The User Databases
In the Solaris and the Trusted Solaris environment, user information is held in four databases:
-
user_attr(4) - The /etc/user_attr file contains extended user attributes, using a keyword=value format.
-
auth_attr(4) - The /etc/security/auth_attr file contains the definitions of authorizations, which can be included in rights profiles.
-
prof_attr(4) - The /etc/security/prof_attr file contains the name, description, authorizations, subordinate rights profiles, and help files for rights profiles.
The following figure shows how the user databases work together and with policy.conf(4) and label_encodings(4) to provide user attributes.
Figure 9-1 Trusted Solaris User Databases
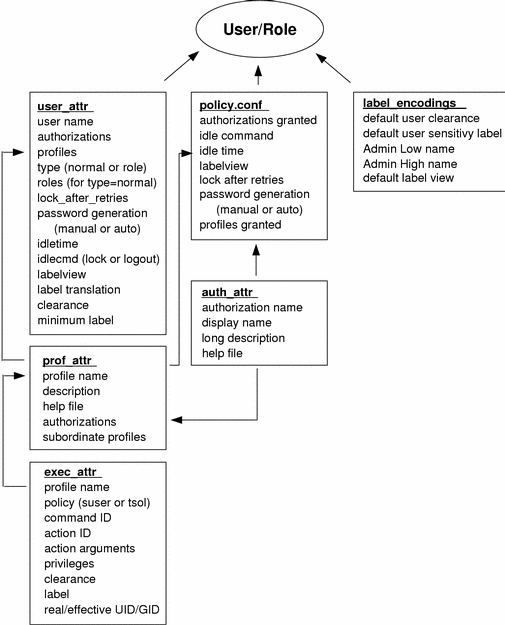
The user_attr database contains the attributes shown, including a comma-separated list of profile names. The contents of the profiles are split between the prof_attr database, which contains profile identification information, authorizations assigned to the profile, and subordinate profiles, and the exec_attr database, which contains commands and actions with their associated security attributes. The auth_attr file supplies available authorizations to the prof_attr database and the policy.conf database. (Note that although it is possible to assign authorizations directly to users through user_attr, this practice is discouraged.) The policy.conf file supplies default attributes to be applied to all users on the machine. The label_encodings file supplies label defaults if they are not otherwise specified.
Note -
The exec_attr entries within a profile are searched only in the scope in which that profile is found. The scope ( files, NIS, or NIS+), is specified in the nsswitch.conf file.
- © 2010, Oracle Corporation and/or its affiliates
