| A P P E N D I X A |
|
Useful Tasks You Will Need to Perform on the Switches |
This appendix describes how to perform certain tasks that can only be performed at the command-line interface to a switch. You will need to refer to it when you are configuring the blade system chassis.
For instructions about logging into the switch command-line interface, see Chapter 2.
This chapter contains the following sections:
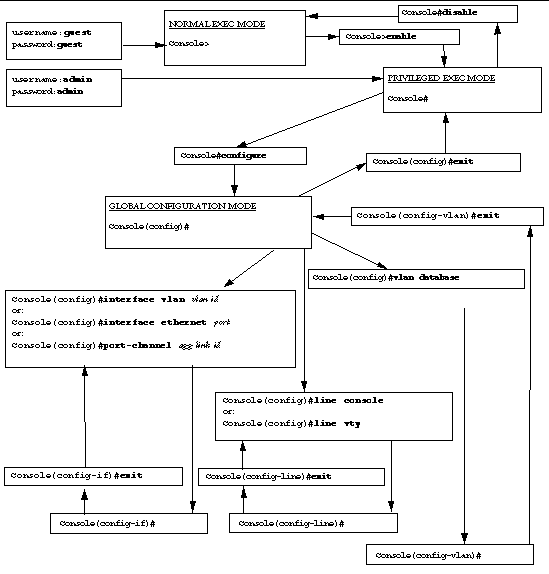
 To exit from the command-line interface on the switch and return to the System Controller's command-line interface, type the `#' character followed immediately by the `.' character.
To exit from the command-line interface on the switch and return to the System Controller's command-line interface, type the `#' character followed immediately by the `.' character.
Wherever you are in the switch's command-line interface, the `#.' escape seq uence will return you to the System Controller's command-line interface.
For example, type (but note that the characters are not echoed to the screen):
 To return to the switch's login prompt, type exit or end until you are at the Console# prompt, then type:
To return to the switch's login prompt, type exit or end until you are at the Console# prompt, then type:
You can use a telnet or a web connection to the switch provided that you have set up a DHCP server on your management network. To ensure that the switch receives the same address each time it boots (and makes a DHCP request), you need to specify the following client identifier on your DHCP server: SUNW,SWITCH_ID=serial number of chassis, 0 (for the switch in SSC0) or SUNW,SWITCH_ID=serial number of chassis, 1 (for the switch in SSC1).
To use the web-based GUI, type the IP address or host name of the switch into the web browser's URL field:
The standard port number for an http server is 80 but it is possible to configure the switch to use a different port number for http (for information about how to do this, refer to the Sun Fire B1600 Blade System Chassis Switch Administration Guide). If you have configured the switch to use a different http port number, you need to specify that number after the ip address of the switch in the URL field of your browser. For example, if a switch with the host name switch_1 has been configured to use port 75 for http, then to access it you would type:
To access the same switch by IP address, you would type the IP address followed by the port number (75). For example:
For more information about using the web-based GUI to configure the switch, refer to the Sun Fire B1600 Blade System Chassis Switch Administration Guide.
 To view information about using online help, type help at any time.
To view information about using online help, type help at any time.
 To view context-sensitive online help at any time, type ?.
To view context-sensitive online help at any time, type ?.
This displays a list of commands or parameters. If you are at a command prompt, typing ? will display a list of the commands available for the current command mode. If you want to know the parameter or parameters required for a command, type the first word of the command followed by ?. This will display a list of the parameters you can enter plus a description of each one. Each time you type ? after typing an incomplete command, the part of the command you have already typed will be echoed to the console. This means that you do not need to re-type that information.
Sample help information for using the vlan database command to go into the command mode for configuring VLANs is as follows:
Console(config)#vlan % Incomplete command. Console(config)#vlan ? database Enter VLAN database mode Console(config)#vlan database ? <cr> |
where <cr> indicates that there are no more parameters required and you must press [ENTER] to return to the command prompt.
For information about the factory default settings of the switch, refer to the Sun Fire B1600 Blade System Chassis Switch Administration Guide.
To restore the switch to its factory default settings, do the following:
1. To check whether the switch is using its factory default configuration, type:
If the bottom line of the output from this command includes "Factory_Default_Config.cfg" in the file name column, then the switch is using the default configuration.
2. To make the switch use its factory default configuration, type:
Console#configure Console(config)#boot system config Factory_Default_Config.cfg Console(config)#exit |
3. Reboot the switch using the factory default configuration.
4. When prompted for your user name and password, type admin for both.
A typical reason for resetting the switch is to revert to the startup configuration after making some changes to the running configuration (and you want to discard those changes).
Another reason for resetting the switch is if you have created or downloaded a new configuration file and you want to designate the new file as the default startup file.
|
Note - Before you reset the switch, save any changes you configuration changes you have made that you want to perserve. |
 To reset the switch from the switch's command line, type:
To reset the switch from the switch's command line, type:
 Alternatively, you can reset the switch from the System Controller's command-line.
Alternatively, you can reset the switch from the System Controller's command-line.
Type the following at the sc> prompt:
where n is 0 or 1depending on whether you are resetting SSC0 or SSC1.
1. Set the IP address and netmask by typing:
Console#configure Console(config)#interface vlan vlan id Console(config-if)#ip address ip address netmask Console(config-if)#exit |
2. To set the default gateway, type:
where ip address is the IP address of the device you are specifying as the default gateway.
3. To confirm the change you have made to the setting for the default gateway, type:
The : characters in the sample output above indicate omitted information. The setting for the default gateway is near the end of the output from the show running-config command.
By default the switch has a management VLAN (VLAN 2) containing its management port (NETMGT), and a data VLAN containing all other ports.
For more information about using VLANs, see Chapter 5, Chapter 6, and Chapter 7.
To create an additional VLAN, you need to set up the VLAN and add ports to it individually.
1. From the Console# prompt, type:
2. Go into vlan configure mode by typing:
where vlan identifier is a number from 1 through 4094.
4. To give the VLAN a name, type:
where vlan identifier is the number of the VLAN and name is the name you want to use for the VLAN.
5. Populate the VLAN by adding it to individual ports.
a. To do this, first return to configure mode by typing:
b. Then enter the configure interface mode by typing:
where port is the name of the port you want to include in the VLAN.
c. Add the VLAN to a port by typing:
d. Repeat Step a through Step c for each port you want to include on the new VLAN.
|
Note - Make sure you save any switch settings that you want to persist beyond the next reboot of the switch. |
 To save any changes you have made, copy the running configuration firmware to the startup configuration firmware.
To save any changes you have made, copy the running configuration firmware to the startup configuration firmware.
To do this, type the following in the switch console:
Console#copy running-config startup-config Startup configuration file name [default filename]:filename Write to FLASH Programming -Write to FLASH finish Success Console# |
where default filename is the current startup configuration file, and filename is the name you want to give to a new startup configuration file. If you type [ENTER] instead of specifying a new file name, the running configuration will be written to the current startup configuration file.
The procedure for transferring a configuration file from one switch to the other requires you to use TFTP. This means that to perform it you need to have a TFTP server available on your network. The instructions in this section tell you how to do this. They then tell you how to perform the file transfer.
If you have VLANs set up on the switch to separate the different regions of your network from each other, and you are also using IP Network Multipathing (IPMP) to give your server blades redundant connections to the network, you must make sure that the configuration of the second switch matches that of the first.
To ensure that the second switch inside the Sun Fire B1600 blade system chassis has the same configuration as the first, follow the instructions in this section.
To configure a Solaris system on your network to serve TFTP requests, do the following:
1. On the system that you intend to set up as the TFTP server, log in as root.
2. Use a text editor to un-comment the following line in the file /etc/inetd.conf:
3. On the same system create a TFTP home directory by typing the following at the Solaris prompt:
5. Verify that TFTP is working.
To do this, use TFTP to get a file from the /tftpboot directory. Follow the instructions below:
a. On the system that you are using as the TFTP server, copy any file (for example, the Solaris /etc/release file) to the /tftpboot directory.
To copy the /etc/release file, at the Solaris prompt, type:
where filename is the name of the file you intend to make available on the TFTP server.
b. Make the file you have just copied read-only by all:
where filename is the name of the file you intend to make available on the TFTP server
c. Get the file from the TFTP server you have created.
At the Solaris prompt on another system, type the following commands:
where tftp server is the host name or IP address of the system running the TFTP server you have set up, and filename is the name of the file you want to try getting from the TFTP server.
d. Still on the Solaris system that you used to initiate the get command, check the content of the file by typing:
where filename is the name of the file you have transferred from the TFTP server.
|
Note - that TFTP is not the same as FTP. It does not display the same error messages as FTP, and you cannot use the cd or ls commands (or indeed most other commands) that FTP allows you to use. |
When you have created a TFTP server, and you have also finished configuring the switch in SSC0 or SSC1, then duplicate the configuration of the switch you have configured onto the second switch.
To do this, follow the instructions below. (The instructions assume you are duplicating the configuration of the switch in SSC0 onto the switch in SSC1, but of course you can duplicate the switch in SSC1 onto the switch in SSC0.)
1. Configure switch 0 according to your requirements by following the instructions in Chapter 2, Chapter 3, Chapter 5, Chapter 6, and/or Chapter 7.
2. Save the configuration of switch 0 to a file called, for example, standard.cfg.
To do this, at the switch Console# prompt, type:
Console#copy running-config file Destination configuration file name: standard.cfg Write to FLASH Programming -Write to FLASH finish Success. Console# |
3. Upload the standard.cfg file to the TFTP server.
a. Log into the TFTP server as root.
b. Change directory to /tftpboot.
c. Create an empty file called standard.cfg.
4. Make the file read-writeable by all:
5. At the command-line interface to the switch, type:
Console#copy file tftp Choose file type: 1. config: 2.opcode: <1-2>:1 Source file name: filename TFTP server ip address: IP address Desitination file name: filename Console# |
where filename, in both cases, is standard.cfg (if this is the name of the file that you saved your switch configuration to) and IP address is the IP address of the TFTP server.
6. On the TFTP server, use a text editor to open the standard.cfg file.
Change the entry for the host name of switch 0 so that it contains the host name of switch 1:
If you have chosen to have manually assigned IP addresses for the switches, you must change the entry for the IP address and netmask so that it contains the IP address and netmask of switch 1 instead of those of switch 0:
If you are using DHCP there is no need to change the IP address and netmask or the DHCP client identifier. The IP address and netmask will be automatically assigned by your DHCP server. And the DHCP client identifier will be automatically assigned by the active System Controller whenever the switch is reset.
7. Save this file with a suitable name, for example, standard1.cfg.
8. Log into switch 1 and (if the switch has not been assigned an IP address by DHCP) set a temporary management IP address on it.
If you have already configured the login and password information for switch 1, then log in using these. If not, log in using the factory default user name (admin) and password (admin).
To set the IP parameters, follow the instructions in Section A.7, Setting the IP address, Netmask, and Default Gateway
9. Download standard1.cfg from the TFTP server to Switch 1.
Console#copy tftp file TFTP server ip address:IP address Choose file type: 1. config: 2.opcode: <1-2>:1 Source file name:standard1.cfg Destination file name:standard1.cfg Console# |
10. Make this the startup configuration for switch 1.
11. Reload the switch firmware.
If you have external data ports that connect to the same switch as each other, we recommend that you combine them into aggregated links. This gives you both resilience and added performance.
For example, if you had four separate connections to the same external switch and one of those connections failed because of a cabling fault, any communication on the broken connection would be lost. But, if you had set up an aggregated link to include all four connections to the external switch, then if one connection failed, communication would continue on the remaining connections defined in the aggregated link.
As long as no connections are broken, the integrated switch treats all the connections in the aggregated linkas a single high-bandwidth connection to the same network.
The following sample commands create an aggregated link using ports NETP2, NETP3, and NETP4:
The switch contains a packet filter which by default blocks all traffic from the server blades to the switch's management port (NETMGT). This prevents any possible hostile attack on your management network being launched from a server blade (in the event, for example, of a hacker gaining access to a blade from the public network). However, it means that you cannot communicate directly with the server blades through the management port until you have configured the packet filter to permit management traffic to pass from the server blades to the management port. This section tells you how to do that.
The instructions below tell you which commands to use to permit DHCP, BOOTP, TFTP, SUNRPC, SNMP and NFS frames to pass from the server blades through the packet filter to the management port. This is the minimum set of protocols required to enable the server blades to be administered via the management port:
1. Enable DHCP and BOOTP frames to pass through the packet filter.
2. Enable TFTP frames to pass through the packet filter.
Console#configure Console(config)#ip filter permit udp 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 69 Console(config)#ip filter permit udp 0.0.0.0 0.0.0.0 699-65535 0.0.0.0 0.0.0.0 699-65535 |
3. Enable SunRPC frames to pass through the packet filter.
Console#configure Console(config)#ip filter permit udp 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 111 Console(config)#ip filter permit tcp 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 111 |
4. Enable SNMP frames to pass through the packet filter.
5. Enable NFS frames to pass through the packet filter.
Console#configure Console(config)#ip filter permit udp 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 2049 Console(config)#ip filter permit tcp 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 2049 |
1. In the switch console, type:
where username is the name you want the user to type when he or she logs in.
The number 15 in the first command signifies that the new user will have access to Privileged Exec mode. (To give a user access to Normal Exec mode only, type 0 instead of 15.)
where username is the name you want the user to type when he or she logs in, and password is the new user's password.
The 0 in this command signifies that the value typed for password is not encrypted. If you were to enter the value in its encrypted form, you would have to indicate this by typing 7 instead of 0 before the encrypted text that you specify as the password. However, there is no reason to enter the password in its encrypted form. The switch stores the password
When you set up a password for a user, you need to tell the switch (by putting a 0 or a 7 on the command line) whether you are specifying the user's password in plain text or encrypted form. In practice, you will always specify a 0 to indicate plain text.
The parameter 7 (indicating encrypted text) exists only for the switch's internal use at boot-time. It stores its passwords in encrypted form for security in the configuration file, because the passwords are viewable in this file. For example, you can view them by typing:
However, at boot time the switch processes the passwords from this file. And it is therefore during the boot process that it needs to be able to distinguish between passwords presented as plain text and passwords presented as encrypted text. In other words, the parameter 7 that it is possible to enter on the command line (when you set up a user with a password) is of no practical use to you as a user.
|
Note - You cannot use passwords stored in encrypted form as a method of accessing the switch if you have forgotten the passwords, because you need password access to the switch in order to view them. |
The default user name (with full access rights) is admin.
The password is admin.
The default user name for guest access (with limited privileges) is guest.
The password is guest.
The default password for the enable command (to transition from guest access to full access) is super.
This section contains the following information:
 To check the IP address and VLAN Id of the management port, at the Console# prompt, type:
To check the IP address and VLAN Id of the management port, at the Console# prompt, type:
Console#show ip interface IP address and netmask: 129.156.223.215 255.255.255.0 on VLAN 2, and address mode: User specified. |
 To check the VLAN configuration of the switch, at the Console# prompt, type:
To check the VLAN configuration of the switch, at the Console# prompt, type:
 To find out who is logged into the command-line and web interfaces, at the Console# prompt, type:
To find out who is logged into the command-line and web interfaces, at the Console# prompt, type:
 To view the current configuration of the switch, at the Console# prompt, type:
To view the current configuration of the switch, at the Console# prompt, type:
If anybody has changed any switch settings since the last time the switch booted, the running configuration will differ from the start-up configuration
 To view the configuration that the switch received when it last booted (and which it will receive the next time it boots), at the Console# prompt, type:
To view the configuration that the switch received when it last booted (and which it will receive the next time it boots), at the Console# prompt, type:
 To find out firmware (and other) version information, at the Console# prompt, type:
To find out firmware (and other) version information, at the Console# prompt, type:
 To find out the MAC address, and to find out firmware (and other) version information, at the Console# prompt, type:
To find out the MAC address, and to find out firmware (and other) version information, at the Console# prompt, type:
Copyright © 2004, Sun Microsystems, Inc. All rights reserved.