Connections When Directory Proxy Server Is Configured for Proxy Authorization
When Directory Proxy Server is configured for proxy authorization, a client is usually authenticated to the Directory Proxy Server by a non-anonymous BIND or by a SASL external BIND, however, clients can also be anonymous. Directory Proxy Server is usually bound to the data sources by using an administrative identity.
Figure 19–2 shows the connections between a client, Directory Proxy Server, and backend LDAP servers, when Directory Proxy Server is configured for proxy authorization.
Figure 19–2 Connections for Proxy Authorization
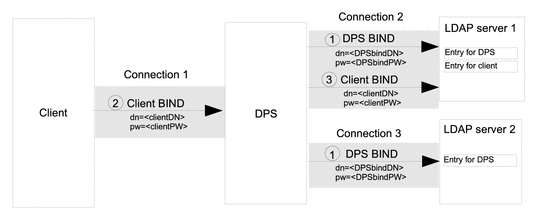
The connections for proxy authorization are made in the following stages:
-
When Directory Proxy Server is initiated, it opens a connection to each LDAP server. Directory Proxy Server binds to LDAP server 1 and LDAP server 2 by providing its DN and password, DPSbindDN and DPSbindPW.
An entry for DPSbindDN exists in both the LDAP servers and the BIND requests are granted. Directory Proxy Server is bound to the LDAP servers, on connection 2 and connection 3.
-
When a client connects to Directory Proxy Server, the client binds by providing its DN and a password, clientDN and clientPW.
-
The Directory Proxy Server authenticates the client to LDAP server 1 by using the client's credentials and by reusing connection 2.
An entry for the client exists in LDAP server 1 and the BIND request is granted. The client is bound to Directory Proxy Server on connection 1.
- © 2010, Oracle Corporation and/or its affiliates
