Chapter 12 Managing Devices
This chapter describes how to protect information on devices. This chapter contains the following procedures:
Controlling Access to Devices
The system administrator controls access to peripheral devices. Users can use a device only when the System Administrator role makes the device allocatable. Devices that the System Administrator makes nonallocatable cannot be used by anyone. Allocatable devices can be allocated only by authorized users. The Security Administrator role restricts the labels at which a device can be accessed.
Following are some highlights of device management in the Trusted Solaris environment:
-
An unauthorized user in the default Trusted Solaris distributed system cannot allocate devices such as tape drives, CD-ROM drives, or floppy disk drives.
-
A normal user with the Allocate Device authorization can import or export information at the label at which the user allocates the device.
-
Users invoke the Device Allocation Manager to allocate devices when logged in directly. When logged in remotely, from scripts and from user-developed applications, the allocate(1) command is used.
-
Only one authorized user at a time can access an allocatable device. After allocation, deallocating the device clears the device of data and frees it for allocation by another user.
-
The label range of each device handled by the device allocation mechanism can be restricted by the Security Administrator. Normal users are limited to accessing devices whose label range includes the labels at which they are allowed to work. The default label range is
ADMIN_LOWtoADMIN_HIGH. -
Nonallocatable devices are devices such as framebuffers and printers whose data is automatically cleared between users.
-
Label ranges can be restricted for both allocatable and nonallocatable devices.
Setting a Label Range
To restrict direct login access through the console, the Security Administrator role can set a restricted label range on the framebuffer.
For example, a restricted label range might be specified to limit access to a publicly accessible computer. The label range enables users to access the computer only at a label within the framebuffer's label range.
When a host has a local printer, a restricted label range on the printer limits the jobs that it can print.
Managing Device Access Policies
In the Trusted Solaris operating environment, as in other UNIX systems, devices are represented by files called device special files. The discretionary access rules for devices are based on the same UNIX permission bits that apply to other types of files. The mandatory access rules that apply to devices are slightly different from those that apply to files or directories. The following table shows the default mandatory access control policy. These policies automatically apply to any new devices added to the system.
Table 12-1 Default Device Access Policy|
Policy Type |
Description |
Default Policy |
|---|---|---|
|
data_mac_policy |
Label required to access the device |
For reads and writes, the process' label must equal the device's label. |
|
attr_mac_policy |
Label required to access the device's attributes (by acl(2), chmod(2), chown(2), and stat(2)) |
For read access to the device's attributes, the process' label must dominate the device's label. For write access to the device's attributes, the process' label must equal the device's label. |
|
open_priv |
Privilege required to open the device |
No privileges are required. |
|
str_type |
Only for STREAMS devices, specifies how the kernel stream head should control STREAMS messages |
Device type stream. Unlabeled STREAMS message are allowed. |
The Security Administrator role can change default policies and define new policies on each host by editing the /etc/security/tsol/device_policy file. Changes go into effect after a reboot. See the device_policy(4) man page for the keywords and values to use, and see also "To Set or Modify Device Policy for a Device".
Initial Device Configuration Decisions
When configuring the Trusted Solaris environment on every system, the Security Administrator role sets device policy. After the system is up and running, the System Administrator role uses the Device Allocation Manager to add and configure devices, and to revoke an allocation, reclaim an allocated device from an allocate error state, or delete a device.
At system configuration, the Security Administrator needs to make the following decisions:
-
Decide whether the default label range settings on nonallocatable devices are consistent with the site's security policy.
-
Decide whether the default settings for the allocatable devices are consistent with the site's security policy.
-
Decide whether to make additional devices allocatable.
-
Decide which users, if any, should be allowed to allocate devices.
-
Decide whether to use the default Allocate Device authorization or to create and require other authorizations for device allocation.
Decide whether to require separate conditions for a device to be allocated locally from the trusted path and for a device to be allocated without the trusted path either remotely or from a script. See the example of adding new device allocation authorizations in "To Add an Authorization to the Environment".
Managing Devices
The add_allocatable(1M), and remove_allocatable(1M) commands, the Add Allocatable Device action, and the Device Allocation Manager make changes to local versions of the device_allocate(4) and device_maps(4) files on the host on which they are run.
The following figure shows the Device Allocation Manager. The manager lists the allocatable devices currently present on the local system.
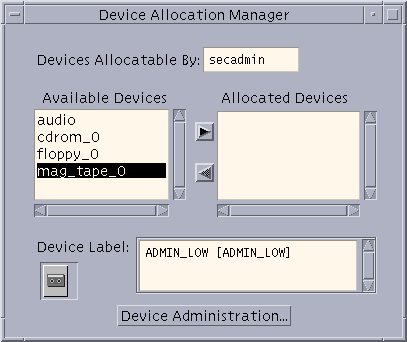
The Device Allocation Manager can be used only by users or roles that have the Allocate Device authorization.
The Device Administration button is visible to roles that have either one or both of the authorizations needed to administer devices, Configure Device Attributes, and Revoke or Reclaim Device.
Making a Device Available
Users see an empty list when they are not authorized to allocate devices, or when the allocatable devices are currently allocated by another user or are in an error state. If a user cannot see a device in the Available Devices list, the user needs to contact the responsible administrator.
-
If the user is not authorized but should be, the Security Administrator role can add the Allocate Device authorization to one of the user's profiles.
-
If the device is not listed because it is already allocated or it is in an allocate error state, the administrator can force deallocation of a device or reclaim it from the error state.
Using the Device Allocation Manager
Clicking the Device Administration button launches the Device Allocation: Administration dialog box. This dialog box is used for reclaiming and revoking devices, deleting, or making entries for new devices.
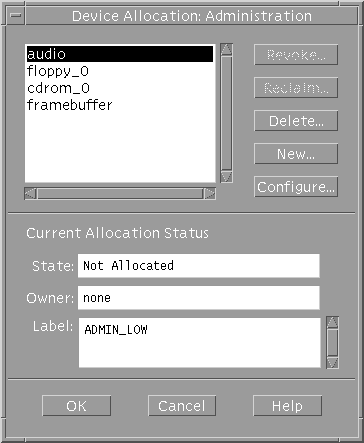
Revoke - Click to force deallocation of the selected device.
Reclaim - Click to release the selected device from the allocate error state and leave it deallocated.
New and Configure - Click to create a new device or configure an existing device.
Configuring a Device
This section describes the information that can be specified for a device using the Device Allocation Configuration dialog box shown in the following figure.
Figure 12-1 Device Allocation Configuration Dialog
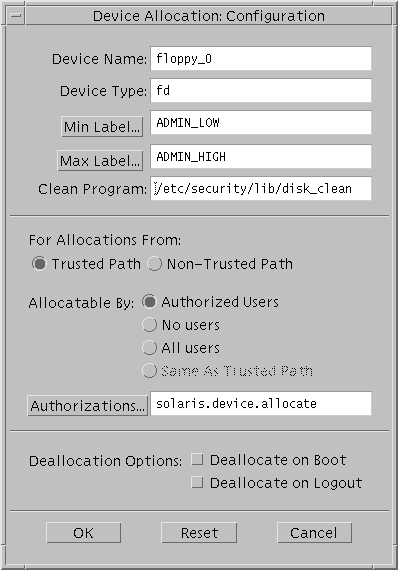
Device Name and Device Type - Displays the name and device type. These fields can be edited when creating a new device.
Min Label and Max Label - Click to set the label range on the device. The default label range is ADMIN_LOW to ADMIN_HIGH. See "Initial Device Configuration Decisions" for more
about setting a device's label range. These fields are valid for allocatable and nonallocatable devices.
Clean Program - Enter the path of a device_clean(1M) script for an allocatable device. If no device_clean script is specified at the time the device is created, the default is /bin/true. For how to write device clean scripts, see "Using Device-Clean Scripts".
For Allocations From: Trusted Path or Non-Trusted Path - Click (Trusted Path) to require users to use the Device Allocation Manager when allocating the device. Click remote (Non-Trusted Path) to enable users to use the allocate command in a script or when remotely logged in to allocate the device.
By default, the Allocate Devices authorizations enables allocation from the trusted path and from outside the trusted path. Sites that are concerned about the potential risk of remote device allocation can restrict it. See "Authorizing Device Allocation" for an example.
Allocatable By - Click one of Authorized Users, All Users, or No Users.
The No Users option is used most often for the framebuffer and printer, which do not have to be allocated to be used. But it is also used as shown in Table 12-3, to prevent an allocatable device from being accessed.
If no authorization is specified at the time the device is created, the default is All Users. If an authorization is specified, the default is Authorized Users.
Because the Add Allocatable action sets up a new device as allocatable by all users, the Security Administrator needs to click Allocatable By No Users when a device, such as the frame buffer and printers, should not be allocatable by anyone.
Authorizations - Click to change from the default authorization, solaris.device.allocate. See "To Add an Authorization to the Environment" for an example of creating and adding new device authorizations.
Deallocation Options - Click Deallocate on Boot or Deallocate on Logout. to specify that any devices that are allocated by a directly-logged-in user are deallocated either at logout or at system boot or both.
Note -
These options do not affect any devices allocated outside the trusted path (either during a remote login, or from a script or customer-written application) . Also, the boot command with the -r option can be used to force the deallocation of all devices at boot time.
Leaving devices allocated after logout could enable remote access to a device that otherwise can only be allocated locally. For example, a user could log in to one computer, allocate a device, then log out. The user then could log back in remotely to the first computer. During that remote session, the first computer's microphone could transmit the talk around the first computer.
Handling of Allocated Devices at Boot
At boot time, by default, allocated devices are reallocated and remounted. The administrator can override the default at boot-time by entering the device_clean(1M)boot command with the -r option. To change the default permanently, the administrator checks the deallocation options in the Device Allocation Manager for every device that the administrator wants to Deallocate on Boot or Deallocate on Logout.
Authorizing Device Allocation
The Allocate Device authorization enables users to allocate a device and to specify the label to associate with information imported from it, or exported to it.
However, site security policy may require that you create separate authorizations for devices that are allocated from the trusted path and devices that are allocated without the trusted path. The following table shows an example:
Table 12-2 Requiring Separate Authorizations for Local and Remote Device Use|
Device Name: cdrom_0 |
|
For Allocations From: Trusted Path Allocatable By: Authorized Users Authorizations: solaris.device.cdrom.local |
|
For Allocations From: Non-Trusted Path Allocatable By: Authorized Users Authorizations: solaris.device.cdrom.remot |
Alternatively, a site can allow a device to be allocatable only during local login sessions.
Table 12-3 Specifying Only Local Allocation of the Audio Device|
Device Name: audio |
|
For Allocations From: Trusted Path Allocatable By: Authorized Users Authorizations: solaris.device.allocate |
|
For Allocations From: Non-Trusted Path Allocatable By: No users |
For added security around device allocation, the Security Administrator role can create a new allocate authorization, such as Allocate Remote Device. See "Adding New Authorizations" and do "To Add an Authorization to the Environment".
Enforcing Device Security
The security administrator decides who can allocate devices. The security administrator should make sure that any user who is authorized to use devices is trained and can be trusted to do the following:
-
Properly label and handle any media containing exported sensitive information so that it does not become available to anyone who should not see it.
For example, if information at a label of
NEED TO KNOW ENGINEERINGis stored on a floppy disk, the person who exports the information must physically label the disk with theNEED TO KNOW ENGINEERINGlabel and store the disk where it is accessible only to members of the engineering group with a need to know. -
Ensure that labels are properly maintained on any information being imported (read) from media on these devices.
An authorized user should allocate the device at the label that matches the label of the information being imported. For example, if a user allocates a floppy drive at
PUBLIC, the user should only import information labeledPUBLIC.
The Security Administrator role also is responsible for enforcing proper compliance with the above-mentioned requirements.
Recovering From the Allocate Error State
As shown in Table 12-5, an allocatable device is in an error state if its ancillary file is owned by user bin and group bin with a device special file mode of 0100 and label of ADMIN_HIGH. One way that a device can be put into an allocate error state is by the device_clean(1M) scripts. A device-clean script puts a device into the allocate error state during deallocation until the user responds to prompts from the script and removable media is ejected. A role with the Reclaim or Revoke authorization can use the Device Allocaiton Manager to reclaim devices from the error state.
Using Device-Clean Scripts
A device-clean script is run any time a device is allocated or deallocated. The user who allocates the device usually deallocates it. If necessary, the Revoke button on the Device Allocation: Maintenance dialog box can be used by an authorized role to forcibly deallocate a device.
If your site adds additional allocatable devices to the system, the added devices may need new scripts. See the following descriptions of the existing device-clean scripts for ideas on how they work, and see also "Writing New Device-Clean Scripts".
Device-Clean Script for Tape Devices
The st_clean device-clean script is used for all tape devices.
The st_clean script uses the mt(1) command with the -rewoffl option to clean the device. When the script is run during system boot, it queries the device to see if it is on line and has any storage media in it. If necessary, the script prompts the operator to eject the storage media, and then it displays the appropriate label for the user to write on a physical label on the storage media.
Until deallocation completes, 1/4 inch tape devices are placed in the allocate error state, and 1/2 inch tape devices are taken off line. The allocate error state forces an authorized user to manually clean up the device before a user can allocate it again.
Device-Clean Scripts for Floppy Disks and CD-ROM
The disk_clean script is used for both floppy disk drives and CD-ROM devices. When the disk_clean script is run during boot time, any media found in a device is ejected. Whether it is run at boot time or when the device is deallocated, if the eject succeeds, the script prompts the user to affix to the media a physical label with the appropriate label. If the eject(1) command fails, the device is put in the allocate error state.
When a file system from either a floppy or CD is mounted as part of allocation, a File Manager pops up with the current directory set to the mount point. The Security Administrator role can prevent the automatic display of the File Manager by following the procedure in "To Prevent File Manager Display After Device Allocation". The mounting of file systems from floppy disks is handled differently from the mounting of file systems from CDs, as described in "Mounting an Allocated CD-ROM Device" and "Mounting an Allocated Floppy Device".
Device-Clean Script for Audio
The audiotool device is cleaned up using the audio_clean program.
This program performs an AUDIO_DRAIN ioctl to flush the device, and then an AUDIO_SETINFO ioctl to reset the device configuration to the default. In addition, this program retrieves the audio chip registers using the AUDIOGETREG ioctl, and any registers deviating from default are reset using AUDIOSETREG ioctl. Because the audio device does not contain any removable media, it does not require an external physical label, and therefore the label is not displayed by the audio_clean script.
Writing New Device-Clean Scripts
Devices that can be made allocatable include modems, terminals, and graphics tablets. The task of making any of these devices allocatable includes writing a new device-clean script. Device-clean scripts should also be created for any added tape devices, except for Xylogics or Archive tape drives, which can use the default device_clean(1M) script (/etc/security/lib/st_clean).
The default location for device-clean scripts is /etc/security/lib.
Device-clean scripts must return 0 for success and greater than 0 for failure.
Failure or inability to forcibly eject the medium must put the device in the allocate error state.
The deallocate(1) command passes four parameters to the device-clean scripts as shown here:
device_clean -[I|F|S] -[A|D] device_name label |
The option letters -I|-F|-S help the script determine its running mode. -I is needed during system boot only. All output must go to the system console. -F is for forced clean up and -S is for standard cleanup. These are interactive and assume that the user is there to respond to prompts. With the -F option, the script must attempt to complete the cleanup if one part of the cleanup fails.
[-[A]-[D]] indicates whether the clean script is called from allocate(1) or deallocate.
The device_name field is a string with the name of the device.
The label field is a hexadecimal representation of the label.
Mounting an Allocated CD-ROM Device
When a CD-ROM device is allocated, the user is queried whether or not to mount the CD-ROM.
-
If the CD contains a file system, answer yes to automatically mount the CD.
-
If the CD is an audio CD, answer no.
When the answer is no, if an audio action is specified in rmmount.conf, the audio action executes. By default, no audio action is specified.
To play an audio CD, the user must allocate both the audio and CD-ROM devices. The user can optionally manually invoke an audioplayer application after allocating the device. See "To Play an Audio CD" for how the security administrator can set up an audio action for users.
Mounting an Allocated Floppy Device
File systems on floppy disks are not automatically mounted at allocation because the user may wish to create a new file system over an existing file system already on the floppy. Programs such as fdformat(1) or newfs(1M) can create a new file system only if the file system on the floppy device is not mounted. Therefore, before mounting an existing file system on a floppy, the disk_clean script asks the user whether or not to mount the file system.
If a floppy disk is not formatted, the disk_clean script asks the user whether or not to format the floppy.
After the file system on a floppy is mounted as part of device allocation, a File Manager pops up with the current directory set to the mount point.
Device-related Commands, Databases, and Files
See the man pages for the following commands and databases:
Table 12-4 Device-related Commands and Databases|
Command or Database Name |
Description |
|---|---|
|
Device allocation command line interface |
|
|
Add a device to device_allocate(4), device_maps(4), and create an ancillary file in /etc/security/dev |
|
|
Device deallocation command line interface |
|
|
Device cleaning programs |
|
|
Report on specified device's entry in the device_maps file. |
|
|
List devices specified in the device_maps file. |
|
|
Remove a device from device_allocate, device_maps and delete its ancillary file from /etc/security/dev. |
|
|
Database for managing allocatable and some nonallocatable devices. |
|
|
Database for device entries that are required for devices to be allocatable or to have their labels restricted. |
Ancillary Files for Allocatable Devices
Each allocatable device has an ancillary file, which is a zero-length file in /etc/security/dev. The ancillary file is also referred to as a DAC file because the file must not only exist but its DAC permissions, owner, and group depend on its state.
The following table shows the DAC permissions, owner, and group for each of the possible states:
Table 12-5 Required Ancillary File Characteristics for Devices|
Device State |
DAC permissions (mode) |
Owner |
Group |
Label |
|---|---|---|---|---|
|
Allocatable |
0000 |
bin |
bin |
|
|
Allocated |
0600 |
user |
user's group |
user's process's label |
|
Error State |
0100 |
bin |
bin |
|
Managing Devices (Tasks)
To Save Files With Security Attributes to a Tape
This procedure can be done by any user or role that has the tar command in a profile.
-
Use the Device Allocation Manager to allocate a tape device.
The example allocates a device named mag_tape_0. See the Trusted Solaris User's Guide for more about how to allocate devices and specify the label at which the device is allocated.
-
Make sure the tape is physically labeled with the label of the current process, and insert the tape into the tape device when prompted.
The window in the example is titled Device Allocation for mag_tape0 window.
st_clean: Insert tape into mag_tape0 st_clean: Make sure the tape is labeled CONFIDENTIAL Press RETURN to quit window...
-
Enter the tar command with the -T security option.
trusted% tar cvT tartest a tartest/(A) 1K a tartest/ 0K a tartest/file1(A) 1K a tartest/file1 0K a tartest/mld1/(A) 1K a tartest/mld1/ 0K a tartest/mld1/(A) 1K a tartest/mld1/ 0K a tartest/mld1/file50(A) 1K a tartest/mld1/file50 1K . . .
-
Use the
Device Allocation Managerto deallocate the device.Eject the tape from the device when prompted.
Please eject the tape in mag_tape_0
-
Make sure to protect the exported information at the security level on the media's physical label.
To Set or Modify Device Policy for a Device
-
Assume the Security Administrator role and go to an
ADMIN_LOWworkspace. -
Determine the driver_name and minor_name and the device special file names for the device.
-
For an existing device, find the device name and minor name by doing a long listing of the device.
# ls -l /dev/dsk/c0t6d0s2 lrwxrwxrwx 1 root root 51 Feb 29 1998 /dev/dsk/c0t6d0s2 -> ../../devices/sbus@1f,0/SUNW,fas@e,8800000/sd@6,0:c
In the final element of the pathname, the string before the @ character is the driver name (sd in the example above) and the string after the colon is the minor name, (c in the example above).
-
For a new device, do the following.
-
Consult the hardware documentation for the device to obtain the device name and minor name and a list of all the physical device names.
See also, Writing Device Drivers.
-
Create a new entry for the device in the /etc/security/device_maps file.
The name used for the device is arbitrary. In the third field, list all the physical device names for the device.The example shows all the physical and logical device names for the cdrom_0 device.
cdrom_0:\ sr:\ /dev/sr0 /dev/rsr0 /dev/dsk/c0t6d0s0 /dev/dsk/c0t6d0s1 /dev/dsk/c0t6d0s2 /dev/dsk/c0t6d0s3 /dev/dsk/c0t6d0s4 /dev/dsk/c0t6d0s5 /dev/dsk/c0t6d0s6 /dev/dsk/c0t6d0s7 /dev/rdsk/c0t6d0s0 /dev/rdsk/c0t6d0s1 /dev/rdsk/c0t6d0s2 /dev/rdsk/c0t6d0s3 /dev/rdsk/c0t6d0s4 /dev/rdsk/c0t6d0s5 /dev/rdsk/c0t6d0s6 /dev/rdsk/c0t6d0s7:\
-
-
Use the Admin Editor action to open the /etc/security/tsol/device_policy file for editing.
-
When the default policy for devices is not consistent with your site's security policy, create a specific entry or a wildcard entry for a new device or modify an existing entry for an already-specified device.
The default device policy is as shown in Table 12-1. For how to specify alternate policy settings, see the device_policy(4) man page.
-
Write the file and exit the editor.
To Revoke or Reclaim a Device
-
Assume the Security Administrator role and go to an
ADMIN_LOWworkspace. -
Click the Device Allocation icon on the Tools subpanel.
-
Click the Device Administration button.
-
Check the status of a device by highlighting the name of the device and looking at the State: field.
-
If the State field is Allocate Error State, click the Reclaim button to correct the error state.
-
If a device is State is Allocated, do one of the following:
-
Contact the Owner to deallocate the device.
-
If the State field is Allocated, click the Revoke button to force deallocation of the device.
-
-
Click OK.
To Play an Audio CD
The following procedure automatically launches a CD player. The user must have allocated both the audio and CD-ROM devices.
-
Assume the Security Administrator role and go to an
ADMIN_LOWworkspace. -
Open the Admin Editor from the System_Admin folder in the Application Manager to edit the /etc/rmmount.conf file.
-
Add your site's CD player program to the cdrom action in the file.
For example, at a site where workman CD program is installed, the following entry in rmmount.conf automatically executes /usr/local/bin/workman and launches the workman action.
action cdrom action_workman.so /usr/local/bin/workman
To Add a Device
Follow the instructions in the Installing Device Drivers guide for the Solaris environment, if needed, then do the following Trusted Solaris-specific steps.
-
If adding a new allocatable device, the System Administrator should create a device_clean script, if needed.
A tape drive can use the default st_clean script as is, or the script can be modified to suit the site's security policy. Otherwise, a new device_clean script is needed. See "To Change or Add a Device Clean Script" for the procedure.
-
Assume the Security Administrator role and go to an
ADMIN_LOWworkspace. -
Click the Device Allocation icon on the Tools subpanel.
-
Click Device Administration, then click New....
-
Enter the Device Name and Device Type.
-
In the Device Map field, enter the pathnames for all the device special files associated with the device. Separate the pathnames with spaces.
-
(Optional) Set the label range on the device to be other than
ADMIN_LOWtoADMIN_HIGH, by clicking the Min Label... and button and Max Label... buttons. -
For Allocations From Trusted Path, choose an option from the Allocatable By: list:
Authorized Users No Users All Users Same as Trusted Path
Note -When configuring a printer, frame buffer, or other device that should not be allocatable, make sure to select No Users.
Same As Trusted Path applies only when Non-Trusted Path is selected.
-
When you choose Allocatable by Authorized Users, the Authorizations field becomes active, and the
solaris.device.allocationauthorization name displays.If you have created site-specific device authorizations, enter them. See "To Add Site-Specific Authorizations to a Device" for the procedure.
-
Click Non-Trusted Path and click whether it should be treated the same as the Trusted Path.
-
If you choose Allocatable by Authorized Users, click the Authorizations... button to require site-specific authorizations to allocate the device from outside the trusted path.
If you have created site-specific device authorizations, enter them. See "To Add Site-Specific Authorizations to a Device" for the procedure.
-
Specify the Deallocation Options for the device when it is allocated locally through the trusted path.
-
Click OK to save your changes.
To Add Site-Specific Authorizations to a Device
-
Assume the Security Administrator role and go to an
ADMIN_LOWworkspace or log in as a user who can assume a role with the Configure Device Attributes authorization. -
Click the Device Allocation icon on the Tools subpanel.
-
Click Device Administration, select the device to allocate, and click Configure....
-
For Allocations From Trusted Path, choose Authorized Users.
When you choose Allocatable by Authorized Users, the Authorizations field becomes active, and the
solaris.device.allocationauthorization name displays. -
If you have created site-specific device authorizations, click the Authorizations... button, and select the authorizations that the user must have to allocate the device.
-
Click Non-Trusted Path and click whether it should be treated the same as the Trusted Path.
Same As Trusted Path applies only when Non-Trusted Path is selected.
-
If you choose Allocatable by Authorized Users, click the Authorizations... button to add site-specific authorizations to allocate the device from outside the trusted path.
-
Click OK to save your changes.
To Configure a Serial Line for Logins
-
Assume the Security Administrator role and go to an
ADMIN_LOWworkspace. -
Bring up a SMC toolbox with the Files scope.
Figure 12-2 Solaris Management Console Tools
-
Select Devices and Hardware, provide a password when prompted, and then double-click Serial Ports.
Follow the online help for how to configure the serial port.
-
Click the Device Allocation icon on the Tools subpanel on the Front Panel.
The device's default label range is
ADMIN_LOWtoADMIN_HIGH. -
To restrict the label range, click the Device Administration button, and then click New.
-
Click OK to save your changes.
To Assign Device Authorizations to an Account
-
Assume the Security Administrator role, launch the Solaris Management Console in the appropriate scope, and click Users. Provide a password when prompted.
-
Double-click the User Accounts tool, and click the Rights tab.
-
Assign to the user a rights profile that contains the Allocate Device authorization.
If the defaults have not been modified, assign the rights profile Convenient Authorizations or All Authorizations.
-
To assign a rights profile to a role account, double-click the Administrative Roles tool, and double-click the role to be modified.
-
If the role should be able to allocate devices, choose a profile from the following table.
Table 12-6 Default Profiles that Include Device Allocation AuthorizationAuthorization Name
Default Profiles
Allocate Device
All Authorizations
Convenient Authorizations
Device Management
Media Backup
Media Restore
Object Label Management
Software Installation
SSP Installation
-
If the role should be able to revoke or reclaim devices, choose one of the following profiles.
Table 12-7 Default Profiles for Administering DevicesName
Default Profile
Default Role
Revoke or Reclaim Devices
Device Management
secadmin
All Authorizations
Not assigned
-
If the role should be able to create or configure devices, choose one of the following profiles.
Table 12-8 Default Profiles for Creating DevicesName
Default Profile
Default Role
Configure Device Attributes
Device Security
secadmin
Host Alternate Pathing
secadmin
All Authorizations
Not assigned
If none of the default profiles are appropriate for the account being reconfigured, the Security Administrator role can create a new profile that includes the device allocation authorization(s), either by themselves or along with any other commands needed by the profile's users to perform the desired work (such as the allocate, deallocate, and tar commands). Creating a new profile is described in "Adding or Modifying a Rights Profile".
-
To Prevent File Manager Display After Device Allocation
-
Assume the Security Administrator role and go to an
ADMIN_LOWworkspace. -
Use the Admin Editor action to open the file /etc/rmmount.conf for editing.
-
Comment out the action for notifying the File Manager for the CD-ROM or floppy or both.
The example shows the action_filemgr.so commented out for both the cdrom and floppy devices.
# action cdrom action_filemgr.so # action floppy action_filemgr.so
To Change or Add a Device Clean Script
For background, see "Using Device-Clean Scripts".
-
Assume the System Administrator role and go to an
ADMIN_LOWworkspace. -
Use the Admin Editor to open a text file.
-
Write the script so that all usable data is purged from the physical device and that it returns 0 for success.
-
For devices with removable media, have the script attempt to eject the media if the user does not do so, and put the device into the allocate error state if the media is not ejected.
-
Copy the
ADMIN_LOWscript into /etc/security/lib. -
Open the Device Allocation Manager from the Tools subpanel, and click the Device Administration button.
-
Highlight the name of the affected device and click the Configure... button.
-
Enter the name of the script in the Clean Program field.
-
Click OK until the Device Allocation Manager closes.
- © 2010, Oracle Corporation and/or its affiliates
