Addresses
SunScreen 3.1 Lite uses IP addresses to define the network elements that make up the configuration. These addresses are then used in defining the Screen's network interfaces and as the source and destination addresses for rules and NAT.
The address can be for a single computer, or it can be for a whole network or subnetwork. Additionally, addresses (individual and network) can be grouped together to form an address group. SunScreen 3.1 Lite allows you to define address groups that specifically include or exclude other defined addresses (single IP hosts, ranges, or groups).
Table 2-2 Address Explanations
The following figure shows an example of various types of addresses and can be used as a reference when completing your own network map.
Figure 2-1 Example of a Network Map
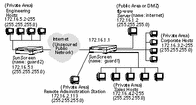
In this figure, the following examples of different types of addresses can be seen:
-
The ftp-www server is an example of a single host address (172.16.1.2).
-
Corporate, sales, and the engineering hosts are examples of ranges of addresses. For example, the range of addresses in the engineering hosts, 172.16.5.2 with the netmask 255.255.255.0, is defined as a range of addresses from 171.16.5.2 to 172.16.5.255.
The Internet is an example of a group of addresses, in this case defined as all. The ftp-www server is an example of a single address. The corporate, sales, and engineering hosts are examples of ranges of addresses.
The following worksheets can help you organize the IP addresses. Expand them as necessary. Group the IP addresses and names for the following network elements:
Rules are used to control access to your computer network and to control encryption for access to your data. In preparing to implement rules, you have:
-
Determined the overall services that are available on your network.
-
Determined the services available to a particular user or host and user groups over particular IP addresses.
-
Determined the correct action for the service and addresses for that user or host.
Note -By default, the Screen drops any packets that do not specifically match a rule. This makes it easier to create rules, since you only have to write a rule for the services you want to pass.
|
Name |
IP Address |
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Table 2-4 Address Ranges
|
Name |
Address |
|
|---|---|---|
|
|
Beginning |
Ending |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Table 2-5 Address Group
|
Name |
Address |
|
|---|---|---|
|
|
Include |
Exclude |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
- © 2010, Oracle Corporation and/or its affiliates
