The Big Picture
Today’s businesses require increased flexibility and capabilities from its IT services. Historically, managing access to business information and systems required direct interaction with a limited number of accounts. Today, managing access means handling not only increased numbers of internal customers, but also partners and customers beyond your enterprise.
The overhead created by this increased need for access can be substantial. As an administrator, you must effectively and securely enable people– both inside and outside your enterprise– to do their jobs. And after you provide initial access, you face continuing detailed challenges, such as forgotten passwords, and changed roles and business relationships.
Additionally, businesses today face strict requirements governing the security and integrity of critical business information. In an environment dictated by compliance-related legislation– such as the Sarbanes-Oxley (SOX) Act, the Health Insurance Portability and Accountability Act (HIPAA), and the Gramm-Leach-Bliley (GLB) Act– the overhead created by monitoring and reporting activities is substantial and costly. You must be able to respond quickly to changes in access control, as well as satisfy the data-gathering and reporting requirements that help keep your business secure.
Identity Manager was developed specifically to help you manage these administrative challenges in a dynamic environment. By using Identity Manager to distribute access management overhead and address the burden of compliance, you facilitate a solution to your primary challenges: How do I define access? And once defined, how do I maintain flexibility and control?
A secure, yet flexible design lets you set up Identity Manager to accommodate the structure of your enterprise and answer these challenges. By mapping Identity Manager objects to the entities that you manage– users and resources– you significantly increase the efficiency of your operations.
In a service provider environment, Identity Manager extends these capabilities to managing extranet users as well.
Goals of the Identity Manager System
The Identity Manager solution enables you to accomplish the following goals:
-
Manage account access to a large variety of systems and resources.
-
Securely manage dynamic account information for each user’s array of accounts.
-
Set up delegated rights to create and manage user account data.
-
Handle large numbers of enterprise resources, as well as an increasingly large number of extranet customers and partners.
-
Securely authorize user access to enterprise information systems. With Identity Manager, you have fully integrated functionality to grant, manage, and revoke access privileges across internal and external organizations.
-
Keep data synchronized by not keeping data. The Identity Manager solution supports two key principles that superior systems management tools should observe:
-
The product should have minimal impact on the system it is managing.
-
The product should not introduce more complexity to your enterprise by adding another resource to manage.
Define audit policies to manage compliance with user access privileges and manage violations through automated remediation actions and email alerts.
-
-
Conduct periodic access reviews and define attestation review and approval procedures that automate the process of certifying user privileges.
-
Monitor key information and audit and review statistics through the dashboard.
Defining User Access to Resources
Users in your extended enterprise can be anyone with a relationship to your company, including employees, customers, partners, suppliers, or acquisitions. In the Identity Manager system, users are represented by user accounts.
Depending on their relationships with your business and other entities, users need access to different things, such as computer systems, data stored in databases, or specific computer applications. In Identity Manager terms, these things are resources.
Because users often have one or more identities on each of the resources they access, Identity Manager creates a single, virtual identity that maps to disparate resources. This allows you to manage users as a single entity. See Figure 1–1.
Figure 1–1 Identity Manager User Account Resource Relationship
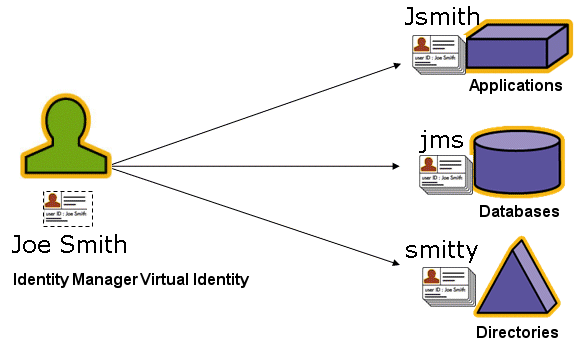
To effectively manage large numbers of users, you need logical ways to group them. In most companies, users are grouped into functional departments or geographical divisions. Each of these departments typically requires access to different resources. In Identity Manager terms, this type of group is called an organization.
Another way to group users is by similar characteristics, such as company relationships or job functions. Identity Manager recognizes these groupings as roles.
Within the Identity Manager system, you assign roles to user accounts to facilitate efficient enabling and disabling of access to resources. Assigning accounts to organizations enables efficient delegation of administrative responsibilities.
Identity Manager users are also directly or indirectly managed through the application of policies, which set up rules and password and user authentication options.
Understanding User Types
Identity Manager provides two user types: Identity Manager Users and Service Provider Users, if you configure your Identity Manager system for a service provider implementation. These types enable you to distinguish users that might have different provisioning requirements based on their relationship with your company, for example extranet users compared with intranet users.
A typical scenario for a service provider implementation is a service provider company with internal users and external users (customers) that it wants to manage with Identity Manager. For information about configuring a service provider implementation, see Sun Identity Manager Service Provider 8.1 Deployment.
You specify the Identity Manager user type when you configure a user account. For more information about service provider users, see Chapter 17, Service Provider Administration
Delegating Administration
To successfully distribute responsibility for user identity management, you need the right balance of flexibility and control. By granting select Identity Manager users administrator privileges and delegating administrative tasks, you reduce your overhead and increase efficiency by placing responsibility for identity management with those who know user needs best, such as a hiring manager. Users with these extended privileges are called Identity Manager administrators.
Delegation only works, however, within a secure model. To maintain an appropriate level of control, Identity Manager lets you assign different levels of capabilities to administrators. Capabilities authorize varying levels of access and actions within the system.
The Identity Manager workflow model also includes a method to ensure that certain actions require approval. Using workflow, Identity Manager administrators retain control over tasks and can track their progress. For detailed information about workflow, see Chapter 2, Workflow, in Sun Identity Manager Deployment Reference.
- © 2010, Oracle Corporation and/or its affiliates
