Sun Management Center Concepts
The following concepts are fundamental to understanding Sun Management Center software:
-
Administrative domains
-
Management information base (MIB)
-
Modules
-
Alarms and rules
Note –
In this document, “domain” refers to a Sun Management Center administrative domain. This term should not be confused with uses of the term “domain” related to other Sun products or documentation. See Chapter 2, Using Sun Management Center Administrative Domains for more information.
Administrative Domains
An administrative domain is a hierarchical collection of resources that you want to monitor and manage. The resources can include a complete campus, individual buildings, hosts, networks, subnets, links, and so on. Each administrative domain consists of these resources, which can be combined with other resources to form groups within a administrative domain. Each of these groups can contain additional groups of resources, providing a multilevel, hierarchical administrative domain.
You can create one or more administrative domains that are based on your business needs. For example, you might create a lab administrative domain that contains all the lab machines. Similarly, you might create an accounting administrative domain that contains all the machines that are used for accounting.
The Sun Management Center software displays the administrative domain and its members in a visual representation. Figure 1–4 shows an example.
In the following example, the host, Payroll2, belongs to the Building B group, which belongs to the Payroll Servers 1 administrative domain.
Figure 1–4 Java Console Window Showing an Administrative Domain and Its Members
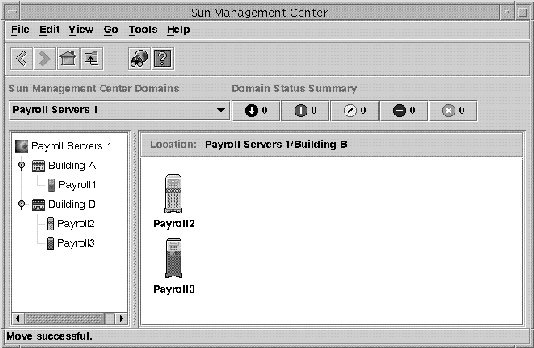
Linux hosts are identified by a generic Linux icon. Zone agents are identified by a generic icon having a “Z” symbol in the middle.
Management Information Base (MIB)
A management information base (MIB) is a hierarchical database schema that describes the data that are available from an agent. Sun Management Center agents use the MIB to store monitored data that can be accessed remotely.
Sun Management Center Modules
Unlike most agents, the Sun Management Center agents do not implement the MIB in a monolithic code that contains a wide variety of functions in a single program. Instead, Sun Management Center software uses several components, that are called modules, for each agent. Each module implements its own MIB. Therefore, the Sun Management Center agent MIB is the cumulative total of all the modules and their individual MIBs, as illustrated in the following figure.
Figure 1–5 Sun Management Center Agent MIB
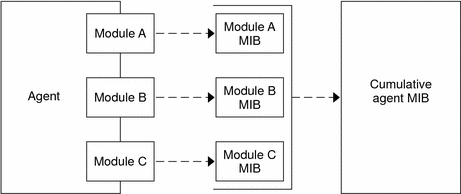
Sun Management Center modules monitor and manage the resources of systems, applications, and network devices. The modules enable you to isolate and monitor specific system components. For example, separate modules are available for monitoring the kernel, for monitoring printers, and for monitoring processes. The modules are primarily used to monitor and to notify you through alarms when error conditions occur or when performance tuning is required. For more information about alarms, see Alarms and Rules.
Each module consists of one or more properties that you can monitor. For example, one of the default modules that is loaded during installation is the Kernel Reader. This module monitors the kernel properties. These properties include user statistics, disk statistics, file system usage, and so on.
Note –
You can add or remove modules dynamically. This feature enables you to customize the modules that are loaded on each agent (object), based on your need.
Alarms and Rules
An alarm is a notification of an abnormal event. Sun Management Center software enables you to monitor your system using alarms that have differing severities. The thresholds that generate these alarms are defined in the modules. The software enables you to set the thresholds that trigger simple alarms.
For example, one of the properties of the Kernel Reader module is the number of user sessions. The software enables you to set a threshold number of user sessions that, when exceeded, generates an alarm. For example, you might tell Sun Management Center software to generate a critical alarm when there are seven or more user sessions. Similarly, you might tell the software to generate a cautionary alarm when there are five or six user sessions.
The software is configured with default alarm conditions. You can set and define your own alarm thresholds for simple alarms, such as those alarms that are based on the simple rCompare (comparison) rule.
Complex rules also generate alarms. For example, one complex rule generates an alert alarm when a disk is more than 75 percent busy, the average queue length is over 10 entries, and the wait queue is increasing. This rule combines three conditions:
-
Percentage of the disk that is busy
-
Average queue length
-
Wait queue
Unlike simple rules, these complex rules are predefined. You cannot modify complex rules. Consequently, you cannot set thresholds for complex alarms.
When an alarm is generated, the software notifies you through the main console window, and through an alarm action. The alarm action can include a message sent to a specified email address or activation of a script. You can also write a customized program that notifies you in other ways that an alarm condition has occurred.
For more information about alarms, see Chapter 12, Managing Alarms. For more information about rules, see Appendix D, Sun Management Center Software Rules.
- © 2010, Oracle Corporation and/or its affiliates
