How Labels Are Used in Access Control Decisions
In the Trusted Solaris system, both discretionary access control checks and mandatory access control checks must be passed before access is allowed to an object. Discretionary access control is based on Permission Bits and Access Control Lists (see the DEFINITIONS section of the Intro(1) man page, if needed).
Most of the Trusted Solaris documentation does not use the term sensitivity label. In releases beginning with Trusted Solaris 7, information labels are not supported, so it is no longer necessary to differentiate between sensitivity labels and information labels. However, because the label encodings file still has sections for both sensitivity labels and information labels, this document uses these terms where it is needed to clarify the differences.
Mandatory access control compares the label and clearance label of a process running an application with the label or the label range of anything that the process tries to access, according to a set of rules that is sometimes called the system security policy.
-
Site security policy is the security policy set up by an organization to protect its information.
Using Trusted Solaris may be part of the site's security policy.
-
System security policy is the set of rules that is enforced by the operating system software to protect information being processed on the Trusted Solaris system.
If the term security policy appears by itself, consider the context.
The write up/read down (wurd) rule applies when a process tries to access an object.
|
Write Up to Session Clearance and Write Equal |
SL[Process] <= SL[Object] |
|
Read Down and Read Equal |
SL[Process] >= SL[Object] |
As shown in the previous table, writes up are always limited by the session clearance. A process cannot read or write an object whose label is higher than the process's clearance.
Strictly speaking everything, whether it is a file, directory, device, or other object, is treated as a file in a UNIX system. However, files and directories have slightly different access rules from each other and from process objects, System V IPC objects, STREAMS objects, network endpoint objects, device objects, and X window objects. In addition, an object can be accessed three different ways shown in the following list, and for each of the three ways an object can be accessed, a slightly-different set of rules applies:
-
The name of the file, directory, or device may be viewed
-
The contents or the attributes of the file, directory, or device may be viewed
-
The contents or the attributes of the file, directory, or device may be modified
For more details about the rules that are enforced when various types of access are attempted, see the DEFINITIONS sections in Intro(1) and Intro(2) man pages.
Simple Mandatory Access Control Example
If a user brings up a text editor in a workspace with a label of PUBLIC, the process executing the text editor gets the same label as the workspace.
Figure 1-1 shows a comparison between two labels used in making an access control decision. When a user in a workspace with the label INTERNAL_USE_ONLY brings up a text editor, the label of the process running the text editor is automatically set to be equal to the label of the current workspace, and the text editor displays a label of INTERNAL_USE_ONLY. When the text editor attempts to open a file for editing, the label of the process running the text editor is compared to the label of the file. In the example, because the two labels are equal, access for writing is allowed.
Figure 1-1 Comparing the Label of a Text Editor with the Label of a File to be Edited
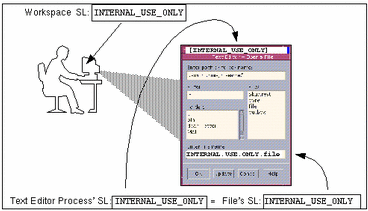
If the label of a file is less than that of the text editor, the file can be opened only for reading. (For example, a normal user can use a text editor to open and read a system file at ADMIN_LOW while working at INTERNAL_USE_ONLY, but the text editor cannot save a change to the file. Another consequence of the WURD rule, because of the read down requirement a user cannot see a file whose label is higher than the current working label. However, if a normal user knows the name of a file that has a higher label, the text editor could be used to make a change to the higher-labeled file, even though the user cannot see the file's name.
- © 2010, Oracle Corporation and/or its affiliates
