1 Planning For Enterprise Manager Ops Center
The Oracle Enterprise Manager Ops Center Concepts Guide (Part Number E17968) introduces you to the role the Enterprise Manager Ops Center software plays in monitoring and managing your hardware and software assets at local and remote sites throughout the life cycle of the assets. All asset types are not managed in the same way and some types of assets are limited in their ability to be managed. Also, some features of Enterprise Manager Ops Center might not be of use to your business. Use this document to plan how the Enterprise Manager Ops Center software operates at your site and to prepare for its installation.
When you are ready to install the software, get the product software and the product documentation from the Oracle Technology Network, as described in Obtaining the Product Software.
Will You Use Connected Mode or Disconnected Mode?
The Enterprise Manager Ops Center software operates in either Connected mode or Disconnected mode. Because you can change modes easily, you can also consider using a combination of Connected and Disconnected modes to maintain your data center. You can run the software in Disconnected mode until you need to access the Knowledge Base or third-party sites and then change to Connected mode. For example, to check for OS updates, change the Enterprise Controller to Connected Mode, connect to the Internet to check the Knowledge Base, and then return the Enterprise Controller to Disconnected Mode.
Connected Mode
The Enterprise Controller connects to the Internet to download OS updates, Oracle Solaris images, and updates for the Enterprise Manager Ops Center software itself. This mode of operation is called Connected mode and is the default setting. If your site policy does not allow an Internet connection, use operate Ops Center in Disconnected mode.
Figure 1-1 Enterprise Controller in Connected Mode
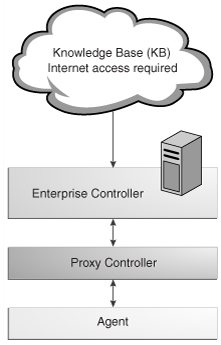
Description of "Figure 1-1 Enterprise Controller in Connected Mode"
Disconnected Mode
Disconnected mode enables you to use the Enterprise Manager Ops Center software in a secured environment without Internet access. To support provisioning and updating functions, you must load images and updates to the Enterprise Controller manually. Because the Enterprise Controller does not download new software automatically, you must plan how and when your site obtains updated software.
To obtain updates, images, and metadata, you run a product script on an Oracle Solaris system that is allowed to be connected to the Internet, download a static version of the Knowledge Base (KB), and copy it to the Enterprise Controller. For other supported operating systems, you can obtain software in a media format such as a DVD, and upload the software to the Local Content section of the product's software library, as illustrated in the following figure.
Figure 1-2 Enterprise Controller in Disconnected Mode
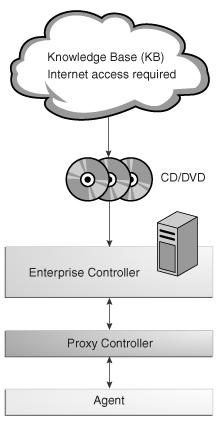
Description of "Figure 1-2 Enterprise Controller in Disconnected Mode"
Will You Manage Virtual Assets?
The Enterprise Manager Ops Center software can manage your virtual assets, such as Oracle Solaris Zones or Oracle VM Server for SPARC (logical domains). However, the software provides the most support to those zones and logical domains that are created using Enterprise Manager Ops Center actions.
Using Zones
When you use the Enterprise Manager Ops Center software's browser interface to create a zone, the software has full access to the zone configuration data and can manage the zone. This type of zone is called a greenfield zone. In contrast, any zone created using the zonecfg and zoneadm commands and later discovered by the Enterprise Manager Ops Center software are called brownfield zones; the product software is not aware of their zone configuration and can manage them in a limited way. Both types of zones are displayed in the product's Asset tree and are labeled by type. You can convert a brownfield zone to greenfield zone.
Do not mix the methods for administering zones. If you use both Enterprise Manager Ops Center actions and zone utility commands to administer zones, the Enterprise Ops Center software no longer recognizes the zone configuration and suspends its management of the zone.
Do not use the product software to create or manage zones if your site uses Live Upgrade to update operating systems of zones. Alternate boot environment (ABE) is not supported for greenfield zones.
Do not install a Proxy Controller in a non-global zone if you intend to use the product to provision operating systems or firmware.
You can install the Enterprise Controller software on a non-global zone but with these constraints:
-
The non-global zone must be a whole root zone.
-
The Proxy Controller cannot be located in the same zone.
-
The Proxy Controller cannot be located in the global zone that supports the Enterprise Controller's non-global zone.
-
No Agent software can be installed on the global zone that supports the Enterprise Controller's non-global zone.
Using Logical Domains
Use Oracle VM Server for SPARC to create multiple virtual machines on one physical hardware system. Unlike Oracle Solaris Zones that use the same operating system in all non-global zones, virtual machines can run instances of different operating systems, or different versions of the same operating system. These instances are called logical domains. Each logical domain has its own operating system, resources, and identity.
Although the Enterprise Manager Ops Center software can discover logical domains that were created using the ldm(1M) command and display them in the Assets tree, the product softare cannot manage them.
Do not install the Proxy Controller on a Linux system if you intend to provision logical domains. Use an Oracle Solaris x86 or SPARC system to run the Proxy Controller.
What Type of Network Configuration?
If you intend to provision OS or firmware on target systems on a subnet, configure one Proxy Controller on each subnet and then enable DHCP services on the Proxy Controller. Proxy Controllers provide the DHCP services that support the netboot or PXE boot operations of target systems.
Network Requirements
Use these guidelines to configure a network switch for a system running the Enterprise Manager Ops Center software.
-
Use an 8-port or 16-port Virtual LAN (VLAN) switch.
-
Discover and manage the switch.
-
If your site uses VLAN, create a separate VLAN for management and provisioning networks.
-
Disable spanning-tree protocols on the switch.
For Ethernet connectivity:
-
The management network must be a 10/100 connection.
-
The provisioning and data networks must be a 10/100/1000 (1 GB) connection.
In Connected mode,the Enterprise Controller also needs to get access to vendor Web sites to download updates or other software.
The following sections describe the communication requirements for the Enterprise Manager Ops Center software.
Network Requirements and Data Flow
At least one Proxy Controller must be installed and configured. You use the co-located Proxy Controller installed with the Enterprise Controller software or install one or more Proxy Controllers on separate systems. The following diagram shows a network configuration for a site running the Enterprise Manager Ops Center software in Connected mode and with two Proxy Controllers.
Figure 1-3 Network Ports and Protocols for Enterprise Controller in Connected Mode
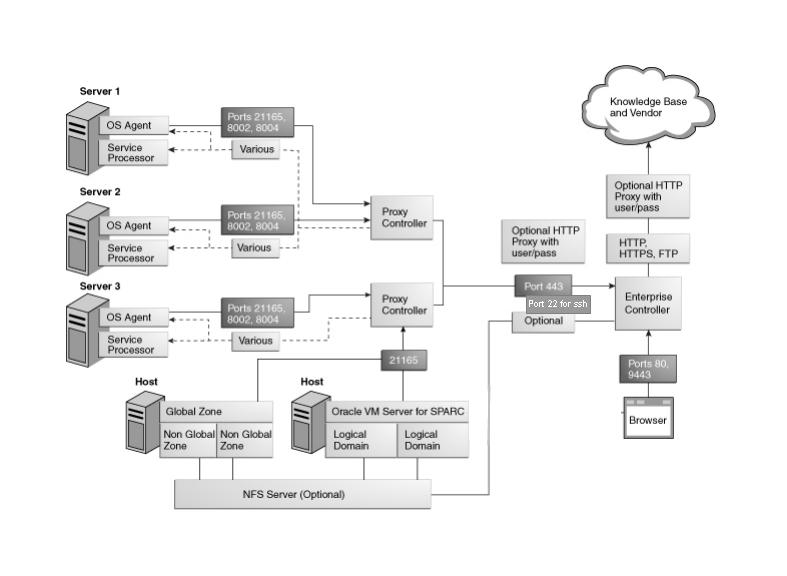
Description of "Figure 1-3 Network Ports and Protocols for Enterprise Controller in Connected Mode"
Ports and Protocols
The Enterprise Controller's default port is 443. If port 443 is in use, the Enterprise Controller uses Port 11165. The following table describes the required ports and their protocols.
Table 1-1 Required Ports and Protocols
| Communication | Protocol and Port | Purpose |
|---|---|---|
|
Browser to Enterprise Controller |
HTTPS, TCP 9443 |
Web interface |
|
Browser to Enterprise Controller |
HTTP, TCP 80 |
Redirects to port 9443 |
|
Proxy Controller to Enterprise Controller |
HTTPS, TCP 443 |
Proxy Controller pushes asset data to Enterprise Controller. Proxy Controller pulls data for jobs, updates, agents, and OS images. |
|
Proxy Controller to Targets |
FTP, TCP: Port 21 SSH, TCP: Port 22 Telnet, TCP: Port 23 DHCP, UDP: Ports 67, 68 SNMP, UDP: Ports 161, 162 IPMI, TCP+UDP: Port 623 Service Tags, TCP: Port 6481 ICMP ping: no port |
Discovery, bare-metal provisioning, management, and monitoring. For ICMP, proxy controllers send an echo request ping (Type 8) and receive either an echo reply ping (Type 0) or destination unreachable (Type 3). |
|
Enterprise Controller to Proxy Controller |
SSH: Port 22 |
During Proxy Controller installation or updates performed through the UI. |
|
Agent to Proxy Controller |
HTTPS, TCP: Port 21165 |
Agents push asset data to Proxy Controller. Agents pull data for jobs. |
|
Agent to Proxy Controller |
HTTPS, TCP: Port 8002 |
Agents pull updates from Proxy Controller. |
|
OS to Proxy Controller |
HTTP, TCP: Port 8004 |
OS provisioning job's completion status Linux OS provisioning Download of the agent archive file. Upload of the status messages about failed agent installations |
|
Java client to public APIs |
Transport Layer Security(TLS): Port 11172 |
JMX access from clients |
|
WMI to agent |
Port 11162 |
Communication to agent on Windows targets |
|
Proxy Controller to NFS server |
Port 2049 (default) See operating system documentation for configuring NFS |
Proxy Controller pulls provisioning images. |
|
Enterprise Controller |
Port 8005 |
Enterprise Controller in Disconnected mode |
Examples of Network Configurations
This section provides the example configurations and connectivity information for Enterprise Manager Ops Center. Other configurations are possible, such as using separate switches for each network. You can implement your network using any combination of VLANs and switches. Each network, whether management, provisioning, or data, must be assigned to separate VLANs.
-
Combined Management and Provisioning Network and a Separate Data Network
-
Combined Provisioning and Data Network and a Separate Management Network
Separate Management, Provisioning, and Data Networks
-
Separate networks provide the highest security and the lowest number of points of failure.
-
Additional NICs are needed to support this configuration.
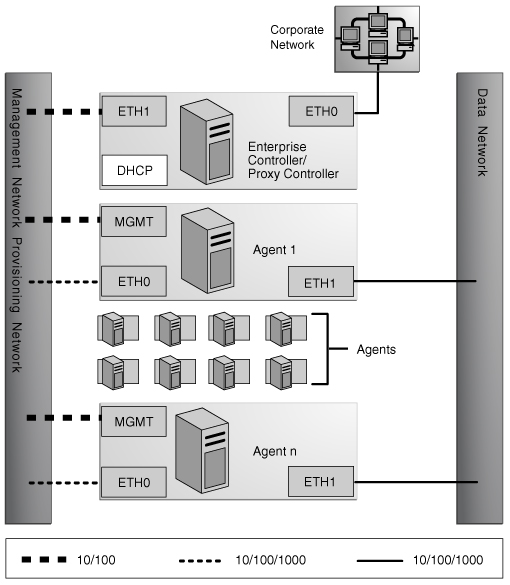
Figure 1-4 Separate Management, Provisioning, Data Networks
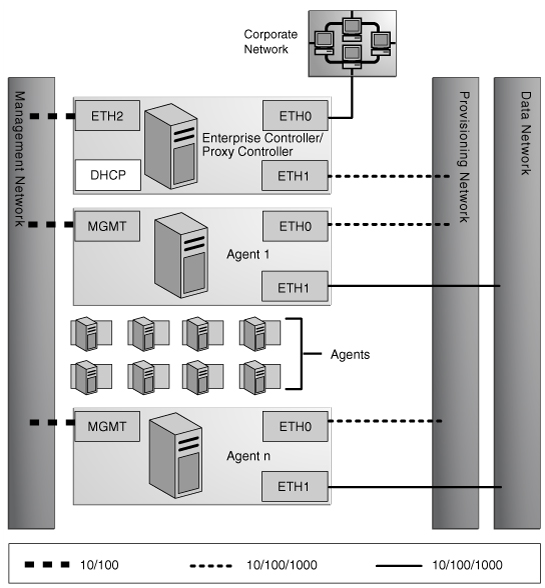
Description of "Figure 1-4 Separate Management, Provisioning, Data Networks"
A configuration with separate management, provisioning, and data networks has the following requirements:
-
Enterprise Controller or Proxy Controller
-
ETH0 connects the Enterprise Controller/Proxy Controller to the corporate network for external access. Configure the ETH0 IP address, netmask, and gateway to meet corporate connectivity requirements.
-
ETH1 connects the Enterprise Controller/Proxy Controller to the provisioning network and must be on the same network as the ETH0 connections of the agents. Only the Enterprise Controller/Proxy Controller and the agents must reside on the provisioning network. ETH1 must be a 1 Gb NIC interface.
-
ETH2 connects the Enterprise Controller/Proxy Controller to the management network and must be on the same network as the management port connections of the agents. Configure the ETH2 IP address, netmask, and gateway to enable connectivity to the agents' management port IP addresses. ETH2 must be a 100 Mb NIC interface.
-
The DHCP service allocates IP addresses to the agents for loading operating systems.
-
-
Agents
-
Each agent's management port connects the agent to the management network and must be on the same network as the ETH2 connection of the Enterprise Controller/Proxy Controller. The management port must be a 100 Mb connection.
-
ETH0 connects the agent to the provisioning network and must be on the same network as the ETH1 connection of the Enterprise Controller/Proxy Controller. ETH0 must be a 1 GB connection.
-
ETH1 connects the agent to the data network through the switch to provide corporate network access to the agent. ETH1 must be a 1 GB connection.
-
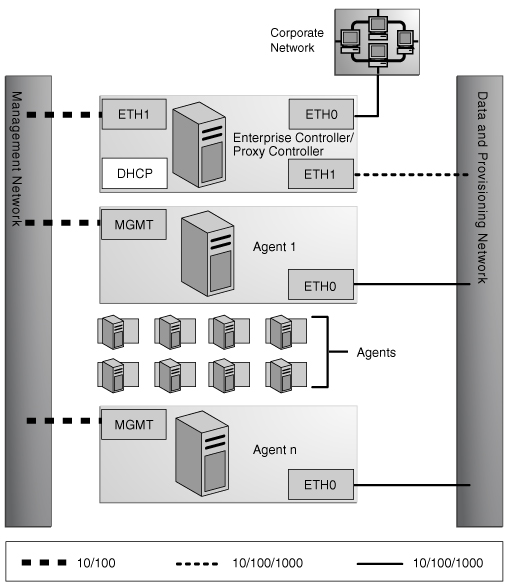
Combined Management and Provisioning Network and a Separate Data Network
-
Reduced system and network security.
-
No additional NIC is needed on the Enterprise Controller or Proxy Controller.
-
Enterprise Controller/Proxy Controller
-
ETH0 connects the Enterprise Controller/Proxy Controller to the corporate network to provide external access. Configure the ETH0 IP address, netmask, and gateway to meet corporate connectivity requirements.
-
ETH1 connects the Enterprise Controller/Proxy Controller to the management and provisioning network and must be on the same network as the MGMT and ETH0 connections of the agents. Only the Enterprise Controller/Proxy Controller and the agents must reside on the management and provisioning network. The ETH1 IP address, netmask, and gateway must be configured to enable connectivity to the agent's management port IP addresses. ETH1 must be a 1 Gb NIC interface.
-
The DHCP service allocates IP addresses to the agents for loading operating systems.
-
-
Agents
-
Each agent's management port connects the agent to the management and provisioning network and must be on the same network as the ETH1 connection of the Enterprise Controller/Proxy Controller. The management port must be a 100 Mb connection.
-
ETH0 connects the agent to the management and provisioning network and must be on the same network as the ETH1 connection of the Enterprise Controller/Proxy Controller. ETH0 must be a 1 GB connection.
-
ETH1 connects the agent to the data network through the switch to provide corporate network access to the agent. ETH1 must be a 1-GB connection.
-
Combined Provisioning and Data Network and a Separate Management Network
-
Enterprise Controller/Proxy Controller
-
ETH0 connects the Enterprise Controller/Proxy Controller to the corporate network to provide external access. Configure the ETH0 IP address, netmask, and gateway to meet corporate connectivity requirements.
-
ETH1 connects the Enterprise Controller/Proxy Controller to the provisioning and data network and must be on the same network as the ETH0 connections of the agents. Only the Enterprise Controller/Proxy Controller and the agents must reside on the data and provisioning network. ETH1 must be a 1 Gb NIC interface.
-
ETH2 connects the Enterprise Controller/Proxy Controller to the management network and must be on the same network as the management port connections of the agents. Configure the ETH2 IP address, netmask, and gateway to enable connectivity to the agent's management port IP addresses. ETH2 must be a 100 Mb NIC interface.
-
The DHCP service allocates IP addresses to the agents for loading operating systems.
-
-
Agents
-
The management port connects the agent to the management network and must be on the same network as the ETH2 connection of the Enterprise Controller/Proxy Controller. The management port must be a 100 Mb connection.
-
ETH0 connects the agent to the data and provisioning network to provide corporate network access to the agent. ETH0 connection must be on the same network as the ETH1 connection of the Enterprise Controller/Proxy Controller. ETH0 must be a 1 GB connection.
-
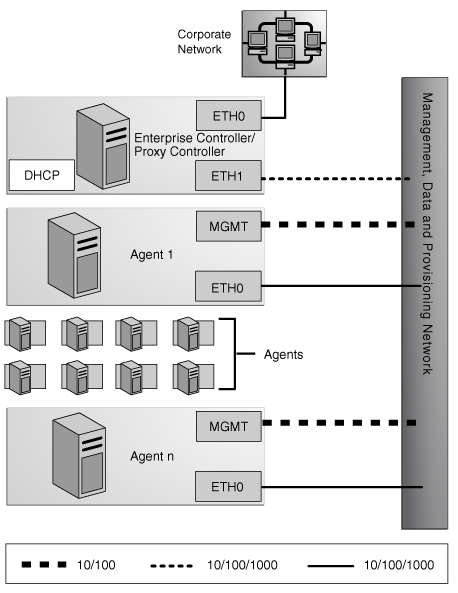
Combined Provisioning, Data, and Management Network
-
Least secure system and network
-
No additional NIC is needed for the Enterprise Controller/Proxy Controller.
-
Enterprise Controller/Proxy Controller
-
ETH0 connects the Enterprise Controller/Proxy Controller to the corporate network to provide external access. Configure the ETH0 IP address, netmask, and gateway to meet corporate connectivity requirements.
-
ETH1 connects the Enterprise Controller/Proxy Controller to the combined management, provisioning, and data network and must be on the same network as the MGMT and ETH0 connections of the agents. Only the Enterprise Controller/Proxy Controller and the agents must reside on the combined network. ETH1 must be a 1 GB NIC interface.
-
The DHCP service allocates IP addresses to the agents for loading operating systems.
-
-
Agents
-
Each agent's management port connects the agent to the management, provisioning, and data network and must be on the same network as the ETH1 connection of the Enterprise Controller/Proxy Controller. The management port must be a 100 MB connection.
-
ETH0 connects the agent to the management, provisioning, and data network, and must be on the same network as the ETH1 connection of the Enterprise Controller/Proxy Controller. ETH0 also connects the agent to the data network through the switch to provide external corporate network access to the agent. ETH0 must be a 1 GB connection.
-
Does Your Site Require High Availability?
The design for a High Availability (HA) architecture must consider all single points of failure, such as power, storage, and network connectivity in addition to the product software.
High Availability for the Enterprise Controller
For the Enterprise Manager Ops Center environment, high availability applies only to the Enterprise Controller and its co-located Proxy Controller. To avoid a single point of failure in the Enterprise Manager Ops Center software, transfer the /var/opt/sun/xvm directory structure manually from the primary Enterprise Controller to a secondary Enterprise Controller. The secondary Enterprise Controller duplicates the primary Enterprise Controller's configuration and takes over much of the primary Enterprise Controller's identity, including its host name, its IP addresses, its ssh keys, and its role. Only one Enterprise Controller, either primary or secondary, can be operational at any time.
In a high-availability configuration, the primary Enterprise Controller is configured and operational. The secondary Enterprise Controller is not configured and not operational. On the primary Enterprise Controller, the habackup program saves the data in the /var/opt/sun/xvm directory structure. The data that is saved by the habackup program is used by the harestore program on the secondary Enterprise Controller to duplicate how the primary Enterprise Controller is configured. The habackup program also backs up the local /etc/passwd file. The harestore program uses that information to change the ownership of the files to match the secondary Enterprise Controller's /etc/passwd file. However, root user passwords on Enterprise Controllers are not changed.
Requirements for High Availability
-
Use two systems of the same model and configured identically:
-
Processor class
-
Operating system
-
Oracle Enterprise Manager Ops Center software version, including updates
-
Network interfaces that are cabled identically to the same subnets
-
-
Add an asset tag to identify the primary Enterprise Controller and to distinguish it from the secondary Enterprise Controller. You can add a tag by using the Edit Asset action.
-
Maintain the secondary Enterprise Controller's system in the same way as the primary Enterprise Controller. The primary and secondary Enterprise Controllers must use the same version of Enterprise Manager Ops Center software. If you cannot use the Enterprise Manager Ops Center's user interface to verify the installed software versions at the time that you need to transfer functions to the secondary system, view the content of the
/n1gc-setup/.version.propertiesfile. Theproduct.versionproperty lists the specific revision of the installed software. For example:# cat /n1gc-setup/.version.properties #Note: This file is created at build time. #Wed Jun 30 15:28:45 PDT 2010 version=dev-ga date=2010/06/30 15\:28 build.variation=xvmopscenter product.version=2.6.0.1395 product.installLocation=/var/opt/sun/xvm/EnterpriseController_installer_2.6.0.1395
Verify that the product.version property lists the same version on the primary and secondary Enterprise Controllers before you perform a failover procedure.
Limitations
-
User accounts and data that are not associated with Oracle Enterprise Manager Ops Center are not part of the failover process. Only Oracle Enterprise Manager Ops Center data is moved between the primary and secondary Enterprise Controllers.
-
UI sessions are lost on failover.
-
The HA configuration applies only to the Enterprise Controller and its co-located Proxy Controller and not to other standalone Proxy Controllers.
High Availability for Storage Resources
You must configure the /var/opt/sun/xvm directory structure on a storage resource that you can move easily between the primary and secondary Enterprise Controllers. Consider dual-ported or SAN storage.
Note:
Configure the transferable storage on the system that you intend to use as the primary Enterprise Controller before you install the Enterprise Manager Ops Center software on that system.Storage devices that you use in an HA configuration must meet these requirements:
-
Storage must offer data redundancy capability, such as mirroring or RAID 5.
-
Storage must be transferable between the primary and secondary Enterprise Controller systems.
-
Storage must offer performance that is sufficient to support operations.
-
Storage must have the capacity to hold the data that the Enterprise Manager Ops Center software stores in the
/var/opt/sun/xvmdirectory structure.
A variety of storage solutions meet these criteria, including hardware RAID arrays and external JBODs. Storage can be attached directly to the Enterprise Controllers or through Storage Area Networks.
You must determine what storage solution offers the required capacity, performance, connectivity, and redundancy capabilities. Configuration procedures vary greatly among the available storage solutions, and among operating systems.
You must determine the specific failover procedures to use for the HA storage solution. Contact My Oracle Support to determine the procedures to use for your particular installation.
How Will You Use Enterprise Manager Ops Center?
The Enterprise Manager Ops Center software provides management for hardware, operating systems, firmware and OS updates, for both physical and virtual assets. The number of types of assets, the total number of assets, and the methods you use to manage the assets all affect resource utilization.
Although the Enterprise Controller and the Proxy Controller can run on the same server, this is recommended only for a small-scale site. In most cases, your site benefits from running the Proxy Controller on a separate system. At large-scale sites, deploy a Proxy Controller on each subnet.
Hardware Management
To monitor and manage hardware, the Proxy Controller discovers assets and then polls each asset for status and configuration changes. The Proxy Controller initiates network sessions to the hardtware's systems management Ethernet port, using specific server and chassis-type protocols. Using the product software to manage only hardware assets has a low resource impact on the system running the product software. However, network traffic from the Proxy Controller to the assets can have a high impact. Make sure Proxy Controllers are scaled appropriately.
Hardware Management + OS Provisioning
OS provisioning is executed from the Proxy Controller. The number of OS provisioning jobs that can occur in parallel is metered by the job management system, but OS provisioning also creates a load on the Proxy Controllers and network. Configure a Proxy Controller on each subnet to provision the assets on that subnet. In addition, configure an NFS server close to the Proxy Controllers to store the OS images and firmware images.
Hardware Management + OS Provisioning + Update Management
To update an OS, an agent must be deployed on the operating system and both update and provisioning jobs must be completed. The jobs include several transactions to determine the operating system's required updates and to perform the update operation. These operations increase the network utilization of the Enterprise Controller and Proxy Controllers.
Hardware Management + OS Provisioning + Update Management + Virtualization Management
The assets running Oracle Solaris 10 that you can manage include virtual hosts such as Oracle Solaris Zones and Oracle VM Server for SPARC (Sun Logical Domains.) Managing these virtual hosts exposes significantly large operating system metrics and increases the memory utilization of the Enterprise and Proxy Controllers. For information about deployment considerations and scaling guidelines, contact your Oracle representative.
What Are the System Requirements?
For the current list of hardware, operating systems, and browsers that Enterprise Manager Ops Center supports, see Supported Systems in the Enterprise Manager Ops Center Reference Guide.
Cache Requirements
The Enterprise Manager Ops Center software uses a central file cache for the following types of content:
-
For provisioning hardware or an OS:
-
Firmware
-
OS Images
-
-
For updating assets:
-
Knowledge Base metadata that specifies the updates for an OS distribution
-
Packages, patches, and RPM files that are a standard part of an OS update distribution
-
Custom content for a site such as software bundles, configuration files, or scripts.
-
The product software propagates content from the cache. For example, a Proxy Controller downloads content from the Enterprise Controller, and an agent downloads content from the Proxy Controller. After content is cached, it can be re-used without additional download operations.
Cache Recommendations for Connected Mode Configurations
The minimum cache size is 74 GB on Enterprise Controllers and Proxy Controllers. Increase the minimum cache size based on the following guidelines:
-
2 GB for software installation (in
/optand/var/tmp) -
4 GB for each OS image used for provisioning
-
10 GB for each distribution for updates
Because agents store only update content for their OS instance, they have reduced caching requirements. Allow 2 GB for both the product software and the update cache.
Example 1-1 Updating Several Operating System Assets
A user runs a job which updates five Oracle Solaris 10 SPARC OS agents managed by a single Proxy Controller. The Proxy Controller downloads and caches all of the patches required by the agents. Each agent downloads and caches the patches it requires. If an agent has cached several updates already, it re-uses those updates and downloads only what it needs from the Proxy Controller.
Example 1-2 Provisioning an Operating System Asset on Several Servers
A user runs a job to provision an OS image to three systems which are managed by two Proxy Controllers. Each Proxy Controller downloads and caches the image. The three systems do not cache the OS image, because they download and install the images from their respective Proxy Controllers.
The installations can use the co-located Proxy Controller, installed on the same OS instance as the Enterprise Controller. The Proxy and Enterprise Controllers share a global file cache so no additional disk space is required for the Proxy Controller's cache.
Example 1-3 Provision and Update Different Operating Systems on Several Servers
A site uses an Enterprise Controller with a co-located Proxy Controller and one other Proxy Controller, which together do the following:
-
Provision Oracle Solaris 10 X86 and SPARC (update 6) and Oracle Linux 5.5, using one ISO image for each distribution.
-
Update the Oracle Solaris 10 X86, Oracle Solaris 10 SPARC and Oracle Linux 5 32-bit X86 distributions. The remote Proxy Controller provisions and updates Oracle Solaris 10 systems on both SPARC and X86 architectures.
Both the Enterprise Controller with its co-located Proxy Controller and the remote Proxy Controller need a cache size of 74 GB, with 2 GB in /var/tmp and /opt, and 72 GB in /var/opt/sun/xvm. No additional caching is required on the Enterprise Controller because the co-located Proxy Controller shares its cache. The Enterprise Controller must have a minimum cache size of 44 GB:
-
30 GB for the three OS update distributions in
/var/opt/sun/xvm -
12 GB for the three OS images in
/var/opt/sun/xvm -
2 GB for the product software in
/var/tmpand/opt
The remote Proxy Controller must have a minimum cache of 30 GB:
-
20 GB for the two Oracle Solaris OS update distributions in
/var/opt/sun/xvm -
8 GB for the two Oracle Solaris OS images in
/var/opt/sun/xvm -
2 GB for the Ops Center software in
/var/tmpand/opt
Cache Requirements for Disconnected Mode Configurations
In Disconnected mode, the Enterprise Manager Ops Center software performs without an Internet connection. Images are managed in the same way as in Connected mode except it is not possible to download Oracle Solaris OS images. Administrators must cache images manually. For OS updates content, administrators must obtain and upload the content:
-
The Knowledge Base content is available as an archive file, which users can obtain by running the
harvesterscript. Depending on the settings, users can download the KB content only, or they can obtain content for one or more Oracle Solaris baselines.
-
Patches, packages, or RPMs must be uploaded to the Enterprise Controller.
Proxy Controllers and agents function the same way in both Connected and Disconnected modes and their cache requirements are the same.
Oracle VM Server for SPARC Requirements
To use Oracle VM Server for SPARC software, the target servers must meet the following requirements.
Hardware Requirements
See Supported Systems in the Enterprise Manager Ops Center Reference Guide for specific hardware requirements for the following servers:
-
Oracle SPARC T3-1 Server with Oracle VM Server for SPARC 2.0 software
-
UltraSPARC T2 Plus based servers
-
UltraSPARC T2 based servers
-
UltraSPARC T1 based servers only with versions of the Logical Domains software earlier than Version 1.3.
OS Requirements
-
Control domain – At least Oracle Solaris 10 10/09
-
Logical domain – At least Oracle Solaris 10 5/08
The operating system on all domains must be at least Oracle Solaris 10 9/10 OS.
OS Patch Requirements
-
Oracle Solaris 10 5/09: 141778-02 and 139983-04
-
Oracle Solaris 10 10/08: 139555-08
-
Oracle Solaris 10 5/08: 139555-08
For Oracle VM Server for SPARC 2.0 version, the following patches need to be installed on systems running an OS version earlier than Oracle Solaris 10 9/10:
-
Control domain: 141514-02
-
Control domain and logical domain: 142909-17
Firmware Requirements
The firmware requirements depend on the hardware that is used for Oracle VM Server for SPARC. The first release of firmware to include Oracle VM Server for SPARC support is System Firmware Version 6.4.x. To enable all the features of Oracle VM Server for SPARC 2.0, the minimum firmware version is 8.0.0.
The following system firmware patches are required:
-
For System Firmware Version 6.7.4:
-
Use 139434-03 for Sun Fire and SPARC Enterprise T2000 Servers
-
Use 139435-03 for Sun Fire and SPARC Enterprise T1000 Servers
-
Use 139436-02 for Netra T2000 Server
-
Use 139437-02 for Netra CP3060 ATCA Blade
-
Use 139438-03 for Sun Blade T6300 Server Module
-
-
For System Firmware Version 7.7.2:
-
Use 139439-04 for Sun SPARC Enterprise T5120 and T5220 Servers |
-
Use 139440-03 for Sun Blade T6320 Server Module |
-
Use 139442-06 for Netra T5220 Server |
-
Use 139441 for Sun Netra CP3260 ATCA Blade Server |
-
Use 139444-03 for Sun SPARC Enterprise T5140 and T5240 Servers |
-
Use 139445-04 for Netra T5440 Server |
-
Use 139446-03 for Sun SPARC Enterprise T5440 Server |
-
Use 139448-02 for Sun Blade T6340 Server Module |
-
Proxy Controller Requirements
Oracle VM Server provisioning is supported on Proxy Controllers running Solaris SPARC or Solaris x86. The Proxy Controller must be same one used during provisioning.
If the Proxy Controller is remote, the Enterprise Controller can run the Linux or Oracle Solaris OS. If the Proxy Controller is co-located, the Enterprise Controller and co-located Proxy Controller must run on an Oracle Solaris OS.
Oracle Solaris Zones Requirements
Oracle Solaris 10 systems that have non-global zones must have at least the following patches:
-
For SPARC systems:
-
124630-03: System Administration Applications, Network, and Core
-
122660-07: Zones patch, obsoleted by Solaris 10 8/07 kernel patch 120011-14
-
-
For x86 systems:
-
124631-03: System Administration Applications, Network, and Core
-
122661-07: Zones patch, obsoleted by Solaris 10 8/07 kernel patch 120012-14
-
Patches 122660-07 and 122661-07 are included on systems that are running at least Solaris 10 8/07.