| C H A P T E R 12 |
|
Lightweight Directory Access Protocol (LDAP) |
The ILOM supports LDAP authentication for users, based on the OpenLDAP software. LDAP is a general-purpose directory service. A directory service is a centralized database for distributed applications, designed to manage the entries in a directory. Thus, multiple applications can share a single user database. For more detailed information on LDAP, go to http://www.openldap.org/.
LDAP is based on a client-server model. LDAP provides the directory, and the clients use the directory service to access entries. The data stored in a directory can be distributed among several LDAP servers.
This chapter includes the following sections:
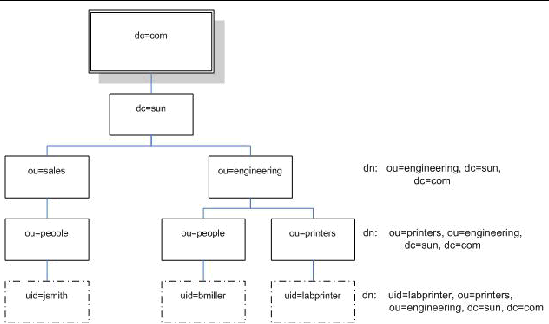
Data in LDAP is organized hierarchically, starting at a root and branching down into individual entries. Entries at the top level of the hierarchy represent larger organizations, and under the larger organizations are entries for smaller organizations. At the bottom of the hierarchy are entries for individual people or resources.
Each entry is uniquely identified by a distinguished name (dn). A distinguished name consists of a name that uniquely identifies the entry at that hierarchical level and a path that traces the entry back to the root of the tree.
For example, the distinguished name for jsmith is:
dn: uid=jsmith, ou=people, dc=sun.com
Here, uid represents the user ID of the entry, ou represents the organizational unit in which the entry belongs, and dc represents the larger organization in which the entry belongs.
FIGURE 12-1 shows how distinguished names are used to identify entries uniquely in the directory hierarchy.
FIGURE 12-1 LDAP Distinguished Names
In the LDAP client-server model, LDAP servers make information about people, organizations, and resources accessible to LDAP clients. Clients make changes to the LDAP database using a client utility, usually bundled with the LDAP server. When a change is made to the LDAP database, all client applications see the change immediately, so there is no need to update each distributed application.
An LDAP client can perform the following operations, among others:
For example, to update an entry in the directory, an LDAP client submits the distinguished name of the entry with updated attribute information to the LDAP server. The LDAP server uses the distinguished name to find the entry and performs a modify operation to update the entry in the directory. The updated information is immediately available to all the distributed applications using that LDAP server.
To perform any of these LDAP operations, an LDAP client needs to establish a connection with an LDAP server. LDAP specifies the use of TCP/IP port number 389, although servers may run on other ports.
Your Sun server can be a client of an LDAP server. To use LDAP authentication, you need to create a user on your LDAP server that your Sun server can authenticate, or bind to, so that the client has permission to search the proper directory on the LDAP server.
To use LDAP, you must configure your LDAP server, according to your LDAP server documentation, and your ILOM, using either the CLI or the WebGUI.
This procedure requires detailed knowledge of your LDAP server configuration. Before you begin, gather basic network information about your LDAP server, including its IP address.
|
Note - This task is similar to configuring LDAP as a name service for Linux or the Solaris operating system. |
1. Ensure that all users authenticating to the CMM ILOM have passwords stored in crypt format or the GNU extension to crypt, commonly referred to as MD5 crypt.
userPassword: {CRYPT}ajCa2He4PJhNo
userPassword: {CRYPT}$1$pzKng1$du1Bf0NWBjh9t3FbUgf46.
The ILOM supports LDAP authentication only, for passwords stored in these two variations of the crypt format.
2. Add object classes posixAccount and shadowAccount, and populate the required property values for this schema (RFC 2307).
3. Provide the ILOM access to user accounts on your LDAP server.
Either enable your LDAP server to accept anonymous binds, or create a proxy user on your LDAP server that has read-only access to all user accounts that will authenticate through the ILOM.
See your LDAP server documentation for more details.
After the LDAP server is configured, you must configure the ILOM, using either the CLI or the WebGUI.
1. Enter the proxy user name and password. From the command line, type:
set /SP/clients/ldap binddn=cn=proxyuser, ou=sales, dc=sun, dc=com bindpw=password
2. Enter the IP address of the LDAP server. From the command line, type:
set /SP/clients/ldap ipaddress=ldapipaddress
3. Assign the port used to communicate with the LDAP server; the default port is 389. From the command line, type:
set /SP/clients/ldap port=ldapport
Enter the distinguished name of the branch of your LDAP tree that contains users and groups. From the command line, type:
set /SP/clients/ldap searchbase="ou=people, ou=sales, dc=sun, dc=com"
This is the location in your LDAP tree that you want to search for user authentication.
4. Set the state of the LDAP service to enabled. From the command line, type:
set /SP/clients/ldap state=enabled
5. To verify that LDAP authentication works, log in to the ILOM using an LDAP user name and password.
|
Note - The ILOM searches local users before it searches LDAP users. If an LDAP user name exists as a local user, the ILOM uses the local account for authentication. |
1. Log in to the ILOM as administrator or operator.
2. Select User Management => LDAP Settings.
The LDAP Settings page appears.
FIGURE 12-2 LDAP Settings Page
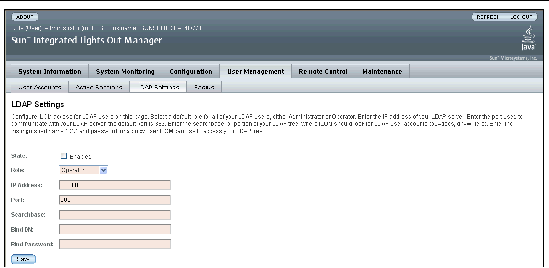
3. Enter the following values:
5. To verify that LDAP authentication works, log in to the ILOM using an LDAP user name and password.
|
Note - The ILOM searches local users before LDAP users. If an LDAP user name exists as a local user, the ILOM uses the local account for authentication. |
Copyright © 2007, Sun Microsystems, Inc. All Rights Reserved.