Chapter 22 Devices in Trusted Extensions (Overview)
This chapter describes the extensions that Solaris Trusted Extensions provides to Solaris device protection.
Device Protection With Trusted Extensions Software
On a Solaris system, devices can be protected by allocation and by authorization. By default, devices are available to regular users without an authorization. A system that is configured with Trusted Extensions software uses the device protection mechanisms of the Solaris OS.
However, by default, Trusted Extensions requires that a device be allocated for use, and that the user be authorized to use the device. In addition, devices are protected by labels. Trusted Extensions provides a graphical user interface (GUI) for administrators to manage devices. The same interface is used by users to allocate devices.
Note –
In Trusted Extensions, users cannot use the allocate and deallocate commands. Users must use the Device Allocation Manager. In Solaris Trusted Extensions (JDS), the title of the GUI is Device Manager.
For information about device protection in the Solaris OS, see Chapter 5, Controlling Access to Devices (Tasks), in System Administration Guide: Security Services.
On a system that is configured with Trusted Extensions, two roles protect devices.
-
The System Administrator role controls access to peripheral devices.
The system administrator makes a device allocatable. Devices that the system administrator makes nonallocatable cannot be used by anyone. Allocatable devices can be allocated only by authorized users.
-
The Security Administrator role restricts the labels at which a device can be accessed and sets device policy. The security administrator decides who is authorized to allocate a device.
The following are the main features of device control with Trusted Extensions software:
-
By default, an unauthorized user on a Trusted Extensions system cannot allocate devices such as tape drives, CD-ROM drives, or diskette drives.
A regular user with the Allocate Device authorization can import or export information at the label at which the user allocates the device.
-
Users invoke the Device Allocation Manager to allocate devices when they are logged in directly. To allocate a device remotely, users must have access to the global zone. Typically, only roles have access to the global zone.
-
The label range of each device can be restricted by the security administrator. Regular users are limited to accessing devices whose label range includes the labels at which the users are allowed to work. The default label range of a device is ADMIN_LOW to ADMIN_HIGH.
-
Label ranges can be restricted for both allocatable and nonallocatable devices. Nonallocatable devices are devices such as frame buffers and printers.
Device Label Ranges
To prevent users from copying sensitive information, each allocatable device has a label range. To use an allocatable device, the user must be currently operating at a label within the device's label range. If the user is not, allocation is denied. The user's current label is applied to data that is imported or exported while the device is allocated to the user. The label of exported data is displayed when the device is deallocated. The user must physically label the medium that contains the exported data.
Effects of Label Range on a Device
To restrict direct login access through the console, the security administrator can set a restricted label range on the frame buffer.
For example, a restricted label range might be specified to limit access to a publicly accessible system. The label range enables users to access the system only at a label within the frame buffer's label range.
When a host has a local printer, a restricted label range on the printer limits the jobs that can be printed on the printer.
Device Access Policies
Trusted Extensions follows the same device policies as the Solaris OS. The security administrator can change default policies and define new policies. The getdevpolicy command retrieves information about device policy, and the update_drv command changes device policy. For more information, see Configuring Device Policy (Task Map) in System Administration Guide: Security Services. See also the getdevpolicy(1M) and update_drv(1M) man pages.
Device-Clean Scripts
A device-clean script is run when a device is allocated or deallocated. The Solaris OS provides scripts for tape drives, CD-ROM drives, and diskette drives. If your site adds allocatable device types to the system, the added devices might need scripts. To see existing scripts, go to the /etc/security/lib directory. For more information, see Device-Clean Scripts in System Administration Guide: Security Services.
For Trusted Extensions software, device-clean scripts must satisfy certain requirements. These requirements are described in the device_clean(5) man page.
Device Manager GUI
The Device Manager is used by administrators to administer allocatable and nonallocatable devices. The Device Manager is also used by regular users to allocate and deallocate devices. The users must have the Allocate Device authorization.
The GUI is called the Device Manager. This GUI is started from the Trusted Path menu by selecting Allocate Device. The following figure shows a Device Manager that was opened by a user who can allocate the audio device.
Figure 22–1 Device Manager Opened by a User
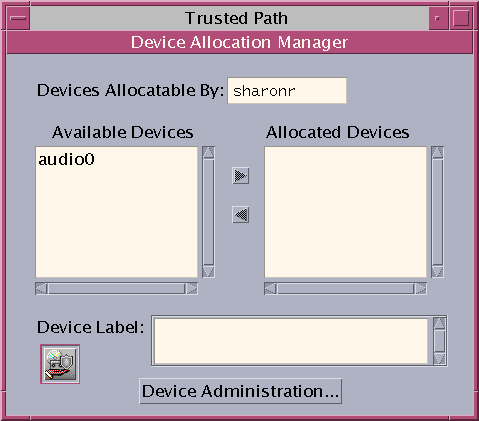
Users see an empty list when they are not authorized to allocate devices. Or, an empty list might indicate that the allocatable devices are currently allocated by another user or are in an error state. If a user cannot see a device in the Available Devices list, the user needs to contact the responsible administrator.
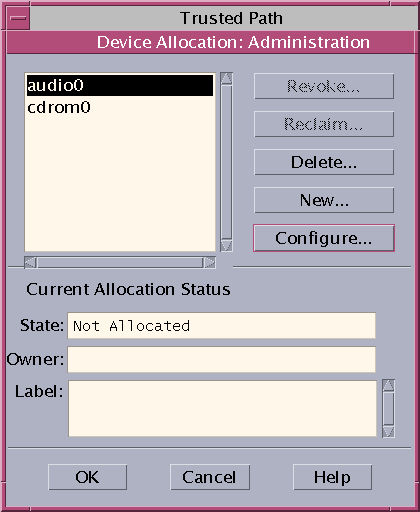
The Device Administration feature is available to roles that have either one or both of the authorizations that are needed to administer devices. The administration authorizations are Configure Device Attributes, and Revoke or Reclaim Device. The following figure shows a Device Allocation Administration dialog box.
Enforcement of Device Security in Trusted Extensions
The security administrator decides who can allocate devices and makes sure that any user who is authorized to use devices is trained. The user is trusted to do the following:
-
Properly label and handle any media containing exported sensitive information so that the information does not become available to anyone who should not see it.
For example, if information at a label of NEED TO KNOW ENGINEERING is stored on a diskette, the person who exports the information must physically label the disk with the NEED TO KNOW ENGINEERING label. The diskette must be stored where it is accessible only to members of the engineering group with a need to know.
-
Ensure that labels are properly maintained on any information being imported (read) from media on these devices.
An authorized user must allocate the device at the label that matches the label of the information that is being imported. For example, if a user allocates a diskette drive at PUBLIC, the user must only import information labeled PUBLIC.
The security administrator is also responsible for enforcing proper compliance with these security requirements.
Devices in Trusted Extensions (Reference)
Trusted Extensions device protection uses Solaris interfaces and Trusted Extensions interfaces.
For Solaris command-line interfaces, see Device Protection (Reference) in System Administration Guide: Security Services.
Administrators who do not have access to the Device Allocation Manager can administer allocatable devices by using the command line. The allocate and deallocate commands have administrative options. For examples, see Forcibly Allocating a Device in System Administration Guide: Security Services and Forcibly Deallocating a Device in System Administration Guide: Security Services.
For Trusted Extensions command-line interfaces, see the add_allocatable(1M) and remove_allocatable(1M) man pages.
- © 2010, Oracle Corporation and/or its affiliates
