Chapter 3 Administering Security
This chapter describes the security features enforced by the CIM Object Manager, including the following topics:
Overview
There are two separate mechanisms for administering security within the Solaris operating environment, WBEM ACL (access control list) based and Solaris RBAC (role-based access control) .
The classes defined in the Solaris_Acl1.0.mof file are used to implement ACL-based security. This provides a default authorization scheme for the Solaris WBEM Services, and applies to all CIM operations. This feature is specific to the Solaris WBEM Services.
Instances of the Solaris_Acl1.0.mof classes determine the default authorizations assigned to a WBEM user and/or namespace. Provider programs, however, are allowed to override this scheme for CIM operations relating to instance manipulation; the Sun Solaris providers use the RBAC scheme to do this.
You can use the (/usr/sadm/bin/wbemadmin) to add users to existing ACLs with either read or write permissions. See "Using the Sun WBEM User Manager to Set Access Control". You can also write WBEM applications using the Solaris_Acl1.0.mof classes to set access control. See "Using the APIs to Set Access Control".
The classes defined in the Solaris_Users1.0.mof file are used to implement Solaris RBAC security for defining user roles and priveleges, via the tool of the . The SMC tool lets you add users to existing roles and grant RBAC rights to existing users. (An RBAC right is managed in the portion of the SMC tool.) See "Solaris Management Console Tool".
Sun WBEM Security Features
The CIM Object Manager validates a user's login information for the machine on which the CIM Object Manager is running. A validated user is granted some form of controlled access to the entire Common Information Model (CIM) Schema. The CIM Object Manager does not provide security for system resources such as individual classes and instances. However, the CIM Object Manager does allow control of global permissions on namespace and access control on a per-user basis.
The following security features protect access to CIM objects on a WBEM-enabled system:
-
Authentication - The process of verifying the identity of a user, device, or other entity in a computer system, often as a prerequisite to allowing access to the resources in a system.
-
Authorization - The granting to a user, program, or process the right of access.
-
Replay protection - The CIM Object Manager protects against a client picking up and sending another client's message to the server by validating a session key.
A client cannot copy another client's last message sent to a CIM Object Manager. The CIM Object Manager uses a MAC for each message, based on a negotiated session key, to guarantee that all communication in the client-server session is with the same client that initiated the session and participated in the client-server authentication.
A MAC is a token parameter added to a remote call which contains security information used to authenticate that single message. It is used to confirm that the message came from the client that was originally authenticated for the session, and that the message is not being replayed from some other client. This type of mechanism is used in WBEM for RMI messages. The session key negotiated in the user authentication exchange is used to encrypt the security information in the message's MAC token.
Note that no digital signing of messages is performed.
Authentication
When a user logs in and enters a user name and password, the client uses the password to generate an encrypted digest which the server verifies. When the user is authenticated, the CIM Object Manager sets up a client session. All subsequent operations occur within that secure client session and contain a MAC token which uses the session key negotiated during authentication.
Authorization
Once the CIM Object Manager has authenticated the user's identity, that identity can be used to verify whether the user should be allowed to execute the application or any of its tasks. The CIM Object Manager supports capability-based authorization, which allows a privileged user to assign read and write access to specific users. These authorizations are added to existing Solaris user accounts.
Solaris Management Console Tool
The SMC tool lets you add users to existing roles and grant RBAC rights to existing users. (An RBAC right is managed in the portion of the SMC tool.)
To Start SMC and Tool
-
Change to the location of the SMC invocation command by typing the following:
# cd /usr/sbin
-
Start SMC by typing the following command:
# smc
-
Double-click on "This Computer" (or single-click the expand/compress icon next to it) in the left-hand Navigation panel to expand the tree beneath it. Do the same for "System Configuration", and you will see the Users icon underneath.
-
Click on the Users icon to start the application.
Figure 3-1 Solaris Management Console, with Users Tool Selected
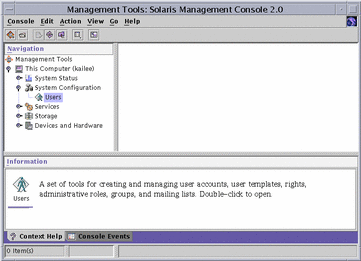
For more information on the , see the man page smc(1M).
Using the Sun WBEM User Manager to Set Access Control
The Sun allows privileged users to add and delete authorized users and to set their access privileges. Use this application to manage user authentication and access to CIM objects on a WBEM-enabled system. A user must have a Solaris user account.
You can set access privileges on individual namespaces or for a user-namespace combination. When you add a user and select a namespace, by default the user is granted read access to CIM objects in the selected namespace. An effective way to combine user and namespace access rights is to first restrict access to a namespace. Then grant individual users read, read and write, or write access to that namespace.
You cannot set access rights on individual managed objects. However you can set access rights for all managed objects in a namespace as well as on a per-user basis.
If you log in as root, you can set the following types of access to CIM objects:
-
Read Only - Allows read-only access to CIM Schema objects. Users with this privilege can retrieve instances and classes, but cannot create, delete, or modify CIM objects.
-
Read/Write - Allows full read, write, and delete access to all CIM classes and instances.
-
Write - Allows write and delete, but not read access to all CIM classes and instances.
-
None - Allows no access to CIM classes and instances.
How to Start Sun WBEM User Manager
-
In a command window, type the command:
# /usr/sadm/bin/wbemadmin
The Sun starts, and the Login dialog box opens. Context-help information is available in the Context Help panel when you click on the fields in the dialog box.
-
In the Login dialog box, do the following:
-
In the User Name field, type the user name.
You must have read access to the root\security namespace to log in. By default, Solaris users have guest privileges, which grant them read access to the default namespaces. Users with read access can view , but cannot change, user privileges.
You must log in as root or a user with write access to the root\security namespace to grant access rights to users.
-
In the Password field, type the password for the user account.
-
-
Click OK.
The User Manager dialog box opens with a list of users and their access rights to WBEM objects within the namespaces on the current host.
How to Grant Default Access Rights to a User
-
In the Users Access portion of the dialog box, click Add.
A dialog box opens that lists the available namespaces.
-
Type the name of a Solaris user account in the User Name text entry field.
-
Select a namespace from the listed namespaces.
-
Click OK.
The user name is added to the User Manager dialog box.
-
Click OK to save the changes and close the User Manager dialog box. Click Apply to save the changes and keep the dialog box open.
This action grants this user read access to CIM objects in the selected namespace.
How to Change Access Rights for a User
-
Start Sun .
-
Select the user whose access rights you want to change.
-
To grant the user read-only access, click the Read check box. To grant the user write access, click the Write check box.
-
Click OK to save the changes and close the User Manager dialog box. Click Apply to save the changes and keep the dialog box open.
How to Remove Access Rights for a User
-
Start Sun .
-
In the Users Access portion of the dialog box, select the user name for which you want to remove access rights.
-
Click Delete to delete the user's access rights to the namespace.
A confirmation dialog box asks you to confirm your decision to delete the user's access rights. Click OK to confirm.
-
Click OK to save the changes and close the User Manager dialog box. Click Apply to save the changes and keep the dialog box open.
How to Set Access Rights for a Namespace
-
Start Sun .
-
In the Namespace Access portion of the dialog box, click Add.
A dialog box opens that lists the available namespaces.
-
Select the namespace for which you want to set access rights.
By default, users have read-only access to a namespace.
-
To allow no access to the namespace, make sure the Read and Write check boxes are not selected.
-
To allow write access, click the Write check box.
-
To allow read access, click the Read check box.
-
-
Click OK to save the changes and close the User Manager dialog box. Click Apply to save the changes and keep the dialog box open.
How to Remove Access Rights for a Namespace
-
Start Sun .
-
In the Namespace Access portion of the dialog box, select the namespace for which you want to remove access control, and then click Delete.
Access control is removed from the namespace, and the namespace is removed from the list of namespaces on the User Manager dialog box.
-
Click OK to save the changes and close the User Manager dialog box. Click Apply to save the changes and keep the dialog box open.
Using the APIs to Set Access Control
You can use the Sun WBEM SDK APIs to set access control on a namespace or on a per-user basis. The following security classes are stored in the root\security namespace:
-
Solaris_Acl - Base class for Solaris Access Control Lists (ACL). This class defines the string property capability and sets its default value to r (read only).
-
Solaris_UserAcl - Represents the access control that a user has to the CIM objects within the specified namespace.
-
Solaris_NamespaceAcl - Represents the access control on a namespace.
You can set access control on individual users to the CIM objects within a namespace by creating an instance of the Solaris_UserACL class and then using the APIs to change the access rights for that instance. Similarly, you can set access control on namespaces by creating an instance of the Solaris_NameSpaceACL class and then using APIs, such as the setInstance method, to set the access rights for that instance.
An effective way to combine the use of these two classes is to first use the Solaris_NameSpaceACL class to restrict access to all users to the objects in a namespace. Then use the Solaris_UserACL class to grant selected users access to the namespace.
The Solaris_UserAcl Class
The Solaris_UserAcl class extends the Solaris_Acl base class, from which it inherits the string property capability with a default value r (read only).
You can set the capability property to any of the following values for access privileges.
| Access Right | Description |
|---|---|
|
r |
Read |
|
rw |
Read and Write |
|
w |
Write |
|
none |
No access |
The Solaris_UserAcl class defines the following two key properties. Only one instance of the namespace-username ACL pair can exist in a namespace.
| Property | Data Type | Purpose |
|---|---|---|
|
nspace |
string |
Identifies the namespace to which this ACL applies. |
|
username |
string |
Identifies the user to which this ACL applies. |
How to Set Access Control on a User
-
Create an instance of the Solaris_UserAcl class. For example:
... /* Create a namespace object initialized with root\security (name of namespace) on the local host. */ CIMNameSpace cns = new CIMNameSpace("", "root\security"); // Connect to the root\security namespace as root. cc = new CIMClient(cns, "root", "root_password"); // Get the Solaris_UserAcl class cimclass = cc.getClass(new CIMObjectPath("Solaris_UserAcl"); // Create a new instance of the Solaris_UserAcl class ci = cimclass.newInstance(); ... -
Set the capability property to the desired access rights. For example:
... /* Change the access rights (capability) to read/write for user Guest on objects in the root\molly namespace.*/ ci.setProperty("capability", new CIMValue(new String("rw")); ci.setProperty("nspace", new CIMValue(new String("root\molly")); ci.setProperty("username", new CIMValue(new String("guest")); ... -
Update the instance. For example:
... // Pass the updated instance to the CIM Object Manager cc.setInstance(new CIMObjectPath(), ci); ...
The Solaris_NamespaceAcl Class
The Solaris_NamespaceAcl extends the Solaris_Acl base class, from which it inherits the string property capability with a default value r (read-only for GUEST and all users). The Solaris_NamespaceAcl class defines the following key property.
| Property | Data Type | Purpose |
|---|---|---|
|
nspace |
string |
Identifies the namespace to which this access control list applies. Only one instance of the namespace ACL can exist in a namespace. |
How to Set Access Control on a Namespace
-
Create an instance of the Solaris_namespaceAcl class. For example:
... /* Create a namespace object initialized with root\security (name of namespace) on the local host. */ CIMNameSpace cns = new CIMNameSpace("", "root\security"); // Connect to the root\security namespace as root. cc = new CIMClient(cns, "root", "root_password"); // Get the Solaris_namespaceAcl class cimclass = cc.getClass(new CIMObjectPath("Solaris_namespaceAcl"); // Create a new instance of the Solaris_namespaceAcl class ci = cimclass.newInstance(); ... -
Set the capability property to the desired access rights. For example:
... /* Change the access rights (capability) to read/write to the root\molly namespace. */ ci.setProperty("capability", new CIMValue(new String("rw")); ci.setProperty("nspace", new CIMValue(new String("root\molly")); ... -
Update the instance. For example:
// Pass the updated instance to the CIM Object Manager cc.setInstance(new CIMObjectPath(), ci);
- © 2010, Oracle Corporation and/or its affiliates
