Secure Reverse Proxying
Secure reverse proxying occurs when one or more of the connections between the proxy server and another machine use the Secure Sockets Layer (SSL) protocol to encrypt data.
Secure reverse proxying has many uses:
-
Provides an encrypted connection from a proxy server outside a firewall to a secure content server inside the firewall
-
Enables clients to connect securely to the proxy server, facilitating the secure transmission of information (such as credit card numbers)
Secure reverse proxying causes each secure connection to be slower due to the overhead involved in encrypting your data. However, because SSL provides a caching mechanism, two connecting parties can reuse previously negotiated security parameters, dramatically reducing the overhead on subsequent connections.
The three ways to configure a secure reverse proxy are:
-
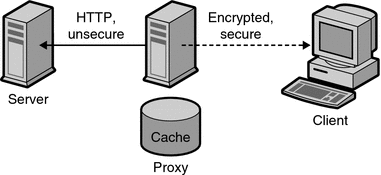
Secure client to proxy. This scenario is effective if there is little or no chance that the information being exchanged between your proxy and content server can be accessed by unauthorized users, as shown in the following figure..
Figure 14–2 Secure client connection to proxy
-
Secure proxy to content server. This scenario is effective if you have clients inside the firewall and a content server that is outside the firewall. In this scenario, your proxy server can act as a secure channel between sites, as shown in the following figure.
Figure 14–3 Secure Proxy Connection to Content Server

-
Secure client to proxy and secure proxy to content server. This scenario is effective if the information exchanged between the server, proxy and client needs to be secure. In this scenario, your proxy server can act like a secure channel between sites with the additional security of client authentication, as shown in the following figure.
Figure 14–4 Secure Client Connection to Proxy and Secure Proxy Connection to Content Server

For information about how to set up each of these configurations, see Setting up a Reverse Proxy.
In addition to SSL, the proxy can use client authentication, which requires that a computer making a request to the proxy provides a certificate or other form of identification to verify its identity.
- © 2010, Oracle Corporation and/or its affiliates
