How Security Works
The following sections describe how the WSIT security technologies, security policy, trust, and secure conversation work.
How Security Policy Works
The WSIT Web Service Security Policy implementation builds on the features provided by the Web Service Policy implementation in WSIT. It enables users to use XML elements to specify the security requirements of a web service endpoint, that is, how messages are secured on the communication path between the client and the web service. The web service endpoint specifies the security requirements to the client as assertions (see Figure 2–9).
Figure 2–9 Security Policy Exchange
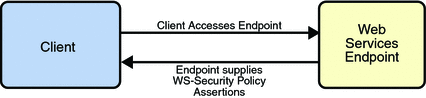
The security policy model uses the policy specified in the WSDL file for associating policy assertions with web service communication. As a result, whenever possible, the security policy assertions do not use parameters or attributes. This enables first-level, QName-based assertion matching to be done at the framework level without security domain-specific knowledge. The first-level matching provides a narrowed set of policy alternatives that are shared by the client and web service endpoint when they attempt to establish a secure communication path.
Note –
A QName is a qualified name, as specified by the XML Schema Part2: Datatypes specification, Namespaces in XML, and Namespaces in XML Errata. A qualified name is made up of a namespace URI, a local part, and a prefix.
The benefit of representing security requirements as assertions is that QName matching is sufficient to find common security alternatives and that many aspects of security can be factored out and reused. For example, it may be common that the security mechanism is constant for a web service endpoint, but that the message parts that are protected, or secured, may vary by message action.
The following types of assertions are supported:
-
Protection assertions: Define the scope of security protection. These assertions identify the message parts that are to be protected and how they are to be protected, that is, whether data integrity and confidentiality mechanisms are to be used.
-
Conditional assertions: Define general aspects or preconditions of the security. These assertions define the relationships within and the characteristics of the environment in which security is being applied, such as the tokens that can be used, which tokens are for integrity or confidentiality protection, applicable algorithms to use, and so on.
-
Security binding assertions: Define the security mechanism that is used to provide security. These assertions are a logical grouping that defines how the conditional assertions are used to protect the indicated message parts. For example, the assertions might specify that an asymmetric token is to be used with a digital signature to provide integrity protection, and that parts are to be encrypted with a symmetric key, which is then encrypted using the public key of the recipient. In their simplest form, the security binding assertions restrict what can be placed in the wsse:Security header and the associated processing rules.
-
Supporting token assertions: Define the token types and usage patterns that can be used to secure individual operations and/or parts of messages.
-
Web Services Security and Trust assertions: Define the token referencing and trust options that can be used.
How Trust Works
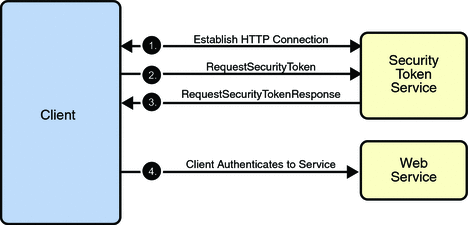
Figure 2–10 shows how the Web Services Trust technology establishes trust.
Figure 2–10 Trust and Secure Conversation
-
The client establishes an HTTPS connection with the Secure Token Service using one of the following methods:
-
Username Authentication and Transport Security: The client authenticates to the Security Token Service using a username token. The Security Token Service uses a certificate to authenticate to the Client. Transport security is used for message protection.
-
Mutual Authentication: Both the client-side and server-side use X509 certificates to authenticate to each other. The client request is signed using Client’s X509 certificate, then signed using ephemeral key. The web service signs the response using keys derived from the client’s key.
-
-
The client sends a RequestSecurityToken message to the Security Token Service.
-
The Security Token Service sends a Security Assertion Markup Language (SAML) token to the Client.
-
The client uses the SAML token to authenticate itself to the web service and trust is established.
To establish trust between a client, a Security Token Service, and a web service:
All communication uses SOAP messages.
How Secure Conversation Works
Figure 2–11 shows how the Web Services Secure Conversation technology establishes a secure conversation when the Trust technology is not used.
Figure 2–11 Secure Conversation

-
The client sends a X509 Certificate to authenticate itself to the web service.
-
The web service sends a X509 Certificate to authenticate itself to the client.
To establish a secure conversation between a Client and a web service:
All communication uses SOAP messages.
- © 2010, Oracle Corporation and/or its affiliates
