Configuring User-Initiated Account Unlock
You can configure OpenSSO Enterprise so that when an end-user account is locked, the user can unlock the account without intervention from an administrator. The OpenSSO LDAP authentication module supports the account lockout controls enforced by most directory servers.
To configure OpenSSO Enterprise for user-initiated account unlock, complete the following steps:
A user can be locked out of his or her account, or unable to log in, due to memory account lockout or physical account lockout.
- Memory account lockout
-
This occurs when the user has exceeded the allowed number of failed attempts to log in as configured in the password policy. The user may remain locked out for a set period of time and can only reset the password after that period has passed. The locked state of the user account is maintained in memory and no information is written to the user's LDAP profile.
- Physical account lockout
-
This occurs when the status of a specified LDAP attribute in the user's profile is explicitly changed to Inactive, either by an administrator or as a result of some automated processes. The specified LDAP attribute is defined as the value of the Lockout Attribute Name attribute in the Core authentication module. By default it is inetuserstatus.
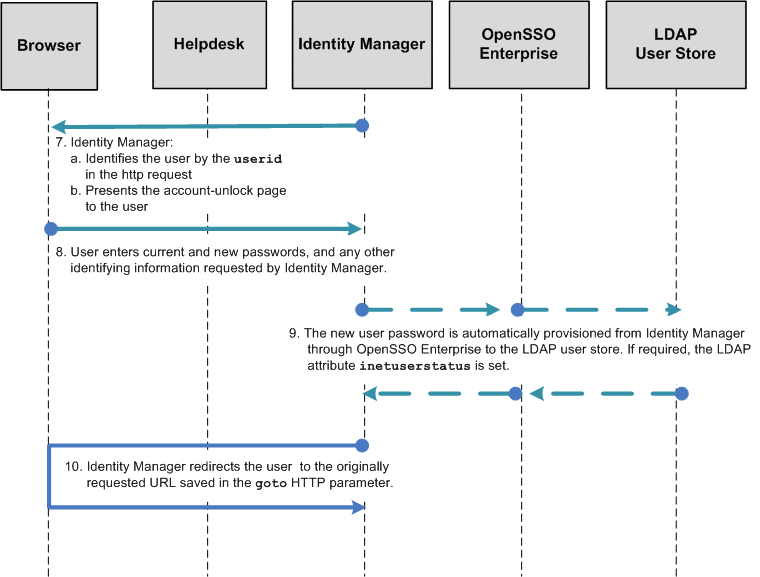
The following figures illustrate the process flow for user-initiated account unlock.
Figure 1–11 Process Flow for User-Initiated Account Unlock
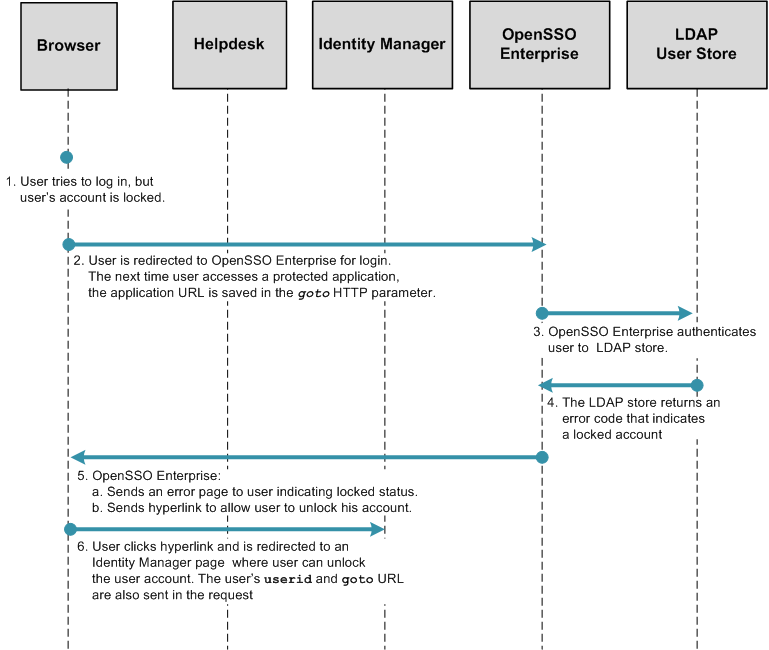
Figure 1–12 Process Flow for User-Initiated Account Unlock (continued)
Configuring the Directory Server
Before you can configure OpenSSO Enterprise for administrator-initiated password reset, you must configure the Directory Server must to meet the following conditions:
-
A password policy is configured and assigned to the test user's LDAP profile in the directory server. The password policy should have the following controls set:
- Enable Account Lockout
-
LDAP attribute: passwordLockout
- Failures Before Lockout
-
LDAP attribute: passwordMaxFailure
- Failure Count Reset
-
LDAP attribute: passwordResetFailureCount
- Set Limit on Lockout Duration
-
LDAP attribute: passwordUnlock
- Lockout Duration
-
LDAP attribute: passwordLockoutDuration
-
The passwordPolicySubentry attribute in the test user's LDAP profile is set with the DN of the password policy. This indicates that the that the password policy has been assigned to this user. Example:
cn=idm_integration,dc=sun,dc=com
See the Sun Java System Directory Server Enterprise Edition 6.3 Administration Guidefor detailed instructions on configuring these settings.
Configuring OpenSSO Enterprise for User-Initiated Account Unlock
The integration between OpenSSO Enterprise and Identity Manager supports only LDAP authentication for this user-initiated account unlock. The LDAP authentication module in OpenSSO supports account-lockout controls enforced by most directory servers.
To configure OpenSSO Enterprise for user-initiated account unlock, complete the following steps:
 To Enable LDAP Authentication
To Enable LDAP Authentication
Before You Begin
Memory account lockout in OpenSSO Enterprise must be disabled because the account lockout controls in the user data store will be used. You can use the OpenSSO Enterprise console to disable memory account lockout. See Enabling Account Lockout in Sun OpenSSO Enterprise 8.0 Administration Guide for detailed information.
-
Log in to the OpenSSO Enterprise console as administrator.
-
Click the Access Control tab.
-
Navigate to Top Level Realm > Authentication > Authentication Chaining.
-
In the Authentication Chaining section, click New.
-
Enter a name for the chain and click OK.
For this example: idmauth.
-
On the new chain's Properties page, add the LDAP module as REQUIRED, and click Save.
-
Click Back to Authentication.
-
For the value of Organization Authentication Configuration, choose the service just created .
-
Save changes and log out of OpenSSO Enterprise.
Next Steps
After completing this configuration, use /opensso/console to log in to the OpenSSO Enterprise console; do not /opensso/UI/Login. This ensures that the authentication module configured for the OpenSSO Enterprise administrator is used when logging into the OpenSSO Enterprise console, and that the LDAP module just configured is not used.
 To Define Identity Manager URLs as Not Enforced
To Define Identity Manager URLs as Not Enforced
-
Log in to the OpenSSO Enterprise console as administrator.
-
Click the Access Control tab.
-
Click the appropriate realm name and navigate to the Policy Agents profile for the policy agent that protects Identity Manager.
-
Under the policy agent profile, click the Application tab.
-
Add the following URIs to the Not Enforced URIs property.
-
/idm/authutil/
-
/idm/authutil/*
-
/idm/authutil/*?*
-
-
Click Save.
-
Log out of OpenSSO Enterprise.
Modifying the OpenSSO Enterprise Login Page
Embed code into the OpenSSO Enterprise Login.jsp file that will save the URL in the HTTP request parameter goto. This URL is required by the user_inactive.jsp that you will create in a subsequent procedure. The URL is saved so that it can be passed onto Identity Manager. Identity Manager ultimately redirects the user to the URL. This is the original URL requested by the user, before the user was redirected to OpenSSO for login.
Choose only one of the following procedures:
 To Manually Modify a Deployed Login.jsp
To Manually Modify a Deployed Login.jsp
-
Use a text editor to open the file web-container-deploy-base/opensso/config/auth/default/Login.jsp.
-
Modify the file as in the following sample.
Changes are highlighted in bold.
... <% String ServiceURI = (String) viewBean.getDisplayFieldValue(viewBean.SERVICE_URI); String encoded = "false"; String gotoURL = (String) viewBean.getValidatedInputURL( request.getParameter("goto"), request.getParameter("encoded"), request); String encodedQueryParams = (String) viewBean.getEncodedQueryParams(request); if ((gotoURL != null) && (gotoURL.length() != 0)) { encoded = "true"; } String replaygotoURL = ""; String goToURL = request.getParameter("goto"); if(gotoURL != null && !gotoURL.equals("null") && (gotoURL.length() > 0)){ replaygotoURL = "&goto=" + goToURL; } System.out.println("replaygotoURL: " + replaygotoURL);%> <link rel="stylesheet" href="<%= ServiceURI %>/css/styles.css" type="text/css" /> <script language="JavaScript" src="<%= ServiceURI %>/js/browserVersion.js"></script> <script language="JavaScript" src="<%= ServiceURI %>/js/auth.js"></script> ... <input type="hidden" name="goto" value="<%= gotoURL %>"> <input type="hidden" name="SunQueryParamsString" value="<%= encodedQueryParams %>"> <input type="hidden" name="encoded" value="<%= encoded %>"> <input type="hidden" name="plaingoto" value="<%= request.getParameter("goto") %>"></auth:form> </jato:content> ...
 To Use the Sample Login.jsp
To Use the Sample Login.jsp
-
Use a text editor to open the file opensso/integrations/idm/jsps/Login.jsp in the decompressed opensso.zip distribution.
-
Replace the deployed /web-container-deploy-base/opensso/config/auth/default/Login.jsp with the modifiedLogin.jsp.
Choose one of the following options:
You can replace your existing Login.jsp with the sample Login.jsp. If you choose this option, the following will occur:
-
You will lose any custom changes made to the existing Login.jsp.
-
You will inherit changes that might have been previously made to the sample Login.jsp to incorporate requirements for other use cases related to the OpenSSO integration with Identity Manager.
-
You must change the Identity Manager URL embedded in the sample to reflect the Identity Manager system URL of your architecture.
You can search for the string /idm to locate the URLs.
Alternatively, you can manually make changes to the file. If you choose this option, run the diff command to view the differences between the two files.
-
-
Remove the web containers temporary, compiled JSP to ensure that the changes made are picked up.
For example, if using GlassFish, the temporary, compiled classes can be found under glassfish-home/domains/your-domain/generated/.
-
Restart the OpenSSO Enterprise web container after making the changes.
Modifying the Account Lockout Message Page
Modify the user_inactive.jsp file. This file notifies the user that the account is locked. Modify the page to include a redirect to an Identity Manager page the user can use to unlock the account. The user_inactive.jsp file forwards the following information to Identity Manager:
-
The original URL requested by the user and defined as the value of the goto parameter.
-
The user identifier defined as the value of the accountId parameter.
The Identity Manager URL used in the following sample refers to anonResetPassword.jsp. You might, however, direct the user to questionLogin.jsp the forgotten password page. If a user has accidentally locked an account it may be because of a forgotten password.
You can manually change the deployed user_inactive.jsp file, or you can use the sample user_inactive.jsp included with the opensso.zip download. Choose only one of the following procedures:
 To Manually Modify the Account Lockout Message
Page
To Manually Modify the Account Lockout Message
Page
-
Use a text editor to open the file web-container-deploy-base/opensso/config/auth/default/user_inactive.jsp.
-
Add the sections of code highlighted in bold in the following example:
... <head> <title><jato:text name="htmlTitle_UserInactive" /></title> <% String ServiceURI = (String) viewBean.getDisplayFieldValue(viewBean.SERVICE_URI); System.out.println("AccountId: " + request.getParameter("IDToken1")); System.out.println("goto: " + request.getParameter("goto")); System.out.println("plaingoto: " + request.getParameter("plaingoto")); String accountId = request.getParameter("IDToken1"); String gotoURL = request.getParameter("plaingoto"); String redirectURL = "http://HostName.domainName.com:6480/idm/authutil/anonResetPassword.jsp"; if(accountId != null){ redirectURL = redirectURL + "?accountId=" + accountId; } if(gotoURL != null && !gotoURL.equals("null") && (gotoURL.length() > 0)){ if(accountId == null){ redirectURL = redirectURL + "?goto=" + gotoURL; }else{ redirectURL = redirectURL + "&goto=" + gotoURL; } } %> ... <div class="AlrtMsgTxt"> <auth:resBundle bundleName="amAuthUI" resourceKey="contactadmin" /> <!-- hyperlink --> <jato:content name="ContentHref"> <p><a href="<%= redirectURL %>">Unlock Yourself</a></p> </jato:content> </div> </td></tr></table></div></td> </tr> <tr> <td> </td> </tr> <tr> <td><img src="<%= ServiceURI %>/images/dot.gif" width="1" height="33" alt="" /></td> <td> </td> </tr> ... -
Embedded in the JSP, you will see the URL to the Identity Manager page that allows the account unlock. Modify this URL as per your deployment.
-
Remove the web containers temporary, compiled JSP to ensure that the changes made are picked up.
For example, if using GlassFish, the temporary, compiled classes can be found under glassfish-home/domains/your-domain/generated/.
-
Restart the OpenSSO Enterprise web container after making the changes.
 To Use the Sample Account Lockout Message
Page
To Use the Sample Account Lockout Message
Page
-
Locate the file opensso/integrations/idm/jsps/user_inactive.jsp in the opensso.zip distribution.
-
Replace the deployed /web-container-deploy-base/opensso/config/auth/default/user_inactive.jsp with the modified file.
Choose only one of the following options:
You can replace your existing user_inactive.jsp with the sample user_inactive.jsp. If you choose this option, the following will occur:
-
You will lose any custom changes made to the existing user_inactive.jsp.
-
You will inherit changes that might have been previously made to the sample user_inactive.jsp to incorporate requirements for other use cases related to the OpenSSO integration with Identity Manager.
-
You must change the Identity Manager URL embedded in the user_inactive.jsp to reflect your Identity Manager system URL. Search for the string /idm in the sample Login.jsp file to locate these URLs.
The Identity Manager URL used in the sample mentions the page anonResetPassword.jsp. However, you might want to direct the user to the forgotten-password page questionLogin.jsp instead. If the user has accidentally locked his account, he may not know his password to be able to reset it.
Alternatively, you can manually make the changes to the file. If you choose this option, run the diff command to view the differences between the two files.
-
-
Remove the web containers temporary, compiled JSP to ensure that the changes made are picked up.
For example, if using GlassFish, the temporary, compiled classes can be found under glassfish-home/domains/your-domain/generated/.
-
Restart the OpenSSO Enterprise web container after making the changes.
To Test the User-Initiated Account Unlock Configurations
Complete the following tests:
 To Test Memory Account Unlock
To Test Memory Account Unlock
In this case, the user account is locked by maintaining a state of the account in memory. No information is stored in the user's LDAP profile to indicate the status of the account (active or inactive) when the account is locked in memory.
-
Configure the password policy and assign the policy to the test user.
See the Sun Java System Directory Server Enterprise Edition 6.3 Administration Guidefor detailed instructions on configuring these settings.
-
Access a resource protected by OpenSSO Enterprise to be redirected to the login page.
-
Log in to OpenSSO Enterprise using an incorrect password.
Do this repeatedly until the account is locked and the error page is displayed. The account is locked based on the number of attempts configured in the password policy.
-
Click the hyperlink on the page.
You are redirected to an Identity Manager page on which are required to change your password. Note that the URL is the one configured in the user_inactive.jsp.
-
Change your password.
Identity Manager determines the account from the accountID parameter and changes the password on both OpenSSO Enterprise and on Identity Manager. After a successful modification, the user is redirected to the original URL defined in the goto parameter.
 To Test Physical Account Unlock
To Test Physical Account Unlock
-
In the test user's profile, set the value of the inetuserstatus attribute in the user data store to Inactive.
-
Access a resource protected by OpenSSO Enterprise to get redirected to the login page.
-
Log in to OpenSSO Enterprise.
An error page is displayed informing you that the account has been locked.
-
Click the hyperlink on the page.
You are redirected to an Identity Manager page on which you are required to change your password. Note that the URL is the one configured in the user_inactive.jsp.
-
Change your password.
Identity Manager determines the account from the accountID parameter and will change the password on both OpenSSO and Identity Manager. After a successful modification, the user is redirected to the original URL defined in the goto parameter.
- © 2010, Oracle Corporation and/or its affiliates
