Chapter 24 Solaris IP Filter (Overview)
This chapter provides an overview of Solaris IP Filter. For Solaris IP Filter tasks, see Chapter 25, Solaris IP Filter (Tasks).
This chapter contains the following information:
What's New in Solaris IP Filter
This section describes new Solaris IP Filter features in the Solaris release.
For a complete listing of new Solaris features and a description of Solaris releases, see Solaris Express Developer Edition What’s New
Packet Filter Hooks
Solaris Express, Developer Edition 1/08 Release: Packet filter hooks are now used for packet filtering in the Solaris Operating System. This feature offers the following advantages in system administration:
-
Packet filter hooks simplify the configuration of the Solaris IP filter.
-
Support for filtering packets across zones is now available.
-
Using filter hooks improves the performance of Solaris IP Filter.
For further details about these hooks, see Packet Filter Hooks. For tasks that are associated with packet filter hooks, see Chapter 25, Solaris IP Filter (Tasks).
IPv6 Packet Filtering for Solaris IP Filter
Solaris 10 6/06: For system administrators who have all or part of their network infrastructure configured with IPv6, Solaris IP Filter has been enhanced to include IPv6 packet filtering. IPv6 packet filtering can filter based on the source/destination IPv6 address, pools containing IPv6 addresses, and IPv6 extension headers.
The -6 option has been added to both the ipf command and the ipfstat command to use with IPv6. Although there is no change to the command line interface for the ipmon and ippool commands, these commands also support IPv6. The ipmon command has been enhanced to accommodate the logging of IPv6 packets, and the ippool command supports the inclusion of IPv6 addresses in pools.
For more information see IPv6 for Solaris IP Filter. For tasks associated with IPv6 packet filtering, see Chapter 25, Solaris IP Filter (Tasks).
Introduction to Solaris IP Filter
Solaris IP Filter replaces the SunScreenTM firewall as the firewall software for the Solaris Operating System (Solaris OS). Like the SunScreen firewall, Solaris IP Filter provides stateful packet filtering and network address translation (NAT). Solaris IP Filter also includes stateless packet filtering and the ability to create and manage address pools.
Packet filtering provides basic protection against network-based attacks. Solaris IP Filter can filter by IP address, port, protocol, network interface, and traffic direction. Solaris IP Filter can also filter by an individual source IP address, a destination IP address, by a range of IP addresses, or by address pools.
Solaris IP Filter is derived from open source IP Filter software. To view license terms, attribution, and copyright statements for open source IP Filter, the default path is /usr/lib/ipf/IPFILTER.LICENCE. If the Solaris OS has been installed anywhere other than the default, modify the given path to access the file at the installed location.
Information Sources for Open Source IP Filter
The home page for the open source IP Filter software by Darren Reed is found at http://coombs.anu.edu.au/~avalon/ip-filter.html. This site includes information for open source IP Filter, including a link to a tutorial entitled “IP Filter Based Firewalls HOWTO” (Brendan Conoboy and Erik Fichtner, 2002). This tutorial provides step-by-step instructions for building firewalls in a BSD UNIX environment. Although written for a BSD UNIX environment, the tutorial is also relevant for the configuration of Solaris IP Filter.
Solaris IP Filter Packet Processing
Solaris IP Filter executes a sequence of steps as a packet is processed. The following diagram illustrates the steps of packet processing and how filtering integrates with the TCP/IP protocol stack.
Figure 24–1 Packet Processing Sequence
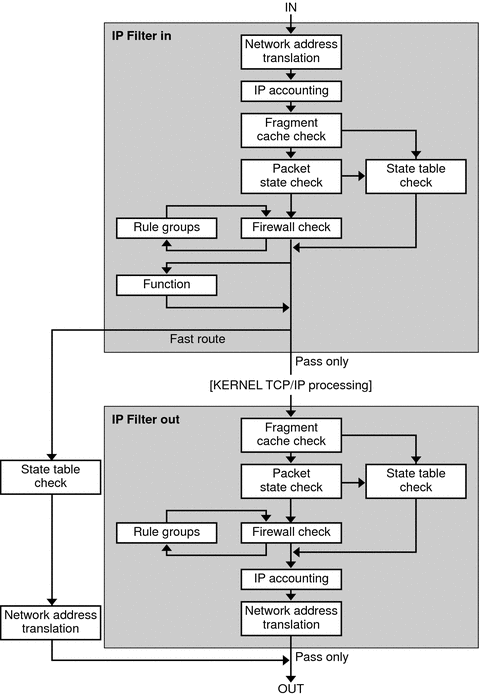
The packet processing sequence includes the following:
-
Network Address Translation (NAT)
The translation of a private IP address to a different public address, or the aliasing of multiple private addresses to a single public one. NAT allows an organization to resolve the problem of IP address depletion when the organization has existing networks and needs to access the Internet.
-
IP Accounting
Input and output rules can be separately set up, recording the number of bytes that pass through. Each time a rule match occurs, the byte count of the packet is added to the rule and allows for collection of cascading statistics.
-
Fragment Cache Check
If the next packet in the current traffic is a fragment and the previous packet was allowed, the packet fragment is also allowed, bypassing state table and rule checking.
-
Packet State Check
If keep state is included in a rule, all packets in a specified session are passed or blocked automatically, depending on whether the rule says pass or block.
-
Firewall Check
Input and output rules can be separately set up, determining whether or not a packet will be allowed through Solaris IP Filter, into the kernel's TCP/IP routines, or out onto the network.
-
Groups
Groups allow you to write your rule set in a tree fashion.
-
Function
A function is the action to be taken. Possible functions include block, pass, literal, and send ICMP response.
-
Fast-route
Fast-route signals Solaris IP Filter to not pass the packet into the UNIX IP stack for routing, which results in a TTL decrement.
-
IP Authentication
Packets that are authenticated are only passed through the firewall loops once to prevent double-processing.
Guidelines for Using Solaris IP Filter
-
Solaris IP Filter is managed by the SMF services svc:/network/pfil and svc:/network/ipfilter. For a complete overview of SMF, see Chapter 16, Managing Services (Overview), in System Administration Guide: Basic Administration. For information on the step-by-step procedures that are associated with SMF, see Chapter 17, Managing Services (Tasks), in System Administration Guide: Basic Administration.
-
Solaris IP Filter requires direct editing of configuration files.
-
Solaris IP Filter is installed as part of the Solaris OS. By default, Solaris IP Filter is not activated after a fresh install. To configure filtering, you must edit configuration files and manually activate Solaris IP Filter. You can activate filtering by either rebooting the system or by plumbing the interfaces using the ifconfig command. For more information, see the ifconfig(1M) man page. For the tasks associated with enabling Solaris IP Filter, see Configuring Solaris IP Filter.
-
To administer Solaris IP Filter, you must be able to assume a role that includes the IP Filter Management rights profile, or become superuser. You can assign the IP Filter Management rights profile to a role that you create. To create the role and assign the role to a user, see Configuring RBAC (Task Map) in System Administration Guide: Security Services.
-
IP Network Multipathing (IPMP) supports stateless filtering only.
-
Sun Cluster configurations do not support filtering with Solaris IP Filter.
-
Filtering between zones is not currently supported with Solaris IP Filter.
Using Solaris IP Filter Configuration Files
Solaris IP Filter can be used to provide firewall services or network address translation (NAT). Solaris IP Filter can be implemented using loadable configuration files. Solaris IP Filter includes a directory called /etc/ipf. You can create and store configuration files called ipf.conf, ipnat.conf and ippool.conf in the /etc/ipf directory. These files are loaded automatically during the boot process when they reside in the /etc/ipf directory. You can also store the configuration files in another location and load the files manually. For example configuration files, see Creating and Editing Solaris IP Filter Configuration Files.
Working With Solaris IP Filter Rule Sets
To manage your firewall, you use Solaris IP Filter to specify rule sets that you use to filter your network traffic. You can create the following types of rule sets:
-
Packet filtering rule sets
-
Network Address Translation (NAT) rule sets
Additionally, you can create address pools to reference groups of IP addresses. You can then use these pools later in a rule set. The address pools help to speed up rule processing. Address pools also make managing large groups of addresses easier.
Using Solaris IP Filter's Packet Filtering Feature
You set up packet filtering by using packet filtering rule sets. Use the ipf command to work with packet filtering rule sets. For more information on the ipf command, see the ipf(1M) command.
You can create packet filtering rules either at the command line, using the ipf command, or in a packet filtering configuration file. If you want the packet filtering rules to be loaded at boot time, create a configuration file called /etc/ipf/ipf.conf in which to put packet filtering rules. If you do not want the packet filtering rules loaded at boot time, put the ipf.conf file in a location of your choice, and manually activate packet filtering by using the ipf command.
You can maintain two sets of packet filtering rule sets with Solaris IP Filter, the active rule set and the inactive rule set. In most cases, you work with the active rule set. However, the ipf -I command enables you to apply the command action to the inactive rule list. The inactive rule list is not used by Solaris IP Filter unless you select it. The inactive rule list provides you with a place to store rules without affecting active packet filtering.
Solaris IP Filter processes the rules in the rules list from the beginning of the configured rules list to the end of the rules list before passing or blocking a packet. Solaris IP Filter maintains a flag that determines whether it will or will not pass a packet. It goes through the entire rule set and determines whether to pass or block the packet based on the last matching rule.
There are two exceptions to this process. The first exception is if the packet matches a rule containing the quick keyword. If a rule includes the quick keyword, the action for that rule is taken, and no subsequent rules are checked. The second exception is if the packet matches a rule containing the group keyword. If a packet matches a group, only rules tagged with the group are checked.
Configuring Packet Filtering Rules
Use the following syntax to create packet filtering rules:
action [in|out] option keyword, keyword...
-
Each rule begins with an action. Solaris IP Filter applies the action to the packet if the packet matches the rule. The following list includes the commonly used actions applied to a packet.
- block
-
Prevents the packet from passing through the filter.
- pass
-
Allows the packet through the filter.
- log
-
Logs the packet but does not determine if the packet is blocked or passed. Use the ipmon command to view the log.
- count
-
Includes the packet in the filter statistics. Use the ipfstat command to view the statistics.
- skip number
-
Makes the filter skip over number filtering rules.
- auth
-
Requests that packet authentication be performed by a user program that validates packet information. The program determines whether the packet is passed or blocked.
- preauth
-
Requests that the filter look at a pre-authenticated list to determine what to do with the packet.
-
Following the action, the next word must be either in or out. Your choice determines whether the packet filtering rule is applied to an incoming packet or to an outgoing packet.
-
Next, you can choose from a list of options. If you use more than one option, they must be in the order shown here.
- log
-
Logs the packet if the rule is the last matching rule. Use the ipmon command to view the log.
- quick
-
Executes the rule containing the quick option if there is a packet match. All further rule checking stops.
- on interface-name
-
Applies the rule only if the packet is moving in or out of the specified interface.
- dup-to interface-name
-
Copies the packet and sends the duplicate out on interface-name to an optionally specified IP address.
- to interface-name
-
Moves the packet to an outbound queue on interface-name.
-
After specifying the options, you can choose from a variety of keywords that determine whether the packet matches the rule. The following keywords must be used in the order shown here.
Note –By default, any packet that does not match any rule in the configuration file is passed through the filter.
- tos
-
Filters the packet based on the type-of-service value expressed as either a hexadecimal or a decimal integer.
- ttl
-
Matches the packet based on its time-to-live value. The time-to-live value stored in a packet indicates the length of time a packet can be on the network before being discarded.
- proto
-
Matches a specific protocol. You can use any of the protocol names specified in the /etc/protocols file, or use a decimal number to represent the protocol. The keyword tcp/udp can be used to match either a TCP or a UDP packet.
- from/to/all/any
-
Matches any or all of the following: the source IP address, the destination IP address, and the port number. The all keyword is used to accept packets from all sources and to all destinations.
- with
-
Matches specified attributes associated with the packet. Insert either the word not or the word no in front of the keyword in order to match the packet only if the option is not present.
- flags
-
Used for TCP to filter based on TCP flags that are set. For more information on the TCP flags, see the ipf(4) man page.
- icmp-type
-
Filters according to ICMP type. This keyword is used only when the proto option is set to icmp and is not used if the flags option is used.
- keep keep-options
-
Determines the information that is kept for a packet. The keep-options available include the state option and the frags option. The state option keeps information about the session and can be kept on TCP, UDP, and ICMP packets. The frags option keeps information on packet fragments and applies the information to later fragments. The keep-options allow matching packets to pass without going through the access control list.
- head number
-
Creates a new group for filtering rules, which is denoted by the number number.
- group number
-
Adds the rule to group number number instead of the default group. All filtering rules are placed in group 0 if no other group is specified.
The following example illustrates how to put together the packet filtering rule syntax to create a rule. To block incoming traffic from the IP address 192.168.0.0/16, you would include the following rule in the rule list:
block in quick from 192.168.0.0/16 to any |
For the complete grammar and syntax used to write packet filtering rules, see the ipf(4) man page. For tasks associated with packet filtering, see Managing Packet Filtering Rule Sets for Solaris IP Filter. For an explanation of the IP address scheme (192.168.0.0/16) shown in the example, see Chapter 2, Planning an IPv4 Addressing Scheme (Tasks).
Using Solaris IP Filter's NAT Feature
NAT sets up mapping rules that translate source and destination IP addresses into other Internet or intranet addresses. These rules modify the source and destination addresses of incoming or outgoing IP packets and send the packets on. You can also use NAT to redirect traffic from one port to another port. NAT maintains the integrity of the packet during any modification or redirection done on the packet.
Use the ipnat command to work with NAT rule lists. For more information on the ipnat command, see the ipnat(1M) command.
You can create NAT rules either at the command line, using the ipnat command, or in a NAT configuration file. NAT configuration rules reside in the ipnat.conf file. If you want the NAT rules to be loaded at boot time, create a file called /etc/ipf/ipnat.conf in which to put NAT rules. If you do not want the NAT rules loaded at boot time, put the ipnat.conf file in a location of your choice, and manually activate packet filtering with the ipnat command.
Configuring NAT Rules
Use the following syntax to create NAT rules:
command interface-name parameters
-
Each rule begins with one of the following commands:
- map
-
Maps one IP address or network to another IP address or network in an unregulated round-robin process.
- rdr
-
Redirects packets from one IP address and port pair to another IP address and port pair.
- bimap
-
Establishes a bidirectional NAT between an external IP address and an internal IP address.
- map-block
-
Establishes static IP address-based translation. This command is based on an algorithm that forces addresses to be translated into a destination range.
-
Following the command, the next word is the interface name, such as hme0.
-
Next, you can choose from a variety of parameters, which determine the NAT configuration. Some of the parameters include:
- ipmask
-
Designates the network mask.
- dstipmask
-
Designates the address that ipmask is translated to.
- mapport
-
Designates tcp, udp, or tcp/udp protocols, along with a range of port numbers.
The following example illustrates how to put together the NAT rule syntax together to create a NAT rule. To rewrite a packet that goes out on the de0 device with a source address of 192.168.1.0/24 and to externally show its source address as 10.1.0.0/16, you would include the following rule in the NAT rule set:
map de0 192.168.1.0/24 -> 10.1.0.0/16 |
For the complete grammar and syntax used to write NAT rules, see the ipnat(4) man page.
Using Solaris IP Filter's Address Pools Feature
Address pools establish a single reference that is used to name a group of address/netmask pairs. Address pools provide processes to reduce the time needed to match IP addresses with rules. Address pools also make managing large groups of addresses easier.
Address pool configuration rules reside in the ippool.conf file. If you want the address pool rules to be loaded at boot time, create a file called /etc/ipf/ippool.conf in which to put address pool rules. If you do not want the address pool rules loaded at boot time, put the ippool.conf file in a location of your choice, and manually activate packet filtering with the ippool command.
Configuring Address Pools
Use the following syntax to create an address pool:
table role = role-name type = storage-format number = reference-number |
- table
-
Defines the reference for the multiple addresses.
- role
-
Specifies the role of the pool in Solaris IP Filter. At this time, the only role you can reference is ipf.
- type
-
Specifies the storage format for the pool.
- number
-
Specifies the reference number that is used by the filtering rule.
For example, to reference the group of addresses 10.1.1.1 and 10.1.1.2, and the network 192.16.1.0 as pool number 13, you would include the following rule in the address pool configuration file:
table role = ipf type = tree number = 13
{ 10.1.1.1/32, 10.1.1.2/32, 192.168.1.0/24 };
Then, to reference pool number 13 in a filtering rule, you would construct the rule similar to the following example:
pass in from pool/13 to any |
Note that you must load the pool file before loading the rules file that contains a reference to the pool. If you do not, the pool is undefined, as shown in the following output:
# ipfstat -io empty list for ipfilter(out) block in from pool/13(!) to any |
Even if you add the pool later, the addition of the pool does not update the kernel rule set. You also need to reload the rules file that references the pool.
For the complete grammar and syntax used to write packet filtering rules, see the ippool(4) man page.
Packet Filter Hooks
Beginning with the Solaris Express, Developer Edition 1/08 release, packet filter hooks replace the pfil module to enable Solaris IP filter. In previous Solaris releases, configuration of the pfil module was required as an additional step to set up Solaris IP Filter. This extra configuration requirement increased the risk of errors that would cause Solaris IP Filter to work improperly. The insertion of the pfil STREAMS module between IP and the device driver also caused performance degradation. Lastly, the pfil module could not perform packet interception between zones.
The use of packet filter hooks streamlines the procedure to enable Solaris IP Filter. Through these hooks, Solaris IP Filter uses pre-routing (input) and post-routing (output) filter taps to control packet flow into and out of the Solaris system.
Packet filter hooks eliminate the need for the pfil module. Thus the following components that are associated with the module are also removed.
-
pfil driver
-
pfil daemon
-
svc:/network/pfil SMF service
For tasks associated with enabling Solaris IP Filter, see Chapter 25, Solaris IP Filter (Tasks).
IPv6 for Solaris IP Filter
Beginning with the Solaris 10 6/06 release, support for IPv6 is available with Solaris IP Filter. IPv6 packet filtering can filter based on the source/destination IPv6 address, pools containing IPv6 addresses, and IPv6 extension headers.
IPv6 is similar to IPv4 in many ways. However, header and packet size differ between the two versions of IP, which is an important consideration for IP Filter. IPv6 packets known as jumbograms contain a datagram longer than 65,535 bytes. Solaris IP Filter does not support IPv6 jumbograms. To learn more about other IPv6 features, see Major Features of IPv6.
Note –
For more information on jumbograms, refer to the document IPv6 Jumbograms, RFC 2675 from the Internet Engineering Task Force (IETF). [http://www.ietf.org/rfc/rfc2675.txt]
IP Filter tasks associated with IPv6 do not differ substantially from IPv4. The most notable difference is the use of the -6 option with certain commands. Both the ipf command and the ipfstat command include the -6 option for use with IPv6 packet filtering. Use the -6 option with the ipf command to load and flush IPv6 packet filtering rules. To display IPv6 statistics, use the -6 option with the ipfstat command. The ipmon and ippool commands also support IPv6, although there is no associated option for IPv6 support. The ipmon command has been enhanced to accommodate the logging of IPv6 packets. The ippool command supports the pools with IPv6 addresses. You can create pools of only IPv4 or IPv6 addresses, or a pool containing both IPv4 and IPv6 addresses within the same pool.
You can use the ipf6.conf file to create packet filtering rule sets for IPv6. By default, the ipf6.conf configuration file is included in the /etc/ipf directory. As with the other filtering configuration files, the ipf6.conf file loads automatically during the boot process when it is stored in the /etc/ipf directory. You can also create and store an IPv6 configuration file in another location and load the file manually.
Note –
Network Address Translation (NAT) does not support IPv6.
Once packet filtering rules for IPv6 have been set up, activate IPv6 packet filtering capabilities by plumbing the inet6 version of the interface.
For more information on IPv6, see Chapter 3, Planning an IPv6 Addressing Scheme (Overview). For tasks associated with Solaris IP Filter, see Chapter 25, Solaris IP Filter (Tasks).
Solaris IP Filter Man Pages
The following table includes the man page documentation relevant to Solaris IP Filter.
- © 2010, Oracle Corporation and/or its affiliates
