NIS+ Authorization and Access--Introduction
The basic purpose of NIS+ authorization is to specify the access rights that each NIS+ principal has for each NIS+ object and service.
Once the principal making an NIS+ request is authenticated, NIS+ places them in an authorization class. The access rights (permissions) that specify which activities a principal may do with a given NIS+ object are assigned on a class basis. In other words, one authorization class may have certain access rights while a different class has different rights.
-
Authorization classes. There are four authorization classes: owner, group, world, and nobody. (See "Authorization Classes" below for details.)
-
Access rights. There are four types of access rights (permissions): create, destroy, modify, and read. (See " NIS+ Access Rights" for details.)
Authorization Classes
NIS+ objects do not grant access rights directly to NIS+ principals. Instead, they grant access rights to four classes of principal:
-
Owner. The principal who happens to be the object's owner gets the rights granted to the owner class.
-
Group. Each NIS+ object has one group associated with it. The members of an object's group are specified by the NIS+ administrator. The principals who belong to the object's group class get the rights granted to the group class. (In this context, group refers to NIS+ groups, not UNIX or net groups.)
-
World. The world class encompasses all NIS+ principals that a server has been able to authenticate. (That is, everyone who has been authenticated but who is not in either the owner or group classes.)
-
Nobody. Everyone belongs to the nobody class even those who are not authenticated.
Figure 6-4 Authorization Classes
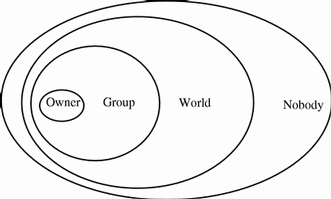
For any NIS+ request, the system determines which class the requesting principal belongs to and the principal then can use whatever access rights belonging to that class.
An object can grant any combination of access rights to each of these classes. Normally, however, a higher class is assigned the same rights as all the lower classes, plus possible additional rights.
For instance, an object could grant read access to the nobody and world classes; both read and modify access to the group class; and read, modify, create, and destroy access to the owner class.
The four classes are described in detail below.
The Owner Class
The owner is a single NIS+ principal.
A principal making a request for access to an NIS+ object must be authenticated (present a valid DES credential) before being granted owner access rights.
By default, an object's owner is the principal that created the object. However, an object's owner can cede ownership to another principal in two ways:
-
One way is for the principal to specify a different owner at the time the object is created (see "Specifying Access Rights in Commands").
-
A second way is for the principal to change the ownership of the object after it is created (see "Changing Ownership of Objects and Entries").
Once a principal gives up ownership, that principal gives up all owner's access rights to the object and keeps only the rights the object assigns to either the group, the world, or nobody.
The Group Class
The object's group is a single NIS+ group. (In this context, group refers to NIS+ groups, not UNIX or net groups.)
A principal making a request for access to an NIS+ object must be authenticated (present a valid DES credential) and belong to the group before being granted group access rights.
An NIS+ group is a collection of NIS+ principals, grouped together as a convenience for providing access to the namespace. The access rights granted to an NIS+ group apply to all the principals that are members of that group. (An object's owner, however, does not need to belong to the object's group.)
When an object is created it may be assigned a default group. A nondefault group can be specified for an object when it is created or later. An object's group may be changed at any time.
Note -
Information about NIS+ groups is not stored in the NIS+ group table. The group table stores information about UNIX groups. Information about NIS+ groups is stored in the appropriate groups_dir directory object.
Information about NIS+ groups is stored in NIS+ group objects, under the groups_dir subdirectory of every NIS+ domain:
Figure 6-5 NIS+ Directory Structure
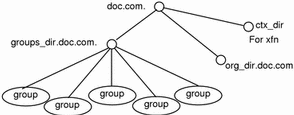
Instructions for administering NIS+ groups are provided in Chapter 12, Administering NIS+ Groups.
The World Class
The world class contains all NIS+ principals that are authenticated by NIS+. In other words, the world class includes everyone in the owner and group class, plus everyone else who presents a valid DES credential.
Access rights granted to the world class apply to all authenticated principals.
The Nobody Class
The nobody class is composed of anyone who is not properly authenticated. In other words, the nobody class includes everyone who does not present a valid DES credential.
Authorization Classes and the NIS+ Object Hierarchy
There is a hierarchy of NIS+ objects and authorization classes that can apply independently to each level. The standard default NIS+ directory hierarchy is:
-
Directory level. In each NIS+ domain there are two NIS+ directory objects: groups_dir and org_dir. Each groups_dir directory object contains various groups. Each org_dir directory object contains various tables.
-
Group level or table level. Groups contain individual entries and possibly other groups. Tables contain both columns and individual entries.
-
Column level. A given table will have one or more columns.
-
Entry (row) level. A given group or table will have one or more entries.
The four authorization classes apply at each level. Thus, a directory object will have its own owner and group. The individual tables within a directory object will have their own individual owners and groups which may be different than the owner and group of the directory object. Within a table, an entry (row) may have its own individual owner or group which may be different than the owner and group of the table as a whole or the directory object as a whole. Within a table, individual columns have the same owner and group as the table as a whole.
NIS+ Access Rights
NIS+ objects specify their access rights as part of their object definitions. (You can examine these by using the niscat -o command, described on page 172.)
NIS+ objects specify access rights for NIS+ principals in the same way that UNIX files specify permissions for UNIX users. Access rights specify the types of operations that NIS+ principals are allowed to perform on NIS+ objects.
NIS+ operations vary among different types of objects, but they all fall into one of the four access rights categories: read, modify, create, and destroy.
-
Read A principal with read rights to an object can view the contents of that object.
-
Modify. A principal with modify rights to an object can change the contents of that object.
-
Destroy. A principal with destroy rights to an object can destroy or delete the object.
-
Create. A principal with create rights to a higher level object can create new objects within that level. In other words, if you have create rights to an NIS+ directory object, you can create new tables within that directory. If you have create rights to an NIS+ table, you can create new columns and entries within that table.
Every communication from an NIS+ client to an NIS+ server is, in effect, a request to perform one of these operations on a specific NIS+ object. For instance, when an NIS+ principal requests the IP address of another workstation, it is effectively requesting read access to the hosts table object, which stores that type of information. When a principal asks the server to add a directory to the NIS+ namespace, it is actually requesting modify access to the directory's parent object.
Keep in mind that these rights logically evolve down from directory to table to table column and entry levels. For example, to create a new table, you must have create rights for the NIS+ directory object where the table will be stored. When you create that table, you become its default owner. As owner, you can assign yourself create rights to the table which allows you to create new entries in the table. If you create new entries in a table, you become the default owner of those entries. As table owner, you can also grant table-level create rights to others. For example, you can give your table's group class table-level create rights. In that case, any member of the table's group can create new entries in the table. The individual member of the group who creates a new table entry becomes the default owner of that entry.
- © 2010, Oracle Corporation and/or its affiliates
