Chapter 18 Trusted Extensions Auditing (Overview)
This chapter describes the additions to auditing that Solaris Trusted Extensions provides.
Trusted Extensions and Auditing
On a system that is configured with Trusted Extensions software, auditing is configured and is administered similarly to auditing on a Solaris system. However, the following are some differences.
-
Trusted Extensions software adds audit classes, audit events, audit tokens, and audit policy options to the system.
-
By default, auditing is enabled in Trusted Extensions software.
-
Solaris per-zone auditing is not supported. In Trusted Extensions, all zones are audited identically.
-
Trusted Extensions provides administrative tools to administer the users' audit characteristics and to edit audit files.
-
Two roles, System Administrator and Security Administrator, are used to configure and administer auditing in Trusted Extensions.
The security administrator plans what to audit and any site-specific, event-to-class mappings. As in the Solaris OS, the system administrator plans disk space requirements for the audit files, creates an audit administration server, and installs audit configuration files.
Audit Management by Role in Trusted Extensions
Auditing in Trusted Extensions requires the same planning as in the Solaris OS. For details about planning, see Chapter 29, Planning for Solaris Auditing, in System Administration Guide: Security Services.
Role Setup for Audit Administration
In Trusted Extensions, auditing is the responsibility of two roles. The System Administrator role sets up the disks and the network of audit storage. The Security Administrator role decides what is to be audited, and specifies the information in the audit configuration files. As in the Solaris OS, you create the roles in software. The rights profiles for these two roles are provided. The initial setup team created the Security Administrator role during initial configuration. For details, see Create the Security Administrator Role in Trusted Extensions in Oracle Solaris Trusted Extensions Configuration Guide.
Note –
A system only records the security-relevant events that the audit configuration files configure the system to record (that is, by preselection). Therefore, any subsequent audit review can only consider the events that have been recorded. As a result of misconfiguration, attempts to breach the security of the system can go undetected, or the administrator is unable to detect the user who is responsible for an attempted breach of security. Administrators must regularly analyze audit trails to check for breaches of security.
Audit Tasks in Trusted Extensions
The procedures to configure and manage auditing in Trusted Extensions differ slightly from Solaris procedures:
-
Audit configuration is performed in the global zone by one of two administrative roles. Then, the system administrator copies specific customized audit files from the global zone to every labeled zone. By following this procedure, user actions are audited identically in the global zone and in labeled zones.
For details, see Audit Tasks of the Security Administrator and Audit Tasks of the System Administrator
-
Trusted Extensions administrators use a trusted editor to edit audit configuration files. In Trusted CDE, Trusted Extensions administrators use CDE actions to invoke the trusted editor. For the list of actions, see Trusted CDE Actions.
-
Trusted Extensions administrators use the Solaris Management Console to configure specific users. User-specific audit characteristics can be specified in this tool. Specifying user characteristics is only required when the user's audit characteristics differ from the audit characteristics of the systems on which the user works. For an introduction to the tool, see Solaris Management Console Tools.
Audit Tasks of the Security Administrator
The following tasks are security-relevant, and are therefore the responsibility of the security administrator. Follow the Solaris instructions, but use the Trusted Extensions administrative tools.
|
Task |
For Solaris Instructions |
Trusted Extensions Instructions |
|---|---|---|
|
Configure audit files. |
Configuring Audit Files (Task Map) in System Administration Guide: Security Services |
Use the trusted editor. For details, see How to Edit Administrative Files in Trusted Extensions. |
|
(Optional) Change default audit policy. |
How to Configure Audit Policy in System Administration Guide: Security Services |
Use the trusted editor. |
|
Disable and re-enable auditing. |
How to Disable the Audit Service in System Administration Guide: Security Services |
Auditing is enabled by default. |
|
Manage auditing. |
Solaris Auditing (Task Map) in System Administration Guide: Security Services |
Use the trusted editor. Ignore per-zone audit tasks. |
Audit Tasks of the System Administrator
The following tasks are the responsibility of the system administrator. Follow the Solaris instructions, but use the Trusted Extensions administrative tools.
|
Task |
For Solaris Instructions |
Trusted Extensions Instructions |
|---|---|---|
|
Create audit partitions and an audit administration server, export audit partitions, and mount audit partitions. Create an audit_warn alias. |
Configuring and Enabling the Audit Service (Tasks) in System Administration Guide: Security Services |
Perform all administration in the global zone. Use the trusted editor. |
|
Copy or loopback mount customized audit files to labeled zones. |
Configuring the Audit Service in Zones (Tasks) in System Administration Guide: Security Services |
Copy the files to the first labeled zone, then copy the zone. Or, loopback mount or copy the files to every labeled zone after the zones are created. |
|
(Optional) Distribute audit configuration files. |
No instructions | |
|
Manage auditing. |
Solaris Auditing (Task Map) in System Administration Guide: Security Services |
Ignore per-zone audit tasks. |
|
How to Select Audit Events From the Audit Trail in System Administration Guide: Security Services |
To select records by label, use the auditreduce command with the -l option. |
Trusted Extensions Audit Reference
Trusted Extensions software adds audit classes, audit events, audit tokens, and audit policy options to the Solaris OS. Several auditing commands are extended to handle labels. Trusted Extensions audit records include a label, as shown in the following figure.
Figure 18–1 Typical Audit Record on a Labeled System

Trusted Extensions Audit Classes
The audit classes that Trusted Extensions software adds to the Solaris OS are listed alphabetically in the following table. The classes are listed in the /etc/security/audit_class file. For more information about audit classes, see the audit_class(4) man page.
Table 18–1 X Server Audit Classes|
Short Name |
Long Name |
Audit Mask |
|---|---|---|
|
xc |
X - Object create/destroy | |
|
xp |
X - Privileged/administrative operations | |
|
xs |
X - Operations that always silently fail, if bad | |
|
xx |
X - All X events in the xl, xc, xp, and xs classes (metaclass) |
The X server audit events are mapped to these classes according to the following criteria:
-
xc – This class audits server objects for creation or for destruction. For example, this class audits CreateWindow().
-
xp – This class audits for use of privilege. Privilege use can be successful or unsuccessful. For example, ChangeWindowAttributes() is audited when a client attempts to change the attributes of another client's window. This class also includes administrative routines such as SetAccessControl().
-
xs – This class audits routines that do not return X error messages to clients on failure when security attributes cause the failure. For example, GetImage() does not return a BadWindow error if it cannot read from a window for lack of privilege.
These events should be selected for audit on success only. When xs events are selected for failure, the audit trail fills with irrelevant records.
-
xx – This class includes all of the X audit classes.
Trusted Extensions Audit Events
Trusted Extensions software adds audit events to the system. The new audit events and the audit classes to which the events belong are listed in the /etc/security/audit_event file. The audit event numbers for Trusted Extensions are between 9000 and 10000. For more information about audit events, see the audit_event(4) man page.
Trusted Extensions Audit Tokens
The audit tokens that Trusted Extensions software adds to the Solaris OS are listed alphabetically in the following table. The tokens are also listed in the audit.log(4) man page.
Table 18–2 Trusted Extensions Audit Tokens|
Token Name |
Description |
|---|---|
|
Sensitivity label |
|
|
X window atom identification |
|
|
X client identification |
|
|
X window color information |
|
|
X window cursor information |
|
|
X window font information |
|
|
X window graphical context information |
|
|
Xwindow pixel mapping information |
|
|
X window property information |
|
|
X window data information |
|
|
X window window information |
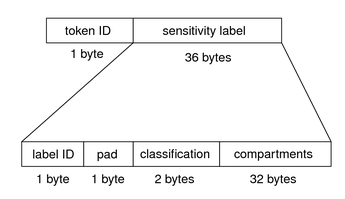
label Token
The label token contains a sensitivity label. This token contains the following fields:
-
A token ID
-
A sensitivity label
The following figure shows the token format.
Figure 18–2 label Token Format
A label token is displayed by the praudit command as follows:
sensitivity label,ADMIN_LOW |
xatom Token
The xatom token contains information concerning an X atom. This token contains the following fields:
-
A token ID
-
The string length
-
A text string that identifies the atom
An xatom token is displayed by praudit as follows:
X atom,_DT_SAVE_MODE |
xclient Token
The xclient token contains information concerning the X client. This token contains the following fields:
-
A token ID
-
The client ID
An xclient token is displayed by praudit as follows:
X client,15 |
xcolormap Token
The xcolormap token contains information about the colormaps. This token contains the following fields:
-
A token ID
-
The X server identifier
-
The creator's user ID
The following figure shows the token format.
Figure 18–3 Format for xcolormap, xcursor, xfont, xgc, xpixmap, and xwindow Tokens
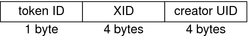
An xcolormap token is displayed by praudit as follows:
X color map,0x08c00005,srv |
xcursor Token
The xcursor token contains information about the cursors. This token contains the following fields:
-
A token ID
-
The X server identifier
-
The creator's user ID
Figure 18–3 shows the token format.
An xcursor token is displayed by praudit as follows:
X cursor,0x0f400006,srv |
xfont Token
The xfont token contains information about the fonts. This token contains the following fields:
-
A token ID
-
The X server identifier
-
The creator's user ID
Figure 18–3 shows the token format.
An xfont token is displayed by praudit as follows:
X font,0x08c00001,srv |
xgc Token
The xgc token contains information about the xgc. This token contains the following fields:
-
A token ID
-
The X server identifier
-
The creator's user ID
Figure 18–3 shows the token format.
An xgc token is displayed by praudit as follows:
Xgraphic context,0x002f2ca0,srv |
xpixmap Token
The xpixmap token contains information about the pixel mappings. This token contains the following fields:
-
A token ID
-
The X server identifier
-
The creator's user ID
Figure 18–3 shows the token format.
An xpixmap token is displayed by praudit as follows:
X pixmap,0x08c00005,srv |
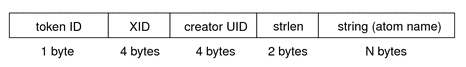
xproperty Token
The xproperty token contains information about various properties of a window. This token contains the following fields:
-
A token ID
-
The X server identifier
-
The creator's user ID
-
A string length
-
A text string that identifies the atom
The following figure shows an xproperty token format.
Figure 18–4 xproperty Token Format
An xproperty token is displayed by praudit as follows:
X property,0x000075d5,root,_MOTIF_DEFAULT_BINDINGS |
xselect Token
The xselect token contains the data that is moved between windows. This data is a byte stream with no assumed internal structure and a property string. This token contains the following fields:
-
A token ID
-
The length of the property string
-
The property string
-
The length of the property type
-
The property type string
-
A length field that gives the number of bytes of data
-
A byte string that contains the data
The following figure shows the token format.
Figure 18–5 xselect Token Format
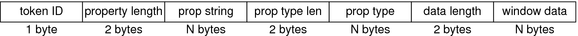
An xselect token is displayed by praudit as follows:
X selection,entryfield,halogen |
xwindow Token
The xwindow token contains information about a window. This token contains the following fields:
-
A token ID
-
The X server identifier
-
The creator's user ID
Figure 18–3 shows the token format.
An xwindow token is displayed by praudit as follows:
X window,0x07400001,srv |
Trusted Extensions Audit Policy Options
Trusted Extensions adds two audit policy options to existing Solaris auditing policy options. List the policies to see the additions:
$ auditconfig -lspolicy ... windata_down Include downgraded window information in audit records windata_up Include upgraded window information in audit records |
Extensions to Auditing Commands in Trusted Extensions
The auditconfig, auditreduce, and bsmrecord commands are extended to handle Trusted Extensions information:
-
The auditconfig command includes the Trusted Extensions audit policies. For details, see the auditconfig(1M) man page.
-
The auditreduce command adds the -l option for filtering records according to the label. For details, see the auditreduce(1M) man page.
-
The bsmrecord command includes the Trusted Extensions audit events. For details, see the bsmrecord(1M) man page.
- © 2010, Oracle Corporation and/or its affiliates
