Chapter 2 Integrating CA SiteMinder
Computer Associates (CA) SiteMinder (formerly Netegrity SiteMinder) is an enterprise infrastructure product that enables centralized, secure Web access management. Its features include user authentication and single sign-on, policy-based authorization, and identity federation. One of the first single sign-on products to arrive on the market, legacy SiteMinder installations still exist to protect enterprise applications in many company networks.
This chapter describes options for integrating CA SiteMinder with Sun OpenSSO Enterprise. The chapter also provides instructions for using OpenSSO Enterprise to configure end-to-end CA SiteMinder single sign-on.
The following topics are included in this chapter:
-
Using OpenSSO Enterprise to Enable SiteMinder Federation in an Identity Provider Environment
-
Using OpenSSO Enterprise to Enable SiteMinder Federation in a Service Provider Environment
About CA SiteMinder
CA SiteMinder consists of two core components that are used for access control and single sign-on:
-
Policy Server
-
Policy Agents
The SiteMinder Policy Server provides policy management, authentication, authorization and accounting. The Policy Server core engine was developed in C/C++ and the core components run like process daemons with predefined TCP/IP ports. The policy user interface is a Java applet-based console. A supported web server configured with a SiteMinder NSAPI plug-in provides the front-end HTTP interface. The policy user interface enables the user to create policies, domains, and realms, as well as to configure authentication schemes. The policy user interface also provides centralized agent configuration. SiteMinder also has a local Java applet-based console utility for managing system configuration such as authentication and authorization settings, port numbers, and so forth.
The SiteMinder Web Agent acts as a filter for protecting enterprise applications. SiteMinder provides various policy agents to access Web applications and content according to predefined security policies:
-
Web policy agents
-
SAML affiliated policy agents
-
Application server policy agents
-
RADIUS database policy agents
-
TransactionMinder XML policy agents
-
Custom policy agents (Any policy agent that is written using the SiteMinder Agent API)
The SAML Affiliated agent is part of CA Federated Security Services. The Security Services provide single sign-on from a producer site, such as a portal, to a SAML consumer acting as an affiliate in a federated network. The communication between the SAML Affiliated policy agent and SiteMinder at the producer site results in the generation of a SAML Assertion. The TransactionMinder XML Agent is an XML-enabled version of the SiteMinder Web Agent that authenticates and authorizes web services-bound URLs.
Authentication and Authorization
SiteMinder supports several authentication schemes as part of its authentication framework. Authentication schemes provide a way to collect credentials and determine the identity of a user. SiteMinder Credential Collector is an application within the web policy agent that gathers specific information about a user's credentials, and then sends the information to the Policy Server. For form-based authentication, credentials are acquired by the Forms Credential Collector (FCC) process. The default extension for FCC files is .fcc. FCC process files are composed in a simple mark-up language that includes HTML and some custom notation. The following describes a simple authentication scheme flow using a form-based authentication scheme:
-
A user requests a resource that is protected by a policy agent and contained in a realm. The realm is protected by an HTML form-based authentication scheme.
-
SiteMinder contacts the Policy Server and determines that the user request must be redirected to the credential collector.
-
The policy agent redirects to the URL of the Credential Collector file.
-
The Credential Collector displays the form described in the .fcc file of the user's browser.
-
The user fills out the custom form and submits it. The Credential Collector processes the credentials by submitting the form to the Policy Server.
-
If the user is authenticated, Credential Collector creates a session cookie and sends it to the browser. The browser redirects the user to the resource that the user originally requested.
-
The web policy agent handles user authorization by using the user's session.
User Sessions
SiteMinder supports persistent and non-persistent sessions. The standard SiteMinder sessions are non-persistent and contain user session data but no other user-specific data. For example, a session does not contain attributes unless configured to do so. The SiteMinder user session is created by the SiteMinder server upon successful authentication.
The servers send the user session SiteMinder Web Agent to set in the browser. The policy agent is responsible for validating the cookie and enforcing session timeouts. The cookie named SMSESSION contains the following parameters by default:
-
Device name or host name
-
User's full DN
-
User Name
-
Session idle timeout
-
Session maximum timeout
-
Session creation time
Understanding the SiteMinder User Cases
This chapter describes three use cases, all built upon legacy SiteMinder deployments. In each use case, SiteMinder continues to provide authentication service for legacy applications even after OpenSSO Enterprise is installed to protect the same enterprise applications. SiteMinder and OpenSSO Enterprise typically co-exist in the following use cases:
-
Simple Single Sign-On
-
Federated Single Sign-On in a Service Provider Environment
-
Federated Single Sign-On in an Identity Provider Environment
Single logout for any these of these use cases can be implemented in many ways. The logout for federation use cases must have a link in the partner portal for the following URL:
http:<sphost>:<spport>/opensso/saml2/jsp/spSingleLogoutInit.jsp?metaAlias= <metaalias>&idpEntityID=<idp entityid>&RelayState=<integrated product logout url> |
Single logout can also be achieved using Identity Provider-initiated single logout.
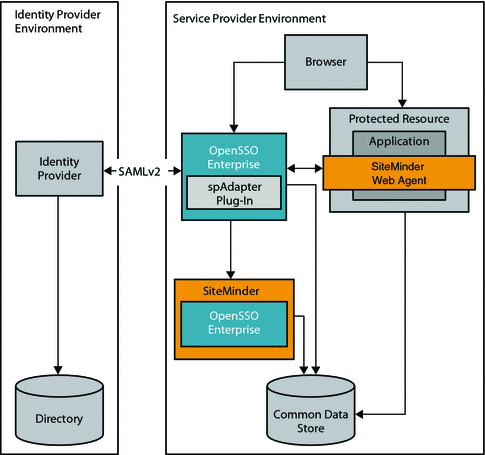
Simple Single Sign-On Use Case
In this use case, a SiteMinder instance is already deployed and configured to protect some of the enterprise applications in a company intranet. In the architecture figure below, the legacy application is contained in the Protected Resource . The company wants to continue leveraging SiteMinder for authentication purposes, while adding OpenSSO Enterprise to the environment to protect the same application. OpenSSO Enterprise is also used to protect all applications subsequently added to the enterprise.
An OpenSSO Enterprise policy agent protects the Protected Resource, while OpenSSO Enterprise itself is protected by a SiteMinder Web Agent. In this use case, an access request goes to OpenSSO Enterprise for policy evaluation or for single sign-on purposes. But the SiteMinder Web Agent, installed on the same container as OpenSSO Enterprise, redirects the user to the SiteMinder login page for authentication. The OpenSSO Enterprise custom authentication module validates the SiteMinder session depending upon whether or not the user has previously logged in to OpenSSO Enterprise. After successful login, the OpenSSO Enterprise custom authentication module uses the SiteMinder session to generate an OpenSSO Enterprise session. OpenSSO Enterprise then honors the user session obtained by the SiteMinder Policy Server.
Figure 2–1 Single Sign-On Architecture
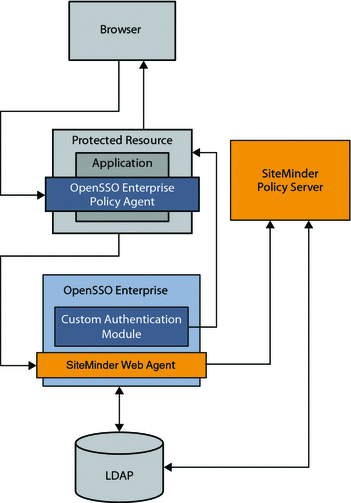
In this use case, both OpenSSO Enterprise server and SiteMinder policy server share the same user repository for user profile verification. OpenSSO Enterprise could also be configured to ignore the profile option if it relies on SiteMinder session for attributes.
The following figure illustrates the process flow for single sign-on using both SiteMinder and OpenSSO Enterprise.
Figure 2–2 Single Sign-On Process Flow
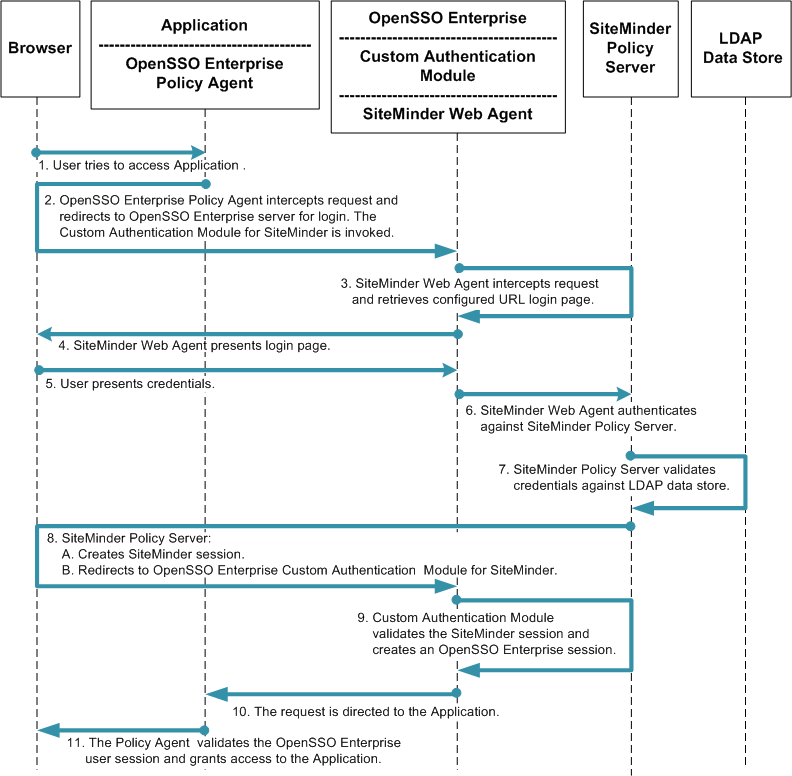
Federated Single Sign-On Use Cases
The SAML, ID-FF, and WS-Federation protocols provide cross-domain single sign-on among multiple trusted business entities. These protocols are also used in Identity Federation. Identity Federation involves an Identity Provider, also known as an authentication provider, and a Service Provider where the user authentication session at the Identity provider is consumed. The following are common use cases in which SiteMinder is enabled for federation protocols:
-
Enabling SiteMinder for federation protocols in a Service Provider environment
-
Enabling SiteMinder for federation protocols in an Identity Provider environment
The deployment examples in this chapter are built upon simple single sign-on integration. You must set up single sign-on before enabling federation. For more information about setting up simple single sign-on, see the Sun OpenSSO Enterprise Deployment Example: Single Sign-On. After setting up simple single sign-on, you can enable SiteMinder for Federation in either the Identity Provider environment or in the Service Provider environment.
The federated single sign-on use cases are configured for transient federation. Transient federation assumes that the users exist only in the Identity Provider environment. The Service Provider honors user authentication at Identity Provider. The Service Provider then creates an anonymous session so that Service Provider applications, protected by single sign-on, can be accessed. During SAML interactions, user attribute information can be exchanged back to the Service Provider for authorization and other purposes.
Usually, bulk federation exists between Identity Provider and Service Provider. For more information about transient and bulk federation, see the OpenSSO Enterprise product documentation.
Federated Single Sign-On in an Identity Provider Environment
In this use case, the company uses SiteMinder in the Identity Provider environment to protect applications within the company intranet. As the company partners with external companies, the company deploys OpenSSO Enterprise in the Service Provider environment to leverage the SAMLv2 Federation protocols.
The following figure illustrates how SiteMinder can be enabled in an Identity Provider environment using OpenSSO Enterprise for federation protocols.
Figure 2–3 SiteMinder Federation in an Identity Provider Environment
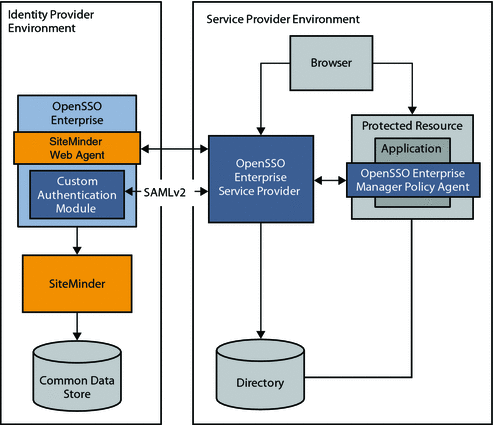
In this deployment, OpenSSO Enterprise provides federated single sign-on among enterprise applications in partner environments, while SiteMinder continues to provide authentication. The following two figures illustrates a typical transaction flow.
Figure 2–4 Process Flow for SiteMinder Federation in the Identity Provider Environment
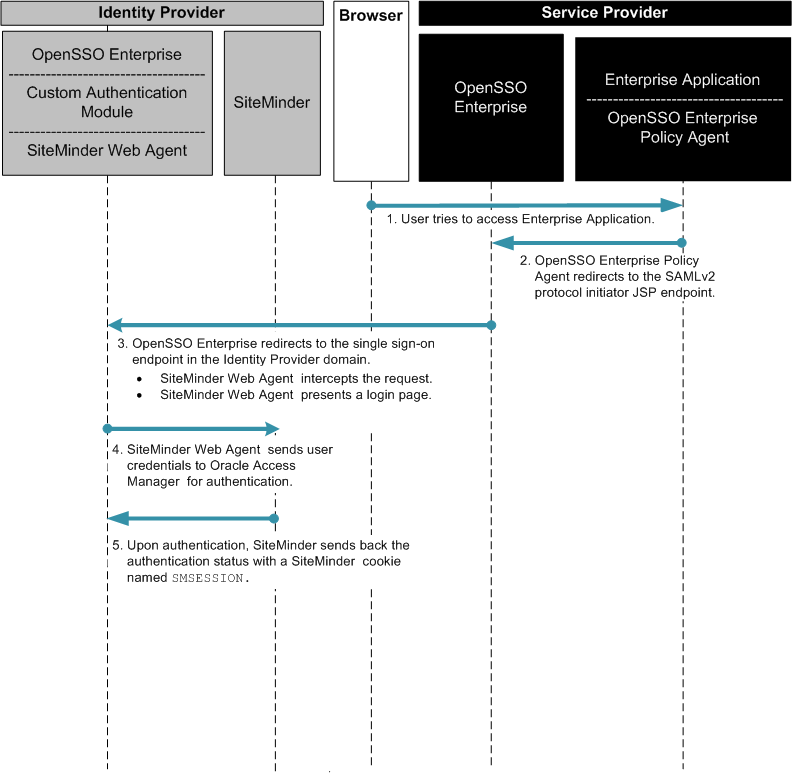
Figure 2–5 Process Flow for SiteMinder Federation in the Identity Provider Environment (continued)
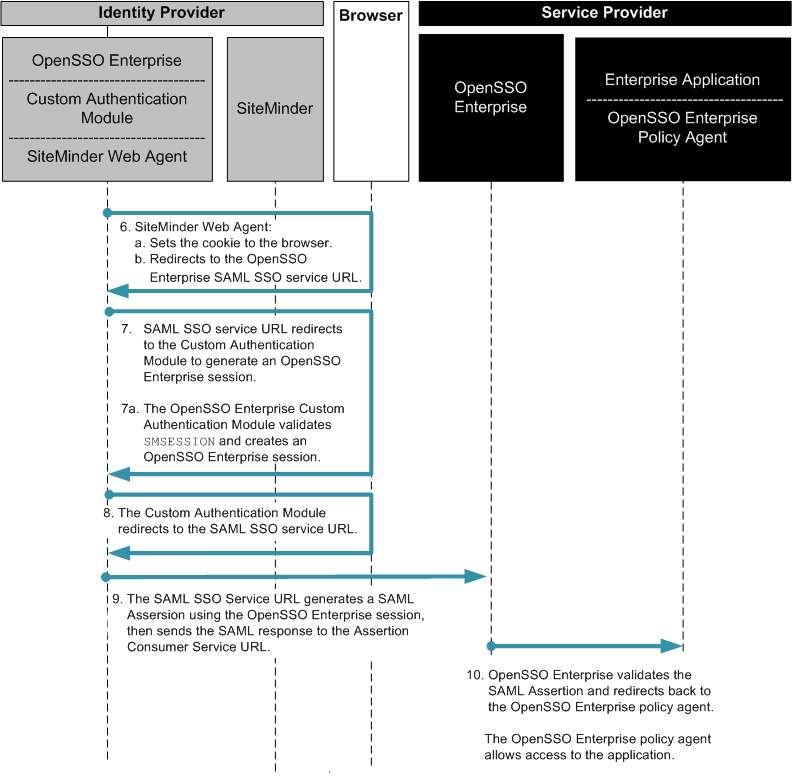
Federated Single Sign-On Use Case in the Service Provider Environment
In this use case, the company uses SiteMinder in the Service Provider environment to protect legacy applications. OpenSSO Enterprise is installed to invoke Federation protocols. The OpenSSO Enterprise server includes a customized authentication module for handling SiteMinder sessions. A SiteMinder Web Agent is installed on the same OpenSSO Enterprise instance to protect OpenSSO Enterprise.
Figure 2–6 SiteMinder Federation in a Service Provider Environment
This use case includes two additional, lightweight components:
- Custom Authentication Module (spAdapter)
-
This is an OpenSSO Enterprise SAMLv2 plug-in that processes operations after federated single sign-on login is completed and before the target URL is displayed. After the OpenSSO Enterprise session is established, the spAdapter plug-in uses the OpenSSO Enterprise session to communicate with the SiteMinder Custom Authentication Scheme.
- Custom Authentication Scheme
-
This is a SiteMinder SAMLv2 plug-in. It uses the OpenSSO Enterprise configuration defined in the SAMLv2 metadata and the SAMLv2 session to generate a SiteMinder session.
When an access request comes from a partner application, the SiteMinder login page is displayed. If the user has already been authenticated, the OpenSSO Enterprise custom authentication module creates a session for the user. The custom authentication module consumes the SiteMinder session, and then generates a SAML assertion. The following two figures illustrate the steps in the single sign-on flow:
Figure 2–7 Process Flow for SiteMinder Federation in the Service Provider Environment
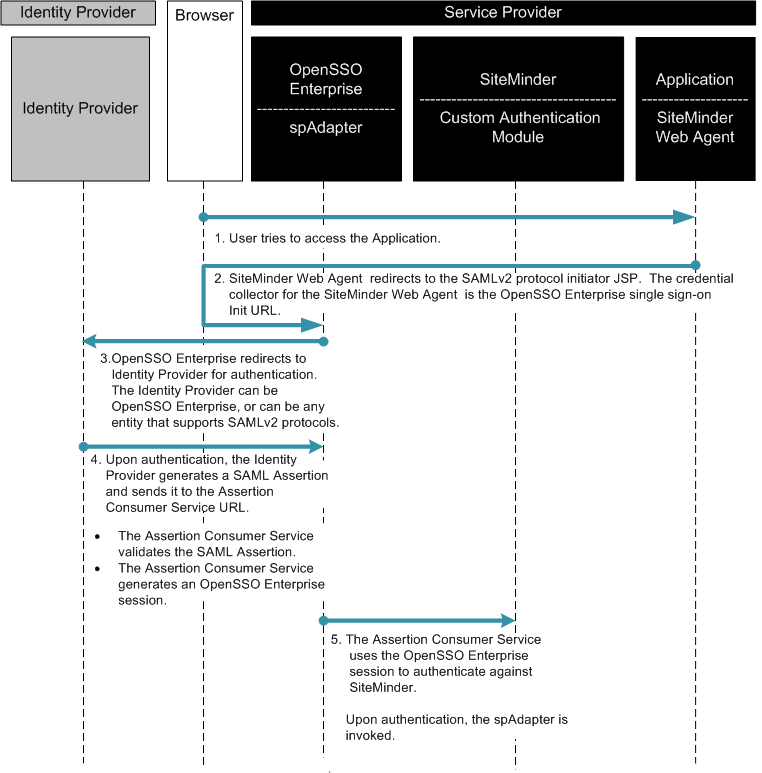
Figure 2–8 Process Flow for SiteMinder Federation in the Service Provider Environment (continued)
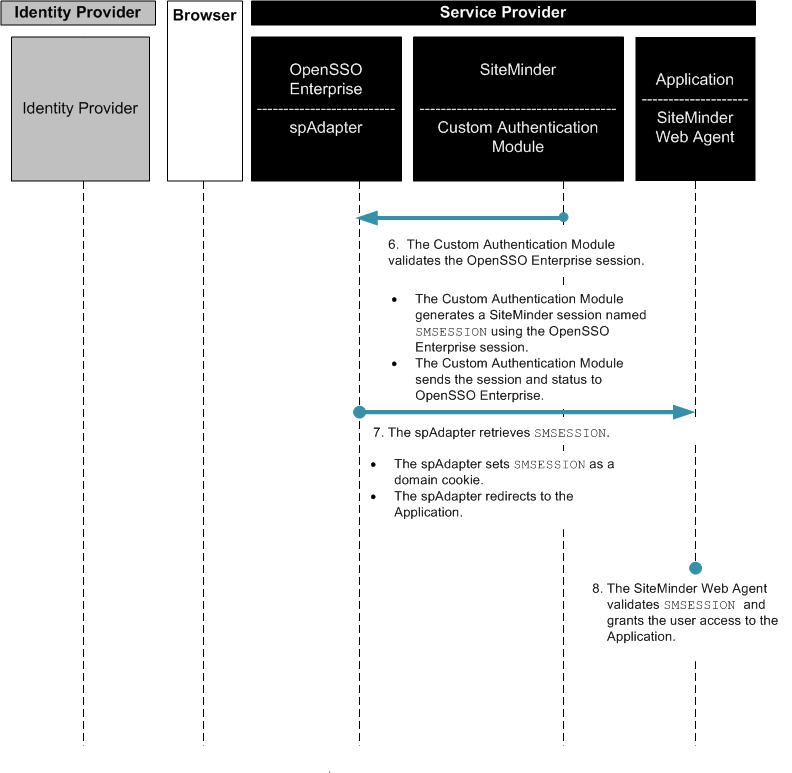
Installing SiteMinder
The use cases in this chapter describe Sun OpenSSO Enterprise 8.0 integrated with CA SiteMinder Server 6.0 Service Provider 5. Both products are installed on the Solaris operating system. Sun Web Server 6.1 SP5 is installed to serve the SiteMinder HTTP administrative interface. Sun Directory Server 6.3 is installed for its user data store and its configuration data store. Use these general instructions to install SiteMinder in any of the use cases discussed later in the chapter.
-
Install CA SiteMinder Access Manager.
You must have a licensed copy of CA SiteMinder to access its product documentation. See the product web page at http://www.ca.com/us/products/product.aspx?id=5262.
-
Install Sun Web Server 6.1 SP5.
See the product documentation at Sun Java System Web Server 6.1 2005Q4 SP5 Release Notes.
-
Install Directory Server 6.3.
See the product documentation at Sun Java System Directory Server Enterprise Edition 6.3 Release Notes.
Configuring SiteMinder After Installation
Use these general instructions after installing SiteMinder in any of the use cases discussed later in the chapter. To configure SiteMinder, follow these steps:
 To Log In to SiteMinder
To Log In to SiteMinder
-
Go to the following URL:
http://hostname:portnumber/SiteMinder
-
On the SiteMinder Policy Server administration console, click “Administer Policy Server. ”
-
In the Policy Server login page, log in using the following credentials:
- User Name:
-
SiteMinder
- Password:
-
password
Creating a Sample User
Create a sample user in the SiteMinder Directory Server. In this use case, the new user is named test. You can base the name of this user on the attributes you use with SiteMinder. By default, Directory Server uses the uid naming attribute for the user.
 To Create a SiteMinder Web Agent Configuration
To Create a SiteMinder Web Agent Configuration
-
In SiteMinder, create a host configuration object.
In this example, the host configuration object is named host1-agent.
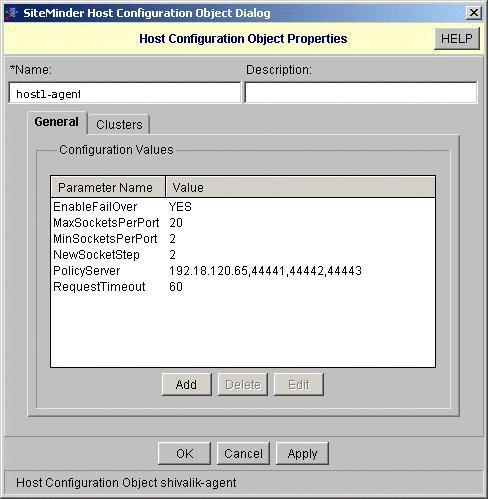
-
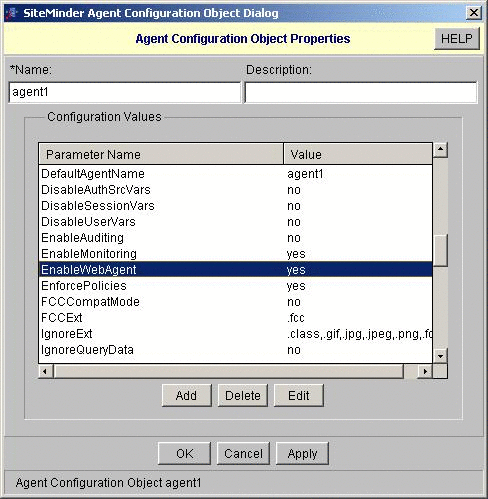
Create a web policy agent, and then create an appropriate Agent Configuration Object for the policy agent.
In this example, the Agent Configuration Object is named agent1.
 To Create and Configure the User Directory
To Create and Configure the User Directory
-
Create a user directory.
In this example, the user directory is named localds.
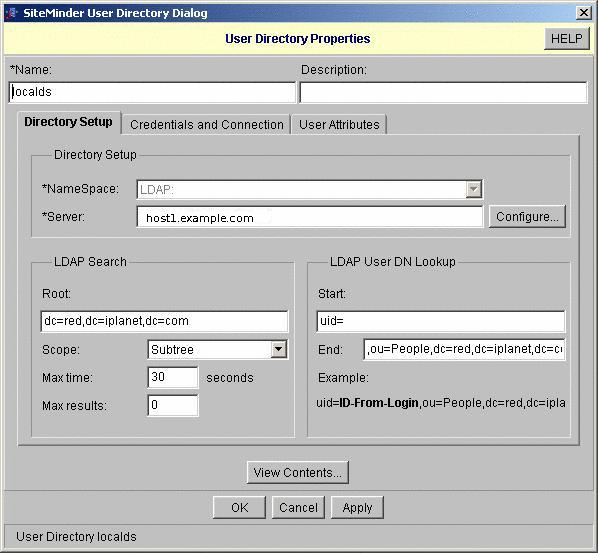
-
Create a domain.
In this example, the domain is named test domain. Under User Directories, specify localds.
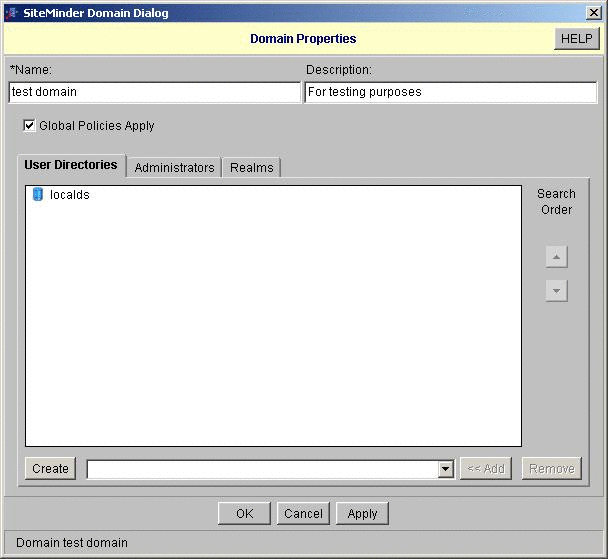
-
Create a realm.
In this example, the new realm is named resource1.
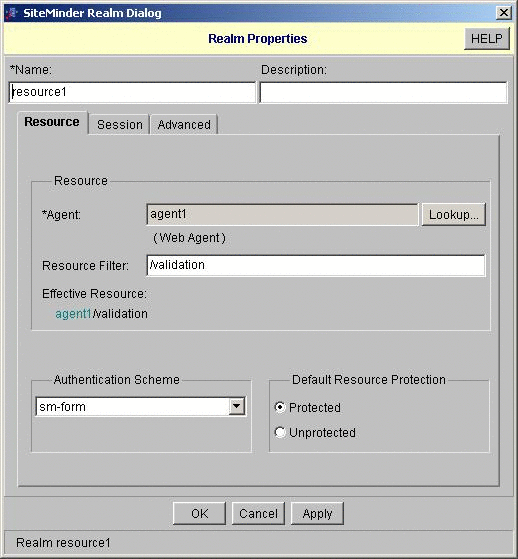
Creating and Configuring a Form-Based Authentication Scheme
In SiteMinder, create a form authentication scheme, and then create a configuration for the authentication scheme.
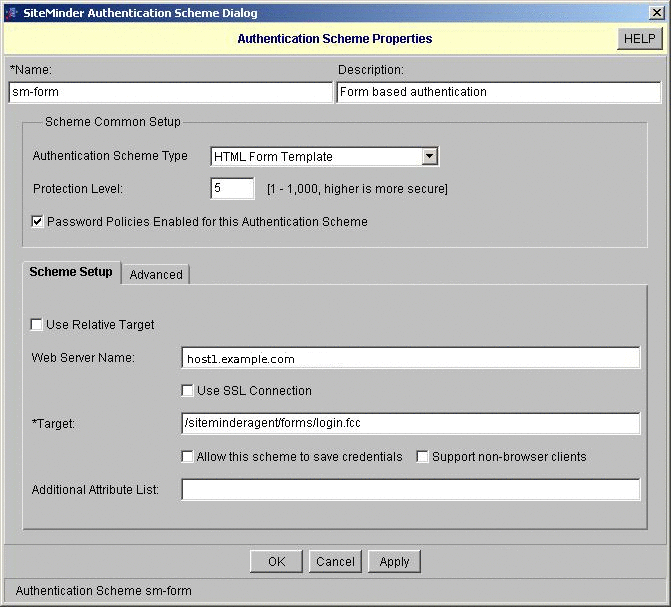
 To Create a Policy
To Create a Policy
-
Create a rule under the resource1 realm, and then configure the rule URLs.
In this example, the new rule is named rule1.
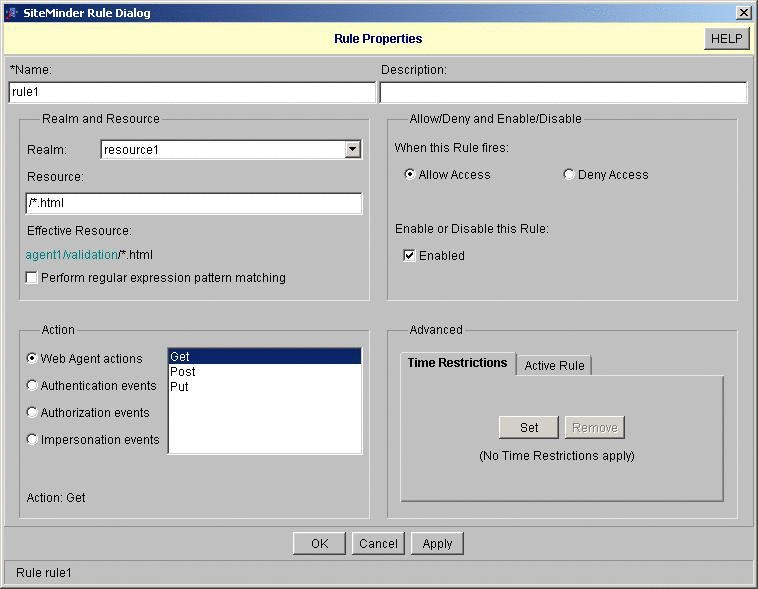
-
Create a policy.
In this example, the new policy is named policy1.
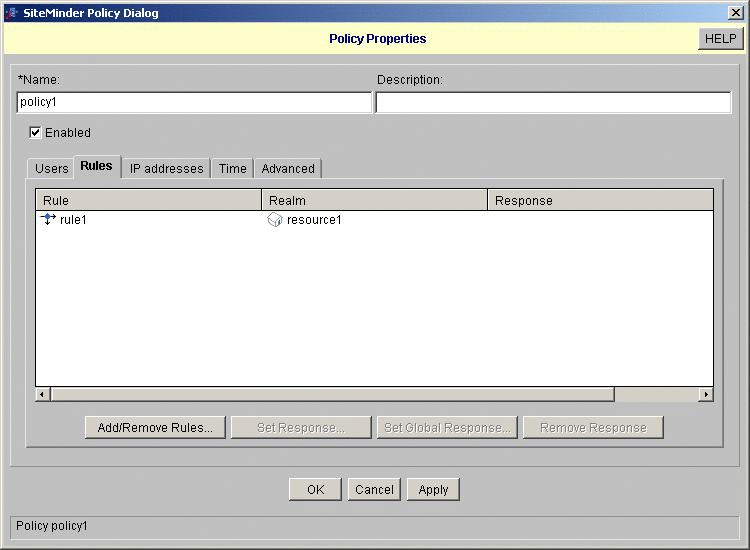
-
Assign the users and add the rules to the policy.
Using OpenSSO Enterprise to Enable SiteMinder Federation in an Identity Provider Environment
The following is a high-level overview of the sequence you must follow to enable SiteMinder with OpenSSO Enterprise in an Identity Provider Environment:
-
Configure the Identity Provider OpenSSO Enterprise to Use SAMLv2 Identity Provider Protocols.
-
Configure the SiteMinder Agent to Protect OpenSSO Enterprise URLs.
-
Install the OpenSSO Enterprise Policy Agent in the Service Provider.
 To Install the Principal Components
To Install the Principal Components
The following are the principal components in this use case:
-
OpenSSO Enterprise in the Identity Provider container
-
SiteMinder Web Agent
-
SiteMinder custom authentication module
-
OpenSSO Enterprise in the Service Provider container
Before You Begin
-
The Identity Provider and Service Provider should be in installed in different domains. If this is not possible, they should minimally use different cookie names or cookie domains.
-
You can defer the installation of OpenSSO Enterprise policy agent for protecting the OpenSSO Enterprise Service Provider until the end of the installation procedures. This gives you the opportunity to verify that the SAML2 setup is working before you proceed.
-
Before proceeding, be sure to read the general instructions in Installing SiteMinder and in Configuring SiteMinder After Installation. The following steps provide additional installation information specific only to this use case.
-
Install and configure OpenSSO Enterprise in the same container in which the Identity Provider is installed.
For detailed installation instructions, see the Sun OpenSSO Enterprise 8.0 Installation and Configuration Guide.
-
Be sure that the Identity Provider container supports SiteMinder Web Agent installation.
-
Configure OpenSSO Enterprise to use the same user repository as the SiteMinder user repository. This enables both OpenSSO Enterprise and SiteMinder to provide a single session for the same user.
-
-
Install and configure the SiteMinder Web Agent on the OpenSSO Enterprise container.
For now, configure the SiteMinder Web Agent to protect an arbitrary URL on the container. In this example, the protected URL is /validation/index.html.
-
As in the previous section, create a context root /validation, or create a directory named validation under the docroot.
-
Be sure that the SiteMinder form authentication scheme is working for the protected URL.
-
-
Install the SiteMinder custom authentication module in OpenSSO Enterprise.
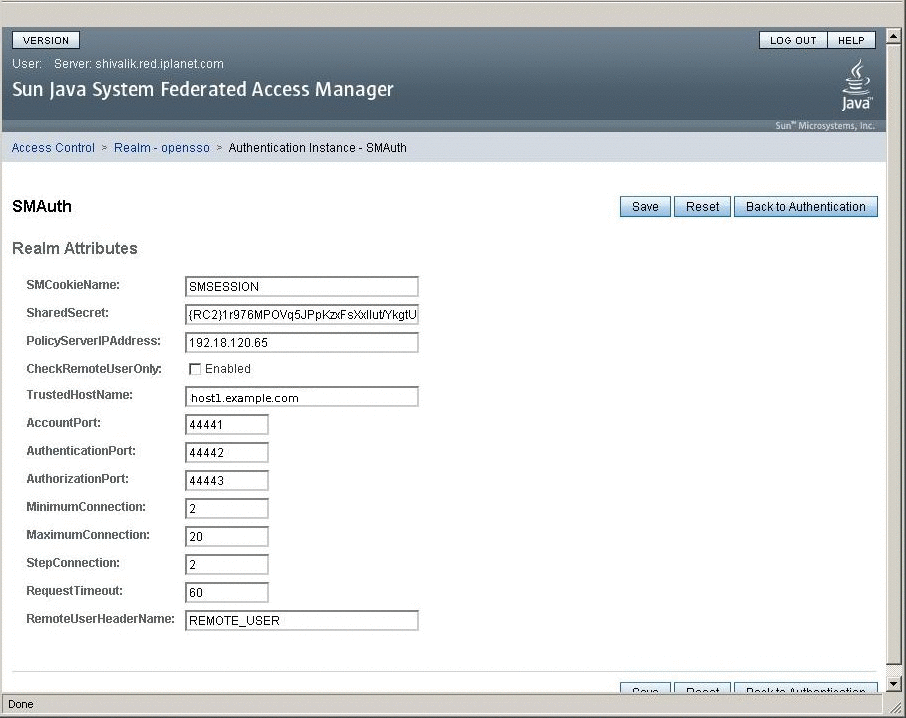
After you unzip the OpenSSO Enterprise binary, the SiteMinder custom authentication module is located under the directory unzip-directory/integrations/siteminder/. The README.html provides steps for building a custom authentication module. The following parameters must be set to enable the SiteMinder SDK to connect to the SiteMinder Policy Server:
- SMCookieName:
-
SiteMinder cookie name. The default name is SMSESSION.
- SharedSecret:
-
Unique policy agent configuration obtained from SiteMinder, and used by OpenSSO Enterprise to point to the SiteMinder SDK .
- PolicyServerIPAddress:
-
Indicates where the SiteMinder Policy Server is located.
- CheckRemoteUserOnly:
-
This attribute should be enabled when the SiteMinder Web Agent is installed on the same host as OpenSSO Enterprise. The SiteMinder Web Agent performs session validation. When this attribute is enabled, the rest of the configuration is not needed.
- TrustedHostName:
-
Name of the SiteMinder SDK host name.
- AccountPort
-
One of 3 TCP ports used by the SiteMinder Server to connect to the SiteMinder SDK.
- AuthenticationPort:
-
One of 3 TCP ports used by the SiteMinder Server to connect to the SiteMinder SDK.
- AuthorizationPort:
-
One of 3 TCP ports used by the SiteMinder Server to connect to the SiteMinder SDK.
- MinimumConnection:
-
In a connection pool implementation, the maximum number of concurrent connections that a can be opened.
- MaximumConnection:
-
In a connection pool implementation, the minimum number of concurrent connections that a can be opened.
- StepConnection:
-
In a connection pool implementation, the number of concurrent connections that can be opened.
- RequestTimeout:
-
Maximum time that the SiteMinder SDKwaits before it connects to SiteMinder Policy Server.
- RemoteUserHeaderName:
-
When configured, the SiteMinder Web Agent sets a header name for the remote user after successful authentication. This parameter is used only when the checkRemoteHeaderOnly flag is set. The SMAuth module uses this parameter to create an OpenSSO Enterprise session.
The following diagram shows an example of SiteMinder custom authentication module configuration.
-
Install and configure OpenSSO Enterprise in the container in which the Service Provider is installed.
For detailed installation instructions, see the OpenSSO Enterprise Installation and Configuration Guide.
-
Install the SiteMinder Web Agent in the OpenSSO Enterprise container.
See the SiteMinder product documentation.
 To Configure the Identity Provider OpenSSO
Enterprise to Use SAMLv2 Identity Provider Protocols
To Configure the Identity Provider OpenSSO
Enterprise to Use SAMLv2 Identity Provider Protocols
Before you can enable the SAMLv2 Identity Provider protocols, you must generate, customize, and load each of the following:
-
Identity Provider metadata
-
Identity Provider extended metadata
-
Service Provider metadata
-
Service Provider extended metadata.
Before You Begin
-
Read through the following instructions for the changes that you must make to the default metadata. The SAML2 samples contain instructions on how to setup SAML2.
-
You must import Identity Provider metadata and Identity Provider extended metadata as hosted metadata. You must import Service Provider metadata and Service Provider extended metadata as remote entity metadata. To change a configuration from the default hosted to remote, modify the extended metadata XML element <EntityConfig>. Change the default attribute hosted=true to hosted=false.
-
See the OpenSSO Enterprise product documentation for commands and syntax.
-
Generate the metadata templates in both Identity Provider and Service Provider environments.
Use thefamadm command. You can also use the browser-based interface at the following URL:
http:host:port/opensso/famadm.jsp
-
At Identity Provider :
famadm create-metadata-templ -y idp_entity_id -u amadmin -f admin_password_file_name -m idp_standard_metadata -x idp_extended_metadata -i idp_meta_aliaswhere idp_meta_alias is /idp
-
At Service Provider:
famadm create-metadata-templ -y sp_entity_id -u amadmin -f admin_password_file_name -m sp_standard_metadata -x sp_extended_metadata -s sp_meta_aliaswhere sp_meta_alias is /sp
-
-
Customize Identity Provider and Service Provider extended metadata.
The Identity Provider extended metadata should be added as an attribute named AuthUrl. This URL attribute is used by the SAML protocols to redirect for authentication purposes. In the following example, AuthUrlredirects to the SiteMinder authentication module.
<Attribute name="AuthUrl"> <Value>http://host:port/opensso/UI/Login?module=SMAuth</Value> </Attribute>Another option is to make the SiteMinder custom authentication module the default login module in OpenSSO Enterprise. The cost of using this option is that you must specify an LDAP login module for logging in as an administrator.
The Service Provider extended metadata uses the attribute named transientUser. Set this value to your anonymous user:
<Attribute name="transientUser"> <Value>anonymous</Value> </Attribute> -
Load the Identity Provider and Service Provider metadata.
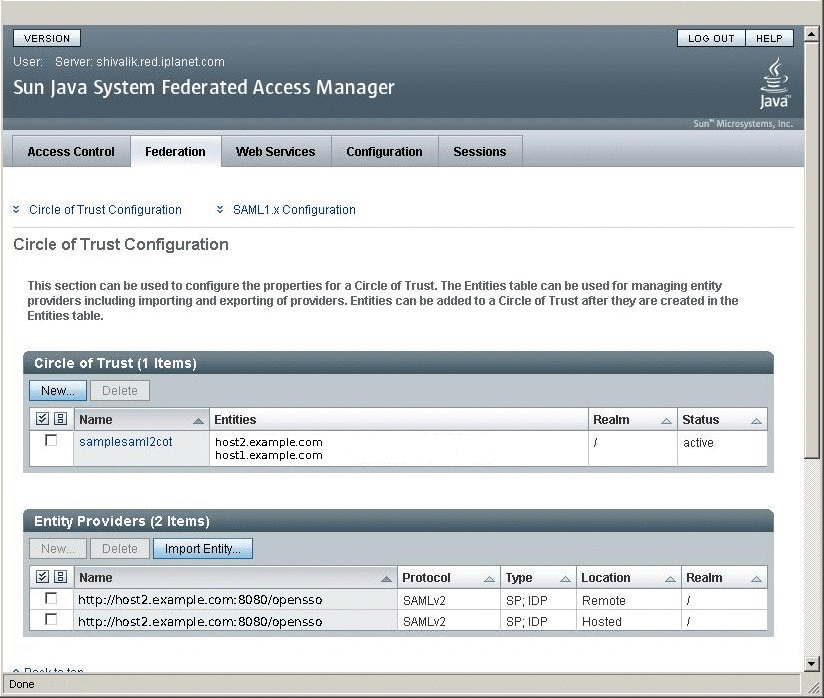
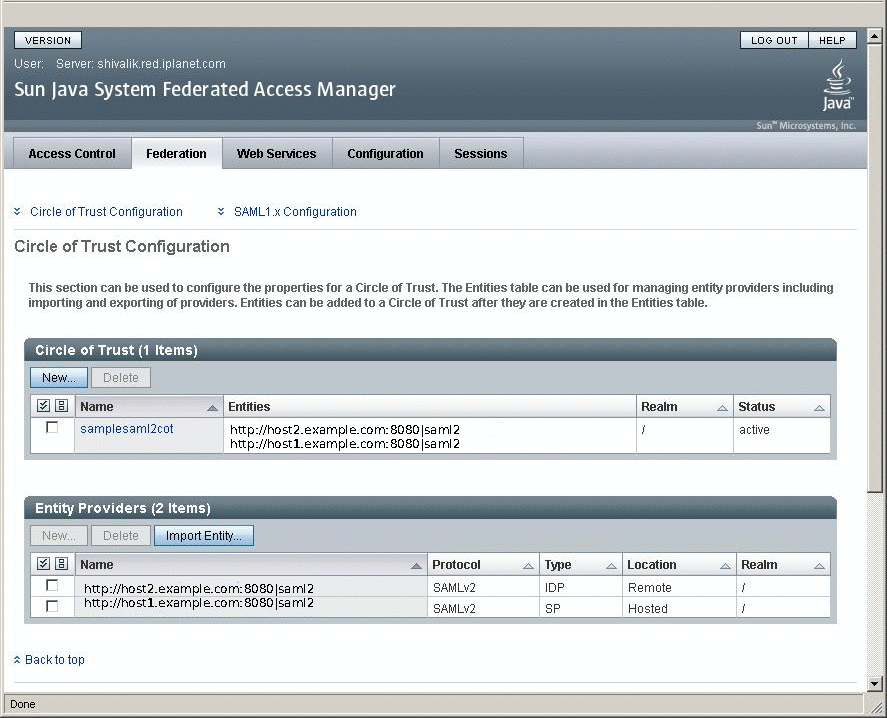
First create a Circle of Trust as mentioned in the URL. The Circle of Trust should also be added in the extended metadata.
In your extended template files, you will see a sample Circle of Trust. Modify the sample to create your Circle of Trust.
<Attribute name="cotlist"> <Value>samplesaml2cot</Value> </Attribute>Load the hosted metadata in both the Identity Provider and the Service Provider using the famadm command or through OpenSSO Enterprise administration console.
-
Exchange the metadata Service Provider with the Identity Provider metadata.
-
Exchange the Identity Provider metadata with the Service Provider.
-
Load all metadata.
-
After successful metadata exchange, verify through the OpenSSO Enterprise administration console that SAMLv2 is working properly.
The following shows a sample UI for SAMLv2 configuration.
 To Configure the SiteMinder Agent to Protect
OpenSSO Enterprise URLs
To Configure the SiteMinder Agent to Protect
OpenSSO Enterprise URLs
This configuration protects the SAML Single Sign-On Service URL so that the SiteMinder session must be established before the SAML assertion is generated.
-
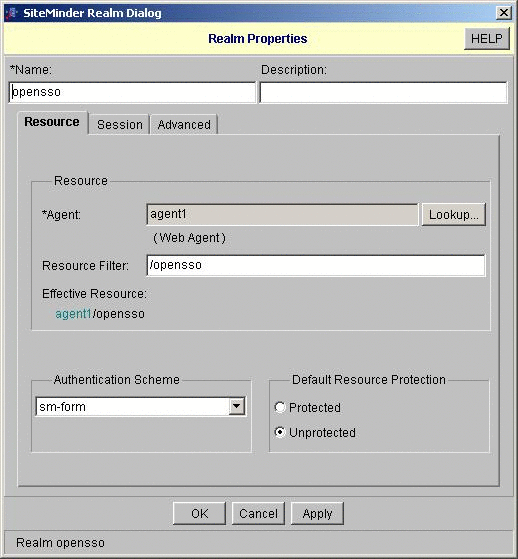
In the SiteMinder administration console, create a new realm in unprotected mode.
In this example, the realm is named opensso.
-
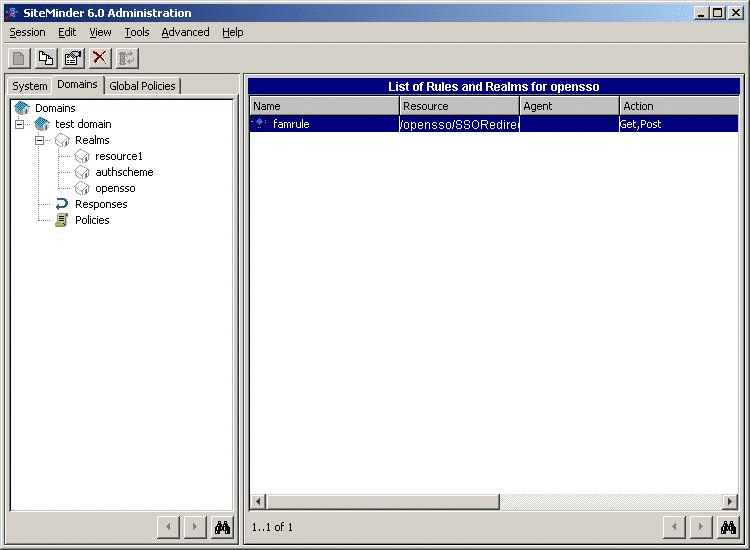
Create a rule that protects only the SAML2 SSO URL.
Other URLs are unprotected for now.
Installing the OpenSSO Enterprise Policy Agent
The policy agent must be supported on the container where the enterprise application is deployed. For detailed installation information, see the policy agent documentation.
Change the policy agent login URL to the OpenSSO Enterprise SAML2 Service Provider-initiated Single Sign-on Service URL. Example:
http://<sphost>:<spport>/opensso/saml2/jsp/spSSOInit.jsp?metaAlias=<Service Provider MetaAlias> &idpEntityID=<Identity Provider Entity ID>&NameIDFormat=transient
 To Verify that Single Sign-On is Working Properly
To Verify that Single Sign-On is Working Properly
-
Authenticate at the SiteMinder login page using user name and password.
-
Access the enterprise application in the Service Provider environment.
The enterprise application is protected by OpenSSO Enterprise Service Provider Agent. The agent should allow access to the application.
Sample Identity Provider Interactions
1. Access the SM Agent protected application
http://HostName.example.com:9898/validation/index.html GET /validation/index.html HTTP/1.1 Host: HostName.example.com:9898 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.8.1.11) Gecko/20071127 Firefox/2.0.0.11 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q=0.9, text/plain;q=0.8,image/png,*/*;q=0.5 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 300 Connection: keep-alive HTTP/1.x 302 Moved Temporarily Server: Netscape-Enterprise/6.0 Date: Fri, 01 Feb 2008 23:46:12 GMT Cache-Control: no-cache Location: http://HostName.example.com:9898/SiteMinderagent/forms/ login.fcc?TYPE=33554433&REALMOID=06-1716e557-15f3-100f-b9a4-835cc8200cb3&GUID= &SMAUTHREASON=0&METHOD=GET&SMAGENTNAME=$SM$sHjbzl4f9R%2bcSa0%2fEgnu6oUQQPMQnUg kU6Zvx5zWZpQ%3d&TARGET=$SM$http%3a%2f%2fshivalik%2ered%2eiplanet%2ecom%3a9898% 2fvalidation%2findex%2ehtml Connection: close |
2. SiteMinder authentication
http://HostName.example.com:9898/SiteMinderagent/forms/login.fcc?TYPE= 33554433&REALMOID=06-1716e557-15f3-100f-b9a4-835cc8200cb3&GUID=&SMAUTHREASON= 0&METHOD=GET&SMAGENTNAME=$SM$sHjbzl4f9R%2bcSa0%2fEgnu6oUQQPMQnUgkU6Zvx5zWZpQ% 3d&TARGET=$SM$http%3a%2f%2fshivalik%2ered%2eiplanet%2ecom%3a9898%2fvalidation% 2findex%2ehtml GET /SiteMinderagent/forms/login.fcc?TYPE=33554433&REALMOID=06-1716e557-15f3- 100f-b9a4-835cc8200cb3&GUID=&SMAUTHREASON=0&METHOD=GET&SMAGENTNAME=$SM$sHjbzl4 f9R%2bcSa0%2fEgnu6oUQQPMQnUgkU6Zvx5zWZpQ%3d&TARGET=$SM$http%3a%2f%2fshivalik%2 ered%2eiplanet%2ecom%3a9898%2fvalidation%2findex%2ehtml HTTP/1.1 Host: HostName.example.com:9898 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.8.1.11) Gecko/20071127 Firefox/2.0.0.11 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q=0.9, text/plain;q=0.8,image/png,*/*;q=0.5 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 300 Connection: keep-alive HTTP/1.x 200 OK Server: Netscape-Enterprise/6.0 Date: Fri, 01 Feb 2008 23:46:12 GMT Content-Type: text/html; charset=ISO-8859-1 Connection: close ---------------------------------------------------------- http://HostName.example.com:9898/SiteMinderagent/forms/login.fcc?TYPE= 33554433&REALMOID=06-1716e557-15f3-100f-b9a4-835cc8200cb3&GUID=&SMAUTHREASON= 0&METHOD=GET&SMAGENTNAME=$SM$sHjbzl4f9R%2bcSa0%2fEgnu6oUQQPMQnUgkU6Zvx5zWZpQ% 3d&TARGET=$SM$http%3a%2f%2fshivalik%2ered%2eiplanet%2ecom%3a9898%2fvalidation% 2findex%2ehtml POST /SiteMinderagent/forms/login.fcc?TYPE=33554433&REALMOID=06-1716e557-15f3- 100f-b9a4-835cc8200cb3&GUID=&SMAUTHREASON=0&METHOD=GET&SMAGENTNAME=$SM$sHjbzl4 f9R%2bcSa0%2fEgnu6oUQQPMQnUgkU6Zvx5zWZpQ%3d&TARGET=$SM$http%3a%2f%2fshivalik% 2ered%2eiplanet%2ecom%3a9898%2fvalidation%2findex%2ehtml HTTP/1.1 Host: HostName.example.com:9898 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.8.1.11) Gecko/20071127 Firefox/2.0.0.11 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q=0.9, text/plain;q=0.8,image/png,*/*;q=0.5 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 300 Connection: keep-alive Referer: http://HostName.example.com:9898/SiteMinderagent/forms/ login.fcc?TYPE=33554433&REALMOID=06-1716e557-15f3-100f-b9a4-835cc8200cb3& GUID=&SMAUTHREASON=0&METHOD=GET&SMAGENTNAME=$SM$sHjbzl4f9R%2bcSa0% 2fEgnu6oUQQPMQnUgkU6Zvx5zWZpQ%3d&TARGET=$SM$http%3a%2f%2fshivalik%2ered% 2eiplanet%2ecom%3a9898%2fvalidation%2findex%2ehtml Content-Type: application/x-www-form-urlencoded Content-Length: 233 SMENC=ISO-8859-1&SMLOCALE=US-EN&USER=test&PASSWORD=test&target=http% 3A%2F%2FHostName.example.com%3A9898%2Fvalidation% 2Findex.html&smauthreason=0&smagentname=sHjbzl4f9R%2BcSa0% 2FEgnu6oUQQPMQnUgkU6Zvx5zWZpQ%3D&postpreservationdata= HTTP/1.x 302 Moved Temporarily Server: Netscape-Enterprise/6.0 Date: Fri, 01 Feb 2008 23:46:18 GMT Content-Type: magnus-internal/fcc Set-Cookie: SMSESSION=2xm2Iw6fTMBcjA6rlK/YUY1CRBudYxwOCkfpCo95YKAp2b4ZzLOPT qi2S14CQ7nRja+fUq53Aj0pmTxDvPKTMcKD1Ql1hGx0gPK7xx2eqMP3IyTAK3qNahRgt7mQRTIB BDEE0rOJcpgrMRtsteC90yMdiJrrEeqfC38utU6mxO9BejwjRuGN2rmf9WM4Odl+4TE0iUOiP/k iCR6sn2r03GBsbBjOi12oSlh/4JAyfOwxsgBJCwDiZVlFXNiKNaKdY1UQr8OcKeO33eNn3w9RW9 ZrjRibQTQcxxmiR+gsvAuM8etEzP6GCFKjc1s8I3DNuSBbDqfyt81YUSYdEYa9UKfvvOJplZOIT BkQajcAEPOq+vTYxQ4BH2RmjdPMVcIxRm2bibM9QtuQD83C9QubTk1lq4j+ywPsvutiYEoGHV+7 6VXws5NsvhK2gH4ZTC0xsd76X2/1no8xMv9c3W4DcSp9cQQ74/7+a7gzT+hxQSpyQFf4mDTnq/D XS5V7tcLS0EyFcf8RwSbvDPnICiebR3vtZgHRL1kEZheEh9ToHmwqIO9cCqz9rJXR7/NL+o/AQr 7M4o+LyA7KxozAueUj0pg8GINteUGVxMLWmR7Xm/Lp0pI9DjM5mfbmP8Ka+w0T6H9LHNlQGaYZA PCkeABAXqLb8q8yJUzPdI0BVlp1awNCx579DereoCIzCZdQ99rVDSQUS77KCQATnYXrHqTxqbXxW beDf6gk9ZCf29XTzO8hBLdScqGOBX1OvDvzdghcjHnupQf1fYltt/3MrZ/Jrxonbpgxg4C5zVgSU PrNqb66RYWQOelZXooh7lTPoFHsMFodVnecsOZmEMXNI8DB08pyo5KhRZJk2Mr4o3rPNtiHPpnXc d+imapuosG3FwF5Sv6flh8jbiE9/MZdIQ06hgWEIiCnUEYdboli4TWgy0/QpCbdJ7OviU275VZiC W6hMTRyrxnEvoQ=; path=/; domain=.red.example.com Cache-Control: no-cache Location: http://HostName.example.com:9898/validation/index.html Connection: close ---------------------------------------------------------- http://HostName.example.com:9898/validation/index.html GET /validation/index.html HTTP/1.1 Host: HostName.example.com:9898 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.8.1.11) Gecko/20071127 Firefox/2.0.0.11 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q=0.9, text/plain;q=0.8,image/png,*/*;q=0.5 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 300 Connection: keep-alive Referer: http://HostName.example.com:9898/SiteMinderagent/forms/ login.fcc?TYPE=33554433&REALMOID=06-1716e557-15f3-100f-b9a4-835cc8200cb3&GUID= &SMAUTHREASON=0&METHOD=GET&SMAGENTNAME=$SM$sHjbzl4f9R%2bcSa0%2fEgnu6oUQQPMQnUg kU6Zvx5zWZpQ%3d&TARGET=$SM$http%3a%2f%2fshivalik%2ered%2eiplanet%2ecom%3a9898% 2fvalidation%2findex%2ehtml Cookie: SMSESSION=2xm2Iw6fTMBcjA6rlK/YUY1CRBudYxwOCkfpCo95YKAp2b4ZzLOPTqi2S14 CQ7nRja+fUq53Aj0pmTxDvPKTMcKD1Ql1hGx0gPK7xx2eqMP3IyTAK3qNahRgt7mQRTIBBDEE0rOJ cpgrMRtsteC90yMdiJrrEeqfC38utU6mxO9BejwjRuGN2rmf9WM4Odl+4TE0iUOiP/kiCR6sn2r03 GBsbBjOi12oSlh/4JAyfOwxsgBJCwDiZVlFXNiKNaKdY1UQr8OcKeO33eNn3w9RW9ZrjRibQTQcxx miR+gsvAuM8etEzP6GCFKjc1s8I3DNuSBbDqfyt81YUSYdEYa9UKfvvOJplZOITBkQajcAEPOq+vT YxQ4BH2RmjdPMVcIxRm2bibM9QtuQD83C9QubTk1lq4j+ywPsvutiYEoGHV+76VXws5NsvhK2gH4Z TC0xsd76X2/1no8xMv9c3W4DcSp9cQQ74/7+a7gzT+hxQSpyQFf4mDTnq/DXS5V7tcLS0EyFcf8Rw SbvDPnICiebR3vtZgHRL1kEZheEh9ToHmwqIO9cCqz9rJXR7/NL+o/AQr7M4o+LyA7KxozAueUj0p g8GINteUGVxMLWmR7Xm/Lp0pI9DjM5mfbmP8Ka+w0T6H9LHNlQGaYZAPCkeABAXqLb8q8yJUzPdI0 BVlp1awNCx579DereoCIzCZdQ99rVDSQUS77KCQATnYXrHqTxqbXxWbeDf6gk9ZCf29XTzO8hBLdS cqGOBX1OvDvzdghcjHnupQf1fYltt/3MrZ/Jrxonbpgxg4C5zVgSUPrNqb66RYWQOelZXooh7lTPo FHsMFodVnecsOZmEMXNI8DB08pyo5KhRZJk2Mr4o3rPNtiHPpnXcd+imapuosG3FwF5Sv6flh8jbi E9/MZdIQ06hgWEIiCnUEYdboli4TWgy0/QpCbdJ7OviU275VZiCW6hMTRyrxnEvoQ= HTTP/1.x 200 OK Server: Netscape-Enterprise/6.0 Date: Fri, 01 Feb 2008 23:46:18 GMT Set-Cookie: SMSESSION=jlO0TgMQfglpU+GHQCJqbnoE2Pevax6fdzPGU7ZAgJuPb/fxTjCbWX1 B1RO6QaLJn6VoVGNK8Sy6IeILAyv+LciS/OMK1E0tSXnL5Uvit3XIuWuiSMuklyDMIlOQ6n3ZSGGr 9sKBUch5YVfGcfGjHQFcBIlzegQxBRrgH/l2rc8aTEHdCrprvBiRHwQlxJbrcWMqfJw7h+HUEtiz9 bQCUkwMbpEW4eBfNyRlZTGov3K5hg4HK4tuoyvOeKdZaewlTB4Lm+QeGWo2qv2mPDP+eVtBiVtRVH HTHGfSthTJYQOOc4rPV2dnl8axpWppGByeUmfmeService Provider9x5hVxDi91iyobTybKpDz0 bltkvnHbqwbLfehUPtJFxS3Z54y9dmiuoQ+B5Kdrs7DNuvrnAI1ZQdDKQEVA4Pt+vA9KO18ah9V1I 7BZ9D/x60uWxfaA3Ty8lRgWhMYqdBulFMD1B29sxboNHWdJ2FaxQJGjMpSEZ5iHB50ovF4YFXRyPP 5Tl7eJxIebLKX02LFrG/osNZ9UKHrMY1MRK5WWHJlYB040ADVcTNrFkc39vcYIA1eGDYhC/NaOd41 2HP5S0UX0/59ADMLBsX/qBjcdODy3li+4eZnK1oHw/9yr3LCjewJ+H9w0k0/dQw99vgwEM2RPFgH5 Y7W6k6h1efp67VKXLBiJ1OZPJe2SCEDAOUla8qsC8fQ0VWTy/TfVhVtqJOaSLZrACX7uhPzbZE1EA Pd8x7UeJquFll3WpdnZYObd0DQLeoWZcF2rPIcfBn+8X8oig5KzvAgQ9R8MR+h7OkYfhmwwBDaQkb KPpIxjpeLNxKpkEVWJ9HoHOpZ/txCQUAHqPV41YjZ6CQfBfUqdOHbfje9O+0pJ1aHMntI4VYZOqdx sA+n9cgKjNQ8ruHOqSKhAQfEgipwcM2fMU3Uqmtr+0/+5bi7Cbs=; path=/; domain=.red.example.com Content-Type: text/html Etag: "dcea10a4-1-0-88" Last-Modified: Thu, 10 Jan 2008 01:42:07 GMT Content-Length: 136 Accept-Ranges: bytes ---------------------------------------------------------- |
3. SAML Service Provider SSO initiation
http://ide-13.red.example.com:8080/opensso/saml2/jsp/spSSOInit.jsp? metaAlias=/sp&idpEntityID= http://HostName.example.com:8080/opensso&NameIDFormat=transient GET /opensso/saml2/jsp/spSSOInit.jsp?metaAlias=/sp&idpEntityID= http://HostName.example.com:8080/opensso&NameIDFormat=transient HTTP/1.1 Host: ide-13.red.example.com:8080 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.8.1.11) Gecko/20071127 Firefox/2.0.0.11 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q=0.9, text/plain;q=0.8,image/png,*/*;q=0.5 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 300 Connection: keep-alive Cookie: SMSESSION=jlO0TgMQfglpU+GHQCJqbnoE2Pevax6fdzPGU7ZAgJuPb/fxTj CbWX1B1RO6QaLJn6VoVGNK8Sy6IeILAyv+LciS/OMK1E0tSXnL5Uvit3XIuWuiSMukly DMIlOQ6n3ZSGGr9sKBUch5YVfGcfGjHQFcBIlzegQxBRrgH/l2rc8aTEHdCrprvBiRHw QlxJbrcWMqfJw7h+HUEtiz9bQCUkwMbpEW4eBfNyRlZTGov3K5hg4HK4tuoyvOeKdZae wlTB4Lm+QeGWo2qv2mPDP+eVtBiVtRVHHTHGfSthTJYQOOc4rPV2dnl8axpWppGByeUm fmeService Provider9x5hVxDi91iyobTybKpDz0bltkvnHbqwbLfehUPtJFxS3Z54y9 dmiuoQ+B5Kdrs7DNuvrnAI1ZQdDKQEVA4Pt+vA9KO18ah9V1I7BZ9D/x60uWxfaA3Ty8l RgWhMYqdBulFMD1B29sxboNHWdJ2FaxQJGjMpSEZ5iHB50ovF4YFXRyPP5Tl7eJxIebLK X02LFrG/osNZ9UKHrMY1MRK5WWHJlYB040ADVcTNrFkc39vcYIA1eGDYhC/NaOd412HP5 S0UX0/59ADMLBsX/qBjcdODy3li+4eZnK1oHw/9yr3LCjewJ+H9w0k0/dQw99vgwEM2RP FgH5Y7W6k6h1efp67VKXLBiJ1OZPJe2SCEDAOUla8qsC8fQ0VWTy/TfVhVtqJOaSLZrAC X7uhPzbZE1EAPd8x7UeJquFll3WpdnZYObd0DQLeoWZcF2rPIcfBn+8X8oig5KzvAgQ9R8 MR+h7OkYfhmwwBDaQkbKPpIxjpeLNxKpkEVWJ9HoHOpZ/txCQUAHqPV41YjZ6CQfBfUqd OHbfje9O+0pJ1aHMntI4VYZOqdxsA+n9cgKjNQ8ruHOqSKhAQfEgipwcM2fMU3Uqmtr+0 /+5bi7Cbs= HTTP/1.x 302 Moved Temporarily X-Powered-By: JService Provider/2.1 Server: Sun Java System Application Server 9.1 Set-Cookie: JSESSIONID=765d4c266461607b4b55811d34ca; Path=/opensso Location: http://HostName.example.com:8080/opensso/SSORedirect/ metaAlias/idp?SAMLRequest=nVTNjtowEL7vU0S%2BQ5ywXcACJAqqirRtKbA99Gac SbHq2KlnwtK3rx1YRNUV2nIdj2e%2BP3uEsjK1mDa0syv41QBSkhwqY1G0J2PWeCucRI 3CygpQkBLr6adHkXe5qL0jp5xhd4v5mGHeH%2BYPSvF8ONxu4aHkWZaDLPpl2Rts%2B8 PBu16ewZDfK5Z8A4%2Fa2TELY1iyQGxgYZGkpVDifNDheYdnm7wn7vuix7%2BzZB6gaS upvbUjqkWa4k7vpdE%2Fux6Krq6NtEBd5Sox4AOeuhosokvX6y8rKLQHRWkFJKdGS0x1 UbPkg%2FMKWvJjVkqDELEsJaLew7myPLF8r22h7Y%2FrkmyPTSg%2BbjbLztSTLqUilk wRwUfwM2exqcCvwe%2B1gqfV45mOLqCT9a6Tebl%2BwQRrNrkbRbtEK6S%2FMPA6WPkC ik3eDmGUXqw6La7F5zB8MV86o9XvWxIUragkXe%2BOFV10yrZVkJcWNdig7noZ939tQh hKDf5%2FFA3WGOOeZx4kBc%2FJN8AmR45%2FszpTPb0TKNrgBEMIDnQL5Zmrauk1xkTD IcZkcrTxcvDMBJdWUN5i6tU2JVQcHcox8M%2FOFzHo4ZFAsYnK1s7TyevX8Jw1elWOIF b679cy%2BQM%3D Content-Type: text/html;charset=ISO-8859-1 Content-Length: 0 Date: Fri, 01 Feb 2008 23:47:30 GMT ---------------------------------------------------------- http://HostName.example.com:8080/opensso/SSORedirect/metaAlias/ idp?SAMLRequest=nVTNjtowEL7vU0S%2BQ5ywXcACJAqqirRtKbA99GacSbHq2Klnw tK3rx1YRNUV2nIdj2e%2BP3uEsjK1mDa0syv41QBSkhwqY1G0J2PWeCucRI3CygpQkB Lr6adHkXe5qL0jp5xhd4v5mGHeH%2BYPSvF8ONxu4aHkWZaDLPpl2Rts%2B8PBu16ew ZDfK5Z8A4%2Fa2TELY1iyQGxgYZGkpVDifNDheYdnm7wn7vuix7%2BzZB6gaSupvbUj qkWa4k7vpdE%2Fux6Krq6NtEBd5Sox4AOeuhosokvX6y8rKLQHRWkFJKdGS0x1UbPkg %2FMKWvJjVkqDELEsJaLew7myPLF8r22h7Y%2FrkmyPTSg%2BbjbLztSTLqUilkwRwU fwM2exqcCvwe%2B1gqfV45mOLqCT9a6Tebl%2BwQRrNrkbRbtEK6S%2FMPA6WPkCik3 eDmGUXqw6La7F5zB8MV86o9XvWxIUragkXe%2BOFV10yrZVkJcWNdig7noZ939tQhhK Df5%2FFA3WGOOeZx4kBc%2FJN8AmR45%2FszpTPb0TKNrgBEMIDnQL5Zmrauk1xkTDI cZkcrTxcvDMBJdWUN5i6tU2JVQcHcox8M%2FOFzHo4ZFAsYnK1s7TyevX8Jw1elWOIF b679cy%2BQM%3D GET /opensso/SSORedirect/metaAlias/idp?SAMLRequest=nVTNjtowEL7vU0S%2 BQ5ywXcACJAqqirRtKbA99GacSbHq2KlnwtK3rx1YRNUV2nIdj2e%2BP3uEsjK1mDa0s yv41QBSkhwqY1G0J2PWeCucRI3CygpQkBLr6adHkXe5qL0jp5xhd4v5mGHeH%2BYPSvF 8ONxu4aHkWZaDLPpl2Rts%2B8PBu16ewZDfK5Z8A4%2Fa2TELY1iyQGxgYZGkpVDifND heYdnm7wn7vuix7%2BzZB6gaSupvbUjqkWa4k7vpdE%2Fux6Krq6NtEBd5Sox4AOeuho sokvX6y8rKLQHRWkFJKdGS0x1UbPkg%2FMKWvJjVkqDELEsJaLew7myPLF8r22h7Y%2F rkmyPTSg%2BbjbLztSTLqUilkwRwUfwM2exqcCvwe%2B1gqfV45mOLqCT9a6Tebl%2Bw QRrNrkbRbtEK6S%2FMPA6WPkCik3eDmGUXqw6La7F5zB8MV86o9XvWxIUragkXe%2BOF V10yrZVkJcWNdig7noZ939tQhhKDf5%2FFA3WGOOeZx4kBc%2FJN8AmR45%2FszpTPb0 TKNrgBEMIDnQL5Zmrauk1xkTDIcZkcrTxcvDMBJdWUN5i6tU2JVQcHcox8M%2FOFzHo4 ZFAsYnK1s7TyevX8Jw1elWOIFb679cy%2BQM%3D HTTP/1.1 Host: HostName.example.com:8080 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.8.1.11) Gecko/20071127 Firefox/2.0.0.11 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q= 0.9,text/plain;q=0.8,image/png,*/*;q=0.5 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 300 Connection: keep-alive Cookie: SMSESSION=jlO0TgMQfglpU+GHQCJqbnoE2Pevax6fdzPGU7ZAgJuPb/fxTjC bWX1B1RO6QaLJn6VoVGNK8Sy6IeILAyv+LciS/OMK1E0tSXnL5Uvit3XIuWuiSMuklyDM IlOQ6n3ZSGGr9sKBUch5YVfGcfGjHQFcBIlzegQxBRrgH/l2rc8aTEHdCrprvBiRHwQlx JbrcWMqfJw7h+HUEtiz9bQCUkwMbpEW4eBfNyRlZTGov3K5hg4HK4tuoyvOeKdZaewlTB 4Lm+QeGWo2qv2mPDP+eVtBiVtRVHHTHGfSthTJYQOOc4rPV2dnl8axpWppGByeUmfme Service Provider9x5hVxDi91iyobTybKpDz0bltkvnHbqwbLfehUPtJFxS3Z54y9dm iuoQ+B5Kdrs7DNuvrnAI1ZQdDKQEVA4Pt+vA9KO18ah9V1I7BZ9D/x60uWxfaA3Ty8lRg WhMYqdBulFMD1B29sxboNHWdJ2FaxQJGjMpSEZ5iHB50ovF4YFXRyPP5Tl7eJxIebLKX02 LFrG/osNZ9UKHrMY1MRK5WWHJlYB040ADVcTNrFkc39vcYIA1eGDYhC/NaOd412HP5S0UX 0/59ADMLBsX/qBjcdODy3li+4eZnK1oHw/9yr3LCjewJ+H9w0k0/dQw99vgwEM2RPFgH5Y 7W6k6h1efp67VKXLBiJ1OZPJe2SCEDAOUla8qsC8fQ0VWTy/TfVhVtqJOaSLZrACX7uhPz bZE1EAPd8x7UeJquFll3WpdnZYObd0DQLeoWZcF2rPIcfBn+8X8oig5KzvAgQ9R8MR+h7O kYfhmwwBDaQkbKPpIxjpeLNxKpkEVWJ9HoHOpZ/txCQUAHqPV41YjZ6CQfBfUqdOHbfje9 O+0pJ1aHMntI4VYZOqdxsA+n9cgKjNQ8ruHOqSKhAQfEgipwcM2fMU3Uqmtr+0/+5bi7Cbs= HTTP/1.x 302 Moved Temporarily X-Powered-By: JService Provider/2.1 Server: Sun Java System Application Server 9.1 Set-Cookie: JSESSIONID=766be1d1028d55badd1ed0fe34ac; Path=/opensso Location: http://HostName.example.com:8080/opensso/UI/Login?module= SMAuth&goto=http%3A%2F%2FHostName.example.com%3A8080%2Fopensso% 2FSSORedirect%2FmetaAlias%2Fidp%3FReqID%3Ds27926cc0299bbe6f0112ead7 ff38b7985321e904c Content-Type: text/html;charset=ISO-8859-1 Content-Length: 0 Date: Fri, 01 Feb 2008 23:48:30 GMT ---------------------------------------------------------- |
4. Redirection to SiteMinder authentication module in OpenSSO Enterprise
http://HostName.example.com:8080/opensso/UI/Login?module=SMAuth&goto= http%3A%2F%2FHostName.example.com%3A8080%2Fopensso%2FSSORedirect% 2FmetaAlias%2Fidp%3FReqID%3Ds27926cc0299bbe6f0112ead7ff38b7985321e904c GET /opensso/UI/Login?module=SMAuth&goto=http%3A%2F%2FHostName.example.com% 3A8080%2Fopensso%2FSSORedirect%2FmetaAlias%2Fidp%3FReqID%3Ds27926cc0299bbe6f0112 ead7ff38b7985321e904c HTTP/1.1 Host: HostName.example.com:8080 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.8.1.11) Gecko/20071127 Firefox/2.0.0.11 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q= 0.9,text/plain;q=0.8,image/png,*/*;q=0.5 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 300 Connection: keep-alive Cookie: JSESSIONID=766be1d1028d55badd1ed0fe34ac; SMSESSION=jlO0TgMQfglpU+GHQ CJqbnoE2Pevax6fdzPGU7ZAgJuPb/fxTjCbWX1B1RO6QaLJn6VoVGNK8Sy6IeILAyv+LciS/OMK1 E0tSXnL5Uvit3XIuWuiSMuklyDMIlOQ6n3ZSGGr9sKBUch5YVfGcfGjHQFcBIlzegQxBRrgH/l2r c8aTEHdCrprvBiRHwQlxJbrcWMqfJw7h+HUEtiz9bQCUkwMbpEW4eBfNyRlZTGov3K5hg4HK4tuo yvOeKdZaewlTB4Lm+QeGWo2qv2mPDP+eVtBiVtRVHHTHGfSthTJYQOOc4rPV2dnl8axpWppGByeU mfmeService Provider9x5hVxDi91iyobTybKpDz0bltkvnHbqwbLfehUPtJFxS3Z54y9dmiuoQ+ B5Kdrs7DNuvrnAI1ZQdDKQEVA4Pt+vA9KO18ah9V1I7BZ9D/x60uWxfaA3Ty8lRgWhMYqdBulFMD 1B29sxboNHWdJ2FaxQJGjMpSEZ5iHB50ovF4YFXRyPP5Tl7eJxIebLKX02LFrG/osNZ9UKHrMY1M RK5WWHJlYB040ADVcTNrFkc39vcYIA1eGDYhC/NaOd412HP5S0UX0/59ADMLBsX/qBjcdODy3li+ 4eZnK1oHw/9yr3LCjewJ+H9w0k0/dQw99vgwEM2RPFgH5Y7W6k6h1efp67VKXLBiJ1OZPJe2SCED AOUla8qsC8fQ0VWTy/TfVhVtqJOaSLZrACX7uhPzbZE1EAPd8x7UeJquFll3WpdnZYObd0DQLeoW ZcF2rPIcfBn+8X8oig5KzvAgQ9R8MR+h7OkYfhmwwBDaQkbKPpIxjpeLNxKpkEVWJ9HoHOpZ/txC QUAHqPV41YjZ6CQfBfUqdOHbfje9O+0pJ1aHMntI4VYZOqdxsA+n9cgKjNQ8ruHOqSKhAQfEgipw cM2fMU3Uqmtr+0/+5bi7Cbs= HTTP/1.x 302 Moved Temporarily X-Powered-By: Servlet/2.5 Server: Sun Java System Application Server 9.1 Cache-Control: private Pragma: no-cache Expires: 0 X-DSAMEVersion: 8.0 (2007-November-29 01:17) AM_CLIENT_TYPE: genericHTML Set-Cookie: AMAuthCookie=AQIC5wM2LY4SfczvfJJpn1IfT3pStks2VjzPMebgYVAxtyE= @AAJTSQACMDE=#; Domain=HostName.example.com; Path=/ Set-Cookie: amlbcookie=01; Domain=HostName.example.com; Path=/ Set-Cookie: iPlanetDirectoryPro=AQIC5wM2LY4SfczvfJJpn1IfT3pStks2VjzPMebgYVAxtyE= @AAJTSQACMDE=#; Domain=HostName.example.com; Path=/ Set-Cookie: AMAuthCookie=LOGOUT; Domain=HostName.example.com; Expires=Thu, 01-Jan-1970 00:00:10 GMT; Path=/ X-AuthErrorCode: 0 Location: http://HostName.example.com:8080/opensso/SSORedirect/metaAlias/ idp?ReqID=s27926cc0299bbe6f0112ead7ff38b7985321e904c&iPlanetDirectoryPro= AQIC5wM2LY4SfczvfJJpn1IfT3pStks2VjzPMebgYVAxtyE%3D%40AAJTSQACMDE%3D%23 Content-Type: text/html; charset=iso-8859-1 Content-Length: 0 Date: Fri, 01 Feb 2008 23:48:30 GMT ---------------------------------------------------------- http://HostName.example.com:8080/opensso/SSORedirect/metaAlias/idp?ReqID= s27926cc0299bbe6f0112ead7ff38b7985321e904c&iPlanetDirectoryPro= AQIC5wM2LY4SfczvfJJpn1IfT3pStks2VjzPMebgYVAxtyE%3D%40AAJTSQACMDE%3D%23 GET /opensso/SSORedirect/metaAlias/idp?ReqID=s27926cc0299bbe6f0112ead7ff38b79 85321e904c&iPlanetDirectoryPro=AQIC5wM2LY4SfczvfJJpn1IfT3pStks2VjzPMebgYVAxtyE% 3D%40AAJTSQACMDE%3D%23 HTTP/1.1 Host: HostName.example.com:8080 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.8.1.11) Gecko/20071127 Firefox/2.0.0.11 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q= 0.9,text/plain;q=0.8,image/png,*/*;q=0.5 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 300 Connection: keep-alive Cookie: JSESSIONID=766be1d1028d55badd1ed0fe34ac; SMSESSION=jlO0TgMQfglpU+ GHQCJqbnoE2Pevax6fdzPGU7ZAgJuPb/fxTjCbWX1B1RO6QaLJn6VoVGNK8Sy6IeILAyv+Lci S/OMK1E0tSXnL5Uvit3XIuWuiSMuklyDMIlOQ6n3ZSGGr9sKBUch5YVfGcfGjHQFcBIlzegQx BRrgH/l2rc8aTEHdCrprvBiRHwQlxJbrcWMqfJw7h+HUEtiz9bQCUkwMbpEW4eBfNyRlZTGov 3K5hg4HK4tuoyvOeKdZaewlTB4Lm+QeGWo2qv2mPDP+eVtBiVtRVHHTHGfSthTJYQOOc4rPV2 dnl8axpWppGByeUmfmeService Provider9x5hVxDi91iyobTybKpDz0bltkvnHbqwbLfehUP tJFxS3Z54y9dmiuoQ+B5Kdrs7DNuvrnAI1ZQdDKQEVA4Pt+vA9KO18ah9V1I7BZ9D/x60uWxfa A3Ty8lRgWhMYqdBulFMD1B29sxboNHWdJ2FaxQJGjMpSEZ5iHB50ovF4YFXRyPP5Tl7eJxIebL KX02LFrG/osNZ9UKHrMY1MRK5WWHJlYB040ADVcTNrFkc39vcYIA1eGDYhC/NaOd412HP5S0UX 0/59ADMLBsX/qBjcdODy3li+4eZnK1oHw/9yr3LCjewJ+H9w0k0/dQw99vgwEM2RPFgH5Y7W6 k6h1efp67VKXLBiJ1OZPJe2SCEDAOUla8qsC8fQ0VWTy/TfVhVtqJOaSLZrACX7uhPzbZE1EAP d8x7UeJquFll3WpdnZYObd0DQLeoWZcF2rPIcfBn+8X8oig5KzvAgQ9R8MR+h7OkYfhmwwBDaQ kbKPpIxjpeLNxKpkEVWJ9HoHOpZ/txCQUAHqPV41YjZ6CQfBfUqdOHbfje9O+0pJ1aHMntI4VY ZOqdxsA+n9cgKjNQ8ruHOqSKhAQfEgipwcM2fMU3Uqmtr+0/+5bi7Cbs=; amlbcookie=01; iPlanetDirectoryPro=AQIC5wM2LY4SfczvfJJpn1IfT3pStks2VjzPMebgYVAxtyE=@AAJTS QACMDE=# HTTP/1.x 302 Moved Temporarily X-Powered-By: JService Provider/2.1 Server: Sun Java System Application Server 9.1 Location: http://ide-13.red.example.com:8080/opensso/Consumer/metaAlias/ sp?SAMLart=AAQAAE6JQxQxFQ72nsd5qDmVUTW5T3ieNSAqIADayEcXVxKAZQSjzCxJMDE%3D Content-Type: text/html;charset=ISO-8859-1 Content-Length: 0 Date: Fri, 01 Feb 2008 23:48:30 GMT ---------------------------------------------------------- |
5. Finish SAML SSO
http://ide-13.red.example.com:8080/opensso/Consumer/metaAlias/sp?SAMLart= AAQAAE6JQxQxFQ72nsd5qDmVUTW5T3ieNSAqIADayEcXVxKAZQSjzCxJMDE%3D GET /opensso/Consumer/metaAlias/sp?SAMLart=AAQAAE6JQxQxFQ72nsd5qDmVUTW5T 3ieNSAqIADayEcXVxKAZQSjzCxJMDE%3D HTTP/1.1 Host: ide-13.red.example.com:8080 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.8.1.11) Gecko/20071127 Firefox/2.0.0.11 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q= 0.9,text/plain;q=0.8,image/png,*/*;q=0.5 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 300 Connection: keep-alive Cookie: JSESSIONID=765d4c266461607b4b55811d34ca; SMSESSION=jlO0TgMQfglpU+ GHQCJqbnoE2Pevax6fdzPGU7ZAgJuPb/fxTjCbWX1B1RO6QaLJn6VoVGNK8Sy6IeILAyv+Lci S/OMK1E0tSXnL5Uvit3XIuWuiSMuklyDMIlOQ6n3ZSGGr9sKBUch5YVfGcfGjHQFcBIlzegQx BRrgH/l2rc8aTEHdCrprvBiRHwQlxJbrcWMqfJw7h+HUEtiz9bQCUkwMbpEW4eBfNyRlZTGov 3K5hg4HK4tuoyvOeKdZaewlTB4Lm+QeGWo2qv2mPDP+eVtBiVtRVHHTHGfSthTJYQOOc4rPV2 dnl8axpWppGByeUmfmeService Provider9x5hVxDi91iyobTybKpDz0bltkvnHbqwbLfehU PtJFxS3Z54y9dmiuoQ+B5Kdrs7DNuvrnAI1ZQdDKQEVA4Pt+vA9KO18ah9V1I7BZ9D/x60uWx faA3Ty8lRgWhMYqdBulFMD1B29sxboNHWdJ2FaxQJGjMpSEZ5iHB50ovF4YFXRyPP5Tl7eJxI ebLKX02LFrG/osNZ9UKHrMY1MRK5WWHJlYB040ADVcTNrFkc39vcYIA1eGDYhC/NaOd412HP5 S0UX0/59ADMLBsX/qBjcdODy3li+4eZnK1oHw/9yr3LCjewJ+H9w0k0/dQw99vgwEM2RPFgH5Y 7W6k6h1efp67VKXLBiJ1OZPJe2SCEDAOUla8qsC8fQ0VWTy/TfVhVtqJOaSLZrACX7uhPzbZE1 EAPd8x7UeJquFll3WpdnZYObd0DQLeoWZcF2rPIcfBn+8X8oig5KzvAgQ9R8MR+h7OkYfhmwwB DaQkbKPpIxjpeLNxKpkEVWJ9HoHOpZ/txCQUAHqPV41YjZ6CQfBfUqdOHbfje9O+0pJ1aHMntI 4VYZOqdxsA+n9cgKjNQ8ruHOqSKhAQfEgipwcM2fMU3Uqmtr+0/+5bi7Cbs= HTTP/1.x 200 OK X-Powered-By: JService Provider/2.1 Server: Sun Java System Application Server 9.1 Set-Cookie: iPlanetDirectoryPro=AQIC5wM2LY4SfcxHYS5DBuFiEDZVArdPot5Wt07zTqKO6+w= @AAJTSQACMDE=#; Domain=ide-13.red.example.com; Path=/ Content-Type: text/html;charset=ISO-8859-1 Transfer-Encoding: chunked Date: Fri, 01 Feb 2008 23:47:30 GMT |
Using OpenSSO Enterprise to Enable SiteMinder Federation in a Service Provider Environment
The following is a high-level overview of the sequence you must follow to enable SiteMinder with OpenSSO Enterprise in a Service Provider Environment:
-
Install and Configure SiteMinder in Service Provider Domain.
-
Configure OpenSSO Enterprise Identity Provider and Service Provider for SAML2 protocols.
 To Install OpenSSO Enterprise Instances
To Install OpenSSO Enterprise Instances
-
Install OpenSSO Enterprise in the Identity Provider Environment.
OpenSSO Enterprise is not the only supported access control software that can be used in the Identity Provider. But for optimum protocol interoperability, choosing OpenSSO Enterprise is a good practice. For detailed installation and configuration information, see the Sun OpenSSO Enterprise 8.0 Installation and Configuration Guide.
Ideally, Service Provider and Identity Provider are deployed in two different domains. At minimum, the cookie domains should be different to ensure cookie validation consistency.
-
Install OpenSSO Enterprise in the Service Provider Environment.
The OpenSSO Enterprise in the Service Provider environment is the SAML2 protocols initiator. The SiteMinder Web Agent can protect the enterprise application, but will still redirect to OpenSSO Enterprise for single sign-on purposes.
 To Install and Configure SiteMinder in the
Service Provider Domain
To Install and Configure SiteMinder in the
Service Provider Domain
Before You Begin
Before proceeding, be sure to read the general instructions in Installing SiteMinder and in Configuring SiteMinder After Installation. The following steps provide additional installation information specific only to this use case.
-
Install SiteMinder.
This is the domain that protects its enterprise applications using their SiteMinder agents. For the installation of SiteMinder and SiteMinder agents, see the CA SiteMinder product documentation.
-
Create a custom authentication scheme.
-
Copy the compiled SiteMinder authentication scheme JAR files into the SiteMinder lib directory.
After you unzip the OpenSSO Enterprise binary, the SiteMinder custom authentication module is located under the directory unzip-directory/integrations/siteminder/. The README.html provides steps for building a custom authentication module. The OpenSSO Enterprise authentication module is a Java-based authentication scheme in SiteMinder. The README.html explains the steps for configuring the SiteMinder authentication scheme.
-
In the SiteMinder console, click Authentication Scheme, and then click “Create Custom Authentication Scheme.”
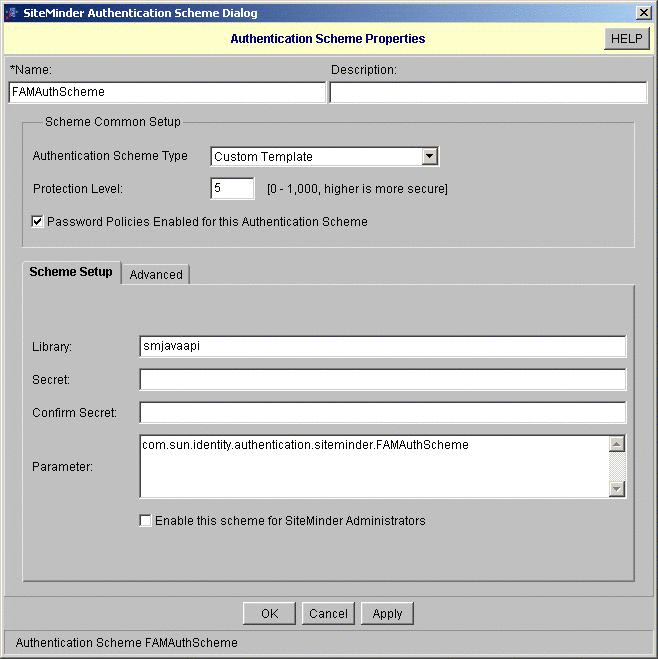
-
-
Configure a resource and a policy to trigger the OpenSSO Enterprise authentication module.
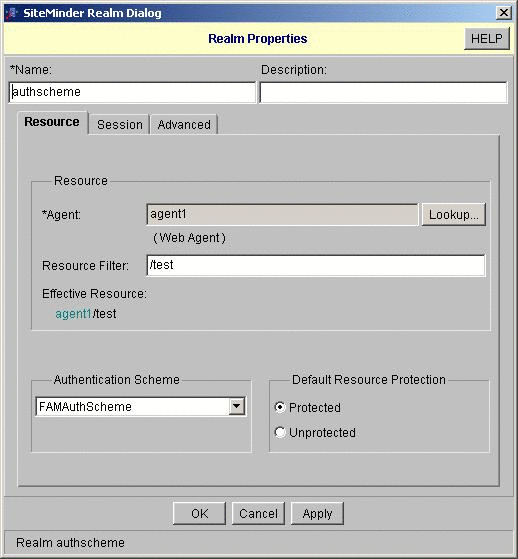
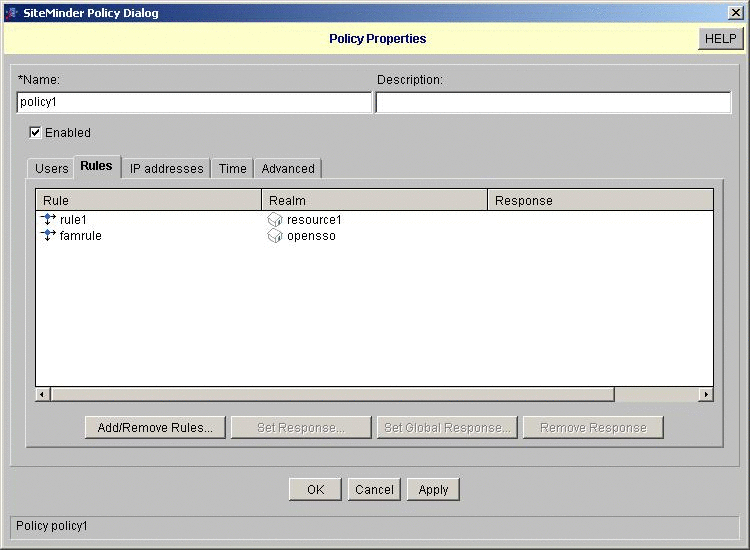
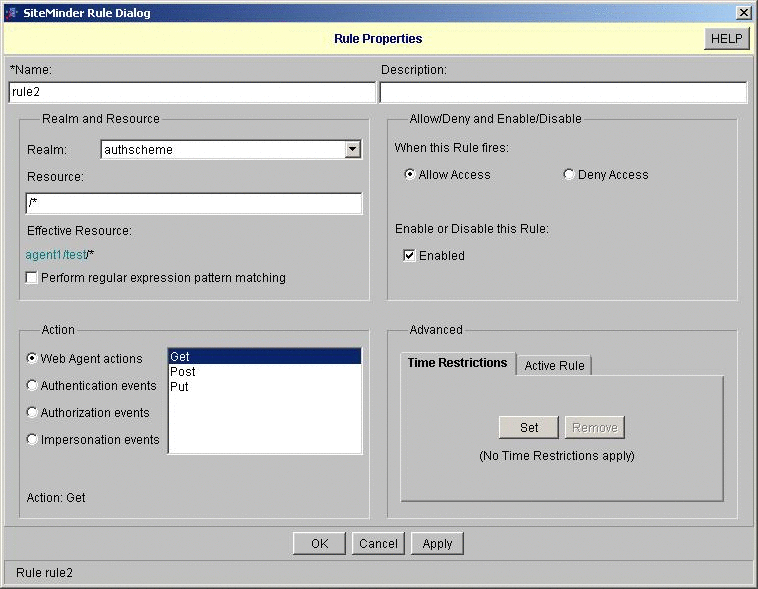
 To Configure the OpenSSO Enterprise Identity
Provider and Service Provider for SAML2 protocols
To Configure the OpenSSO Enterprise Identity
Provider and Service Provider for SAML2 protocols
For these configurations, you must have the following:
-
Identity Provider metadata
-
Identity Provider extended metadata
-
Service Provider metadata
-
Service Provider extended metadata
In Identity Provider, import Identity Provider metadata and Identity Provider extended metadata as hosted metadata. Import Service Provider metadata and Service Provider extended metadata as remote entity metadata.
Before You Begin
Before loading metadata, read through the following steps for the changes that you must make to the metadata. See the SAML2 samples for detailed instructions on how to setup SAML2, See the OpenSSO website for commands and syntax.
-
Edit the extended metadata XML element <EntityConfig>.
Change the hosted attribute from true to false.
-
Generate the metadata templates in both Identity Provider and Service Provider environments.
You can generate the metadata templates in one of two ways:
-
Use the browser-based URL http://host:port/opensso/famadm.jsp
-
Use the famadm command.
At the Identity Provider, where idp_meta_alias is /idp:
famadm create-metadata-templ -y idp_entity_id -u amadmin -f admin_password_file_name -m idp_standard_metadata -x idp_extended_metadata -i idp_meta_alias
At the Service Provider, where sp_meta_alias is /sp:
famadm create-metadata-templ -y sp_entity_id -u amadmin -f admin_password_file_name -msp_standard_metadata -x sp_extended_metadata -s sp_meta_alias
-
-
Customize the extended metadata at the Service Provider.
Add the Service Provider extended metadata as an attribute. This attribute is used by the SAML protocols to do any post-SSO Authentication process. In this example, the attribute is named spAdapter. In the architecture diagram, this is the SiteMinder Plug-In. The SiteMinder Plug-In uses the OpenSSO Enterprise session to authenticate against SiteMinder and to establish the SiteMinder session. The Service Provider metadata must have the following attributes:
<Attribute name="spAdapter"> <Value>com.sun.identity.saml2.plugins.SMAdapter</Value> </Attribute> <Attribute name="spAdapterEnv"> <Value>AgentIP=192.18.120.65</Value> <Value>AgentID=agent1</Value> <Value>PolicyServerIPAddress=192.18.120.65</Value> <Value>AuthorizationPort=44443</Value> <Value>AuthenticationPort=44442</Value> <Value>AccountingPort=44441</Value> <Value>AgentHostName=HostName.example.com</Value> <Value>ConnectionMinimum=2</Value> <Value>ConnectionMaximum=20</Value> <Value>ConnectionStep=2</Value> <Value>RequestTimeout=60</Value> <Value>FAMCookieName=iPlanetDirectoryPro</Value> <Value>SMCookieName=SMSESSION</Value> <Value>CookieDomain=.red.example.com</Value> <Value>Resource=/test/index.html</Value> <Value>SharedSecret={RC2}1r976MPOVq5JPpKzxFsXxIlut/YkgtUeklaceAoONCN mFJKDY+W8CkVpGY0to+x6apsIQAMPWLsgrm6NcdvyXv7K9Vf0vEALeWOy5BqLAhw fgKp4TbFRQspgv4w24ZOWsk57rwJ0N4kUJdM9lsLRu5hGKXArRJNpF80vS/U53TZ vM/qE5I3DcCOWKY4lJBZh</Value> </Attribute> -
Set the Service Provider extended metadata attribute transientUser to your anonymous user.
<Attribute name="transientUser"> <Value>anonymous</Value> </Attribute>Also verify that the OpenSSO Enterprise Service Provider is enabled for Anonymous authentication. See the OpenSSO Enterprise product documentation for more information.
-
Add the Circle of Trust through the OpenSSO Enterprise administration console.
Before loading, verify that the hosted attribute in the extended metadata has been changed to false.
-
Load the hosted metadata in both the Identity Provider and the Service Provider.
You can use the famadm command or the OpenSSO Enterprise administration console.
-
Exchange the Service Provider metadata with the Identity Provider.
-
Exchange the Identity Provider metadata with the Service Provider metadata.
-
Load the metadata.
-
After successful metadata exchange, verify through OpenSSO Enterprise administration console that metadata is properly configured.
-
Verify that Single Sign-On works properly.
Access the enterprise application protected by SiteMinder Service Provider Agent. This should redirect to the OpenSSO Enterprise for authentication where the SAML2 SSO is initiated.
Sample Service Provider Interactions
This section provides sample output from the following interactions:
1. Invocation of SAML SSO request
http://HostName.example.com:8080/opensso/saml2/jsp/ spSSOInit.jsp?metaAlias=/sp&idpEntityID= http://ide-13.red.example.com:8080/opensso&NameIDFormat=transient GET /opensso/saml2/jsp/spSSOInit.jsp?metaAlias=/sp&idpEntityID= http://ide-13.red.example.com:8080/opensso&NameIDFormat=transient HTTP/1.1 Host: HostName.example.com:8080 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.8.1.11) Gecko/20071127 Firefox/2.0.0.11 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q= 0.9,text/plain;q=0.8,image/png,*/*;q=0.5 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 300 Connection: keep-alive Cookie: JSESSIONID=5fa8300161a1d5dc746ad8f9fb31 |
2. Redirection to Identity Provider
HTTP/1.x 302 Moved Temporarily X-Powered-By: JService Provider/2.1 Server: Sun Java System Application Server 9.1 Location: http://ide-13.red.example.com:8080/opensso/SSORedirect/ metaAlias/idp?SAMLRequest=nVRfb9owEH%2Fvp4j8DnESaMECJAaahtRtDOge9 maSy7Dm2JnvQtm3rx0oYmqFVF7P57vfP3uEstK1mDa0Myv42wBSFB0qbVC0J2PWOCO sRIXCyApQUC7W06%2BPIu1yUTtLNrea3S3mY4bpYJvxLNsW5Rb60O89DNNhWQ4l7yV 8cJ8kUAzT7J5nKYt%2BgkNlzZj5MSxaIDawMEjSkC9xPujwtMN7m2Qoej3Rf%2FjFo rmHpoyk9taOqBZxrAroJFnXQdFVtZYGqJvbSgz4gMe2BoNo4%2FX6%2BwoK5SCnuAK SU60k%2Bps1iz5bl0NLfcxKqRECkqVEVHs4V5Ynjp%2BUKZT5fV2Q7bEJxZfNZtmZO lKlzIlFU0RwAfrMGmwqcGtwe5XD0%2BrxTAZ3ai%2B1%2BnOdzuuACy5Ys8ndKNglWi HdhYHX4cpXWGzyERCj%2BGLZaXUtvvnxi%2FnSapX%2FuyVDwY5K0vXuUFFFp2xbBTl pUIHxCq%2BXYf%2BPxoMvFbiPqeoN0to%2BzxxI8s6Ta4BNjiz%2F53Ume3orULTx8a YQHOgW0jNb1dIpDKmGQwjL5Gjl5eCZ9k6toLzF2KttucjDaF8OsX%2B2rghx908Fik3 QtraOTm6%2Fh%2Bes0btyeLHit9%2FL5AU%3D Content-Type: text/html;charset=ISO-8859-1 Content-Length: 0 Date: Mon, 04 Feb 2008 19:44:57 GMT ---------------------------------------------------------- http://ide-13.red.example.com:8080/opensso/SSORedirect/metaAlias/ idp?SAMLRequest=nVRfb9owEH%2Fvp4j8DnESaMECJAaahtRtDOge9maSy7Dm2Jn vQtm3rx0oYmqFVF7P57vfP3uEstK1mDa0Myv42wBSFB0qbVC0J2PWOCOsRIXCyApQ UC7W06%2BPIu1yUTtLNrea3S3mY4bpYJvxLNsW5Rb60O89DNNhWQ4l7yV8cJ8kUAz T7J5nKYt%2BgkNlzZj5MSxaIDawMEjSkC9xPujwtMN7m2Qoej3Rf%2FjFormHpoyk 9taOqBZxrAroJFnXQdFVtZYGqJvbSgz4gMe2BoNo4%2FX6%2BwoK5SCnuAKSU60k% 2Bps1iz5bl0NLfcxKqRECkqVEVHs4V5Ynjp%2BUKZT5fV2Q7bEJxZfNZtmZOlKlzI lFU0RwAfrMGmwqcGtwe5XD0%2BrxTAZ3ai%2B1%2BnOdzuuACy5Ys8ndKNglWiHdh YHX4cpXWGzyERCj%2BGLZaXUtvvnxi%2FnSapX%2FuyVDwY5K0vXuUFFFp2xbBTlp UIHxCq%2BXYf%2BPxoMvFbiPqeoN0to%2BzxxI8s6Ta4BNjiz%2F53Ume3orULTx8 aYQHOgW0jNb1dIpDKmGQwjL5Gjl5eCZ9k6toLzF2KttucjDaF8OsX%2B2rghx908F ik3QtraOTm6%2Fh%2Bes0btyeLHit9%2FL5AU%3D GET /opensso/SSORedirect/metaAlias/idp?SAMLRequest=nVRfb9owEH%2Fvp 4j8DnESaMECJAaahtRtDOge9maSy7Dm2JnvQtm3rx0oYmqFVF7P57vfP3uEstK1mDa 0Myv42wBSFB0qbVC0J2PWOCOsRIXCyApQUC7W06%2BPIu1yUTtLNrea3S3mY4bpYJv xLNsW5Rb60O89DNNhWQ4l7yV8cJ8kUAzT7J5nKYt%2BgkNlzZj5MSxaIDawMEjSkC9 xPujwtMN7m2Qoej3Rf%2FjFormHpoyk9taOqBZxrAroJFnXQdFVtZYGqJvbSgz4gMe 2BoNo4%2FX6%2BwoK5SCnuAKSU60k%2Bps1iz5bl0NLfcxKqRECkqVEVHs4V5Ynjp% 2BUKZT5fV2Q7bEJxZfNZtmZOlKlzIlFU0RwAfrMGmwqcGtwe5XD0%2BrxTAZ3ai%2B 1%2BnOdzuuACy5Ys8ndKNglWiHdhYHX4cpXWGzyERCj%2BGLZaXUtvvnxi%2FnSapX% 2FuyVDwY5K0vXuUFFFp2xbBTlpUIHxCq%2BXYf%2BPxoMvFbiPqeoN0to%2BzxxI8s6 Ta4BNjiz%2F53Ume3orULTx8aYQHOgW0jNb1dIpDKmGQwjL5Gjl5eCZ9k6toLzF2Ktt ucjDaF8OsX%2B2rghx908Fik3QtraOTm6%2Fh%2Bes0btyeLHit9%2FL5AU%3D HTTP/1.1 Host: ide-13.red.example.com:8080 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.8.1.11) Gecko/20071127 Firefox/2.0.0.11 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q= 0.9,text/plain;q=0.8,image/png,*/*;q=0.5 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 300 Connection: keep-alive |
3. Redirection to Login
HTTP/1.x 302 Moved Temporarily X-Powered-By: JService Provider/2.1 Server: Sun Java System Application Server 9.1 Set-Cookie: JSESSIONID=5f9f32d1896460b979b16ac14fb3; Path=/opensso Location: http://ide-13.red.example.com:8080/opensso/UI/Login?realm= /&goto=http%3A%2F%2Fide-13.red.example.com%3A8080%2Fopensso% 2FSSORedirect%2FmetaAlias%2Fidp%3FReqID%3Ds28b3033bdfbe5e547929ff9a 04108611ed9236032 Content-Type: text/html;charset=ISO-8859-1 Content-Length: 0 Date: Mon, 04 Feb 2008 19:43:58 GMT ---------------------------------------------------------- http://ide-13.red.example.com:8080/opensso/UI/Login?realm=/&goto= http%3A%2F%2Fide-13.red.example.com%3A8080%2Fopensso%2FSSORedirect% 2FmetaAlias%2Fidp%3FReqID%3Ds28b3033bdfbe5e547929ff9a04108611ed9236032 GET /opensso/UI/Login?realm=/&goto=http%3A%2F%2Fide-13.red.example.com% 3A8080%2Fopensso%2FSSORedirect%2FmetaAlias%2Fidp%3FReqID%3Ds28b3033bdfb e5e547929ff9a04108611ed9236032 HTTP/1.1 Host: ide-13.red.example.com:8080 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.8.1.11) Gecko/20071127 Firefox/2.0.0.11 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q= 0.9,text/plain;q=0.8,image/png,*/*;q=0.5 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 300 Connection: keep-alive Cookie: JSESSIONID=5f9f32d1896460b979b16ac14fb3 HTTP/1.x 200 OK X-Powered-By: JService Provider/2.1 Server: Sun Java System Application Server 9.1 Cache-Control: private Pragma: no-cache Expires: 0 X-DSAMEVersion: 8.0 (2007-November-29 01:17) AM_CLIENT_TYPE: genericHTML Set-Cookie: AMAuthCookie=AQIC5wM2LY4SfczOj691d2eiNkQCzmceO14vekWbCSzRU/ E=@AAJTSQACMDE=#; Domain=ide-13.red.example.com; Path=/ Set-Cookie: amlbcookie=01; Domain=ide-13.red.example.com; Path=/ Content-Type: text/html;charset=UTF-8 Transfer-Encoding: chunked Date: Mon, 04 Feb 2008 19:43:58 GMT ---------------------------------------------------------- http://ide-13.red.example.com:8080/opensso/UI/Login?AMAuthCookie= AQIC5wM2LY4SfczOj691d2eiNkQCzmceO14vekWbCSzRU%2FE%3D%40AAJTSQACMDE%3D%23 POST /opensso/UI/Login?AMAuthCookie=AQIC5wM2LY4SfczOj691d2eiNkQCzmceO14v ekWbCSzRU%2FE%3D%40AAJTSQACMDE%3D%23 HTTP/1.1 Host: ide-13.red.example.com:8080 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.8.1.11) Gecko/20071127 Firefox/2.0.0.11 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q= 0.9,text/plain;q=0.8,image/png,*/*;q=0.5 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 300 Connection: keep-alive Referer: http://ide-13.red.example.com:8080/opensso/UI/Login?realm=/ &goto=http%3A%2F%2Fide-13.red.example.com%3A8080%2Fopensso%2FSSORedirect% 2FmetaAlias%2Fidp%3FReqID%3Ds28b3033bdfbe5e547929ff9a04108611ed9236032 Cookie: JSESSIONID=5f9f32d1896460b979b16ac14fb3; AMAuthCookie=AQIC5wM2LY4 SfczOj691d2eiNkQCzmceO14vekWbCSzRU/E=@AAJTSQACMDE=#; amlbcookie=01 Content-Type: application/x-www-form-urlencoded Content-Length: 254 IDToken0=&IDToken1=amadmin&IDToken2=admin123&IDButton=Log+In&goto= aHR0cDovL2lkZS0xMy5yZWQuaXBsYW5ldC5jb206ODA4MC9vcGVuc3NvL1NTT1JlZGlyZWN0L2 1ldGFBbGlhcy9pZHA%2FUmVxSUQ9czI4YjMwMzNiZGZiZTVlNTQ3OTI5ZmY5YTA0MTA4NjExZW Q5MjM2MDMy&encoded=true&gx_charset=UTF-8 HTTP/1.x 302 Moved Temporarily X-Powered-By: Servlet/2.5 Server: Sun Java System Application Server 9.1 Cache-Control: private Pragma: no-cache Expires: 0 X-DSAMEVersion: 8.0 (2007-November-29 01:17) AM_CLIENT_TYPE: genericHTML X-AuthErrorCode: 0 Set-Cookie: iPlanetDirectoryPro=AQIC5wM2LY4SfczOj691d2eiNkQCzmceO14vekWbCSzRU/ E=@AAJTSQACMDE=#; Domain=ide-13.red.example.com; Path=/ Set-Cookie: AMAuthCookie=LOGOUT; Domain=ide-13.red.example.com; Expires=Thu, 01-Jan-1970 00:00:10 GMT; Path=/ Location: http://ide-13.red.example.com:8080/opensso/SSORedirect/ metaAlias/idp?ReqID=s28b3033bdfbe5e547929ff9a04108611ed9236032 Content-Type: text/html; charset=iso-8859-1 Content-Length: 0 Date: Mon, 04 Feb 2008 19:44:05 GMT ---------------------------------------------------------- http://ide-13.red.example.com:8080/opensso/SSORedirect/metaAlias/ idp?ReqID=s28b3033bdfbe5e547929ff9a04108611ed9236032 GET /opensso/SSORedirect/metaAlias/idp?ReqID=s28b3033bdfbe5e54792 9ff9a04108611ed9236032 HTTP/1.1 Host: ide-13.red.example.com:8080 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.8.1.11) Gecko/20071127 Firefox/2.0.0.11 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q= 0.9,text/plain;q=0.8,image/png,*/*;q=0.5 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 300 Connection: keep-alive Referer: http://ide-13.red.example.com:8080/opensso/UI/Login?realm= /&goto=http%3A%2F%2Fide-13.red.example.com%3A8080%2Fopensso%2FSSORedirect% 2FmetaAlias%2Fidp%3FReqID%3Ds28b3033bdfbe5e547929ff9a04108611ed9236032 Cookie: JSESSIONID=5f9f32d1896460b979b16ac14fb3; amlbcookie=01; iPlanetDirectoryPro=AQIC5wM2LY4SfczOj691d2eiNkQCzmceO14vekWbCSzRU/E=@AAJTSQACMDE=# HTTP/1.x 302 Moved Temporarily X-Powered-By: JService Provider/2.1 Server: Sun Java System Application Server 9.1 Location: http://HostName.example.com:8080/opensso/Consumer/metaAlias/ sp?SAMLart=AAQAAI4sWYpfoDDYJrHzsMnG%2BjyNM94p5ejn49a%2BnZ0s3ylY7knQ6tkLMDE%3D Content-Type: text/html;charset=ISO-8859-1 Content-Length: 0 Date: Mon, 04 Feb 2008 19:44:05 GMT |
4. Redirection to Service Provider Assertion Consumer Service
http://HostName.example.com:8080/opensso/Consumer/metaAlias/sp?SAMLart= AAQAAI4sWYpfoDDYJrHzsMnG%2BjyNM94p5ejn49a%2BnZ0s3ylY7knQ6tkLMDE%3D GET /opensso/Consumer/metaAlias/sp?SAMLart=AAQAAI4sWYpfoDDYJrHzsMnG% 2BjyNM94p5ejn49a%2BnZ0s3ylY7knQ6tkLMDE%3D HTTP/1.1 Host: HostName.example.com:8080 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.8.1.11) Gecko/20071127 Firefox/2.0.0.11 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q= 0.9,text/plain;q=0.8,image/png,*/*;q=0.5 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 300 Connection: keep-alive Referer: http://ide-13.red.example.com:8080/opensso/UI/Login?realm= /&goto=http%3A%2F%2Fide-13.red.example.com%3A8080%2Fopensso%2FSSORedirect% 2FmetaAlias%2Fidp%3FReqID%3Ds28b3033bdfbe5e547929ff9a04108611ed9236032 Cookie: JSESSIONID=5fa8300161a1d5dc746ad8f9fb31 |
5. Check the SMSESSION Creation
HTTP/1.x 200 OK X-Powered-By: JService Provider/2.1 Server: Sun Java System Application Server 9.1 Set-Cookie: iPlanetDirectoryPro=AQIC5wM2LY4SfcwFsRqmpq0e6m+iL+tjmqYhTDsKeABb4Eg= @AAJTSQACMDE=#; Domain=HostName.example.com; Path=/Set-Cookie: SMSESSION=jnNJdOyhPMa6A7FKeD0tCgHyq3yt8Tsvtmj6G4NjbP05ftAMggw+ hqolfo32FJ8iOnggFoZ19qXVAJyqf0DvMqhM+X0oUVw3P3R83sBAT4uKtUaib7OxyTSi8W5pBI+hLexr NczdpVWN9vCGDU97uBlJgpI8L9aeSNBgCSwo+gluvd1I72KGyFVgMLkIkfLMJhctpz+zKVt252yEf5Oh QZlGhzT/DzNqBc+142eek5VwMzxABLhwuEQ1jI1VAGOYAeyQpSmikgNfWphDSV3X36L3+ZQqHZmzCwjb 8QKSrBZnMdGuZKCYc9U6N8VJ1Ft5zwi/lotOU198apSU2bI5nQzWnGjpz60Dxc6Ycy83bjOqby/ZYHrl 3OLv2wJ0RtEN8FPYFjbHLGg=; Domain=.red.example.com Content-Type: text/html;charset=ISO-8859-1 Transfer-Encoding: chunked Date: Mon, 04 Feb 2008 19:45:04 GMT |
- © 2010, Oracle Corporation and/or its affiliates
