Chapter 6 Example: Planning an Organization's Labels
This chapter discusses the creation of a set of labels that meet a company's goals for information protection.
Identifying the Site's Label Requirements
SecCompany, Inc. is a fictional name for the company whose label requirements are modeled in this example. To protect the corporation's intellectual property, the company's legal department mandates that employees use three labels on all sensitive email and printed materials. The three labels, from most sensitive to least sensitive are the following:
-
SecCompany Confidential: Registered
-
SecCompany Confidential: Need To Know
-
SecCompany Confidential: Internal Use Only
The legal department also approves the use of an optional fourth label, Public. The Public label is for information that can be distributed to anyone without restrictions.
Satisfying Information Protection Goals
At SecCompany, Inc, the manager in charge of Information Protection makes use of all possible channels to communicate labeling requirements. However, some employees do not understand the requirements. Other employees forget about requirements or ignore the requirements. Even when labels are properly applied, the information is not always properly handled, stored, and distributed. For example, reports indicate that even Registered information is sometimes found unattended. Copies of Registered information have been left next to copy machines and printers, in break rooms, or in lobbies.
The legal department wants a better way to ensure that information is properly labeled without relying totally on employee compliance. The system administrators want a better way to control the following:
-
Who can see or modify sensitive information
-
Which information is printed on which printers
-
How printer output is handled
-
How email at various levels of security is distributed internally and externally
Trusted Extensions Features That Address Labeling and Access
Trusted Extensions software does not leave labeling up to the discretion of computer users. All printer output from print servers that are configured with Trusted Extensions is automatically labeled according to the site's requirements.
Even though security was not yet fully understood at the company, executives knew that Trusted Extensions could implement certain features immediately.
-
Automatic labeling of print jobs
-
Printers with restricted access by label
-
Email with restricted access by label
Figure 6–1 Automatic Labeling of Print Jobs
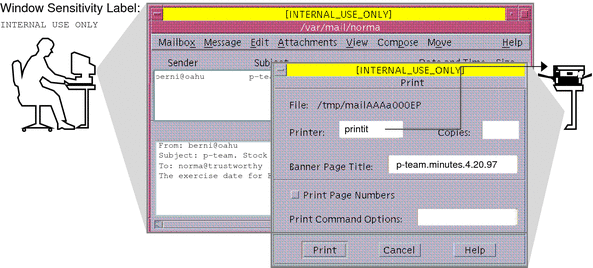
Each print job is automatically assigned a label. The label corresponds either to the level at which the user is working or to the user's level of responsibility.
Figure 6–1 shows an employee working at a level of INTERNAL_USE_ONLY. At this level, the work should only be accessible by SecCompany employees and others who have signed nondisclosure agreements. When the employee sends email to the printer, the print job is automatically assigned the label INTERNAL_USE_ONLY.
Figure 6–2 Label Automatically Printed on Body Pages

The printer automatically prints a company-specified label at the top and bottom of each page of printed output.
Figure 6–2 shows the letter that was sent to the printer in Figure 6–1 being printed with the user's working label. The label, INTERNAL_USE_ONLY, is printed at the top and bottom of every page.
Example 6–1 Handling Guidelines on Banner and Trailer Pages
This example shows the wording for a print job whose sensitivity level has a classification of NEED_TO_KNOW and a department of HUMAN_RESOURCES. Banner and trailer pages are automatically created for each print job and are printed with company-specific handling guidelines.
NEED_TO_KNOW HR DISTRIBUTE ONLY TO HUMAN RESOURCES (NON-DISCLOSURE AGREEMENT REQUIRED) |
Printed below the sensitivity label, handling instructions provides distribution instructions for the printed material. The instructions state that the information should be distributed only to human resources personnel who need to know the information. Also, a reader must have signed a nondisclosure agreement.
Printers can be configured to print only jobs with labels within a restricted label range. For example, Figure 6–3 illustrates that the legal department's printer has been set up to print only jobs that have been assigned one of three labels:
-
NEED_TO_KNOW LEGAL – Can be viewed only by employees with a need to know within the legal department
-
INTERNAL_USE_ONLY – Can be viewed only by permanent employees of the SecCompany company and customers who have signed nondisclosure agreements
-
PUBLIC – Can be viewed by anyone
This printer setup excludes jobs that are sent at any other label. For example, this printer would reject jobs at the labels NEED_TO_KNOW MARKETING and REGISTERED.
Figure 6–3 How a Printer With a Restricted Label Range Handles Jobs
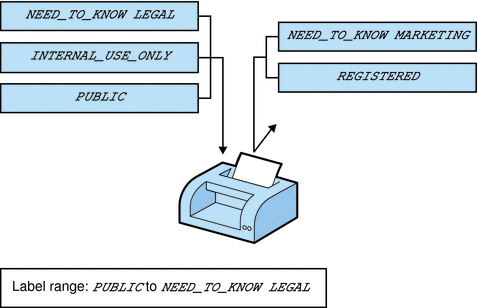
Printers in locations that are accessible to all employees can be similarly restricted. For example, printers can be configured to print jobs only at the two labels that all employees can view, INTERNAL_USE_ONLY and PUBLIC.
Similar to how the printer label range controls which jobs can be printed on a particular printer, a user's account sensitivity label range limits which email the person can handle. Figure 6–4 shows email that is being labeled at the sensitivity label of the user's mail application. The email is sent to the mail application at that label.
Figure 6–4 A User Receiving Email Within the Account Label Range
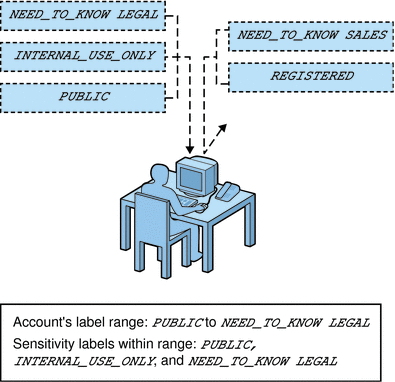
Gateways to the Internet were set up to screen email so that emails at inappropriate labels could not be sent outside of the company. Inappropriate labels are any labels except PUBLIC.
Climbing the Security Learning Curve
The management identifies an experienced administrator with the following qualifications:
-
Is assessed to be trustworthy
-
Knows how to administer Solaris systems
-
Understands the organization's information-processing goals well enough to be responsible for overseeing or implementing the site's security
That person is assigned the job of security administrator.
Long before installing Trusted Extensions software, the security administrator starts to learn about security and to prepare a plan for the site's security policy. First, the security administrator reads the following documents:
-
Chapter 1, Security Planning for Trusted Extensions, in Solaris Trusted Extensions Administrator’s Procedures – For guidance on creating a site's security policy
-
Solaris Trusted Extensions User’s Guide – To become familiar with label types and appearance
-
Solaris Trusted Extensions Administrator’s Procedures – To become familiar with security administrator responsibilities and tools
-
Chapter 1, Labels in Trusted Extensions Software – To review label concepts
Then, the security administrator starts with a plan for the site's labels. The planning process is described in the following sections.
Analyzing the Requirements for Each Label
The security administrator agrees that the set of labels that are mandated by the legal department is a useful starting point. However, the further analysis is needed before the labels can be encoded.
Requirements for CONFIDENTIAL: INTERNAL_USE_ONLY
The CONFIDENTIAL: INTERNAL_USE_ONLY label is for information that is proprietary to the company but which, because of its low level of sensitivity, can be distributed to all employees. All employees have signed nondisclosure agreements before starting employment. Information with this label might also be distributed to others. For example, the employees of vendors and contractors who have signed a nondisclosure agreement can receive the information. Because the Internet can be snooped, information with this label cannot be sent over the Internet. The information can be sent over email within the company.
Candidates for the CONFIDENTIAL: INTERNAL_USE_ONLY label include the following:
-
Spending guidelines
-
Internal job postings
Requirements for CONFIDENTIAL: NEED_TO_KNOW
The CONFIDENTIAL: NEED_TO_KNOW label is intended for information that is proprietary to the company, has a higher level of sensitivity than INTERNAL_USE_ONLY, and has a more limited audience. Distribution is limited to employees who need to know the information. Other people who need to know the information and who have signed nondisclosure agreements might also be in the audience.
For example, if only the group of people working in a particular project should see certain information, then NEED_TO_KNOW should be used on that information. Whenever information should be restricted to a particular group, the name of the group should be specified on the paper version of the information.
Having the name of a group in this label makes it clear that the information should not be given to anyone outside of the group. Information with this label cannot be sent over the Internet but it can be sent over email within the company.
Candidates for the NEED_TO_KNOW label include the following:
-
Product design documents
-
Project details
-
Employee Status Change form
Requirements for CONFIDENTIAL: REGISTERED
The CONFIDENTIAL: REGISTERED classification is intended for information that is proprietary to the company, has a very high level of sensitivity, and could significantly harm the company if released. Registered information must be numbered and be tracked by the owner. Each copy must be assigned to a specific person. The copy must be returned to the owner for destruction after being read. Copies can be made only by the owner of the information. Use of brownish-red paper is recommended because this color cannot be copied.
This label is to be used when only one specific group of people should be allowed to see the proprietary information. This information cannot be shown to anyone who is not authorized by the owner. The information cannot be shown to employees of other companies who have not signed a nondisclosure agreement, even if the owner authorizes the disclosure. Information with this label cannot be sent through email.
Candidates for the CONFIDENTIAL: REGISTERED label include the following:
-
End of quarter financial information that has not yet been released
-
Sales forecasts
-
Marketing forecasts
Names of Groups With NEED_TO_KNOW Label
The security administrator decided that the NEED_TO_KNOW label should contain the names of groups or departments. The security Administrator asked for suggestions about what words to use to define groups or areas of interest within the organization. The following items were in the initial list:
-
Engineering
-
Executive Management
-
Finance
-
Human Resources
-
Legal
-
Manufacturing
-
Marketing
-
Sales
-
System Administration
Later, the security administrator added the Project Team group, which enabled all members of the Engineering and Marketing groups to share project data.
Understanding the Set of Labels
The next step is to resolve the following issues:
-
How to use the classifications and compartments to encode the labels and clearances
-
Which handling instructions should appear on printed output
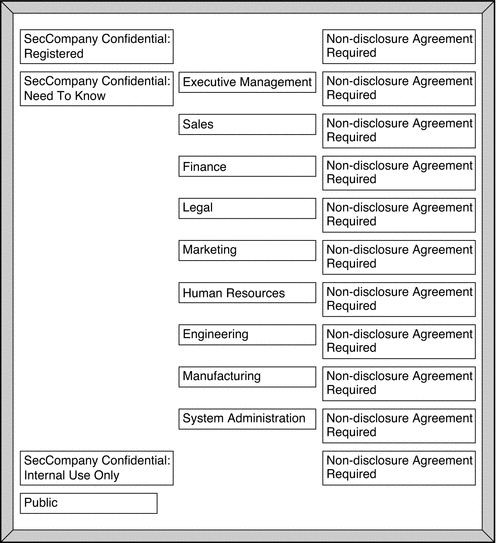
The security administrator used a large board. Pieces of paper were marked with the words that should be in the labels, as shown in Figure 6–5. This setup graphed the relationships. The pieces could be rearranged until all the pieces fit together.
The administrator drafted the following label relationships:
-
The four labels are hierarchical with the label that contains REGISTERED the highest. The PUBLIC label is the lowest.
-
Only one label needs to be associated with group names
The list of people who are cleared to receive registered information is limited on a case by case basis. Therefore, REGISTERED does not need any group names. INTERNAL_USE_ONLY applies to all employees and people who have signed nondisclosure agreements and PUBLIC labels are for everybody. Therefore, INTERNAL_USE_ONLY and PUBLIC labels do not need further qualification. The NEED_TO_KNOW label does need to be associated with non-hierarchical words, such as NEED_TO_KNOW MARKETING or NEED_TO_KNOW ENGINEERING. The words that identify the group or department can also be included in a user's clearance, as part of establishing that user's need to know.
-
Each of the labels except PUBLIC requires the person who is accessing the information to have signed a nondisclosure agreement.
A phrase such as NON-DISCLOSURE AGREEMENT REQUIRED would be a good reminder that this requirement exists.
-
The handling instructions on banner and trailer pages should have clear wording on how to handle the information. How to handle the information is based on the classification and on any group name that can appear in the label.
Along with information on the sensitivity of the printer output, handling instructions should print that a nondisclosure agreement is required when the label requires such an agreement.
Figure 6–5 Sample Planning Board for Label Relationships
Defining the Set of Labels
In this section the set of labels is defined in lists that include all of the following required aspects of labels:
-
Classifications
-
Other words
-
Relations between and among the words
-
Classification restrictions that are associated with use of each word
-
Intended use of the words in sensitivity labels and clearances
-
Intended use of the words in labeling system output, such as print and email
Planning the Classifications
Because the four labels are hierarchical, the four labels are encoded as hierarchical classifications.
With the legal department's approval, the security administrator shortened the labels by omitting SecCompany Confidential: from the label names. Long classifications make labels hard to read in window frames. The name of a label is truncated from right to left in the window frames. Because the truncated names of all the label names above PUBLIC would begin with the words SECCOMPANY, the truncated names would be indistinguishable without manually extending the frame for each window.
The security administrator defined the following labels:
-
REGISTERED
-
NEED_TO_KNOW
-
INTERNAL_USE_ONLY
-
PUBLIC
Planning the Compartments
The group names will be encoded as non-hierarchical compartments. Compartments will be restricted to appear only in labels that have the NEED_TO_KNOW classification. Compartment restrictions are encoded in the ACCREDITATION RANGE section under COMBINATION CONSTRAINTS.
User clearances will control which users can create files and directories that have a group name in the label. User clearances will also control which users can create documents that have a label with more than one group name along with the NEED_TO_KNOW classification.
Planning the Use of Words in MAC
The classifications and compartments in sensitivity labels and user clearances are used in mandatory access control (MAC). Therefore, the legal department's hierarchical labels and the group names need to be encoded as classifications and compartments so that they can be used in the labels that control which individual employees can access files and do other work.
SecCompany, Inc. defines a sensitivity label with the PUBLIC classification, which is assigned the lowest value in the User Accreditation Range, and another sensitivity label with the INTERNAL_USE_ONLY classification with the next highest value above PUBLIC.
An employee with no authorizations whose clearance is PUBLIC and whose minimum label is PUBLIC is able to use the system as follows:
-
Works only in a PUBLIC workspace.
-
Creates files only at PUBLIC.
-
Reads email only at PUBLIC.
-
Uses printers that have PUBLIC in their label range.
In contrast, an employee with no authorizations whose clearance is INTERNAL_USE_ONLY is able to use the system as follows:
-
Works in either a PUBLIC or an INTERNAL_USE_ONLY workspace.
-
Creates files at either PUBLIC or INTERNAL_USE_ONLY, depending on the employee's current workspace.
-
Receives and sends email at either sensitivity label.
-
Can print a file that is labeled PUBLIC on any printer with PUBLIC in its label range. Can send a file labeled INTERNAL_USE_ONLY to any printer with INTERNAL_USE_ONLY in its label range.
Planning the Use of Words in Labeling System Output
When the sensitivity label of a printer job contains a group name compartment, the mandatory printer banner and trailer pages print the following text:
Distribute Only To Group Name (Non-Disclosure Agreement Required) |
Planning Unlabeled Printer Output
The Print Without Labels authorization allows a user or role to use the lp -o nolabels option to suppress the printing of top and bottom labels on body pages of a print job. The Security Administrator role can give the Print Without Labels authorization to everyone or to no one.
The Print PostScript File authorization allows a user to submit a PostScript file to the printer. PostScript printing is usually not allowed because of the risk that a knowledgeable user can change the labels in the PostScript file.
To permit technical writers to produce master copies of documents without labels printed on them, the Security Administrator role gives the Print Without Labels and Print PostScript File authorizations to all the writers.
Planning for Supporting Procedures
The security administrator creates security policies to enforce the labeling scheme.
Rules for Protecting a REGISTERED File or Directory
The security administrator realizes that anyone with a clearance that includes the word REGISTERED can access any registered information anywhere in the company. Further precautions are needed. For example, users who have REGISTERED in their clearance must be instructed to use UNIX permissions to protect their files. Permissions should be set so that only the creator can look at or modify the file. The following example shows a user who is applying discretionary access control to protect the contents of a REGISTERED directory.
Example 6–2 Using DAC to Protect Registered Information
% plabel REGISTERED % mkdir registered.dir % chmod 700 registered.dir % cd registered.dir % touch registered.file % ls -l -rwxrwxrwx registered.file % chmod 600 registered.file % ls -l -rw------- registered.file |
As shown in the example, the user who creates a file or directory while working at an sensitivity label of REGISTERED needs to set the file's permissions to be read and write for the owner only. Directory permissions are set to be readable, writable, and searchable only by the owner. These permissions ensure that another user who can work at REGISTERED cannot read the file.
Rules for Configuring Printers
The following table shows how printers that are available to various work groups need to be configured.
Table 6–1 Printer Label Range Example Settings in Various Locations|
Printer Location |
Type of Access |
Label Range |
|---|---|---|
|
Lobby or public meeting room |
Anyone |
PUBLIC to PUBLIC |
|
Internal company printer room |
Available to all employees and others who have signed nondisclosure agreements |
PUBLIC to INTERNAL_USE_ONLY |
|
Restricted area for one group |
Members of group specified in the NEED_TO_KNOW group-name compartment |
NEED_TO_KNOW group-name to NEED_TO_KNOW group-name |
|
Strictly controlled area |
Available only to people who have the REGISTERED classification in their clearance |
REGISTERED to REGISTERED |
Rules for Handling Printer Output
People who have access to restricted printers will be instructed to do the following:
-
Protect information according to the instructions on the printer banner and trailer pages.
-
Shred jobs that do not have both a banner and a trailer page. Also shred jobs that do not have matching job numbers on the banner and trailer pages.
Planning the Classification Values in a Worksheet
The worksheet in the following table shows names and hierarchical values defined for the four classifications. Because the value 0 is reserved for the administrative ADMIN_LOW label, the value of the PUBLIC classification is set to 1. The values of the other classifications are set higher in ascending sensitivity.
Note –
The names of groups in the labels are specified later, as WORDS in the SENSITIVITY LABELS and CLEARANCES sections.
Table 6–2 Classifications Planner
|
name= |
sname=/aname= |
value= |
initial compartments= bit numbers/WORD |
|---|---|---|---|
|
PUBLIC |
PUB |
1 |
None |
|
INTERNAL_USE_ONLY |
IUO |
4 |
None |
|
NEED_TO_KNOW |
NTK |
5 |
None |
|
REGISTERED |
REG |
6 |
None |
Planning the Compartment Values and Combination Constraints in a Worksheet
The following table defines the relationships between words and classifications. The relationships were determined by moving things around on the planning board in Figure 6–5. PUBLIC and INTERNAL_USE_ONLY can never appear in a label with any compartment. NEED_TO_KNOW can appear in a label with any of the compartments or all of the compartments.
Table 6–3 Compartments and User Accreditation Range Combinations Planner|
Classification |
Compartment Name/ sname/ Bit |
Combination Constraints |
|---|---|---|
|
PUBLIC |
|
PUBLIC only valid combinations |
|
INTERNAL_USE_ONLY |
|
INTERNAL_USE_ONLY only valid combinations |
|
NEED_TO_KNOW |
SYSTEM ADMINISTRATION/ SYSADM/ 19 |
NEED_TO_KNOW all combinations valid |
|
|
MANUFACTURING/ MANU/ 18 |
|
|
|
ENGINEERING/ ENG/ 17 20 |
|
|
|
HUMAN RESOURCES/ HR/ 16 |
|
|
|
MARKETING/ MKTG/ 15 20 |
|
|
|
LEGAL/ LEGAL/ 14 |
|
|
|
FINANCE/ FINANCE/ 13 |
|
|
|
SALES/ SALES/ 12 |
|
|
|
EXECUTIVE MANAGEMENT GROUP/ EMGT/ 11 |
|
|
|
ALL_DEPARTMENTS/ ALL/ 11-20 |
|
|
REGISTERED |
|
REGISTERED only valid combinations |
The security administrator uses the following table to keep track of which bits have been used for compartments.
Table 6–4 Compartment Bit Tracking Table|
11 |
12 |
13 |
14 |
15 |
16 |
17 |
18 |
19 |
20 |
|
Planning the Clearances in a Worksheet
The components of these labels are also assigned to users in clearances. The worksheet's Clearance Planner, Table 6–5, defines the label components to be used in clearances.
Key to Table 6–5:
|
Abbreviation |
Name |
|---|---|
|
REG |
REGISTERED |
|
NTK |
NEED_TO_KNOW |
|
IUO |
INTERNAL_USE_ONLY |
|
EMGT |
EXECUTIVE MANAGEMENT GROUP |
|
SALES |
SALES |
|
FIN |
FINANCE |
|
LEGAL |
LEGAL |
|
MKTG |
MARKETING |
|
HR |
HUMAN RESOURCES |
|
ENG |
ENGINEERING |
|
MANU |
MANUFACTURING |
|
SYSADM |
SYSTEM ADMINISTRATION |
|
NDA |
NON-DISCLOSURE AGREEMENT |
Table 6–5 Clearance Planner
|
CLASS |
COMP |
COMP |
COMP |
COMP |
COMP |
COMP |
COMP |
COMP |
COMP |
Notes |
|---|---|---|---|---|---|---|---|---|---|---|
|
REG |
EMGT |
ENG |
FIN |
HR |
LEGAL |
MANU |
MKTG |
SALES |
SYSADM |
Highest, not used *
|
|
REG |
|
|
|
|
|
|
|
|
|
Assigned to selected personnel as needed **
|
|
NTK |
|
ENG |
|
|
|
|
|
|
|
Assigned to ENG group |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
SYSADM |
Assigned to system administrator |
|
IUO |
|
|
|
|
|
|
|
|
|
Assigned to employees. and others with NDAs |
|
PUB |
|
|
|
|
|
|
|
|
|
Assigned to anyone |
* The highest possible label in the system consists of the highest classification and all of the defined compartments. Because no one should be able to access all information in all departments, this label is not in the user accreditation range. No one should be assigned this clearance.
** When working at the REGISTERED sensitivity label, the user should set permissions to restrict access to everyone except the owner. File permissions of 600 and directory permissions of 700 restrict access.
Planning the Printer Banners in a Worksheet
The SecCompany legal department wants the following to appear on printer banner and trailer pages.
SecCompany Confidential: |
The PRINTER BANNERS can be used to associate a string with any compartment that appears in the sensitivity label of the print job. In this encodings, only the NEED_TO_KNOW classification has compartments. The following table shows how the desired wording is specified as a prefix and assigned to each compartment. The abbreviation NTK is assigned to each channel so that the wording in the PRINTER BANNERS section includes the group name:
SecCompany Confidential: group-name |
|
Prefix |
Printer Banner (Word, No Suffix) |
|---|---|
|
SECCOMPANY CONFIDENTIAL: |
ALL_DEPARTMENTS |
|
SECCOMPANY CONFIDENTIAL: |
EXECUTIVE_MANAGEMENT_GROUP |
|
SECCOMPANY CONFIDENTIAL: |
SALES |
|
SECCOMPANY CONFIDENTIAL: |
FINANCE |
|
SECCOMPANY CONFIDENTIAL: |
LEGAL |
|
SECCOMPANY CONFIDENTIAL: |
MARKETING |
|
SECCOMPANY CONFIDENTIAL: |
HUMAN_RESOURCES |
|
SECCOMPANY CONFIDENTIAL: |
ENGINEERING |
|
SECCOMPANY CONFIDENTIAL: |
MANUFACTURING |
|
SECCOMPANY CONFIDENTIAL: |
SYSTEM_ADMINISTRATION |
|
SECCOMPANY CONFIDENTIAL: |
PROJECT_TEAM |
Planning the Channels in a Worksheet
The SecCompany legal department wants the following handling instructions to appear on printer banner and trailer pages.
DISTRIBUTE ONLY TO group-name EMPLOYEES (NON-DISCLOSURE AGREEMENT REQUIRED) |
This goal is met by assigning in the CHANNELS section the same compartment bits that were assigned to group names earlier in this example. The SecCompany company plans to use the same group names both in the compartments and in the channels.
The words that come before the channel name are specified as prefixes and the words that come after the channel name are specified as suffixes. The security administrator specifies prefixes and suffixes in the following worksheets.
Table 6–7 SecCompany Channels Planner|
Prefix |
Channel |
Suffix |
|---|---|---|
|
DISTRIBUTE_ONLY_TO |
EXECUTIVE_MANAGEMENT_GROUP |
EMPLOYEES (NON-DISCLOSURE_AGREEMENT_REQUIRED) |
|
DISTRIBUTE_ONLY_TO |
SALES |
EMPLOYEES (NON-DISCLOSURE_AGREEMENT_REQUIRED) |
|
DISTRIBUTE_ONLY_TO |
FINANCE |
EMPLOYEES (NON-DISCLOSURE_AGREEMENT_REQUIRED) |
|
DISTRIBUTE_ONLY_TO |
LEGAL |
EMPLOYEES (NON-DISCLOSURE_AGREEMENT_REQUIRED) |
|
DISTRIBUTE_ONLY_TO |
MARKETING |
EMPLOYEES (NON-DISCLOSURE_AGREEMENT_REQUIRED) |
|
DISTRIBUTE_ONLY_TO |
HUMAN_RESOURCES |
EMPLOYEES (NON-DISCLOSURE_AGREEMENT_REQUIRED) |
|
DISTRIBUTE_ONLY_TO |
ENGINEERING |
EMPLOYEES (NON-DISCLOSURE_AGREEMENT_REQUIRED) |
|
DISTRIBUTE_ONLY_TO |
MANUFACTURING |
EMPLOYEES (NON-DISCLOSURE_AGREEMENT_REQUIRED) |
|
DISTRIBUTE_ONLY_TO |
SYSTEM_ADMINISTRATION |
EMPLOYEES (NON-DISCLOSURE_AGREEMENT_REQUIRED) |
|
DISTRIBUTE_ONLY_TO |
PROJECT_TEAM |
EMPLOYEES (NON-DISCLOSURE_AGREEMENT_REQUIRED) |
Planning the Minimums in an Accreditation Range
The following minimums must be set:
-
Minimum sensitivity label
-
Minimum clearance
-
Minimum protect as classification
The SecCompany company wants employees to be able to use all the defined sensitivity labels. Also, the company wants to be able to assign the PUBLIC clearance to some employees. Therefore, the minimum sensitivity label and minimum clearance need to be set to PUBLIC.
The minimum protect as classification is printed on printer banner and trailer pages instead of the actual classification from the job's sensitivity label. The minimum protect as classification can be set higher than the actual minimum classification. However, the SecCompany company requirements allow the minimum protect as classification to always be equal to the real classification of the print job's sensitivity label. The security administrator specifies the value PUBLIC for the minimum sensitivity label, minimum clearance and minimum protect as classification.
Planning the Colors in a Worksheet
The color that is assigned to a label displays in the background whenever the name of the label appears at the top of a window. The lettering is displayed in a color that is computed by the window system to complement the background. In our example, the security administrator chooses to keep the colors already assigned to the administrative labels in the default label_encodings file. The administrator assigns green to PUBLIC, yellow to INTERNAL_USE_ONLY, blue to labels that contain NEED_TO_KNOW (with different shades of blue assigned to each compartment), and red to REGISTERED, as shown in the following table.
Table 6–8 SecCompany Color Names Planner|
Label or Name (label= or name=) |
Color |
|---|---|
|
ADMIN_LOW |
#BDBDBD |
|
PUBLIC |
green |
|
INTERNAL_USE_ONLY |
yellow |
|
NEED_TO_KNOW |
blue |
|
NEED_TO_KNOW EMGT |
#7FA9EB |
|
NEED_TO_KNOW SALES |
#87CEFF |
|
NEED_TO_KNOW FINANCE |
#00BFFF |
|
NEED_TO_KNOW LEGAL |
#7885D0 |
|
NEED_TO_KNOW MKTG |
#7A67CD |
|
NEED_TO_KNOW HR |
#7F7FFF |
|
NEED_TO_KNOW ENG |
#007FFF |
|
NEED_TO_KNOW MANU |
#0000BF |
|
NEED_TO_KNOW PROJECT_TEAM |
#9E7FFF |
|
NEED_TO_KNOW SYSADM |
#5B85D0 |
|
NEED_TO_KNOW ALL |
#4D658D |
|
NEED_TO_KNOW SYSADM |
#5B85D0 |
|
REGISTERED |
red |
|
ADMIN_HIGH |
#636363 |
Editing and Installing the label_encodings File
The install team makes a printed copy and an online copy of the installed label_encodings file. The copy is used in case of problems with the new version of the file that the Security Administrator role supplies.
The Security Administrator role uses a text editor to create the label_encodings file, and then uses the Check Encodings action to check the file. If the file passes Check Encodings, the action offers the option of installing the new version. When the Security Administrator role answers Yes, Check Encodings backs up the current version of the label_encodings file, and creates a new label_encodings file.
Encoding the Version
The following example shows the VERSION string that is modified with the name of company, a title, version number, and date.
Example 6–3 SecCompany VERSION Entry
VERSION= SecCompany, Inc. Example Version - 2.2 00/04/18 |
Encoding the Classifications
The following example shows the SecCompany classifications and values from Table 6–2, Table 6–3 and Table 6–4 added to the CLASSIFICATIONS section.
Example 6–4 SecCompany CLASSIFICATIONS Section
CLASSIFICATIONS: name= PUBLIC; sname= PUBLIC; value= 1; name= INTERNAL_USE_ONLY; sname= INTERNAL; aname= INTERNAL; value= 4; name= NEED_TO_KNOW; sname= NEED_TO_KNOW; aname= NEED_TO_KNOW; value= 5; name= REGISTERED; sname= REGISTERED; aname= REGISTERED; value= 6; |
Note –
A classification cannot contain the slash (/), or comma (,) character. The classifications are specified from the lowest value to the highest.
Encoding the Sensitivity Labels
The compartments in the Table 6–3 are encoded in the following example. The labels do not have any required combinations or combination constraints.
Example 6–5 SecCompany WORDS in the SENSITIVITY LABELS Section
SENSITIVITY LABELS: WORDS: name= ALL_DEPARTMENTS; sname= ALL; compartments= 11-20; minclass= NEED_TO_KNOW; name= EXECUTIVE_MGT_GROUP; sname= EMGT; compartments= 11; minclass= NEED_TO_KNOW; name= SALES; sname= SALES; compartments= 12; minclass= NEED_TO_KNOW; name= FINANCE; sname= FINANCE; compartments= 13; minclass= NEED_TO_KNOW; name= LEGAL; sname= LEGAL; compartments= 14; minclass= NEED_TO_KNOW; name= MARKETING; sname= MKTG; compartments= 15 20; minclass= NEED_TO_KNOW; name= HUMAN_RESOURCES; sname= HR; compartments= 16; minclass= NEED_TO_KNOW; name= ENGINEERING; sname= ENG; compartments= 17 20; minclass= NEED_TO_KNOW; name= MANUFACTURING; sname= MANUFACTURING; compartments= 18; minclass= NEED_TO_KNOW; name= SYSTEM_ADMINISTRATION; sname= SYSADM; compartments= 19; minclass= NEED_TO_KNOW; name= PROJECT_TEAM; sname= P_TEAM; compartments= 20; minclass= NEED_TO_KNOW; REQUIRED COMBINATIONS: COMBINATION CONSTRAINTS: |
Encoding the Information Labels
Even though information labels are not used, values must be supplied under the INFORMATION LABELS: WORDS: section for the file to pass the encodings check. The Security Administrator role copies the words from the SENSITIVITY LABELS: WORDS: section, as shown in the following example.
Example 6–6 SecCompany WORDS in the INFORMATION LABELS Section
INFORMATION LABELS: WORDS: name= ALL_DEPARTMENTS; sname= ALL; compartments= 11-20; minclass= NEED_TO_KNOW; name= EXECUTIVE_MGT_GROUP; sname= EMGT; compartments= 11; minclass= NEED_TO_KNOW; name= SALES; sname= SALES; compartments= 12; minclass= NEED_TO_KNOW; name= FINANCE; sname= FINANCE; compartments= 13; minclass= NEED_TO_KNOW; name= LEGAL; sname= LEGAL; compartments= 14; minclass= NEED_TO_KNOW; name= MARKETING; sname= MKTG; compartments= 15 20; minclass= NEED_TO_KNOW; name= HUMAN_RESOURCES; sname= HR; compartments= 16; minclass= NEED_TO_KNOW; name= ENGINEERING; sname= ENG; compartments= 17 20; minclass= NEED_TO_KNOW; name= MANUFACTURING; sname= MANUFACTURING; compartments= 18; minclass= NEED_TO_KNOW; name= SYSTEM_ADMINISTRATION; sname= SYSADM; compartments= 19; minclass= NEED_TO_KNOW; name= PROJECT_TEAM; sname= P_TEAM; compartments= 20; minclass= NEED_TO_KNOW; REQUIRED COMBINATIONS: COMBINATION CONSTRAINTS: |
Encoding the Clearances
Because the clearance words are the same as the sensitivity labels words, the words in the following example are the same as the words in Example 6–5.
Example 6–7 SecCompany WORDS in the CLEARANCES Section
CLEARANCES: WORDS: name= ALL_DEPARTMENTS; sname= ALL; compartments= 11-20; minclass= NEED_TO_KNOW; name= EXECUTIVE_MANAGEMENT_GROUP; sname= EMGT; compartments= 11; minclass= NEED_TO_KNOW; name= SALES; sname= SALES; compartments= 12; minclass= NEED_TO_KNOW; name= FINANCE; sname= FINANCE; compartments= 13; minclass= NEED_TO_KNOW; name= LEGAL; sname= LEGAL; compartments= 14; minclass= NEED_TO_KNOW; name= MARKETING; sname= MKTG; compartments= 15 20; minclass= NEED_TO_KNOW; name= HUMAN_RESOURCES; sname= HR; compartments= 16; minclass= NEED_TO_KNOW; name= ENGINEERING; sname= ENG; compartments= 17 20; minclass= NEED_TO_KNOW; name= MANUFACTURING; sname= MANUFACTURING; compartments= 18; minclass= NEED_TO_KNOW; name= SYSTEM_ADMINISTRATION; sname= SYSADM; compartments= 19; minclass= NEED_TO_KNOW; name= PROJECT_TEAM; sname= P_TEAM; compartments= 20; minclass= NEED_TO_KNOW; REQUIRED COMBINATIONS: COMBINATION CONSTRAINTS: |
Encoding the Channels
This example is encoded with one channel for each group name compartment. Each channel uses the same compartment bits that are assigned to the compartment words in the SENSITIVITY LABELS: WORDS: section. The prefix is defined as DISTRIBUTE ONLY TO. The suffix is defined as (NON-DISCLOSURE AGREEMENT REQUIRED).
DISTRIBUTE ONLY TO group-name (NON-DISCLOSURE AGREEMENT REQUIRED) |
The channel specifications in the following example create the desired wording in the handling instructions section.
Note –
The prefixes and suffixes are defined at the top of the section as shown in the following example. No compartments are assigned to them. The prefixes and suffixes are used to define the channels.
Example 6–8 SecCompany WORDS in the CHANNELS Section
CHANNELS: WORDS: name= DISTRIBUTE_ONLY_TO; prefix; name= EMPLOYEES (NON-DISCLOSURE AGREEMENT REQUIRED); suffix; name= EXECUTIVE_MANAGEMENT_GROUP; prefix= DISTRIBUTE_ONLY_TO; compartments= 11; suffix= EMPLOYEES (NON-DISCLOSURE AGREEMENT REQUIRED); name= SALES; prefix= DISTRIBUTE_ONLY_TO; compartments= 12; suffix= EMPLOYEES (NON-DISCLOSURE AGREEMENT REQUIRED); name= FINANCE; prefix= DISTRIBUTE_ONLY_TO; compartments= 13; suffix= EMPLOYEES (NON-DISCLOSURE AGREEMENT REQUIRED); name= LEGAL; prefix= DISTRIBUTE_ONLY_TO; compartments= 14; suffix= EMPLOYEES (NON-DISCLOSURE AGREEMENT REQUIRED); name= MARKETING; prefix= DISTRIBUTE_ONLY_TO; compartments= 15 20; suffix= EMPLOYEES (NON-DISCLOSURE AGREEMENT REQUIRED); name= HUMAN_RESOURCES; prefix= DISTRIBUTE_ONLY_TO; compartments= 16; suffix= EMPLOYEES (NON-DISCLOSURE AGREEMENT REQUIRED); name= ENGINEERING; prefix= DISTRIBUTE_ONLY_TO; compartments= 17 20; suffix= EMPLOYEES (NON-DISCLOSURE AGREEMENT REQUIRED); name= MANUFACTURING; prefix= DISTRIBUTE_ONLY_TO; compartments= 18; suffix= EMPLOYEES (NON-DISCLOSURE AGREEMENT REQUIRED); name= SYSTEM_ADMINISTRATION; prefix= DISTRIBUTE_ONLY_TO; compartments= 19; suffix= EMPLOYEES (NON-DISCLOSURE AGREEMENT REQUIRED); name= PROJECT_TEAM; prefix= DISTRIBUTE_ONLY_TO; compartments= 20; suffix= EMPLOYEES (NON-DISCLOSURE AGREEMENT REQUIRED); |
Encoding the Printer Banners
Note –
The term printer banners has a specialized meaning in the label_encodings file. A printer banner appears as a string on the printer banner page when the compartment that is associated with it appears in a job's label.
The printer banner specifications that are shown in the following example create the desired wording in the PRINTER BANNERS section. For a sample banner page, see Figure 4–2.
Note –
Prefixes are defined at the top of the section, as shown in the following example. The prefixes have no assigned compartments.
Example 6–9 SecCompany WORDS in the PRINTER BANNERS Section
PRINTER BANNERS: WORDS: name= COMPANY CONFIDENTIAL:; prefix; name= ALL_DEPARTMENTS; prefix= COMPANY CONFIDENTIAL:; suffix=(NON-DISCLOSURE AGREEMENT REQUIRED); compartments= 11-20; name= EXECUTIVE_MANAGEMENT_GROUP; prefix= COMPANY CONFIDENTIAL:; suffix=(NON-DISCLOSURE AGREEMENT REQUIRED); compartments= 11; name= SALES; prefix= COMPANY CONFIDENTIAL:; suffix=(NON-DISCLOSURE AGREEMENT REQUIRED); compartments= 12; name= FINANCE; prefix= COMPANY CONFIDENTIAL:; suffix=(NON-DISCLOSURE AGREEMENT REQUIRED); compartments= 13; name= LEGAL; prefix= COMPANY CONFIDENTIAL:; suffix=(NON-DISCLOSURE AGREEMENT REQUIRED); compartments= 14; name= MARKETING; prefix= COMPANY CONFIDENTIAL:; suffix=(NON-DISCLOSURE AGREEMENT REQUIRED); compartments= 15 20; name= HUMAN_RESOURCES; prefix= COMPANY CONFIDENTIAL:; suffix=(NON-DISCLOSURE AGREEMENT REQUIRED); compartments= 16; name= ENGINEERING; prefix= COMPANY CONFIDENTIAL:; suffix=(NON-DISCLOSURE AGREEMENT REQUIRED); compartments= 17 20; name= MANUFACTURING; prefix= COMPANY CONFIDENTIAL:; suffix=(NON-DISCLOSURE AGREEMENT REQUIRED); compartments= 18; name= SYSTEM_ADMINISTRATION; prefix= COMPANY CONFIDENTIAL:; suffix=(NON-DISCLOSURE AGREEMENT REQUIRED); compartments= 19; name= PROJECT_TEAM; prefix= COMPANY CONFIDENTIAL:; suffix=(NON-DISCLOSURE AGREEMENT REQUIRED); compartments= 20; |
Encoding the Accreditation Range
The combination constraints from Table 6–3, and the minimum clearance, minimum sensitivity label and minimum protect as classification from Planning the Minimums in an Accreditation Range are encoded in the ACCREDITATION RANGE: section in the following example. PUBLIC and INTERNAL_USE_ONLY are defined to never appear in a label with any compartment. NEED_TO_KNOW is defined to appear in a label with any combination of compartments. REGISTERED is defined to appear with no compartments.
Example 6–10 SecCompany ACCREDITATION RANGE Section
ACCREDITATION RANGE: classification= PUBLIC; only valid compartment combinations: PUBLIC classification= INTERNAL_USE_ONLY; only valid compartment combinations: INTERNAL classification= NEED_TO_KNOW; all compartment combinations valid; classification= REGISTERED; only valid compartment combinations: REGISTERED minimum clearance= PUBLIC; minimum sensitivity label= PUBLIC; minimum protect as classification= PUBLIC; |
Encoding the Local Definitions
SecCompany, Inc. encodes site column headers and colors in the LOCAL DEFINITIONS section.
Encoding the Column Headers in Label Builders
Label builders are displayed whenever you need to set a label. The following example shows the modifications that changed the default values for the Classification Name and Compartments Name in the label builders.
Example 6–11 SecCompany Headers in label_encodings File
The following excerpt shows the modifications that changed the column headers in the label builders. The SecCompany Security Administrator role modified the compartment name.
Classification Name= Classification; Compartments Name= Department; |
Encoding the Color Names
The color names that are used in Example 6–12 were taken from the worksheet in Table 6–8.
Example 6–12 SecCompany COLOR NAMES Section
COLOR NAMES:
label= Admin_Low; color= #bdbdbd;
label= PUBLIC; color= green;
label= INTERNAL_USE_ONLY; color= yellow;
label= NEED_TO_KNOW; color= blue;
label= NEED_TO_KNOW EMGT; color= #7FA9EB;
label= NEED_TO_KNOW SALES; color= #87CEFF;
label= NEED_TO_KNOW FINANCE; color= #00BFFF;
label= NEED_TO_KNOW LEGAL; color= #7885D0;
label= NEED_TO_KNOW MKTG; color= #7A67CD;
label= NEED_TO_KNOW HR; color= #7F7FFF;
label= NEED_TO_KNOW ENG; color= #007FFF;
label= NEED_TO_KNOW MANUFACTURING; color= #0000BF;
label= NEED_TO_KNOW PROJECT_TEAM; color= #9E7FFF;
label= NEED_TO_KNOW SYSADM; color= #5B85D0;
label= NEED_TO_KNOW ALL; color= #4D658D;
label= REGISTERED; color= red;
label= Admin_High; color= #636363;
*
* End of local site definitions
|
Configuring Users and Printers for Labels
Labeling decisions need to be enforced on users, and on printers.
When setting up user accounts, the Security Administrator role needs to specify the following for every user:
-
The appropriate clearance
To plan user clearances, see Planning the Clearances in a Worksheet.
-
The appropriate minimum label
-
Label visibility
For details, see Managing Users and Rights With the Solaris Management Console (Task Map) in Solaris Trusted Extensions Administrator’s Procedures.
The Security Administrator role can customize labeling or not labeling printed output. For the procedures, see Managing Printing in Trusted Extensions (Task Map) in Solaris Trusted Extensions Administrator’s Procedures.
- © 2010, Oracle Corporation and/or its affiliates
