Chapter 7 TCP/IP Network Reference
This chapter provides TCP/IP network reference information about TCP/IP configuration files, including the types, their purpose, and the format of the file entries. The existing network databases are also described in detail.
The chapter also shows how the structure of IPv4 addresses are derived based on defined network classifications and subnet numbers.
TCP/IP Configuration Files
Each machine on the network gets its TCP/IP configuration information from the following TCP/IP configuration files and network databases:
-
/etc/hostname.interface file
-
/etc/nodename file
-
/etc/defaultdomain file
-
/etc/defaultrouter file (optional)
-
hosts database
-
ipnodes database
-
netmasks database (optional)
The Solaris installation program creates these files as part of the installation process. You can also edit the files manually, as explained in this section. The hosts and netmasks databases are two of the network databases read by the name services available on Solaris networks. "Network Databases and nsswitch.conf File" describes the concept of network databases in detail. For information on the ipnodes file, see "/etc/inet/ipnodes File".
/etc/hostname.interface File
This file defines the network interfaces on the local host for IPv4. At least one /etc/hostname.interface file should exist on the local machine. The Solaris installation program creates this file for you. In the file name, interface is replaced by the device name of the primary network interface.
Note -
If you add a new network interface to your system after the initial Solaris software installation, you must create an /etc/hostname.interface file for that interface, add the interface's IP address to the /etc/inet/hosts file, and reboot the system with the -r option. See substeps within "How to Configure a Host for Local Files Mode" for instructions. Also, in order for the Solaris software to recognize and use the new network interface, you need to load the interface's device driver into the appropriate directory. Refer to the documentation that comes with the new network interface for the appropriate interface name and device driver instructions.
The file contains only one entry: the host name or IPv4 address associated with the network interface. For example, suppose smc0 is the primary network interface for a machine called tenere. Its /etc/hostname.interface file would have the name /etc/hostname.smc0; the file would contain the entry tenere.
Files for Multiple Network Interfaces
If a machine contains more than one network interface, you must create additional /etc/hostname.interface files for the additional network interfaces. You must create these files with a text editor; the Solaris installation program does not create them for you.
For example, consider the machine timbuktu, shown in Figure 6-1. It has two network interfaces and functions as a router. The primary network interface le0 is connected to network 192.9.200. Its IP address is 192.9.200.70, and its host name is timbuktu. The Solaris installation program creates the file /etc/hostname.le0 for the primary network interface and enters the host name timbuktu in the file.
The second network interface is le1; it is connected to network 192.9.201. Although this interface is physically installed on machine timbuktu, it must have a separate IPv4 address. Therefore, you have to manually create the /etc/hostname.le1 file for this interface; the entry in the file would be the router`s name, timbuktu-201.
/etc/hostname6.interface File
IPv6 uses the file /etc/hostname6.interface at start-up to automatically define network interfaces in the same way IPv4 uses /etc/hostname.interface. At least one /etc/hostname. or /etc/hostname6. file should exist on the local machine. The Solaris installation program creates these files for you. In the file name, replace interface with the device name of the primary network interface. For more information about the /etc/hostname6.interface file, see "IPv6 Network Interface Configuration File".
/etc/nodename File
This file should contain one entry: the host name of the local machine. For example, on machine timbuktu, the file /etc/nodename would contain the entry timbuktu.
/etc/defaultdomain File
This file should contain one entry, the fully qualified domain name of the administrative domain to which the local host's network belongs. You can supply this name to the Solaris installation program or edit the file at a later date.
In Figure 6-1, the networks are part of the domain deserts.worldwide, which was classified as a .com domain. Therefore, /etc/defaultdomain should contain the entry deserts.worldwide.com. For more information on network domains, refer to the Solaris Naming Administration Guide.
/etc/defaultrouter File
This file should contain an entry for each router directly connected to the network. The entry should be the name for the network interface that functions as a router between networks.
In Figure 6-1, the network interface le1 connects machine timbuktu with network 192.9.201. This interface has the unique name timbuktu-201. Thus, the machines on network 192.9.200 that are configured in local files mode have the name timbuktu-201 as the entry in /etc/defaultrouter.
hosts Database
The hosts database contains the IPv4 addresses and host names of machines on your network. If you use the NIS, NIS+, or DNS name services, the hosts database is maintained in a database designated for host information. For example, on a network running NIS+, the hosts database is maintained in the host table.
If you use local files for name service, the hosts database is maintained in the /etc/inet/hosts file. This file contains the host names and IPv4 addresses of the primary network interface, other network interfaces attached to the machine, and any other network addresses that the machine must know about.
Note -
For compatibility with BSD-based operating systems, the file /etc/hosts is a symbolic link to /etc/inet/hosts.
/etc/inet/hosts File Format
The /etc/inet/hosts file uses the basic syntax that follows. (Refer to the hosts(4) man page for complete syntax information.)
IPv4-address hostname [nicknames] [#comment]
IPv4-address contains the IPv4 address for each interface that the local host must recognize.
hostname contains the host name assigned to the machine at setup, plus the host names assigned to additional network interfaces that the local host must recognize.
[nickname] is an optional field containing a nickname for the host.
[# comment] is an optional field for a comment.
Initial /etc/inet/hosts File
When you run the Solaris installation program on a machine, it sets up the initial /etc/inet/hosts file. This file contains the minimum entries that the local host requires: its loopback address, its IPv4 address, and its host name.
For example, the Solaris installation program might create the following /etc/inet/hosts file for machine tenere shown in Figure 6-1:
Example 7-1 /etc/inet/hosts File for Machine ahaggar
127.0.0.1 localhost loghost #loopback address 192.9.200.3 tenere #host name |
Loopback Address
In Example 7-1, the IPv4 address 127.0.0.1 is the loopback address, the reserved network interface used by the local machine to allow interprocess communication so that it sends packets to itself. The ifconfig command uses the loopback address for configuration and testing, as explained in "ifconfig Command". Every machine on a TCP/IP network must use the IP address 127.0.0.1 for the local host.
Host Name
The IPv4 address 192.9.200.1 and the name tenere are the address and host name of the local machine. They are assigned to the machine's primary network interface.
Multiple Network Interfaces
Some machines have more than one network interface, because they ar eeither routers or multihomed hosts. Each additional network interface attached to the machine requires its own IPv4 address and associated name. When you configure a router or multihomed host, you must add this information manually to the router's /etc/inet/hosts file. (See "Configuring Routers" for more information on setting up routers and multihomed hosts.)
Example 7-2 is the /etc/inet/hosts file for machine timbuktu shown in Figure 6-1.
Example 7-2 /etc/inet/hosts File for Machine timbuktu
127.0.0.1 localhost loghost 192.9.200.70 timbuktu #This is the local host name 192.9.201.10 timbuktu-201 #Interface to network 192.9.201 |
With these two interfaces, timbuktu connects networks 192.9.200 and 192.9.201 as a router.
How Name Services Affect the hosts Database
The NIS, NIS+, and DNS name services maintain host names and addresses on one or more servers. These servers maintain hosts databases containing information for every host and router (if applicable) on the servers' network. Refer to the Solaris Naming Administration Guide for more information about these services.
When Local Files Provide Name Service
On a network using local files for name service, machines running in local files mode consult their individual /etc/inet/hosts files for IPv4 addresses and host names of other machines on the network. Therefore, their /etc/inet/hosts files must contain the:
-
Loopback address
-
IPv4 address and host name of the local machine (primary network interface)
-
IPv4 address and host name of additional network interfaces attached to this machine, if applicable
-
IPv4 addresses and host names of all hosts on the local network
-
IPv4 addresses and host names of any routers this machine must know about, if applicable
-
IPv4 address of any machine your machine wants to refer to by its host name
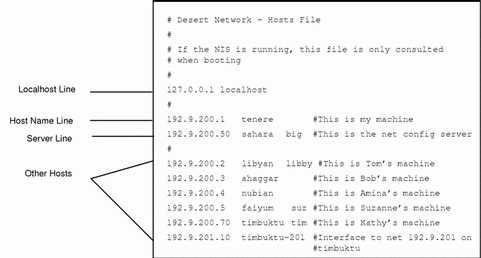
The figure below shows the /etc/inet/hosts file for machine tenere, a machine that runs in local files mode. Notice that the file contains the IPv4 addresses and host names for every machine on the 192.9.200 network. It also contains the IPv4 address and interface name timbuktu-201, which connects the 192.9.200 network to the 192.9.201 network.
A machine configured as a network client uses the local /etc/inet/hosts file for its loopback address and IPv4 address.
Figure 7-1 /etc/inet/hosts File for Machine Running in Local Files Mode
ipnodes Database
The ipnodes database contains the IPv6 addresses and host names of machines on your network. If you use the NIS, NIS+, or DNS name services, the ipnodes database is maintained in a database designated for host information. For example, on a network running NIS+, the ipnodes database is maintained in the host table. For more information about the ipnodes database, see "/etc/inet/ipnodes File".
netmasks Database
You need to edit the netmasks database as part of network configuration only if you have set up subnetting on your network. The netmasks database consists of a list of networks and their associated subnet masks.
Note -
When you create subnets, each new network must be a separate physical network. You cannot apply subnetting to a single physical network.
What Is Subnetting?
Subnetting is a method for getting the most out of the limited 32-bit IPv4 addressing space and reducing the size of the routing tables in a large internetwork. With any address class, subnetting provides a means of allocating a part of the host address space to network addresses, which lets you have more networks. The part of the host address space allocated to new network addresses is known as the subnet number.
In addition to making more efficient use of the IPv4 address space, subnetting has several administrative benefits. Routing can become very complicated as the number of networks grows. A small organization, for example, might give each local network a class C number. As the organization grows, administering a number of different network numbers could become complicated. A better idea is to allocate a few class B network numbers to each major division in an organization. For instance, you could allocate one to Engineering, one to Operations, and so on. Then, you could divide each class B network into additional networks, using the additional network numbers gained by subnetting. This can also reduce the amount of routing information that must be communicated among routers.
Creating the Network Mask for IPv4 Addresses
As part of the subnetting process, you need to select a network-wide netmask. The netmask determines how many and which bits in the host address space represent the subnet number and how many and which represent the host number. Recall that the complete IPv4 address consists of 32 bits. Depending on the address class, as many as 24 bits and as few as 8 bits can be available for representing the host address space. The netmask is specified in the netmasks database.
If you plan to use subnets, you must determine your netmask before you configure TCP/IP. If you plan to install the operating system as part of network configuration, the Solaris installation program requests the netmask for your network.
As described in "Administering Network Numbers", 32-bit IP addresses consist of a network part and a host part. The 32 bits are divided into 4 bytes. Each byte is assigned to either the network number or the host number, depending on the network class.
For example, in a class B IPv4 address, the 2 left-hand bytes are assigned to the network number, and the 2 right-hand bytes are assigned to the host number. In the class B IPv4 address 129.144.41.10, you can assign the 2 right-hand bytes to hosts.
If you are going to implement subnetting, you need to use some of the bits in the bytes assigned to the host number to apply to subnet addresses. For example, a 16-bit host address space provides addressing for 65,534 hosts. If you apply the third byte to subnet addresses and the fourth to host addresses, you can address up to 254 networks, with up to 254 hosts on each.
The bits in the host address bytes that are applied to subnet addresses and those applied to host addresses are determined by a subnet mask. Subnet masks are used to select bits from either byte for use as subnet addresses. Although netmask bits must be contiguous, they need not align on byte boundaries.
The netmask can be applied to an IPv4 address using the bit-wise logical AND operator. This operation selects out the network number and subnet number positions of the address.
It is easiest to explain netmasks in terms of their binary representation. You can use a calculator for binary-to-decimal conversion. The following examples show both the decimal and binary forms of the netmask.
If a netmask 255.255.255.0 is applied to the IPv4 address 129.144.41.101, the result is the IPv4 address of 129.144.41.0.
129.144.41.101 & 255.255.255.0 = 129.144.41.0
In binary form, the operation is:
10000001.10010000.00101001.01100101 (IPv4 address)
ANDed with
11111111.11111111.11111111.00000000 (netmask)
Now the system looks for a network number of 129.144.41 instead of a network number of 129.144. If your network has the number 129.144.41, that is what the system looks for and finds. Because you can assign up to 254 values to the third byte of the IPv4 address space, subnetting lets you create address space for 254 networks, where previously there was room for only one.
If you want to provide address space for only two additional networks, you could use a subnet mask of:
255.255.192.0
This netmask provides a result of:
11111111.11111111.1100000.00000000
This still leaves 14 bits available for host addresses. Since all 0s and 1s are reserved, at least two bits must be reserved for the host number.
The /etc/inet/netmasks File
If your network runs NIS or NIS+, the servers for these name services maintain netmasks databases. For networks that use local files for name service, this information is maintained in the /etc/inet/netmasks file.
Note -
For compatibility with BSD-based operating systems, the file /etc/netmasks is a symbolic link to /etc/inet/netmasks.
The following example shows the /etc/inet/netmasks file for a class B network.
Example 7-3 /etc/inet/netmasks File for a Class B Network
## The netmasks file associates Internet Protocol (IPv4) address # masks with IPv4 network numbers. # # network-number netmask # # Both the network-number and the netmasks are specified in # "decimal dot" notation, e.g: # # 128.32.0.0 255.255.255.0 129.144.0.0 255.255.255.0 |
If the file does not exist, create it. Use the following syntax:
network-number netmask-number
Refer to the netmasks(4) man page for complete details.
When creating netmask numbers, type the network number assigned by the InterNIC (not the subnet number) and netmask number in /etc/inet/netmasks. Each subnet mask should be on a separate line.
For example:
128.78.0.0 255.255.248.0 |
You can also type symbolic names for network numbers in the /etc/inet/hosts file. You can then use these network names instead of the network numbers as parameters to commands.
Network Databases and nsswitch.conf File
The network databases are files that provide information needed to configure the network. The network databases are:
-
hosts
-
ipnodes
-
netmasks
-
ethers
-
bootparams
-
protocols
-
services
-
networks
As part of the configuration process, you edit the hosts database and the netmasks database, if your network is subnetted. Two network databases, bootparams and ethers, are used to configure machines as network clients. The remaining databases are used by the operating system and seldom require editing.
Although it is not a network database, the nsswitch.conf file needs to be configured along with the relevant network databases. nsswitch.conf specifies which name service to use for a particular machine: NIS, NIS+, DNS, or local files.
How Name Services Affect Network Databases
Your network database takes a form that depends on the type of name service you select for your network. For example, the hosts database contains, at minimum, the host name and IPv4 address of the local machine and any network interfaces directly connected to the local machine. However, the hosts database could contain other IPv4 addresses and host names, depending on the type of name service on your network.
The network databases are used as follows:
-
Networks that use local files for their name service rely on files in the /etc/inet and /etc directories
Note -
DNS boot and data files do not correspond directly to the network databases.
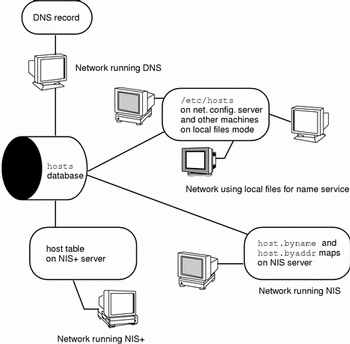
The following figure shows the forms of the hosts database used by these name services:
Figure 7-2 Forms of the hosts Database Used by Name Services
The following table lists the network databases and how they are used by local files, NIS+, and NIS.
Table 7-1 Network Databases and Corresponding Name Service Files|
Network Database |
Local Files |
NIS+ Tables |
NIS Maps |
|---|---|---|---|
|
/etc/inet/hosts |
hosts.org_dir |
hosts.byaddr hosts.byname |
|
|
ipnodes |
/etc/inet/ipnodes |
ipnodes.org_dir |
ipnodes.byaddr ipnodes.byname |
|
/etc/inet/netmasks |
netmasks.org_dir |
netmasks.byaddr |
|
|
/etc/ethers |
ethers.org_dir |
ethers.byname ethers.byaddr |
|
|
/etc/bootparams |
bootparams.org_dir |
bootparams |
|
|
/etc/inet/protocols |
protocols.org_dir |
protocols.byname protocols.bynumber |
|
|
/etc/inet/services |
services.org_dir |
services.byname |
|
|
/etc/inet/networks |
networks.org_dir |
networks.byaddr networks.byname |
This book discusses network databases as viewed by networks using local files for name services. Information regarding the hosts database is in "hosts Database"; information regarding the ipnodes database is in "/etc/inet/ipnodes File"; information regarding the netmasks database is in "netmasks Database". Refer to Solaris Naming Administration Guide for information on network databases correspondences in NIS, DNS, and NIS+.
nsswitch.conf File -- Specifying Which Name Service to Use
The /etc/nsswitch.conf file defines the search order of the network databases. The Solaris installation program creates a default /etc/nsswitch.conf file for the local machine, based on the name service you indicate during the installation process. If you selected the "None" option, indicating local files for name service, the resulting nsswitch.conf file resembles the following example.
Example 7-4 nsswitch.conf for Networks Using Files for Name Service
# /etc/nsswitch.files: # # An example file that could be copied over to /etc/nsswitch.conf; # it does not use any naming service. # # "hosts:" and "services:" in this file are used only if the # /etc/netconfig file contains "switch.so" as a # nametoaddr library for "inet" transports. passwd: files group: files hosts: files networks: files protocols: files rpc: files ethers: files netmasks: files bootparams: files publickey: files # At present there isn't a 'files' backend for netgroup; the # system will figure it out pretty quickly, # and won't use netgroups at all. netgroup: files automount: files aliases: files services: files sendmailvars: files |
The nsswitch.conf(4) man page describes the file in detail. Its basic syntax is:
database name-service-to-search
The database field can list one of many types of databases searched by the operating system. For example, it could indicate a database affecting users, such as passwd or aliases, or a network database. The parameter name-service-to-search can have the values files, nis, or nis+ for the network databases. (The hosts database can also have dns as a name service to search.) You can also list more than one name service, such as nis+ and files.
In Example 7-4, the only search option indicated is files. Therefore, the local machine gets security and automounting information, in addition to network database information, from files located in its /etc and /etc/inet directories.
Changing nsswitch.conf
The /etc directory contains the nsswitch.conf file created by the Solaris installation program. It also contains template files for the following name services:
-
nsswitch.files
-
nsswitch.nis
-
nsswitch.nis+
If you want to change from one name service to another, you can copy the appropriate template to nsswitch.conf. You can also selectively edit the nsswitch.conf file, and change the default name service to search for individual databases.
For example, on a network running NIS, you might have to change the nsswitch.conf file on network clients. The search path for the bootparams and ethers databases must list files as the first option, and nis. The following example shows the correct search paths.
Example 7-5 nsswitch.conf for a Client on a Network Running NIS
## /etc/nsswitch.conf:# . . passwd: files nis group: file nis # consult /etc "files" only if nis is down. hosts: nis [NOTFOUND=return] files networks: nis [NOTFOUND=return] files protocols: nis [NOTFOUND=return] files rpc: nis [NOTFOUND=return] files ethers: files [NOTFOUND=return] nis netmasks: nis [NOTFOUND=return] files bootparams: files [NOTFOUND=return] nis publickey: nis netgroup: nis automount: files nis aliases: files nis # for efficient getservbyname() avoid nis services: files nis sendmailvars: files |
For complete details on the name service switch, refer to Solaris Naming Administration Guide.
bootparams Database
The bootparams database contains information used by machines configured to boot in the network client mode. You need to edit it if your network will have network clients. (See "Configuring Network Clients" for procedures.) The database is built from information entered into the /etc/bootparams file.
The bootparams(4) man page contains complete syntax for this database. Its basic syntax is shown in the example below:
machine-name file-key-server-name:pathname
For each network client machine, the entry might contain the following information: the name of the client, a list of keys, the names of servers, and path names.
The first item of each entry is the name of the client machine. Next is a list of keys, names of servers, and path names, separated by tab characters. All items but the first are optional. The database can contain a wildcard entry that will be matched by all clients. Here is an example:
Example 7-6 bootparams Database
myclient root=myserver : /nfsroot/myclient \ swap=myserver : /nfsswap//myclient \ dump=myserver : /nfsdump/myclient |
In this example, the term dump=: tells client hosts not to look for a dump file.
Wildcard Entry for bootparams
In most cases, you will want to use the wildcard entry when editing the bootparams database to support clients. This entry is:
* root=server:/path dump=:
The asterisk (*) wildcard indicates that this entry applies to all clients not specifically named within the bootparams database.
ethers Database
The ethers database is built from information entered into the /etc/ethers file. It associates host names to their Ethernet addresses. You need to create an ethers database only if you are running the RARP daemon--that is, if you are configuring network clients.
RARP uses the file to map Ethernet addresses to IP addresses. If you are running the RARP daemon in.rarpd, you need to set up the ethers file and maintain it on all hosts running the daemon to reflect changes to the network.
The ethers(4) man page contains complete syntax information for this database. Its basic format is:
Ethernet-address hostname #comment
Ethernet-address is the Ethernet address of the host.
hostname is the official name of the host.
#comment is any kind of note you want to append to an entry in the file.
The equipment manufacturer provides the Ethernet address. If a machine does not display the Ethernet address when you power up, see your hardware manuals for assistance.
When adding entries to the ethers database, make sure that host names correspond to the primary names in the hosts and ipnodes databases, not to the nicknames, as shown below.
Example 7-7 Entries in the ethers Database
8:0:20:1:40:16 fayoum 8:0:20:1:40:15 nubian 8:0:20:1:40:7 sahara # This is a comment 8:0:20:1:40:14 tenere |
Other Network Databases
The remaining network databases seldom need to be edited.
networks database
The networks database associates network names with network numbers, enabling some applications to use and display names rather than numbers. The networks database is based on information in the /etc/inet/networks file. It contains the names of all networks to which your network connects via routers.
The Solaris installation program sets up the initial networks database. The only time you need to update it is when you add a new network to your existing network topology.
The networks(4) man page contains full syntax information for /etc/inet/networks. Here is its basic format
network-name network-number nickname(s) #comment
network-name is the official name for the network.
network-number is the number assigned by the InterNIC.
nickname is any other name by which the network is known.
#comment is any kind of note you want to append to an entry in the file.
It is particularly important that you maintain the networks file. The netstat program uses the information in this database to produce status tables.
A sample /etc/networks file is shown below.
Example 7-8 /etc/networks File
#ident "@(#)networks 1.4 92/07/14 SMI" /* SVr4.0 1.1 */ # # The networks file associates Internet Protocol (IP) network numbers with network names. The format of this file is: # # network-name network-number nicnames . . . # The loopback network is used only for intra-machine communication #loopback 127 # Internet networks # arpanet 10 arpa # Historical ucb-ether 46 ucbether # # local networks eng 193.9.0 #engineering acc 193.9.1 #accounting prog 193.9.2 #programming |
protocols Database
The protocols database lists the TCP/IP protocols installed on your system and their numbers; the Solaris installation program automatically creates it. It is rare when this file requires administrative handling.
The protocols database contains the names of the TCP/IP protocols installed on the system. Its syntax is completely described in the protocols(4) man page. An example of the /etc/inet/protocols file is shown below.
Example 7-9 /etc/inet/protocols File
# # Internet (IP) protocols # ip 0 IP # internet protocol, pseudo protocol number icmp 1 ICMP # internet control message protocol tcp 6 TCP # transmission control protocol udp 17 UDP # user datagram protocol |
services Database
The services database lists the names of TCP and UDP services and their wellknown port numbers; it is used by programs that call network services. The Solaris installation automatically creates the services database; it generally requires no administrative handling.
The services(4) man page contains complete syntax information. An excerpt from a typical /etc/inet/services file is shown below.
Example 7-10 /etc/inet/services File
# # Network services # echo 7/udp echo 7/tcp discard 9/udp sink null discard 11/tcp daytime 13/udp daytime 13/tcp netstat 15/tcp ftp-data 20/tcp ftp 21/tcp telnet 23/tcp time 37/tcp timeserver time 37/udp timeserver name 42/udp nameserver whois 43/tcp nickname |
Overview of the Booting Processes
The following information is provided for your reference. It is a brief overview of the network booting processes to help you better visualize what is happening during configuration.
Note -
The names of startup scripts might change from one release to another.
-
You start the operating system on a host.
-
The kernel runs /sbin/init, as part of the booting process.
-
/sbin/init runs the /etc/rcS.d/S30rootusr.sh. startup script.
-
The script runs a number of system startup tasks, including establishing the minimum host and network configurations for diskless and dataless operations. /etc/rcS.d/S30rootusr.sh also mounts the /usr file system.
-
If the local database files contain the required configuration information (host name and IP address), the script uses it.
-
If the information is not available in local host configuration files, /etc/rcS.d/S30rootusr.sh uses RARP to acquire the host's IP address.
-
-
If the local files contain domain name, host name, and default router address, the machine uses them. If the configuration information is not in local files, then the system uses the Bootparams protocol to acquire the host name, domain name, and default router address. Note that the required information must be available on a network configuration server that is located on the same network as the host. This is necessary because no internetwork communications exist at this point.
-
After /etc/rcS/S30rootusr.sh completes its tasks and several other boot procedures have executed, /etc/rc2.d/S69inet runs. This script executes startup tasks that must be completed before the name services (NIS, NIS+, or DNS) can start. These tasks include configuring the IP routing and setting the domain name.
-
At completion of the S69inet tasks, /etc/rc2.d/S71rpc runs. This script starts the NIS, NIS+, or DNS name service.
-
After /etc/rc2.d/S71 runs, /etc/rc2.d/S72inetsvc runs. This script starts up services that depend on the presence of the name services. S72inetsvc also starts the daemon inetd, which manages user services such as telnet.
See System Administration Guide, Volume 1 for a complete description of the booting process.
Routing Protocols
Solaris system software supports two routing protocols: Routing Information Protocol (RIP) and ICMP Router Discovery (RDISC). RIP and RDISC are both standard TCP/IP protocols.
Routing Information Protocol (RIP)
RIP is implemented by in.routed, the routing daemon, which automatically starts when the machine boots. When run on a router with the s option specified, in.routed fills the kernel routing table with a route to every reachable network and advertises "reachability" through all network interfaces.
When run on a host with the q option specified, in.routed extracts routing information but does not advertise reachability. On hosts, routing information can be extracted in two ways:
-
Do not specify the S flag (capital "S": "Space-saving mode") and in.routed builds a full routing table exactly as it does on a router.
-
Specify the S flag and in.routed creates a minimal kernel table, containing a single default route for each available router.
ICMP Router Discovery (RDISC) Protocol
Hosts used RDISC to obtain routing information from routers. Thus, when hosts are running RDISC, routers must also run another protocol, such as RIP, in order to exchange router information among themselves.
RDISC is implemented by in.rdisc, which should run on both routers and hosts. Normally, when in.rdisc runs on a host, it enters a default route for each router that is also running in.rdisc. A host that is running in.rdisc can not discover routers that are running only RIP. Furthermore, when routers are running in.rdisc (rather than in.routed), they can be configured to have a different preference, which causes hosts to select a better router. See the rdisc(1M) man page.
How a Machine Determines if it Is a Router
The /etc/rc2.d/S69inet startup script, which runs when the machine boots, determines whether a machine is a router or a host. This decision also determines whether the routing protocols (RIP and RDISC) should run in router mode or host mode.
The /etc/rc2.d/S69inet script concludes that a machine is a router if the following two conditions exist:
-
More than one /etc/hostname.interface file exists.
-
More than one interface was configured "up" by the ifconfig command. (See the ifconfig(1M) man page.)
If only one interface is found, the script concludes that the machine is a host. See "Configuring Both Router Network Interfaces". An interface that is configured by any means other than an /etc/hostname.interface file is not taken into account.
Parts of the IPv4 Address
Each network running TCP/IP must have a unique network number, and every machine on it must have a unique IP address. It is important to understand how IP addresses are constructed before you register your network and obtain its network number. This section describes IPv4 addresses. For information on IPv6 addresses, see "IPv6 Addressing".
The IPv4 address is a 32-bit number that uniquely identifies a network interface on a machine. An IPv4 address is typically written in decimal digits, formatted as four 8-bit fields separated by periods. Each 8-bit field represents a byte of the IPv4 address. This form of representing the bytes of an IPv4 address is often referred to as the dotted-decimal format.
The bytes of the IPv4 address are further classified into two parts: the network part and the host part. The following figure shows the component parts of a typical IPv4 address, 129.144.50.56.
Figure 7-3 Parts of an IPv4 Address
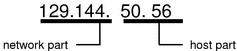
Network Part
This part specifies the unique number assigned to your network. It also identifies the class of network assigned. In Figure 7-3, the network part takes up two bytes of the IPv4 address.
Host Part
This is the part of the IPv4 address that you assign to each host. It uniquely identifies this machine on your network. Note that for each host on your network, the network part of the address will be the same, but the host part must be different.
Subnet Number (Optional)
Local networks with large numbers of hosts are sometimes divided into subnets. If you choose to divide your network into subnets, you need to assign a subnet number for the subnet. You can maximize the efficiency of the IPv4 address space by using some of the bits from the host number part of the IPv4 address as a network identifier. When used as a network identifier, the specified part of the address becomes the subnet number. You create a subnet number by using a netmask, which is a bit mask that selects the network and subnet parts of an IPv4 address. (Refer to "Creating the Network Mask for IPv4 Addresses" for details.)
Network Classes
The first step in planning for IPv4 addressing on your network is to determine which network class is appropriate for your network. After you have done this, you can take the crucial second step: obtain the network number from the InterNIC addressing authority.
Currently there are three classes of TCP/IP networks. Each class uses the 32-bit IPv4 address space differently, providing more or fewer bits for the network part of the address. These classes are class A, class B, and class C.
Class A Network Numbers
A class A network number uses the first eight bits of the IPv4 address as its "network part." The remaining 24 bits makeup the host part of the IPv4 address, as illustrated below.
Figure 7-4 Byte Assignment in a Class A Address
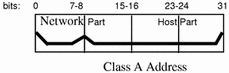
The values assigned to the first byte of class A network numbers fall within the range 0-127. Consider the IPv4 address 75.4.10.4. The value 75 in the first byte indicates that the host is on a class A network. The remaining bytes, 4.10.4, establish the host address. The InterNIC assigns only the first byte of a class A number. Use of the remaining three bytes is left to the discretion of the owner of the network number. Only 127 class A networks can exist. Each one of these numbers can accommodate up to 16,777,214 hosts.
Class B Network Numbers
A class B network number uses 16 bits for the network number and 16 bits for host numbers. The first byte of a class B network number is in the range 128-191. In the number 129.144.50.56, the first two bytes, 129.144, are assigned by the InterNIC, and makeup the network address. The last two bytes, 50.56, make up the host address, and are assigned at the discretion of the owner of the network number. The following figure graphically illustrates a class B address.
Figure 7-5 Byte Assignment in a Class B Address
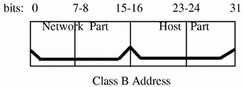
Class B is typically assigned to organizations with many hosts on their networks.
Class C Network Numbers
Class C network numbers use 24 bits for the network number and 8 bits for host numbers. Class C network numbers are appropriate for networks with few hosts--the maximum being 254. A class C network number occupies the first three bytes of an IPv4 address. Only the fourth byte is assigned at the discretion of the network owners. The following figure graphically represents the bytes in a class C address.
Figure 7-6 Byte Assignment in a Class C Address
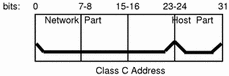
The first byte of a class C network number covers the range 192-223. The second and third each cover the range 1- 255. A typical class C address might be 192.5.2.5. The first three bytes, 192.5.2, form the network number. The final byte in this example, 5, is the host number.
- © 2010, Oracle Corporation and/or its affiliates
