Chapter 7 Setting Up and Using Proxies
A proxy is a user-level application that runs on the Screen. The main purpose of proxies is to provide content filtering (as opposed to packet filtering.) For example, you can use proxies to allow or deny Java applets access through the firewall. Proxies can also provide user authentication (as in the case of telnet traffic.)
Matching Proxy Rules
Each proxy is an independent program that reads its own policy file. The file for each proxy consists of policy rules selected by the compiler; rules may in turn reference data in the user database.
The following is the sequence of tests that each proxy makes to determine whether a rule matches:
-
Is the source address of the packet in source-address range in the policy rule?
-
Is the destination address of the final connection (that is, the host that the user specifies) in the destination address in the policy rule?
-
If the policy rule requires user authentication, did the user authenticate correctly? Is that user enabled?
-
Is this possibly-anonymous authenticated user included (either directly or by group membership) in the policy rule?
Note -
At present, there is no way for SunScreen High Availability systems to share proxy state. Proxies are not highly available.
Preparing to Use Proxies
SunScreen includes four proxies:
-
FTP
-
TELNET
-
SMTP
-
HTTP
Each one is a completely separate user-level application, although they use some shared data and policy files for authentication. Certain of the proxies provide some content filtering or user authentication or both. They allow or deny sessions based on the source and destination addresses.
The rc script, proxy, located in /etc/init.d and the symbolic link to /etc/rc2.d/S79proxy is used to start up the proxies as needed. The script checks if the proxy executable is in /opt/SUNWicg/SunScreen/proxies, that the corresponding policy file is in /etc/opt/SUNWicg/SunScreen/proxies, and that the policy file has a size larger than zero. If these requirements are not met, the proxy will not start.
Note -
The policy rule compiler uses this script to cause the each proxy to reread its policy file as needed.
You must disable the corresponding standard network service (if any) for HTTP proxies to function. If you have installed an HTTP daemon, you must disable it before the HTTP proxy will work. Conflicting standard Solaris servers for telnet, FTP, and SMTP are handled automatically during policy activation. See the SunScreen Reference Manual for further details.
Defining Proxy Data
You define proxy data on the Policy Rules page. The databases for proxies are the Java archive (Jar) Signatures, Jar hashes, the Proxy Users, and SMTP Proxy data.
Adding Jar Signatures and Jar Hashes
Make sure that you have set Medium Security for HotJava for both Signed and Unsigned Java as the default security settings. If you are using another browser, see the documentation that came with it.
You administer the Screen through any browser that supports Java and is compliant with Java Developers Kit (JDK) 1.1. Because Netscape Navigator and Internet Explorer do not support the Java mechanism for applet signing, the administration GUI cannot access your system's local resources. (Browser security mechanisms prevent this type of access to local system resources.) See Section "Administration GUI Browser Requirements" for more information.
Jar Signatures and Jar hashes are described in the SunScreen Reference Manual.
To Add a Jar Signature
-
In the Common Objects area, select Jar Signature from the Type choice list.
-
Select New... from the Add New choice list.
The Jar Signature dialog window appears.
Figure 7-1 Jar Signature Dialog Window
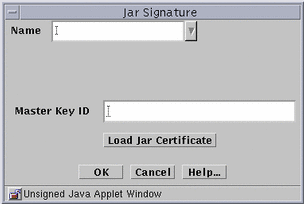
-
Type a name in the Name field.
-
Click the Load Jar Certificate button.
A dialog window appears. Navigate through the paths to find the certificate used to sign the Java archive.
-
Click on the Certificate file.
-
Click the OK button.
To Add a Jar Hash
You can set up the HTTP proxy to filter the Java applets based on the hash value of the Jar file. The Jar hash object is automatically saved when it is edited or a new Jar hash object is added. Any changes apply immediately and cannot be reversed.
-
Select Jar Hash from the Type choice list.
-
Select New... from the Add New button.
The Jar Hash dialog window appears.
Figure 7-2 Jar Hash Dialog Window
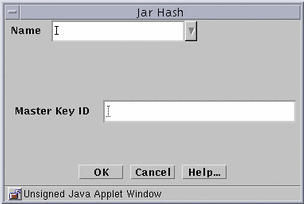
-
Type the name for this certificate in the Name field.
-
Type the MD5 hash of the Jar archive in the Master Key ID field.
-
Click the OK button.
Proxy Users and Authentication
The proxy users database depends on information in the authorized users database. You must define a user first in the Authorized User area in the Policy Rules page. Proxy users are used in FTP and Telnet proxy rules. You have to create entries for both authorized users and proxy users to take full advantage of the user authentication feature of the FTP and Telnet proxies.
The proxy user database contains the mapping information for users of SunScreen proxies. FTP and Telnet rules reference the proxy user entries. Additionally, a user connecting through either of these proxies will often be configured to require authentication by using an authorized user identity. Users logging in using a Telnet proxy are authenticated through the authorized user identity.
You can also use external authentication mechanisms (such as RADIUS or SecurID) to enable user authentication by using special proxy user entries, which create a translation.
By referencing these special mechanisms directly in rules or by adding references to other proxy user groups, you can allow users authenticated by those mechanisms to behave as authenticated users in the referenced contexts.
Names of proxy users must not contain the following characters: !, @, #, $, %, ^, &, *, {, }, [, ], <, >, ", `, \or , ?. It also must not contain a "NULL" character.
To Add an Authorized User
-
Select Authorized User from the Type choice list.
-
Select New... from the Add New button.
The User dialog window appears.
Figure 7-3 User Dialog Window
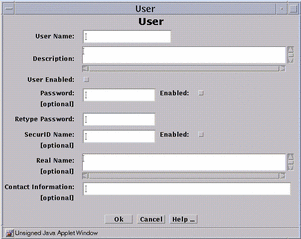
-
Type the user name in the User Name field.
-
(Optional) Type a description in the Description field.
-
Click the User Enabled button.
-
You need to defijne the authorization method by either assigning a password or choosing a SecureID name.
-
Check the Enabled check box.
-
(Optional) Type a name in the Real Name field.
-
(Optional) Type an email address in the Contact Information field.
-
Repeat the above steps until you have added all the authorized users.
-
Click the OK button. All changes apply immediately.
To Add a Single Proxy User
-
Select Proxy User from the Type choice list.
-
Select New Single... from the Add New button.
The Proxy User dialog window is displayed.
Figure 7-4 Proxy User Dialog Window
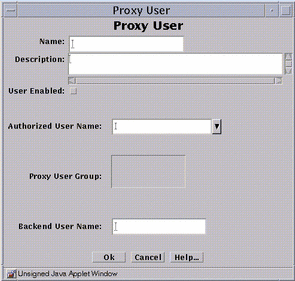
-
Type a name for this Proxy User in the Name field.
-
(Optional) Type a description in the Description field.
-
Check the User Enabled box.
If this box is not checked, the proxy user becomes inactive and can no longer use the proxies.
-
Click and highlight the name of the authorized user that you want to place in the Authorized User Name field.
-
(Optional) Click and highlight the name or names of the user group or groups with which you want to associate this proxy user.
-
Type the name that the proxy user should use when connecting to the target server (which is also known as the backend sever) in the Backend User Name field.
This name will be the identity the proxy user assumes on any target server connected through this proxy user.
-
Click the OK button.
-
Repeat the above steps until you have added all the proxy users.
All changes apply immediately.
To Add a Proxy User Group
You can group proxy users into logical groups for convenience; then you can use a group instead of single names in a policy rule.
-
Select Proxy User from the Type choice list.
-
Select New Group... from the Add New choice list.
The Proxy User dialog window appears.
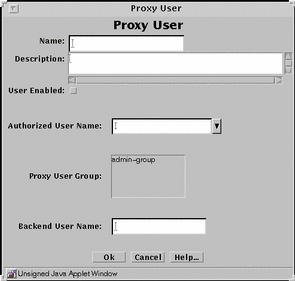
Figure 7-5 Proxy User Dialog Window
-
Type the name for this group of proxy users in the Name field.
-
(Optional) Type a short description of this definition in the Description field.
-
Click the User Enabled box to enable the user group.
-
Click and highlight the name of the proxy user or group of proxy users in the list of Proxy Users that you want to include in this group of Member Users.
-
Click the Add button to move it to the Member Users list.
Similarly, you can remove proxy users and lists of groups of proxy users from the Member Users list by clicking and highlighting the name and clicking the Remove button.
-
Do this for all the proxy users and groups of proxy users that you wish to include in your definition.
-
Click the OK button.
-
Repeat the above steps until you have defined all the groups of users required.
To Add Spam Domains
You can define the domains from which you think that you receive spam mail.
-
Select Screen from the Type choice list.
-
Select New... from the Add New choice list.
The Screen dialog window appears.
-
Type a name in the Name field.
-
(Optional) Type a brief description in the Description field.
-
Click the Mail Proxy tab.
The Spam Domain list appears.
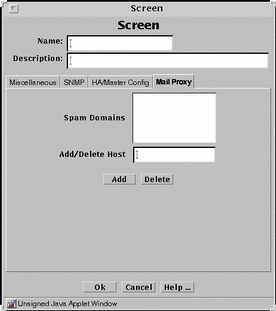
Figure 7-6 Screen Dialog Window, Mail Proxy Tab
-
Click on the name you want to add to the Spam Domain list.
-
Click the Add button.
-
Click the OK button.
-
Repeat these steps until you have added all the domains from which you receive Spam mail.
To Delete Spam Domains
-
Select the rule in the Policy Rules area.
-
Click the Search button.
-
Select the Spam domain from the Results field.
-
Click the Edit... button.
The Screen dialog window appears.
-
Click the Mail Proxy tab.
-
Select and highlight the Spam domain to be deleted in the Spam Domains field.
-
Click the Delete button.
-
Click the OK button.
All changes apply immediately.
Writing and Editing Policy Rules for Proxies
Policy Rules are strictly ordered; that is, they take effect in the order in which they are listed. You can define them in the order in which you want them to take effect or you can reorder your policy rules after you have defined them.
To Write Policy Rules for the Proxies
-
From the Policies List page, highlight the policy you want use and click the Edit button to move to the Policy Rules page.
-
Select the Packet Filtering tab in the Policy Rules area.
Proxies are defined in the Packet Filtering page.
-
Click the Add New... button in the Packet Filtering area to display the Rule Definition dialog window for that policy.
-
In the Rule Definition dialog window, the Rule Index field is filled with the next available rule index.
-
If a rule is valid only for a particular Screen, select that Screen only in the Common Objects area; otherwise the rule is valid for all Screens.
-
Select a Service from the Type choice list:
-
ftp
-
www
-
smtp
-
telnet
-
-
Choose source and destination address that you want for the Source and Destination Address fields.
Be sure you have defined these addresses on the Policy Rules page.
-
If it is a proxy rule, select ALLOW or DENY in the Action field.
There are four entries in the Action field: ALLOW, DENY, ENCRYPT, SECURE; proxy rules can only be defined with allow or deny.
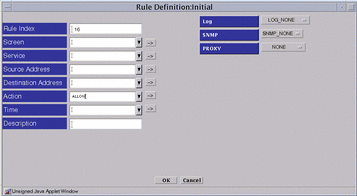
When ALLOW is chosen, three fields appear on the right side of the Rule Definition dialog window:
-
LOG
-
SNMP
-
PROXY
Figure 7-7 Rule Definition Dialog Window, Action ALLOW
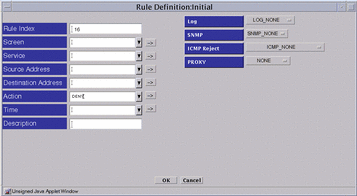
When DENY is chosen, four fields appear on the right side of the Rule Definition dialog window:
-
LOG
-
SNMP
-
ICMP Reject
-
PROXY
Figure 7-8 Rule Definition Dialog Window, Action DENY
-
-
Select the information into the LOG and SNMP fields.
There are five items in the Proxy choice list:
-
NONE
-
PROXY_HTTP
-
PROXY_FTP
-
PROXY_SMTP
-
PROXY_Telnet
Select the proxy you want to use.
-
-
Click and highlight the name of the proxy service for which you are writing this policy rule for the Service field.
If you plan to use proxies, you must select the appropriate proxy service:
Choose This Service
For This Proxy
ftp
PROXY_FTP
www
PROXY_HTTP
smtp
PROXY_SMTP
telnet
PROXY_TELNET
Optionally, if you know the name of the service that you want, you can type the first few letters of its name and that service appears in the field. You must type the first few letters exactly as the appear in the name because this feature is case sensitive.
-
Click the name of the proxy for which you are writing this policy rule to put it in the Proxy field:
PROXY_FTP
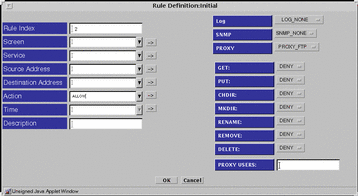
If you choose PROXY_FTP for the Proxy field, eight fields appears below the Proxy field on the right side of the Rule Definition dialog window:
-
GET
-
PUT
-
CHDIR
-
MKDIR
-
RENAME
-
REMOVE
-
DELETE
Figure 7-9 Rule Definition Dialog Window, PROXY_FTP
-
Choose an action for GET, PUT, CHDIR, MKDIR, RENAME, REMOVE, and DELETE or accept the default in the Proxy Details area.
-
Type a proxy user for the Proxy User in Proxy Details.
Be sure you have already defined the proxy user.
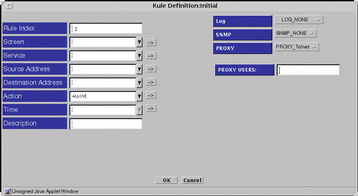
PROXY_Telnet
If you choose PROXY_Telnet for the Proxy field, the Proxy Users field appears below the Proxy field on the right side of the Rule Definition dialog window.
Figure 7-10 Rule Definition Dialog Window, PROXY_TELNET
PROXY_SMTP
If you choose the PROXY_SMTP for the Proxy field, the Relay field appears below the Proxy field on the right side of the Rule Definition dialog window.
Figure 7-11 Rule Definition Dialog Window, PROXY_SMTP
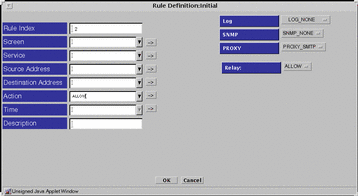
Choose whether you want to allow relaying of mail messages through the proxy in the Proxy Details area.
-
If you want to allow relaying, select the RELAY: ALLOW setting
-
If you do not want to allow the relaying, define the local domain name for the Screen or create a list of valid relay (domain) targets.
Define the Local Domain Name
Create or edit the etc/defaultdomain file, to contain the domain suffix for the Screen
Note -
You must shut down and reboot the Screen for this default domain to become active.
Create a List of Valid Relay Targets
Use the mail_relay feature of the ssadm command to create a list of valid relay (domain) targets (see the SunScreen Reference Manual manual).
PROXY_HTTP
If you chose PROXY_HTTP as the proxy, click that name to put it into the Proxy field.
Figure 7-12 Rule Definition Dialog Window, PROXY_HTTP
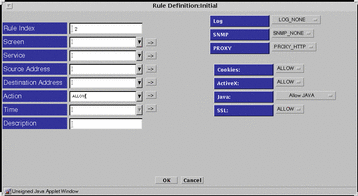
Four fields then appear below the Proxy field, on the right side of the Rule Definition dialog window. The first three fields are:
-
Cookies
-
ActiveX
-
SSL
Choose an action for Cookies, ActiveX, and SSL, or accept the default under Proxy Details.
The last field is Java. Click the button by the Java field, and choose the type of Java you will permit under Proxy Details:
-
Allow all Java
-
Block all Java
-
All Java with signed Jars, with the signature in the Jar Signature database
-
Allow both signed Jar signature and Jar Hash.
Note -If you selected Jar Signature or Jar Hash, they must be defined in the Common Objects area of the Policy Rules page.
FTP Proxy
To use the proxy and successfully make FTP connections through the Screen, you must FTP to the proxy on the Screen rather than directly to the end system. The Screen's policy rules will only allow FTP connections to and from the proxy.
For information on setting up the ftp proxy, see "PROXY_FTP".
To Use the FTP Proxy
The following example steps show what happens when a user wants to connect to the system named ftp.sun.com, which has an anonymous FTP account. To get there, they must first ftp to the SunScreen proxy named Screen.
Note -
The anonymous proxy user is prefigured during the installation of the software. It is an unauthenticated proxy user; as such, any string provided before the first @ ("at" sign) in the password is ignored. The password after the first@ (here: zzz@thereisnohelp.com) is the back-end user password--in this case, the user name as is customary usage for anonymous FTP.
-
Type the command:
% ftp screen
The following text appears:
Connected to screen 220-Proxy: SunScreen FTP Proxy Version 3.1 : Username to be given as <proxy-user´@´<FTP-server-host> : Password to be given as <proxy-password´@´<FTP-server-password> 220 Ready Name (screen:zzz):anonymous@ftp.sun.com
The format for the username is the username and the destination server separated by an "at" sign.
-
Type your password at the prompt to authenticate you to this proxy:
331- Proxy: Authenticate & connect: 331 Password needed to authenticate 'anonymous'. password:
The password is not echoed. Its format is two passwords separated by an "at" sign: The first password is the password for the proxy and the second is the password for the destination ftp server, for example, anonymous@zzz@thereisnohelp.com. anonymous is the password for the proxy and zzz@thereisnohelp is the email address that ftp.sun.com requires for anonymous ftp.
The following text appears:
230- Proxy: : Authentication mapped ´anonymous´ to backend user ´anonymous´. : Connecting to ftp.sun.com (192.9.9.73) - done Server: : 220 ftp.sun.com FTP server (Version 2.0.9) ready : 220-Welcome to Sun Microsystems Corporate FTP Server. : 220- : 220 ftp FTP server (ftpd Wed Oct 30 23:31:06 PST 1996) ready. Proxy: Login on server as ´anonymous´. Server:331 Guest login ok, send your e-mail address as password. Proxy supplying password to server 230 Guest login ok, access restrictions apply. ftp>... ftp>... ftp>... ftp> bye 221- Proxy: Quitting service. 221 Server: Goodbye. %
TELNET Proxy
The SunScreen telnet proxy logon process takes place in two stages:
-
First, you must telnet and log on to the Screen and be authenticated by the proxy
-
Then, you can log on on to the target system and be authenticated in the usual manner.
For information on setting up the telnet proxt, see "PROXY_Telnet".
To Use the Telnet Proxy
The following these steps illustrate what a user logging into a system through the telnet proxy would experience. In this example, the proxy is running on a Screen named Screen and the user wants to connect to the system namned foo.com:
-
Type the following:
% telnet Screen
The following text appears:
SunScreen Telnet Proxy Version: 3.1
-
Type the username at the prompt:
Username@Hostname: username@foo.com
-
Type your password to authenticate you to this proxy:
password:
The password is not echoed. If you are successful, you will see the normal telnet connection information for the system foo.com, for example:
% Trying 172.16.6.74... Connected to foo.com Escape character is `^]'. UNIX(r) System V Release 4.0 (foo.com) login:
-
Log in to the system as you normally would and, if required, type a password.
SMTP Proxy
The SMTP proxy provides a relay for email. It determines access based on source and destination addresses. The only content filtering that the proxy performs is based on the source and destination values for the mail itself. The source (the sender's address) is compared to the list of spam domains; if the address matches any specifiec spam domain, the packet gets dropped. The destination (the recipients's address) is compared with the local domain to see if relaying is being attempted. If relaying is allowed, the packet gets passed through, if not, the packet gets dropped.
Be sure you have defined any necessary spam and relay restrictors that you want. See "To Add Spam Domains" and "PROXY_SMTP".
To Use the SMTP Proxy
Point the MX record for the domain to the proxy for mail to be processed properly.
SMTP connection will then be made to the proxy, rather than to the actual SMTP server.
HTTP Proxy
The HTTP proxy provides a relay capability for the World Wide Web supporting the HTTP protocol. As with all proxies, it allows or denies sessions base on the source or destination address. It also provides selective filtering, such as Java filtering, Active-X, and cookies, of content based on the source and destination of sessions.
The HTTP proxy also filters Java, based on the signatures encapsulated in Java Archives (Jars) or on a precomputed hash of valid dialog windows.
For information on configuring the HTP proxy, see "PROXY_HTTP"
To Configure the Browser to Use the HTTP Proxy
Basically, you point your browser at the the Screen instead of another HTTP server. This example procedure is for configuring the HotJava browser. Consult the documentation for your browser to determine how to set the HTTP proxy sever address and port number.
The server address should be the Screen's address and the port number must be 80.
-
Click the down arrow on Preferences to display the choice list.
-
Click and highlight Proxies to display the Proxies page.
-
Type the name of the Screen or its IP address in the HTTP field.
-
Type the number 80 as the number of the Port in the Port field for HTTP.
The HTTP proxy is fixed at port 80 in the current version of SunScreen.
-
Click the Apply button at the bottom of the Proxies page to set these choices as defaults.
Figure 7-13 PROXY_HTTP

-
Chose an action for Cookies, ActiveX, and SSL or accept the default under Proxy Details.
-
Click the button by the Java field, and choose the type of Java you will permit under Proxy Details:
-
Allow all Java
-
Block all Java
-
All Java with signed Jars, with the signature in the Jar Signature database
-
Allow both c and d.
If you selected a through e, enter the Jar signature and Jar hash for these objects
Note -If you selected Jar Signature or Jar Hash, they must be defined in the Common Objects area of the Policy Rules page.
-
-
-
Click the OK button in the dialog window.
-
Click the Save Changes button.
Proxy Logging
You control proxy logging by selecting Logging as part of a rule's action and by configuring the log limiter variables.
When logging is specified in a proxy rule, all (non-debug) events relating to a session enabled by that rule are logged for the proxy.
Also, events based on the limiters for a given proxy are logged, regardless of rule action.
See the SunScreen Reference Manual manual for the specifications of log limiter variables.
- © 2010, Oracle Corporation and/or its affiliates
