Chapter 8 Specifying Routing and Security for Remote Computers
This chapter provides implementation details and procedures for securing the network. This chapter includes the following procedures.
Assigning Security Attributes to Remote Hosts and Network Gateways
Each site's Security Administrator decides which hosts should be allowed to communicate with the Trusted Solaris system and the security attributes of the hosts. The Security Administrator role uses the Security Families tool in the Solaris Management Console to assign security attributes to hosts by means of templates.
Templates can be assigned directly to a host or indirectly through a wildcard entry that assigns a template to a network address that includes the host. If a host does not have a template assigned either directly or indirectly, no communications can get through. Computers (hosts or routers) that share the same template are considered to be part of the same security family.
Optionally, the SMC Interface Manager tool can be used to assign security attributes to network interfaces, but doing so is useful only in limited circumstances when the defaults are not acceptable:
-
To limit the range of labels at which communications are allowed through a network interface, the Security Administrator role can set a restricted label range. The default label range is
ADMIN_LOWtoADMIN_HIGH. -
If it is desirable to be able to leave certain fields empty in a single template assigned to one computer or to a group of computers that is accessed through the same network interface, the Security Administrator can specify the values in an entry that applies to that network interface.
The entries assigned to network interfaces are looked at only if certain fields are left empty in the template assigned to a computer. If a value is not found either in the template that covers the host or in an entry that applies to the interface through which the remote computer is accessed, then a set of default values is applied.
Before assigning templates, the Security Administrator role should do the following:
-
Review the existing templates.
-
Choose View->Details from the Security Families tool, which displays some of the values specified for each template.
-
Use the Security Families tool to bring up the Template Manager dialog box, select each template in turn and view its contents.
-
-
Decide which templates should be used for each host and network.
-
Modify existing templates or create any new templates needed for the site.
Setting Up Templates
Before assigning templates to hosts, have the following information available:
-
A list of the available templates.
-
A list of all the hosts and networks with which the hosts in the Trusted Solaris network are allowed to communicate.
Make the following decisions before starting:
-
Decide which security attributes to apply to each host.
-
Decide whether you can use existing templates or must modify them.
Storing Network Information
The Security Families tool in the Solaris Management Console stores template definitions in the tnrhtp(4) database and stores template to host assignments in the tnrhdb(4) database. The Interface Manager stores network interface definitions in the tnidb(4) file.
The Trusted Solaris version of the name service switch file, nsswitch.conf(4), includes entries for tnrhtp and tnrhdb, which should be modified to suit each site's configuration. The default for NIS+ is shown below.
# TSOL tnrhtp: files nisplus tnrhdb: files nisplus |
To modify these entries, the System Administrator role uses the Name Service Switch action. See "To Launch Local Administrative Actions", if needed, for how to access the Name Service Switch action. To preserve the required file attributes (owner, group, mode and label), the role should not edit the nsswitch.conf file directly.
Modifying the Boot-Time Tnrhdb File
Local versions of the tnidb(4) and tnrhdb(4) files reside in the /etc/security/tsol directory on every Trusted Solaris computer. These local files are consulted before the system is configured and before the naming server is available. As delivered, the local tnrhdb file has a wildcard entry, 0.0.0.0:admin_low.
The admin_low template may be a security risk on a Trusted Solaris network. Depending on site security requirements, the Security Administrator role may remove the 0.0.0.0 entry once the computer is installed. If it is removed, it must be replaced with entries for every computer the host contacts during boot. Alternatively, the 0.0.0.0 wildcard entry may be assigned a different unlabeled template.
See "To Replace the 0.0.0.0 Entry in the Local Tnrhdb File" for how to change or remove the entry.
Setting Up Tunneling
Tunneling enables the sharing of emetrics for routes on an Intranet even when there is a non-Trusted Solaris cloud of hosts and gateways between two Trusted Solaris gateways. All hosts must be in the same Intranet with gateways using Trusted Solaris extended RIP. Without tunneling, the security response packets generated by extended RIP on one gateway cannot be received on the remote Trusted Solaris gateway to pass along the emetrics of its known routes.
To set up tunneling, the Security Administrator role creates a tunnel file on a Trusted Solaris gateway. The tunnel file contains the IP addresses of remote networks connected to Trusted Solaris gateways. Unlabeled broadcast packets containing security information are sent directly to the networks listed in the tunnel file, where they are picked by Trusted Solaris gateways. See "To Set Up Tunneling".
Note -
The term tunneling as used here has nothing to do with the IP-in-IP tunneling feature in the Solaris environment.
Managing Trusted Networking (Tasks)
To Open the Security Families Tool
-
Assume the Security Administrator role and go to an
ADMIN_LOWworkspace. -
Bring up the Solaris Management Console and load the Trusted Solaris Management Console in the appropriate name service scope.
-
Click the Trusted Solaris Configuration to open its list of tools.
-
Click the Computers and Networks tool and enter a password when prompted.
-
Double-click the Security Families tool.
All currently-defined templates display in the right hand pane. Use the online help.
To Construct Templates for Hosts
-
In the Security Administrator role, open the Security Families tool.
See "To Open the Security Families Tool" for the steps in detail.
-
To modify an existing template, double-click the name of a template, then choose Action --> Properties.
The Modify Template dialog displays with the name of the currently-selected template at its top.
-
To add a new template, choose Action --> Add Template.
Refer to the online help when adding a template.
 Caution -
Caution - When creating a new template, do not forget to change the Default Label. The Default Label in the default template is
ADMIN_LOW, and normal users cannot work at that label.
-
Supply the desired values in the tabs in the Template Manager.
Refer to the online help for assistance.
-
Click OK when done.
To Assign Templates to Hosts
-
In the Security Administrator role, open the Security Families tool.
See "To Open the Security Families Tool" for the steps in detail.
-
To change the assignment of a computer or network to a template, double-click the name of the ALL template.
All computers and networks that are currently in the ALL family display in the right hand pane.
-
Double-click the icon for the computer or network, then choose Action->Properties.
The Modify Remote Host Entry dialog displays with the IP address of the network or computer at its top.
-
Supply the desired values in the fields in the Template Manager, and click OK.
-
To assign an existing template to a computer or network, double-click the name of a template.
All computers currently defined in the same Security Family display in the right hand pane.
-
Choose Action->Add Host.
The New Remote Host Entry dialog displays.
-
Type in either the Hostname or the IP Address for any computer or network to which the template should be assigned.
If a Hostname is entered, when you click the Load button the IP address is looked up. If an IP Address is entered, then the hostname is looked up. The IP Address field accepts any valid IPv4 or IPv6 address for the computer or network.
-
Type in an optional Prefix Length that indicates the length of the network portion of the address.
-
Choose the name of a template from the Template pull-down menu.
-
Click OK.
To Create a Wildcard Entry for Remote Hosts
-
In the Security Administrator role, open the Security Families tool.
See "To Open the Security Families Tool" for the steps in detail.
-
Double-click the ALL template.
-
Choose Action --> Add host(s).
-
Click Wildcard, then give an IP address that ends in a zero (0).
For example, 192.168.0.0 or 192.168.113.0.
-
Assign an existing template to it.
 Caution -
Caution - The wildcard entry allows any host on the wildcard's network to communicate with this system at the label of the assigned template.
To Change the tnd Polling Interval
By default, the tnd polls the trusted network databases every 2 minutes. The default for name service database polling is 30 minutes. You may want to change the tnd polling interval to match the name service interval once the network is up and running, and you have added all the templates and hosts.
-
Assume the Security Administrator role and go to an
ADMIN_LOWworkspace. -
Open the Admin Editor from the System_Admin folder in the Application Manager, and edit the /etc/init.d/inetsvc file.
-
Find the 120 second polling interval, and change it to 1800 or another reasonable value.
To Replace the 0.0.0.0 Entry in the Local Tnrhdb File
The local tnrhdb(4) file on each computer is used to contact the network at boot time. For greater security, you can remove the 0.0.0.0 wildcard entry. However, you must replace it with every remote address that the host contacts at boot time.
-
In the Security Administrator role, open the Security Families tool in the Files scope.
See "To Open the Security Families Tool" for the steps in detail.
-
Double-click ALL, then select 0.0.0.0.
-
If you know all machines that this computer contacts, remove the wildcard entry by choosing Edit --> Delete.
-
To replace the wildcard entry, the following entries must be in the /etc/hosts or /etc/inet/ipnodes file, and in the tnrhdb database.
-
An entry for this system, the name service master, and the loopback address, 127.0.0.1
The install team added these entries during configuration.
-
An entry for every local IP address
The install team should have added these entries during configuration.
-
One or more router entries
If the name service client is a router, list all the routers with which it needs to communicate during boot. Include broadcast addresses.
If the name service client is not a router, create a fallback network entry, such as 192.168.113.0.
-
For a router, make the following entries by clicking Add --> Host(s).
Make sure all network interfaces are in the file. For example,
Host Name: trusted-gw IP Address: 192.168.112.111 Template: tsol
Host Name: trusted IP Address: 192.168.113.111 Template: tsol
Make an entry for every router that this host communicates with. This is most easily done when the network uses static routing. For example,
Host Name: gateway-2 IP Address: 192.168.112.12 Template: unclassified
Host Name: gateway-3 IP Address: 192.168.113.12 Template: unclassified
Make an entry for every broadcast and multicast address. For example,
Host Name: broadcast IP Address: 255.255.255.255 Template: admin_low
Host Name: multicast IP Address: 224.0.0.2 Template: admin_low
Host Name: broadcast-112 IP Address: 192.168.112.255 Template: tsol
Host Name: broadcast-113 IP Address: 192.168.113.255 Template: tsol
The following shows the local tnrhdb file with entries for a name service client with two interfaces. The client communicates with another network and routers.
192.168.112.111:tsol Interface 1 of this system 192.168.113.111:tsol Interface 2 192.168.113.5:tsol NIS+ master 192.168.113.6:tsol Audit server 192.168.113.8:tsol Mail server 192.168.112.255:tsol Subnet broadcast address 192.168.113.255:tsol Subnet broadcast address 127.0.0.1:tsol Loopback address 192.168.117.0:tsol Another Trusted Solaris network 192.168.112.12:unclassified Specific network router 192.168.113.12:unclassified Specific network router 224.0.0.2:unclassified Multicast address 255.255.255.255:admin_low Broadcast address
-
If the host being configured is not a router, click Add --> Host(s) to create a fallback entry so that the host can find its router.
For example,
Click the Wildcard button IP Address: 192.168.113.0 Template: tsol
For example, for a non-router on a dynamically configured network, the entries might look like:
192.168.113.99:tsol This system 192.168.113.5:tsol NIS+ master 192.168.113.0:tsol Subnet wildcard address 127.0.0.1:tsol Loopback address 192.168.117.0:tsol Another Trusted Solaris network 224.0.0.2:unclassified Multicast address 255.255.255.255:admin_low Broadcast address
Note -If a network that has Trusted Solaris hosts is assigned a wildcard template that is not a tsol template and the network has any tsol routers, then the administrator must assign the netmask entry the tsol template. For example,
192.168.112.98:tsol This system 192.168.112.0:confidential Subnet wildcard address 192.168.112.111:tsol TSOL router 255.255.255.255:tsol Broadcast address
-
Example -- Changing the Label of the 0.0.0.0 Tnrhdb Entry
You may want to give the 0.0.0.0 tnrhdb(4) entry a different unlabeled template, such as the unclassified template from the default set of templates. The system then recognizes any computer not otherwise listed in its tnrhdb file as an unlabeled machine at the label unclassified. Choose Action --> Properties from the menu when 0.0.0.0 is selected to change the assigned template.
Many sites create an unlabeled template specifically for gateways, and assign the gateway template to all gateway systems. The following is an unlabeled template specifically for gateways,
unlab_gateway:host_type=unlabeled;\ def_label=[0x00010000000000000000000000000000000000000000000000000000000000000000];\ def_cl=0x00010000000000000000000000000000000000000000000000000000000000000000;\ forced_privs=empty;\ min_sl=0x00000000000000000000000000000000000000000000000000000000000000000000;\ max_sl=0x7fffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff;\ doi=0;\ ip_label=none;\ ripso_label=empty;\ ripso_error=empty; |
The backslashes above are for ease of reading. See "To Construct Templates for Hosts" for how to construct a template, and then assign it to the 0.0.0.0 wildcard.
To Configure a Network Interface
-
If adding a new interface, insert the network interface card, following the hardware and software installation steps in the guides shipped with the interface.
The interface installation program installs a new device file called hostname.device_abbreviation in /etc.
-
For a host with more than one network interface, do the configuration either for a router or multihomed host, as described in the the Solaris TCP/IP and Data Communications Administration Guide.
-
If the site security policy requires other than default settings for any interfaces, change the entries in the Interface Manager.
As described in "Understanding Security Attributes Assigned to Network Interfaces", interfaces on a computer running Trusted Solaris software are automatically detected by the trusted network software and assigned a default set of attributes. The Interface Manager shown below is used only when the security administrator role wants to change the defaults for an interface.
The Interface Manager tool is available when Scope=Files. The default attributes for network interfaces are shown in the following screen shot.
Figure 8-1 Interface Manager with Default Security Attributes
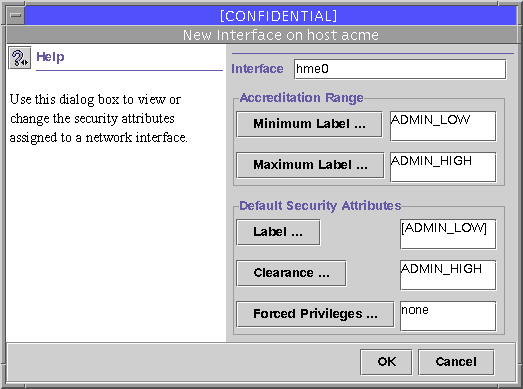
Note -Do not change the Min SL from
ADMIN_LOWunless you have explicitly defined all routes.
To Set Up Static Routes with Emetrics
-
Assume the System Administrator role and go to an
ADMIN_LOWworkspace. -
Double-click the Set TSOL Gateways action in the System_Admin folder to open the /etc/tsolgateways file for editing.
See the tsolgateways(4) man page for more about the syntax and use of /etc/tsolgateways. The syntax of the emetric in tsolgateways is the same as for the route command.
-
Set up one or more default entries, if desired.
The first entry sets up a default route, using a specific gateway's address 192.168.113.36 and a metric of 1 to be used when there is no specific route defined for either the host or destination of a packet.
default 192.168.113.36 1
-
Set up one or more network entries, if desired.
The second line below shows a network entry set up with a standard metric. The third line shows a network entry set up with an emetric, setting a label range of PUBLIC to INTERNAL.
default 192.168.113.36 1 net 192.168.102.0 gateway-101 1 net 192.168.101.0 gateway-102 -m metric=2,min_sl="PUBLIC", max_sl="INTERNAL"
-
Set up one or more host entries, if desired.
The new fourth line shows a host entry set up for a gateway host named trusted with an emetric setting a label range of PUBLIC to PUBLIC.
default 192.168.113.36 1 net 192.168.102.0 gateway-101 1 net 192.168.101.0 gateway-102 -m metric=2,min_sl="PUBLIC", max_sl="INTERNAL" host 192.168.101.3 trusted -m metric=2,min_sl="PUBLIC", max_sl="PUBLIC"
-
Make sure there is an entry for any destination host(s) and gateway(s) in the local /etc/hosts file, or NIS+ hosts.org_dir table.
192.168.113.36 mynah
-
Make sure there is an entry for all destination hosts, network(s) and gateway(s) in the local /etc/security/tsol/tnrhdb file.
192.168.113.36:tsol1
-
Write and quit the file.
:wq
To Set Up Tunneling
A forwarding host is any Trusted Solaris 8 4/01, Trusted Solaris 8, Trusted Solaris 7, or Trusted Solaris 2.5.1 gateway being set up to tunnel through one or more gateway(s) not running a Trusted Solaris 8 4/01, Trusted Solaris 8, Trusted Solaris 7, or Trusted Solaris 2.5.1 release to advertise the emetrics of its routes to the Trusted Solaris gateways on the other side.
-
Assume the Security Administrator role on the forwarding host and go to an
ADMIN_LOWworkspace. -
Use the Admin Editor action to create or open the /etc/security/tsol/tunnel file for editing.
-
Enter one IP address of a target (sub)network on per line.
See the following example.
192.168.36.0
-
Write and quit the file.
:wq
-
To set up two-way routing using emetrics, repeat the previous steps on the remote gateway(s), specifying the IP address for the local network.
- © 2010, Oracle Corporation and/or its affiliates
