Chapter 14 SPARC: Installing With WAN Boot (Examples)
This chapter provides an example of setting up and installing client systems over a wide area network (WAN). The examples in this chapter describe how to perform a secure WAN boot installation over an HTTPS connection.
-
(Optional) Configure the WAN Boot Server as a Logging Server
-
(Optional) Use Private Key and Certificate for Client Authentication
Sample Site Setup
Figure 14–1 shows the site setup for this example.
Figure 14–1 Sample Site for WAN Boot Installation
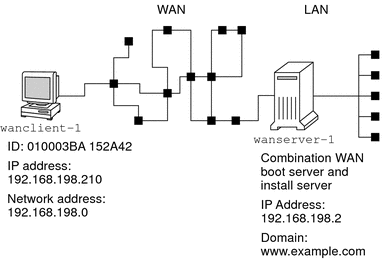
This sample site has the following characteristics.
-
The server wanserver-1 is to be configured as a WAN boot server and an install server.
-
The IP address of wanserver-1 is 192.168.198.2.
-
The domain name of wanserver-1 is www.example.com.
-
wanserver-1 is running the current Solaris release.
-
wanserver-1 is running the Apache web server. The Apache software on wanserver-1 is configured to support HTTPS.
-
The client to be installed is named wanclient-1.
-
wanclient-1 is an UltraSPARCII system.
-
The client ID for wanclient-1 is 010003BA152A42.
-
The IP address of wanclient-1 is 192.168.198.210.
-
The IP address of the client's subnet is 192.168.198.0.
-
The client system wanclient-1 has Internet access, but is not directly connected to the network that includes wanserver-1.
-
wanclient-1 is a new system that is to be installed with the current Solaris release software.
Create the Document Root Directory
To store the installation files and data, set up the following directories in the document root directory (/opt/apache/htdocs) on wanserver-1.
-
Solaris Flash directory
wanserver-1# mkdir -p /opt/apache/htdocs/flash/
-
WAN boot miniroot directory
wanserver-1# mkdir -p /opt/apache/htdocs/miniroot/
-
wanboot program directory
wanserver-1# mkdir -p /opt/apache/htdocs/wanboot/
Create the WAN Boot Miniroot
Use the setup_install_server(1M) with the -w option to copy the WAN boot miniroot and the Solaris software image to the /export/install/Solaris_10 directory of wanserver-1.
Insert the Solaris Software media in the media drive that is attached to wanserver-1. Type the following commands.
wanserver-1# mkdir -p /export/install/cdrom0 wanserver-1# cd /cdrom/cdrom0/Solaris_10/Tools wanserver-1# ./setup_install_server -w /export/install/cdrom0/miniroot \ /export/install/cdrom0 |
Move the WAN boot miniroot to the document root directory (/opt/apache/htdocs/) of the WAN boot server.
wanserver-1# mv /export/install/cdrom0/miniroot/miniroot \ /opt/apache/htdocs/miniroot/miniroot.s10_sparc |
Check the Client OBP for WAN Boot Support
Determine that the client OBP supports WAN boot by typing the following command on the client system.
# eeprom | grep network-boot-arguments network-boot-arguments: data not available |
In the previous example, the network-boot-arguments: data not available output indicates that the client OBP supports WAN boot.
Install the wanboot Program on the WAN Boot Server
To install the wanboot program on the WAN boot server, copy the program from the Solaris Software media to the WAN boot server's document root directory.
Insert the Solaris DVD or the Solaris Software - 1 CD in the media drive that is attached to wanserver-1 and type the following commands.
wanserver-1# cd /cdrom/cdrom0/Solaris_10/Tools/Boot/platform/sun4u/ wanserver-1# cp wanboot /opt/apache/htdocs/wanboot/wanboot.s10_sparc |
Create the /etc/netboot Hierarchy
Create the wanclient-1 subdirectories of the /etc/netboot directory on the WAN boot server. The WAN boot installation programs retrieve configuration and security information from this directory during the installation.
wanclient-1 is located on the subnet 192.168.198.0, and has a client ID of 010003BA152A42. To create the appropriate subdirectory of /etc/netboot for wanclient-1, perform the following tasks.
-
Create the /etc/netboot directory.
-
Change the permissions of the /etc/netboot directory to 700.
-
Change the ownership of the /etc/netboot directory to the owner of the web server process.
-
Assume the same user role as the web server user.
-
Create a subdirectory of /etc/netboot that is named after the subnet (192.168.198.0).
-
Create a subdirectory of the subnet directory that is named after the client ID.
-
Change the permissions of the /etc/netboot subdirectories to 700.
wanserver-1# cd / wanserver-1# mkdir /etc/netboot/ wanserver-1# chmod 700 /etc/netboot wanserver-1# chown nobody:admin /etc/netboot wanserver-1# exit wanserver-1# su nobody Password: nobody# mkdir -p /etc/netboot/192.168.198.0/010003BA152A42 nobody# chmod 700 /etc/netboot/192.168.198.0 nobody# chmod 700 /etc/netboot/192.168.198.0/010003BA152A42 |
Copy the wanboot-cgi Program to the WAN Boot Server
On systems that are running the current Solaris release, the wanboot-cgi program is located in the /usr/lib/inet/wanboot/ directory. To enable the WAN boot server to transmit the installation data, copy the wanboot-cgi program to the cgi-bin directory in the web server software directory.
wanserver-1# cp /usr/lib/inet/wanboot/wanboot-cgi \ /opt/apache/cgi-bin/wanboot-cgi wanserver-1# chmod 755 /opt/apache/cgi-bin/wanboot-cgi |
(Optional) Configure the WAN Boot Server as a Logging Server
By default, all WAN boot logging messages are displayed on the client system. This default behavior enables you to quickly debug any installation issues.
If you want to view the boot and installation messages on the WAN boot server, copy the bootlog-cgi script to the cgi-bin directory on wanserver-1.
wanserver-1# cp /usr/lib/inet/wanboot/bootlog-cgi /opt/apache/cgi-bin/ wanserver-1# chmod 755 /opt/apache/cgi-bin/bootlog-cgi |
Configure the WAN Boot Server to Use HTTPS
To use HTTPS in your WAN boot installation, you must enable SSL support in the web server software. You must also install a digital certificate on the WAN boot server. This example assumes that the Apache web server on wanserver-1 is configured to use SSL. This example also assumes that a digital certificate and a certificate authority that establish the identity of wanserver-1 are already installed on wanserver-1.
For examples about how to configure your web server software to use SSL, see you web server documentation.
Provide the Trusted Certificate to the Client
By requiring the server to authenticate itself to the client, you protect the data that is transmitted from the server to the client over HTTPS. To enable server authentication, you provide a trusted certificate to the client. The trusted certificate enables the client to verify the identity of the server during the installation.
To provide the trusted certificate to the client, assume the same user role as the web server user. Then, split the certificate to extract a trusted certificate. Then, insert the trusted certificate in the client's truststore file in the /etc/netboot hierarchy.
In this example, you assume the web server user role of nobody. Then, you split the server PKCS#12 certificate that is named cert.p12, and insert the trusted certificate in /etc/netboot directory for wanclient-1.
wanserver-1# su nobody Password: wanserver-1# wanbootutil p12split -i cert.p12 -t \ /etc/netboot/192.168.198.0/010003BA152A42/truststore |
(Optional) Use Private Key and Certificate for Client Authentication
To further protect your data during the installation, you might want to require wanclient-1 to authenticate itself to wanserver-1. To enable client authentication in your WAN boot installation, insert a client certificate and private key in the client subdirectory of the /etc/netboot hierarchy.
To provide a private key and certificate to the client, perform the following tasks.
-
Assume the same user role as the web server user
-
Split the PKCS#12 file into a private key and a client certificate
-
Insert the certificate in the client's certstore file
-
Insert the private key in the client's keystore file
In this example, you assume the web server user role of nobody. Then, you split the server PKCS#12 certificate that is named cert.p12. You insert certificate in the /etc/netboot hierarchy for wanclient-1. You then insert the private key that you named wanclient.key in the client's keystore file.
wanserver-1# su nobody Password: wanserver-1# wanbootutil p12split -i cert.p12 -c \ /etc/netboot/192.168.198.0/010003BA152A42/certstore -k wanclient.key wanserver-1# wanbootutil keymgmt -i -k wanclient.key \ -s /etc/netboot/192.168.198.0/010003BA152A42/keystore \ -o type=rsa |
Create the Keys for the Server and the Client
To protect the data transmitted between the server and client, you create a hashing key and an encryption key. The server uses the hashing key to protect the integrity of the wanboot program. The server uses the encryption key to encrypt the configuration and installation data. The client uses the hashing key to check the integrity of the downloaded wanboot program. The client uses the encryption key to decrypt the data during the installation.
First, you assume the same user role as the web server user. In this example, the web server user role is nobody.
wanserver-1# su nobody Password: |
Then, you use the wanbootutil keygen command to create a master HMAC SHA1 key for wanserver-1.
wanserver-1# wanbootutil keygen -m |
Then, create a hashing key and an encryption key for wanclient-1.
wanserver-1# wanbootutil keygen -c -o net=192.168.198.0,cid=010003BA152A42,type=sha1 wanserver-1# wanbootutil keygen -c -o net=192.168.198.0,cid=010003BA152A42,type=3des |
The previous command creates a HMAC SHA1 hashing key and a 3DES encryption key for wanclient-1. 192.168.198.0 specifies the subnet of wanclient-1, and 010003BA152A42 specifies the client ID of wanclient-1.
Create the Solaris Flash Archive
In this example, you create your Solaris Flash archive by cloning the wanserver-1 master system. The archive is named sol_10_sparc, and is copied exactly from the master system. The archive is an exact duplicate of the master system. The archive is stored in sol_10_sparc.flar. You save the archive in the flash/archives subdirectory of the document root directory on the WAN boot server.
wanserver-1# flarcreate -n sol_10_sparc \ /opt/apache/htdocs/flash/archives/sol_10_sparc.flar |
Create the sysidcfg File
To preconfigure the wanclient-1 system, specify keywords and values in the sysidcfg file. Save this file in the appropriate subdirectory of the document root directory of wanserver-1.
Example 14–1 sysidcfg File for client-1 System
The following is an example of a sysidcfg file for wanclient-1. The host name, IP address, and netmask of these systems have been preconfigured by editing the naming service. This file is located in the /opt/apache/htdocs/flash/ directory.
network_interface=primary {hostname=wanclient-1
default_route=192.168.198.1
ip_address=192.168.198.210
netmask=255.255.255.0
protocol_ipv6=no}
timezone=US/Central
system_locale=C
terminal=xterm
timeserver=localhost
name_service=NIS {name_server=matter(192.168.254.254)
domain_name=leti.example.com
}
security_policy=none
Create the Client's Profile
For the wanclient-1 system, create a profile that is named wanclient_1_prof. The wanclient_1_prof file contains the following entries, which define the current Solaris release software to be installed on the wanclient-1 system.
# profile keywords profile values # ---------------- ------------------- install_type flash_install archive_location https://192.168.198.2/flash/archives/cdrom0.flar partitioning explicit filesys c0t1d0s0 4000 / filesys c0t1d0s1 512 swap filesys c0t1d0s7 free /export/home
The following list describes some of the keywords and values from this example.
- install_type
-
The profile installs a Solaris Flash archive on the clone system. All files are overwritten as in an initial installation.
- archive_location
-
The compressed Solaris Flash archive is retrieved from wanserver-1.
- partitioning
-
The file system slices are determined by the filesys keywords, value explicit. The size of root (/) is based on the size of the Solaris Flash archive. The size of swap is set to the necessary size and is installed on c0t1d0s1. /export/home is based on the remaining disk space. /export/home is installed on c0t1d0s7.
Create and Validate the rules File
The custom JumpStart programs use the rules file to select the correct installation profile for the wanclient-1 system. Create a text file that is named rules. Then, add keywords and values to this file.
The IP address of the wanclient-1 system is 192.168.198.210, and the netmask is 255.255.255.0. Use the network rule keyword to specify the profile that the custom JumpStart programs should use to install wanclient-1.
network 192.168.198.0 - wanclient_1_prof - |
This rules file instructs the custom JumpStart programs to use the wanclient_1_prof to install the current Solaris release software on wanclient-1.
Name this rule file wanclient_rule.
After you create the profile and the rules file, you run the check script to verify that the files are valid.
wanserver-1# ./check -r wanclient_rule |
If the check script does not find any errors, the script creates the rules.ok file.
Save the rules.ok file in the /opt/apache/htdocs/flash/ directory.
Create the System Configuration File
Create a system configuration file that lists the locations of the sysidcfg file and the custom JumpStart files on the install server. Save this file in a directory that is accessible to the WAN boot server.
In the following example, the wanboot-cgi program looks for the sysidcfg and custom JumpStart files in the document root directory of the WAN boot server. The domain name of the WAN boot server is https://www.example.com. The WAN boot server is configured to use secure HTTP, so the data and files are protected during the installation.
In this example, the system configuration file is named sys-conf.s10–sparc, and the file is saved in the /etc/netboot hierarchy on the WAN boot server. The sysidcfg and custom JumpStart files are located in the flash subdirectory of the document root directory.
SsysidCF=https://www.example.com/flash/ SjumpsCF=https://www.example.com/flash/
Create the wanboot.conf File
WAN boot uses the configuration information that is included in the wanboot.conf file to install the client machine. Create the wanboot.conf file in a text editor. Save the file to the appropriate client subdirectory in the /etc/netboot hierarchy on the WAN boot server.
The following wanboot.conf file for wanclient-1 includes configuration information for a WAN installation that uses secure HTTP. This file also instructs WAN boot to use a HMAC SHA1 hashing key and a 3DES encryption key to protect data.
boot_file=/wanboot/wanboot.s10_sparc root_server=https://www.example.com/cgi-bin/wanboot-cgi root_file=/miniroot/miniroot.s10_sparc signature_type=sha1 encryption_type=3des server_authentication=yes client_authentication=no resolve_hosts= boot_logger= system_conf=sys-conf.s10–sparc
This wanboot.conf file specifies the following configuration.
- boot_file=/wanboot/wanboot.s10_sparc
-
The wanboot program is named wanboot.s10_sparc. This program is located in the wanboot directory in the document root directory on wanserver-1.
- root_server=https://www.example.com/cgi-bin/wanboot-cgi
-
The location of the wanboot-cgi program on wanserver-1 is https://www.example.com/cgi-bin/wanboot-cgi. The https portion of the URL indicates that this WAN boot installation uses secure HTTP.
- root_file=/miniroot/miniroot.s10_sparc
-
The WAN boot miniroot is named miniroot.s10_sparc. The miniroot is located in the miniroot directory in the document root directory on wanserver-1.
- signature_type=sha1
-
The wanboot program and the WAN boot file system are signed by using a HMAC SHA1 hashing key.
- encryption_type=3des
-
The wanboot program and the WAN boot file system are encrypted with a 3DES key.
- server_authentication=yes
-
The server is authenticated during the installation.
- client_authentication=no
-
The client is not authenticated during the installation.
Note –If you performed the tasks in (Optional) Use Private Key and Certificate for Client Authentication, set this parameter as client_authentication=yes
- resolve_hosts=
-
No additional host names are needed to perform the WAN installation. All the host names that are required by the wanboot-cgi program are specified in the wanboot.conf file and the client certificate.
- boot_logger=
-
Booting and installation log messages are displayed on the system console. If you configured the logging server in (Optional) Configure the WAN Boot Server as a Logging Server, and you want WAN boot messages to appear on the WAN boot server as well, set this parameter to boot_logger=https://www.example.com/cgi-bin/bootlog-cgi.
- system_conf=sys-conf.s10–sparc
-
The system configuration file that specifies the locations of the sysidcfg and JumpStart files is located in the sys-conf.s10–sparc file in the /etc/netboot hierarchy on wanserver-1.
In this example, you save the wanboot.conf file in the /etc/netboot/192.168.198.0/010003BA152A42 directory on wanserver-1.
Check the net Device Alias in OBP
To boot the client from the WAN with the boot net, the net device alias must be set to the client's primary network device. At the client ok prompt, type the devalias command to verify that the net alias is set to the primary network device /pci@1f,0/pci@1,1/network@c,1.
ok devalias screen /pci@1f,0/pci@1,1/SUNW,m64B@2 net /pci@1f,0/pci@1,1/network@c,1 net2 /pci@1f,0/pci@1,1/network@5,1 disk /pci@1f,0/pci@1/scsi@8/disk@0,0 cdrom /pci@1f,0/pci@1,1/ide@d/cdrom@0,0:f keyboard /pci@1f,0/pci@1,1/ebus@1/su@14,3083f8 mouse /pci@1f,0/pci@1,1/ebus@1/su@14,3062f8 |
In the previous output example, the primary network device /pci@1f,0/pci@1,1/network@c,1 is assigned to the net alias. You do not need to reset the alias.
Install Keys on the Client
In Create the Keys for the Server and the Client, you created the hashing key and encryption key to protect your data during the installation. To enable the client to decrypt the data transmitted from wanserver-1 during the installation, install these keys on wanclient-1.
On wanserver-1, display the key values.
wanserver-1# wanbootutil keygen -d -c -o net=192.168.198.0,cid=010003BA152A42,type=sha1 b482aaab82cb8d5631e16d51478c90079cc1d463 wanserver-1# wanbootutil keygen -d -c -o net=192.168.198.0,cid=010003BA152A42,type=3des 9ebc7a57f240e97c9b9401e9d3ae9b292943d3c143d07f04 |
The previous example uses the following information.
- net=192.168.198.0
-
Specifies the IP address of the client's subnet
- cid=010003BA152A42
-
Specifies the client's ID
- b482aaab82cb8d5631e16d51478c90079cc1d463
-
Specifies the value of the client's HMAC SHA1 hashing key
- 9ebc7a57f240e97c9b9401e9d3ae9b292943d3c143d07f04
-
Specifies the value of the client's 3DES encryption key
If you use an AES encryption key in your installation, change type=3des to type=aes to display the encryption key value.
At the ok prompt on wanclient-1, install the keys.
ok set-security-key wanboot-hmac-sha1 b482aaab82cb8d5631e16d51478c90079cc1d463 ok set-security-key wanboot-3des 9ebc7a57f240e97c9b9401e9d3ae9b292943d3c143d07f04 |
The previous commands perform the following tasks.
-
Installs the HMAC SHA1 hashing key with a value of b482aaab82cb8d5631e16d51478c90079cc1d463 on wanclient-1
-
Installs the 3DES encryption key with a value of 9ebc7a57f240e97c9b9401e9d3ae9b292943d3c143d07f04 on wanclient-1
Install the Client
You can perform an unattended installation by setting network boot argument variables for wanclient-1 at the ok prompt, and then booting the client.
ok setenv network-boot-arguments host-ip=192.168.198.210, router-ip=192.168.198.1,subnet-mask=255.255.255.0,hostname=wanclient-1, file=http://192.168.198.2/cgi-bin/wanboot-cgi ok boot net - install Resetting ... Sun Blade 100 (UltraSPARC-IIe), No Keyboard Copyright 1998-2003 Sun Microsystems, Inc. All rights reserved. OpenBoot 4.x.build_28, 512 MB memory installed, Serial #50335475. Ethernet address 0:3:ba:e:f3:75, Host ID: 83000ef3. Rebooting with command: boot net - install Boot device: /pci@1f,0/network@c,1 File and args: - install <time unavailable> wanboot progress: wanbootfs: Read 68 of 68 kB (100%) <time unavailable> wanboot info: wanbootfs: Download complete Fri Jun 20 09:16:06 wanboot progress: miniroot: Read 166067 of 166067 kB (100%) Fri Jun 20Tue Apr 15 09:16:06 wanboot info: miniroot: Download complete SunOS Release 5.10 Version WANboot10:04/11/03 64-bit Copyright 1983-2003 Sun Microsystems, Inc. All rights reserved. Use is subject to license terms. Configuring devices. |
The following variables are set.
-
The client IP address is set to 192.168.198.210.
-
The client's router IP address is set to 192.168.198.1
-
The client's subnet mask is set to 255.255.255.0
-
The client's host name is set to wanclient-1
-
The wanboot-cgi program is located at http://192.168.198.2/cgi-bin/wanboot-cgi
The client installs over the WAN. If the wanboot program does not find all the necessary installation information, you might be prompted to provide the missing information at the command line.
- © 2010, Oracle Corporation and/or its affiliates
