8.1 Installing Web Server 1 and Web Policy Agent 1
Use the following as your checklist for installing Web Server 1 and Web Policy Agent 1:
-
Import the root CA certificate into the Web Server 1 key store.
-
Configure the Web Policy Agent to use the new agent profile.
For this part of the deployment, you must have the JES 5 installer and Web Policy Agent installer mounted on the host Protected Resource 1. See 3.2 Downloading and Mounting the Java Enterprise System 2005Q4 Installer at the beginning of this manual.
Figure 8–1 Protected Resources and Policy Agents
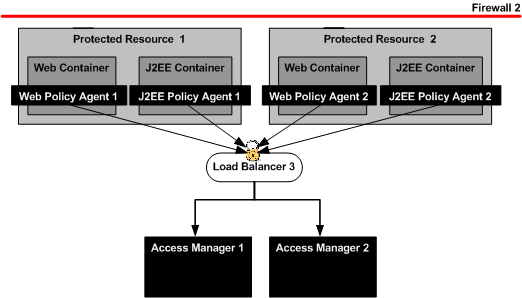
 To Install Web Server 1 on Protected Resource
1
To Install Web Server 1 on Protected Resource
1
-
As a root user, log into host ProtectedResource-1.
-
Start the Java Enterprise System installer with the -nodisplay option.
# cd /mnt/Solaris_sparc # ./installer -nodisplay
-
When prompted, provide the following information:
-
(Optional) During installation, you can monitor the log to watch for installation errors. Example:
# cd /var/sadm/install/logs
# tail —f Java_Enterprise_System_install.B xxxxxx
-
Upon successful installation, enter ! to exit.
-
Verify that the Web Server is installed properly.
-
Start the Web Server administration server to verify it starts with no errors.
# cd /opt/SUNWwbsvr/https-admserv
# ./stop; ./start
-
Run the netstat command to verify that the Web Server ports are open and listening.
# netstat -an | grep 8888 *.8888 *.* 0 0 49152 0 LISTEN
-
Go to the Web Server URL.
http://ProtectedResource-1.example.com:8888
-
Log in to the Web Server using the following information:
- Username
-
admin
- Password
-
web4dmin
You should be able to see the Web Server console. You can log out of the console now.
-
Start the Protected Resource 1 instance.
# cd /opt/SUNWwbsvr/https-ProtectedResource-1.example.com # ./stop; ./start
-
Run the netstat command to verify that the Web Server ports are open and listening.
# netstat -an | grep 1080 *.1080 *.* 0 0 49152 0 LISTEN
-
Go to the instance URL.
http://ProtectedResource-1.example.com:1080
You should see the default Web Server index page.
-
 To Install Web Policy Agent 1
To Install Web Policy Agent 1
Before You Begin
Due to a known problem with this version of the Web Policy Agent, you must start an X-display session on the server host using a program such as Reflections X or VNC, even though you use the command-line installer. For more information about this known problem, see http://docs.sun.com/app/docs/doc/819-2796/6n52flfoq?a=view#adtcd.
-
As a root user, log into to host ProtectedResource–1.
-
Download the Java System Web Policy Agents 2.2 package from the following website:
-
Unpack the downloaded package.
In this example, the package was downloaded into the directory /temp.
# cd /temp # gunzip sun-one-policy-agent-2.2-es6-solaris_sparc.tar.gz # tar —xvof sun-one-policy-agent-2.2-es6-solaris_sparc.tar
-
Start the Web Policy Agents installer.
# ./setup -nodisplay
-
When prompted, provide the following information:
When you are ready, press Enter to continue. <Press ENTER to Continue>
Press Enter.
Press ENTER to display the Sun Software License Agreement
Press Enter.
Have you read, and do you accept, all of the terms of the preceding Software License Agreement [no] y
Enter y.
Install the Sun Java(tm) System Access Manager Policy Agent in this directory [/opt] :
Accept the default value.
Enter information about the server instance this agent will protect. Host Name [ProtectedResource-2.example.com]:
Accept the default value.
Web Server Instance Directory []:
Enter
/opt/SUNWwbsvr/ https-ProtectedResource-1.example.com
Web Server Port [80]: :
Enter 1080.
Web Server Protocol [http]
Accept the default value.
Agent Deployment URI [/amagent]:
Accept the default value.
Enter the Sun Java(tm) System Access Manager Information for this Agent. Primary Server Host [ProtectedResource-2.example.com] :
For this example, enter the external-facing load balancer host name. Example: LoadBalancer-3.example.com
Primary Server Port [1080]
Enter the load balancer HTTP port number. For this example, enter 90.
Primary Server Protocol [http]:
Accept the default value.
Primary Server Deployment URI [/amserver]:
Accept the default value.
Primary Console Deployment URI [/amconsole] :
Accept the default value.
Failover Server Host [] :
Accept the default value.
Agent-Access Manager Shared Secret:
Enter the amldapuser password that was entered when Access Manager was installed. For this example, enter 4mld4puser .
Re-enter Shared Secret:
Enter the 4mld4puser password again to confirm it.
CDSSO Enabled [false]:
Accept the default value.
Press "Enter" when you are ready to continue.
First, see the next (Optional) numbered step. When you are ready to start installation, press Enter.
-
(Optional) During installation, you can monitor the log to watch for installation errors. Example:
# cd /var/sadm/install/logs # tail —f var/sadm/install/logs/ Sun_Java_tm__System_Access_Manager_Policy_Agent_install.Bxxxxxxxx
-
Modify the AMAgent.properties file.
# cd /etc/opt/SUNWam/agents/es6/ config/_opt_SUNWwbsvr_https-ProtectedResource-1.example.com
Make a backup of AMAgent.properties before setting the following property:
com.sun.am.policy.am.login.url = https://LoadBalancer-4.example.com:9443/distAuth/UI/Login?realm=users
-
Restart the Web Server.
# cd /opt/SUNWwbsvr/https-ProtectedResource-1.example.com # ./stop; ./start
Examine the Web Server log for startup errors.
# /opt/SUNWwbsvr/https-ProtectedResource-1.example.com/logs # vi errors
 To Verify that Web Policy Agent 1 Works Properly
To Verify that Web Policy Agent 1 Works Properly
-
Start a new browser and go to the Access Manager URL.
Example: https://loadbalancer-3.example.com:9443/amserver/console
-
Log in to the Access Manager console using the following information:
- Username
-
amadmin
- Password
-
4m4dmin1
-
Create a referral policy in the top-level realm.
-
On the Access Control tab, under Realms, click example.com.
-
Click the Policies tab.
-
On the Policies tab for example.com-Policies, click New Referral.
-
In the New Policy page, provide the following information:
- Name:
-
Referral URL Policy for users realm.
- Active:
-
Mark the Yes checkbox.
-
On the same page, in the Rules section, click New.
-
Select a Service Type.
On the page “Step 1 of 2: Select Service Type for the Rule,” select URL Policy Agent (with resource name)
-
Click Next.
-
On the page “Step 2 of 2: New Rule,” provide the following information:
- Name:
-
URL Rule for ProtectedResource-1
- Resource Name:
-
http://ProtectedResource-1.example.com:1080/*
-
Click Finish.
-
On the same page, in the Referrals section, click New.
-
In the New Referral — Sub Realm page, provide the following information:
- Name:
-
Sub-Realm users
- Filter:
-
Type an asterisk (*), and then click Search.
- Value:
-
In the list, choose users.
-
Click Finish.
-
On the New Policy page, click Create.
In the Policies tab for example.com — Policies, you should see the policy named “Referral URL Policy for users realm.”
-
-
Create a policy in the users realm.
-
Click Realms.
-
On the Access Control tab, under Realms, click the Realm Name users.
-
Click the Policies tab.
-
On the Policies tab for users-Policies, click New Policy.
-
In the New Policy page, provide the following information:
- Name:
-
URL Policy for ProtectedResource-1
- Active:
-
Mark the Yes checkbox.
-
On the same page, in the Rules section, click New.
-
On the page “Step 1 of 2: Select Service Type for the Rule,” click Next.
The Service Type “URL Policy Agent (with resource name) is the only choice.
-
On the page “Step 2 of 2: New Rule,” provide the following information:
- Name:
-
URL Rule for ProtectedResource-1
- Resource Name:
-
Click the URL listed in the Parent Resource Name list: http://ProtectedResource-1.example.com:1080/*
The URL is automatically added to the Resource Name field.
- GET:
-
Mark this checkbox, and select the Allow value.
- POST:
-
Mark this checkbox, and select the Allow value.
-
Click Finish.
-
-
Create a new subject.
On the New Policy page, in the Subjects section, click New.
-
Select the subject type and then click Next.
On the page “Step 1 of 2: Select Subject Type,” select the “Access Manager Identity Subject” type.
-
On the page “Step 2 of 2: New Subject — Access Manager Identity Subject,” provide the following information:
- Name:
-
Enter Test Subject.
- Filter:
-
Choose User, and then click Search. Four users are added to the Available list.
- Available:
-
In the list, selecttestuser1, and then click Add.
The user testuser1 is added to the Selected list.
-
Click Finish.
-
-
In the New Policy page, click Create.
On the Policies tab for users-Policies, the new policy “URL Policy for ProtectedResource-1” is now in the Policies list.
-
Log out of the console.
-
Verify that an authorized user can access the Web Server 1.
-
Go to the following URL:
http://ProtectedResource-1.example.com:1080
-
Log in to Access Manager using the following information:
- Username
-
testuser1
- Password
-
password
You should see the default index.html page for Web Server 1.
The user testuser1 was configured in the test policy to be allowed to access Protected Resource 1.
-
-
Verify that an unauthorized user cannot access the Web Server 1.
-
Go to the following URL:
http://ProtectedResource-1.example.com:1080
-
Log in to Access Manager using the following information:
- Username
-
testuser2
- Password
-
password
You should see the message, “You're not authorized to view this page.”
The user testuser2 was not included in the test policy tat allows access to Protected Resource 1.
-
 To Import the Root CA Certificate into the
Web Server 1 Key Store
To Import the Root CA Certificate into the
Web Server 1 Key Store
The Web Policy Agent on Protected Resource 1 connects to Access Manager servers through Load Balancer 3. The load balancer is SSL-enabled, so the agent must be able to trust the load balancer SSL certificate in order to establish the SSL connection. To do this, import the root CA certificate that issued the Load Balancer 3 SSL server certificate into the Web Policy Agent certificate store.
Before You Begin
Obtain the root CA certificate, and copy it to ProtectedResource-1.
-
Copy the root CA certificate to Protected Resource 1.
-
Open a browser, and go to the Web Server 1 administration console.
http://ProtectedResource-1.example.com:8888
-
Log in to the Web Server 2 console using the following information:
- User Name:
-
admin
- Password:
-
web4dmin
-
In the Select a Server field, select ProtectedResource-1.example.com, and then click Manage.
Tip –If a “Configuration files have not been loaded” message is displayed, it may be that the administration server has never been accessed, and so the configuration files have never been loaded. First click Apply, and then click Apply Changes. The configuration files are read, and the server is stopped and restarted.
-
Click the Security tab.
-
On the Initialize Trust Database page, enter a Database Password.
Enter the password again to confirm it, and then click OK.
-
In the left frame, click Install Certificate and provide the following information, and then click OK:
- Certificate For:
-
Choose Trusted Certificate Authority (CA).
- Key Pair File Password:
-
password
- Certificate Name:
-
OpenSSL_CA_Cert
- Message in this File:
-
/export/software/ca.cert
-
Click Add Server Certificate.
-
Click Manage Certificates.
The root CA Certificate name OpenSSL_CA_Cert is included in the list of certificates.
-
Click the Preferences tab.
-
Restart Web Server 2.
On the Server On/Off page, click Server Off. When the server indicates that the administration server is off, click Server On.
-
Configure the Web Policy Agent 1 to point to the Access Manager SSL port.
-
Edit the AMAgent.properties file.
# cd /opt/SUNWam/agents/es5/config/ _optSUNWwbsvr_https=ProtectedResource-1.example.com
Make a backup of the AMAgent.properties file before setting the following property:
# com.sun.am.naming.url = https://LoadBalancer-3.example.com:9443/amserver/namingservice
-
Save the file.
-
-
Restart Web Server 1.
# cd /opt/SUNWwbsvr/https-ProtectedResource-1.example.com # ./stop; ./start
 To Verify that the Web Policy Agent is Working
Properly
To Verify that the Web Policy Agent is Working
Properly
-
Verify that an authorized user can access the Web Server 1.
-
Go to the following URL:
http://ProtectedResource-1.example.com:1080
-
Log in to Access Manager using the following information:
- Username
-
testuser1
- Password
-
password
You should see the default index.html page for Web Server 1.
The user testuser1 was configured in the test policy to be allowed to access Protected Resource 1.
-
-
Verify that an unauthorized user cannot access the Web Server 1.
-
Go to the following URL:
http://ProtectedResource-1.example.com:1080
-
Log in to Access Manager using the following information:
- Username
-
testuser2
- Password
-
password
You should see the message, “You're not authorized to view this page.”
The user testuser2 was not included in the test policy tat allows access to Protected Resource 1.
-
 To Create an Agent Profile on Access Manager
To Create an Agent Profile on Access Manager
The web agent will, by default, use the account with the uid UrlAccessAgent to authenticate to Access Manager. Creating an agent profile is not a requirement for Web Policy Agents. You can use the default values and never change the Web Policy Agent user name. However, in certain cases, you might want to change these default values. For example, if you want to audit the interactions between multiple agents and the Access Manager server, you want be able to distinguish one agent from another. This would not be possible if all the agents used the same default agent user account. For more information, see the Sun Java System Access Manager Policy Agent 2.2 User’s Guide.
-
Create an agent profile on Access Manager.
This new account will be used by Web Policy Agent 1 to access the Access Manager server.
-
Go to Access Manage load balancer URL:
https://LoadBalancer-3.example.com:9443/amserver/UI/Login
-
Log in to the Access Manager console using the following information:
- Username
-
amadmin
- Password
-
4m4dmin1
-
On the Access Control tab, under Realms, click the realm name example.com.
-
Click the Subjects tab.
-
Click the Agents tab.
-
On the Agent page, click New.
-
On the New Agent page, provide the following information:
- ID:
-
webagent-1
- Password:
-
web4gent1
- Password Confirm:
-
web4gent1
- Device State:
-
Choose Active.
-
Click Create.
The new agent webagent–1 is now display in the list of Agent Users.
-
 To Configure the Web Policy Agent to Use the
New Agent Profile
To Configure the Web Policy Agent to Use the
New Agent Profile
-
Log in to as a root user to Protected Resource 1.
-
Run the cypt_util utility.
The utility encrypts the password.
# cd /opt/SUNWam/agents/bin # ./crypt_util web4gent1 BXxzBswD+PZdMRDRMXQQA==
Copy the encrypted password, and save it in a text file.
-
Edit the AMAgent.properties file.
# cd /etc/opt/SUNWam/agents/es6/ config/_opt_SUNWwbsvr_https-ProtectedResource-1.example.com
Make a backup of AMAgent.properties you make the following change in the file:
com.sun.am.policy.am.password = webagent-1 com.sun.am.policy.am.password = BXxzBswD+PZdMRDRMXQQA==
Use the encrypted password obtained in the previous step.
Save the file.
-
Restart Web Server 1.
# cd /opt/SUNWwbsvr/https-ProtectedResource-1.example.com # ./stop; ./start
 To Verify that the Web Policy Agent
is Working Properly
To Verify that the Web Policy Agent
is Working Properly
-
Verify that an authorized user can access the Web Server 1.
-
Go to the following URL:
http://ProtectedResource-1.example.com:1080
-
Log in to Access Manager using the following information:
- Username
-
testuser1
- Password
-
password
You should see the default index.html page for Web Server 1.
The user testuser1 was configured in the test policy to be allowed to access Protected Resource 1.
-
-
Verify that an unauthorized user cannot access the Web Server 1.
-
Go to the following URL:
http://ProtectedResource-1.example.com:1080
-
Log in to Access Manager using the following information:
- Username
-
testuser2
- Password
-
password
You should see the message, “You're not authorized to view this page.”
The user testuser2 was not included in the test policy tat allows access to Protected Resource 1.
-
- © 2010, Oracle Corporation and/or its affiliates
