Chapter 15 Using SOCKS
This chapter describes how to configure and use the SOCKS server included with Proxy Server. Proxy Server supports SOCKS versions 4 and 5.
This chapter contains the following sections:
About SOCKS
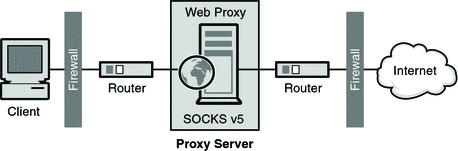
SOCKS is a networking proxy protocol that redirects connection requests from hosts on opposite sides of a SOCKS server, enabling hosts on one side to gain full access to hosts on the other without requiring direct IP reachability. SOCKS is commonly used as a network firewall that enables hosts behind a SOCKS server to gain full access to the Internet while preventing unauthorized access from the Internet to the internal hosts.
A SOCKS server is a generic firewall daemon that controls access through the firewall on a point-to-point basis. The SOCKS server authenticates and authorizes requests, establishes a proxy connection, and relays data. The SOCKS server works at the network level instead of the application level, and therefore has no knowledge of protocols or methods used for transferring requests. Because the SOCKS server has no knowledge of protocols, it can be used to pass those protocols that are not supported by the Proxy Server, such as Telnet.
Figure 15–1 Position of a SOCKS Server in a Network
Using the Bundled SOCKS v5 Server
Proxy Server includes its own SOCKS daemon that understands the standard socks5.conf file format used by other SOCKS daemons. This daemon can be used by the Proxy Server to route requests, or it can be run from the Proxy Server to provide additional capabilities for the network. For more information about configuring the Proxy Server to route requests through a SOCKS server, see Configuring Routing Entries.
The SOCKS daemon included with Proxy Server is disabled by default. You can enable the daemon from the SOCKS tab in the Server Manager interface, or from the command line. For more information, see Starting and Stopping the SOCKS v5 Server.
Note –
In Proxy Server 4 the name of the SOCKS daemon has been changed from ns-sockd to sockd.
The overall steps that must be taken to use the SOCKS server included with the Proxy Server are:
 To use the SOCKS
To use the SOCKS
-
Configure the SOCKS server. See Configuring the SOCKS v5 Server.
-
If the SOCKS server will be running on a computer with multiple interfaces, create SOCKS routing entries. See Configuring Routing Entries.
-
Create authentication entries. See Configuring SOCKS v5 Authentication Entries.
-
Create connection entries. See Configuring SOCKS v5 Connection Entries.
-
Enable the SOCKS server. See Starting and Stopping the SOCKS v5 Server.
About socks5.conf
Proxy Server uses the socks5.conf file to control access to the SOCKS server and its services. Each entry defines what the Proxy Server does when a request is received that matches the entry. Choices made in the Server Manager are written to socks5.conf. The file can also be edited manually. The socks5.conf file is located in the installation root directory server-rootas follows:
server-root/proxy-serverid/config directory
This section provides general information about socks5.conf. For detailed information about the file and its directives and syntax, see the Proxy Server Configuration File Reference.
Authentication
The SOCKS daemon can be configured to require authentication to use its services. Authentication is based on the host name and port of the connecting client. If you choose to require a user name and password, the information is authenticated against a user name and password file referenced by the socks5.conf file. If the provided user name and password do not match a listing in the password file, access is denied. The format for user names and passwords in the password file is username password, where the user name and password are separated by a space. .
You can also ban users. To require user name and password authentication, the SOCKS5_PWDFILE directive must be added to socks5.conf. For more information about the directive and its syntax, see the socks5.conf section in the Proxy Server Configuration File Reference
User name and password authentication can also be performed against a configured LDAP server, and not just a file.
Access Control
Access control is performed using a set of ordered lines in the socks5.conf file. Each line contains a single directive that permits or denies access to a resource. Directives are processed in the order in which they appear in the configuration file. A request that does not match any of the permit directives is denied access.
Logging
The SOCKS daemon logs both error and access messages in the SOCKS log file. The log file location and type of logging can be specified in socks5.conf.
The SOCKS daemon also generates a stat entry each hour, which gives statistics for the daemon.
Tuning
You can use the socks5.conf file to determine the number of worker and accept threads used by the SOCKS server. These numbers influence the performance of the SOCKS server.
For more information about worker and accept thread settings and their impact on performance, see the relevant section in Configuring the SOCKS v5 Server.
Starting and Stopping the SOCKS v5 Server
The SOCKS server can be started and stopped from the Server Manager or from the command line.
 To Start and Stop the SOCKS Server From the Server
Manager
To Start and Stop the SOCKS Server From the Server
Manager
-
Access the Server Manager for a server instance and click the SOCKS tab.
-
Click the Start/Stop SOCKS Server link.
-
Start or stop the SOCKS server.
To Start and Stop the SOCKS Server From the Command Line
Run the scripts found in the server-root/proxy-serverid directory, where server-root is the installation root:
-
start-sockd starts the SOCKS daemon
-
stop-sockd stops the SOCKS daemon
-
restart-sockd restarts the SOCKS daemon
Configuring the SOCKS v5 Server
 To Configure the SOCKS Server
To Configure the SOCKS Server
-
Access the Server Manager for a server instance and click the SOCKS tab.
-
Click the Configure SOCKS v5 link.
-
In the SOCKS Port field, type the port number on which the SOCKS server will listen. The default is 1080.
-
Select the SOCKS options you want to use.
The following options are available:
-
Disable Reverse DNS Lookup. Disables reverse DNS lookup for the SOCKS server. Reverse DNS translates IP addresses into host names. Disabling reverse DNS lookup can conserve network resources. DNS Lookup is disabled by default. If reverse DNS lookup is disabled and a URL is requested with a host name, the server will not map the host name to the IP address. If reverse DNS lookup is enabled, the server performs the mapping, and an entry is added to the SOCKS log file, listing the DNS translation.
-
Use Client-specific Bind Port. Allows the client to specify the port in a BIND request. With this option disabled, SOCKS ignores the client’s requested port and assigns a random port. This option is disabled by default.
-
Allow Wildcard As Bind IP Address. Allows the client to specify an IP address of all zeros (0.0.0.0) in a BIND request, which means that any IP address can connect. With this option disabled, the client must specify the IP address that will be connecting to the bind port, and the SOCKS server rejects requests to bind to 0.0.0.0. This option is disabled by default.
-
Quench Updates. Disables the automatic stat file writing once an hour. If disabled, the writing takes place with every request. For more information, see Logging.
-
The Quench Updates element displays in the user interface but is not implemented in this release of Proxy Server 4.
-
-
In the Log File field, type the full path name of the SOCKS log file.
The default is server-root/proxy-serverid/logs/socks5.log.
-
From the Log Level drop-down list, select whether the log file should contain warnings and errors only, all requests, or debugging messages.
-
Select an RFC 1413 ident response.
Ident allows the SOCKS server to determine the user name for a client. Generally, this feature only works when the client is running some version of UNIX. The following options are available
-
Don’t Ask. Never use ident to determine the user name for a client. This setting is the recommended and default setting.
-
Ask But Don’t Require. Ask for the user name of all clients but do not require it. This option uses ident for logging purposes only.
-
Require. Ask for the user name of all clients and only permit access to those with valid responses.
-
-
-
In the SOCKS Tuning section, specify the number of worker and accept threads the SOCKS server should use. These numbers influence performance of the SOCKS server. Click OK.
-
Number Of Worker Threads. The default is 40. If the SOCKS server is too slow, increase the number of worker threads. If the server is unstable, decrease the number. When changing this number, start with the default and increase or decrease as necessary. The typical number of worker threads is between 10 and 150. The absolute maximum is 512, but more than 150 tends to be wasteful and unstable.
-
Number Of Posted Accepts. The default is 1. If the SOCKS server is dropping connections, increase the number of accept threads. If the server is unstable, decrease the sever number. When changing this number, start with the default and increase or decrease as necessary. The typical number of accept threads is between 1 and 10. The absolute maximum is 512, but than 60 tends to be wasteful and unstable. Tune this setting if requests are failing when the SOCKS server is put under load and connections are being dropped.
-
-
Configuring SOCKS v5 Authentication Entries
SOCKS authentication entries identify the hosts from which the SOCKS daemon should accept connections, and which types of authentication the SOCKS daemon should use to authenticate those hosts.
 To Create SOCKS Authentication Entries
To Create SOCKS Authentication Entries
-
Access the Server Manager for a server instance and click the SOCKS tab.
-
Click the Set SOCKS v5 Authentication link.
-
Click the Add button.
-
In the Host Mask field, type the IP addresses or host names of the hosts that the SOCKS server will authenticate.
If you type an IP address, follow the address with a forward slash and the mask to be applied to the incoming IP address. The SOCKS server applies this mask to the IP address to determine if it is a valid host. Do not use spaces in the host mask entry. If you do not type a host mask, the authentication entry applies to all hosts.
For example, you can type 155.25.0.0/255.255.0.0 in the host mask field. If the host’s IP address is 155.25.3.5, the SOCKS server applies the mask to the IP address and determines that the host’s IP address matches the IP address for which the authentication record applies (155.25.0.0).
-
In the Port Range field, type the ports on the host computers that the SOCKS server will authenticate.
Do not use spaces in the port range entry. If you do not provide a port range, the authentication entry applies to all ports.
You can use brackets [ ] to include the ports at each end of the range or parentheses ( ) to exclude them. For example, [1000-1010] means all port numbers between and including 1000 and 1010, while (1000-1010) means all port numbers between, but not including, 1000 and 1010. You can also mix brackets and parentheses. For instance, (1000-1010] means all numbers between 1000 and 1010, excluding 1000 but including 1010.
-
From the Authentication Type drop-down list, select the authentication type.
The following options are available:
-
Require user-password. User name and password are required to access the SOCKS server.
-
User-password, if available. If a user name and password are available, they should be used to access the SOCKS server but they are not required for access.
-
Ban. Banned from the SOCKS server.
-
None. No authentication is required to access the SOCKS server.
-
-
From the Insert drop-down list, select the position for this entry in the socks5.conf file and click OK.
Because you can have multiple authentication methods, you must specify the order in which they are evaluated. Therefore, if the client does not support the first authentication method listed, the second method is used instead. If the client does not support any of the authentication methods listed, the SOCKS server disconnects without accepting a request.
 To Edit Authentication Entries
To Edit Authentication Entries
-
Access the Server Manager for a server instance and click the SOCKS tab.
-
Click the Set SOCKS v5 Authentication link.
-
Select the authentication entry you want to edit and click the Edit button.
-
Make changes as desired.
-
Click OK.
 To Delete Authentication Entries
To Delete Authentication Entries
-
Access the Server Manager for a server instance and click the SOCKS tab.
-
Click the Set SOCKS v5 Authentication link.
-
Select the authentication entry you want to delete.
-
Click the Delete button.
 To Move Authentication Entries
To Move Authentication Entries
Entries are evaluated in the order in which they appear in the socks5.conf file. You can change the order by moving them.
-
Access the Server Manager for a server instance and click the SOCKS tab.
-
Click the Set SOCKS v5 Authentication link.
-
Select the authentication entry you want to move and click the Move button.
-
From the Move drop-down list, select the position for this entry in the socks5.conf file.
-
Click OK.
Configuring SOCKS v5 Connection Entries
SOCKS connection entries specify whether the SOCKS daemon should permit or deny a request.
 To Create Connection Entries
To Create Connection Entries
-
Access the Server Manager for a server instance and click the SOCKS tab.
-
Click the Set SOCKS v5 Connections link.
-
Click the Add button.
-
From the Authentication Type drop-down list, select the authentication method for which this access control line applies.
-
From the Connection Type drop-down list, select the type of command the line matches. Possible command types are:
-
In the Source Host Mask field, type the IP address or host names of the hosts for which the connection control entry applies.
If you type an IP address, follow it with a forward slash and the mask to be applied to the source’s IP address. The SOCKS server applies this mask to the source’s IP address to determine if it is a valid host. Do not use spaces in the host mask entry. If you do not type a host mask, the connection entry applies to all hosts.
For example, you can type 155.25.0.0/255.255.0.0 in the host mask field. If the host’s IP address is 155.25.3.5, the SOCKS server applies the mask to the IP address and determines that the host’s IP address matches the IP address for which the connection control entry applies (155.25.0.0).
-
In the Port Range field, type the ports on the source computers for which the connection control entry applies.
Do not use spaces in the port range entry. If you do not specify a port range, the connection entry applies to all ports.
You can use brackets [ ] to include the ports at each end of the range or parentheses ( ) to exclude them. For example, [1000-1010] means all port numbers between and including 1000 and 1010, while (1000-1010) means all port numbers between, but not including, 1000 and 1010. You can also mix brackets and parentheses. For instance, (1000-1010] means all numbers between 1000 and 1010, excluding 1000, but including 1010.
-
In the Destination Host Mask field, type the IP address or host name for which the connection entry applies.
If you type an IP address, follow it with a forward slash and the mask to be applied to the incoming IP address. The SOCKS server applies this mask to the IP address of the destination computer to determine if it is a valid destination host. Do not use spaces in the host mask entry. If you do not type a destination host mask, the connection entry applies to all hosts.
For example, you can type 155.25.0.0/255.255.0.0 into the destination host mask field. If the destination host’s IP address is 155.25.3.5, the SOCKS server applies the mask to the IP address and determines that the destination host’s IP address matches the IP address for which the proxy entry applies (155.25.0.0).
-
In the Port Range field, type the ports on the destination host computers for which the connection control entry applies.
Do not use spaces in the port range entry. If you do not type a port range, the connection entry applies to all ports.
Note –Most SOCKS applications request port 0 for bind requests, meaning they have no port preference. Therefore, the destination port range for bind should always include port 0.
You can use brackets [ ] to include the ports at each end of the range or parentheses ( ) to exclude them. For example, [1000-1010] means all port numbers between and including 1000 and 1010, while (1000-1010) means all port numbers between, but not including, 1000 and 1010. You can also mix brackets and parentheses. For instance, (1000-1010] means all numbers between 1000 and 1010, excluding 1000, but including 1010.
-
In the User Group field, type the group to which you want to permit or deny access.
If a group is not specified, the connection entry applies to all users.
-
From the Action drop-down list, choose to permit or deny access for the connection you are creating.
-
From the Insert drop-down list, select the position for this entry in the socks5.conf file and click OK.
Because you can have multiple connection directives, you must specify the order in which they are evaluated.
 To Edit Connection Entries
To Edit Connection Entries
-
Access the Server Manager for a server instance and click the SOCKS tab.
-
Click the Set SOCKS v5 Connections link.
-
Select the connection entry you want to edit and click the Edit button.
-
Make changes as desired.
-
Click OK.
 To Delete Connection Entries
To Delete Connection Entries
-
Access the Server Manager for a server instance and click the SOCKS tab.
-
Click the Set SOCKS v5 Connections link.
-
Select the connection entry you want to delete.
-
Click the Delete button.
 To Move Connection Entries
To Move Connection Entries
Entries are evaluated in the order in which they appear in the socks5.conf file. You can change the order by moving them.
-
Access the Server Manager for a server instance and click the SOCKS tab.
-
Click the Set SOCKS v5 Connections link.
-
Select the connection entry you want to move.
-
Click the Move button.
-
From the Move drop-down list, select the position for this entry in the socks5.conf file and click OK.
Configuring SOCKS v5 Server Chaining
SOCKS servers can be chained together in the same manner as Proxy Servers, meaning that a SOCKS server can route through another SOCKS server.
 To Configure SOCKS Server Chaining
To Configure SOCKS Server Chaining
-
Access the Server Manager for a server instance and click the SOCKS tab.
-
Click the Set SOCKS v5 Routing link.
-
If the downstream proxy in the proxy chain requires authentication to serve any requests, in the Server Chaining section, type the user name and password for authenticating to chained Proxy Servers. Click OK.
Configuring Routing Entries
Routing entries can be used to configure a Proxy Server to route requests through a SOCKS server. The two types of routing entries are, the SOCKS v5 routes and the SOCKS v5 proxy routes.
-
The SOCKS v5 routes identify which interface the SOCKS daemon should use for particular IP addresses.
-
The SOCKS v5 proxy routes identify the IP addresses that are accessible through another SOCKS server, and whether that SOCKS server connects directly to the host. Proxy routes are important when routing through a SOCKS server.
 To Create Routing Entries
To Create Routing Entries
-
Access the Server Manager for a server instance and click the SOCKS tab.
-
Click the Set SOCKS v5 Routing link.
-
In the Routing section, click the Add button.
-
In the Host Mask field, type the IP address or host name for which incoming and outgoing connections must go through the specified interface.
If you type an IP address, follow it with a forward slash and the mask to be applied to the incoming IP address. The SOCKS server applies this mask to the IP address to determine whether it is a valid host. Do not use spaces in the host mask entry. If you do not provide a host mask, the SOCKS v5 entry applies to all hosts.
For example, you can type 155.25.0.0/255.255.0.0 in the host mask field. If the host’s IP address is 155.25.3.5, the SOCKS server applies the mask to the IP address and determines that the host’s IP address matches the IP address for which the routing entry applies (155.25.0.0).
-
In the Port Range field, type the ports for which incoming and outgoing connections must go through the specified interface. Your port range should not have any spaces.
If you do not specify a port range, the SOCKS v5 entry applies to all ports.
You can use brackets [ ] to include the ports at each end of the range or parentheses ( ) to exclude them. For example, [1000-1010] means all port numbers between and including 1000 and 1010, while (1000-1010) means all port numbers between, but not including, 1000 and 1010. You can also mix brackets and parentheses. For instance, (1000-1010] means all numbers between 1000 and 1010, excluding 1000, but including 1010.
-
In the Interface/Address field, type the IP address or name of the interface through which incoming and outgoing connections must pass.
-
From the Insert drop-down list, select the position for this entry in the socks5.conf file and click OK.
Because you can have multiple routing methods, you must specify the order in which they are evaluated.
Note –The interface specified should be used for both incoming and outgoing connections, otherwise the incoming route will be different from the configured interface and an error message will be received.
 To Create Proxy Routing Entries
To Create Proxy Routing Entries
-
Access the Server Manager for a server instance and click the SOCKS tab.
-
Click the Set SOCKS v5 Routing link.
-
In the Proxy Routing section, click the Add button.
-
From the Proxy Type drop-down list, select the type of Proxy Server through which you are routing. The following options are available
-
In the Destination Host Mask field, type the IP address or host name for which the connection entry applies.
If you type an IP address, follow it with a forward slash and the mask to be applied to the incoming IP address. The SOCKS server applies this mask to the IP address of the destination computer to determine whether it is a valid destination host. Do not use spaces in the host mask entry. If you do not provide a destination host mask, the connection entry applies to all hosts.
For example, you can type 155.25.0.0/255.255.0.0 in the destination host mask field. If the destination host’s IP address is 155.25.3.5, the SOCKS server applies the mask to the IP address and determines that the destination host’s IP address matches the IP address for which the proxy entry applies (155.25.0.0).
-
In the Destination Port Range field, type the ports on the destination host for which the proxy entry applies.
Do not use spaces in the port range entry. If you do not specify a port range, the proxy entry applies to all ports.
You can use brackets [ ] to include the ports at each end of the range or parentheses ( ) to exclude them. For example, [1000-1010] means all port numbers between and including 1000 and 1010, while (1000-1010) means all port numbers between, but not including, 1000 and 1010. You can also mix brackets and parentheses. For instance, (1000-1010] means all numbers between 1000 and 1010, excluding 1000, but including 1010.
-
In the Destination Proxy Address field, type the host name or IP address of the Proxy Server to use.
-
In the Destination Proxy Port field, type the port number on which the Proxy Server will listen for SOCKS requests.
-
From the Insert drop-down list, select the position for this entry in the socks5.conf file and click OK.
Because you can have multiple routing methods, you must specify the order in which they are evaluated.
 To Edit Routing Entries
To Edit Routing Entries
-
Access the Server Manager for a server instance and click the SOCKS tab.
-
Click the Set SOCKS v5 Routing link.
-
Select the entry you want to edit.
-
Click the Edit button.
-
Make changes as desired.
-
Click OK.
 To Delete Routing Entries
To Delete Routing Entries
-
Access the Server Manager for a server instance and click the SOCKS tab.
-
Click the Set SOCKS v5 Routing link.
-
Select the entry you want to delete.
-
Click the Delete button.
 To Move Routing Entries
To Move Routing Entries
Entries are evaluated in the order in which they appear in the socks5.conf file. You can change the order by moving them.
- © 2010, Oracle Corporation and/or its affiliates
