| C H A P T E R 11 |
|
Using Simple Network Management Protocol (SNMP) |
This chapter describes how to use SNMP. It includes the following sections:
The Sun server supports the Simple Network Management Protocol (SNMP) interface, versions 1, 2c, and 3. SNMP is an open technology that enables the management of networks and devices, or nodes, connected to the network. SNMP messages are sent over IP using the User Datagram Protocol (UDP). Any management application that supports SNMP can manage your server.
Utilizing SNMP requires two components, a network management station and a managed node (in this case, the ILOM). Network management stations host management applications, which monitor and control managed nodes.
Managed nodes are any number of devices, including servers, routers, and hubs, which host SNMP management agents responsible for carrying out the requests from management stations. The management station monitors nodes by polling management agents for the appropriate information using queries. Managed nodes can also provide unsolicited status information to a management station in the form of a trap. SNMP is the protocol used to communicate management information between the management stations and agents.
The SNMP agent is preinstalled and runs on the ILOM, so all SNMP management of the server should occur through the ILOM. To utilize this feature, your operating system must have an SNMP client application. See your operating system vendor for more information.
The SNMP agent on your ILOM provides the following capabilities: inventory management, and sensor and system state monitoring.
The base component of an SNMP solution is the Management Information Base (MIB). A MIB is a text file that describes a managed node's available information and where it is stored. When a management station requests information from a managed node, the agent receives the request and retrieves the appropriate information from the MIBs. The Sun server supports the following SNMP classes of Management Information Base (MIB) files. Download and install the product-specific MIB files from your Resource CD or Tools and Drivers CD for your platform.
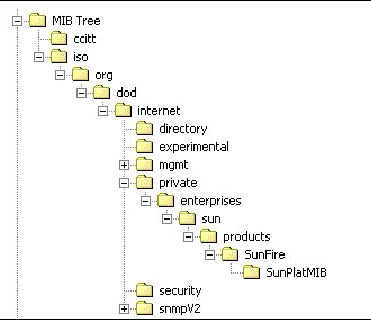
Use the MIBs to integrate the management and monitoring of the server into SNMP management consoles. The MIB branch is a private enterprise MIB, located at MIB object iso(1).org (3). dod (6). internet (1). private (4). enterprises (1). sun (42). products (2). FIGURE 11-1. The standard SNMP port (161) is used by the SNMP agent on the ILOM.
SNMP is a protocol, not an operating system so you need some type of application to use SNMP messages. Your SNMP management software may provide this functionality, or you can use an open source tool like net-SNMP, which is available at
http://net-snmp.sourceforge.net/
Both management stations and agents use SNMP messages to communicate. Management stations can send and receive information. Agents can respond to requests and send unsolicited messages in the form of a trap. There are five functions that management stations and agent use:
By default, port 161 is used for SNMP messages and port 162 is used to listen for SNMP traps.
The ILOM has a preinstalled SNMP agent that supports trap delivery to an SNMP management application.
To use this feature, you must 1) integrate the platform-specific MIBs into your SNMP environment, 2) tell your management station about your server, then 3) configure the specific traps.
The Sun server MIB tree appears in FIGURE 11-1.
Use a third party SNMP management application to load the SUN-PLATFORM-MIB.
Add your Sun server as a managed node using your SNMP management application. See your SNMP management application documentation for further details.
To configure a trap in your ILOM, see Section 3.8, Managing ILOM Alerts, or Section 5.6, Viewing Alert Destinations and Configuring Alerts.
You can add, delete, or configure SNMP user accounts from the CLI. By default, SNMP v3 is enabled, and SNMP v1 and v2c are disabled.
To do this on the WebGUI, see Section 5.8.1, Configuring SNMP Settings.
To add an SNMP v3 read-only user account, type the following command:
create /SP/services/snmp/users/username authenticationpassword=password
To add an SNMP v1/v2c user account, type this command:
create /SP/services/snmp/communities/communityname
To delete an SNMP v3 user account, type this command :
delete /SP/services/snmp/users/username
To delete an SNMP v1/v2c user account, type this command:
delete /SP/services/snmp/communities/communityname
To configure SNMP user accounts, use the set command.
set target [propertyname=value]
These targets, properties, and values are valid for SNMP user accounts.
|
* If the privacyprotocol property has a value other than none, then a privacypassword must be set. |
|||
When changing the parameters of SNMP users, you must set values for all of the properties, even if you are not changing all of the values. For example, to change user al's privacyprotocol to DES you must type:
-> set /SP/services/snmp/users/al privacyprotocol=DES privacypassword=password authenticationprotocol=SHA authenticationpassword=password
Your changes would be invalid if you only typed:
-> set /SP/services/snmp/users/al privacyprotocol=DES
|
Note - You can change SNMP user permissions without resetting the privacy and authentication properties. |
Copyright © 2006, Sun Microsystems, Inc. All Rights Reserved.