationManagerMBean as described in Chapter 5, "Managing a Domain's Configuration with JMX."