The Audit Trail
The collection of all audit files in a distributed system is called the audit trail. The audit trail may consist of audit files in several audit directories, or an audit directory may contain several audit trails. Most often the audit directories will be separate audit file system partitions. Even though they can be included in other file systems, this is not recommended.
Audit files by default are stored in the audit root directory, defined as /etc/security/audit/*/files. Once each workstation has created an audit root directory, and the directories have been mounted (with mount points that follow the naming convention) on the audit administration server, the management tools, auditreduce and praudit, can examine the entire audit trail. See "Basic Audit Setup Procedures" for how to set up an audit trail.
Even though it is possible to locate audit directories within other file systems that are not dedicated to auditing, this is not recommended. If other factors dictate placing audit files on a partition not dedicated to auditing, only do so for directories of last resort. Directories of last resort would be directories where audit files would be written only when there is no other suitable directory available. One other scenario where locating audit directories outside of dedicated audit file systems could be acceptable would be in an environment where auditing is optional, and where it is more important to make full use of disk space than to keep an audit trail. Putting audit directories within other file systems is unworkable in a security-conscious production environment.
How the Audit Trail Is Created
The audit trail is created by the audit daemon, auditd(1M). The audit daemon starts on each workstation when the workstation is booted. After auditd starts, it is responsible for collecting the audit trail data and writing the audit records into audit files, which are also called audit log files. See the audit.log(4) man page for a description of the file format.
Figure 3-1 How Auditing Works
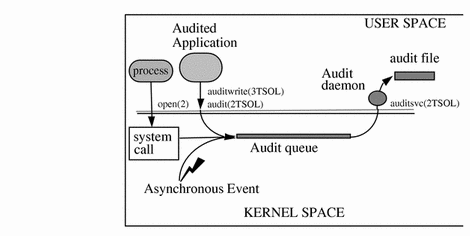
The audit daemon runs as root. All files it creates are owned by root. Even when auditd has no classes to audit, auditd continuously operates, looking for a place to put audit records. The auditd operations continue even if the rest of the workstation's activities are suspended because the kernel's audit buffers are full. The audit operations can continue because auditd is not audited.
- © 2010, Oracle Corporation and/or its affiliates
