Configuring the Software
After the installation image is installed, the install team logs in as the user "install" and assumes the root role to configure initial security, network, and administrative role information, as shown in the following figure.
Figure 1-1 Two Roles Administering a System
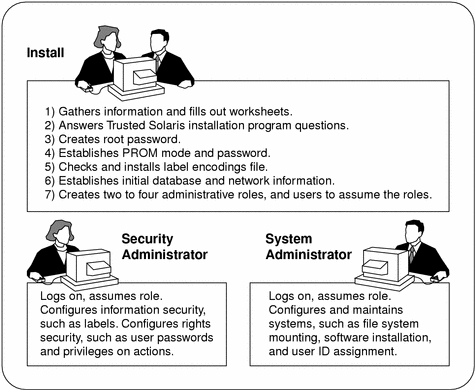
Once users who can assume the administrative roles are created, the install team reboots the computer. Further configuration tasks are then partitioned by the software to a particular role.
The security administrator sets up auditing, protects file systems, sets device policy, determines which programs require privilege to run, and protects users, among other tasks. The system administrator shares and mounts file systems, installs software packages, and creates users, among other tasks.
- © 2010, Oracle Corporation and/or its affiliates
