6.1 Installing and Deploying the Distributed Authentication UI Servers
Use the following as your checklist for installing and Deploying the Distributed Authentication UI servers:
-
Install a container for Distributed Authentication UI Server 1.
-
Install a container for Distributed Authentication UI Server 2.
-
Import the root CA certificate for the Access Manager load balancer into Authentication UI Server 1.
-
Verify that authentication through Authentication UI Server 1 is successful.
-
Import the root CA certificate for the Access Manager load balancer into Authentication UI Server 2.
-
Verify that authentication through Authentication UI Server 2 is successful.
Figure 6–1 Distributed Authentication
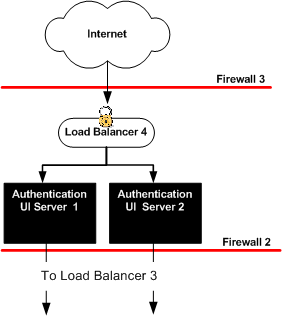
The Java ES installer must be mounted on the host AuthenticationUI-1 where you will install Web Server. See the section “To Download and Unpack the Java Enterprise System 2005Q4 Installer”3.2 Downloading and Mounting the Java Enterprise System 2005Q4 Installer in this document.
 To Install a Container for Distributed Authentication
UI Server 1
To Install a Container for Distributed Authentication
UI Server 1
-
As a root user, log in to host Authentication UI-1.
-
Start the Java Enterprise System installer with the -nodisplay option.
# /mnt/Solaris_sparc # ./installer -nodisplay
-
When prompted, provide the following information:
 To Build and Deploy Distributed Authentication
UI Server 1
To Build and Deploy Distributed Authentication
UI Server 1
-
Log in as a root user to AccessManager-1.
For this example, log into AccessManager-1.
-
Copy the Distributed Authentication UI files to another workspace on the AccessManager-1.
# cd /opt/SUNWcomm/SUNWam # cp README.distAuthUI amauthistui.war Makefile.distAuthUI /opt/SUNWam
-
Edit the Makefile.distAuthUI file and set the following properties:
JAVA_HOME=/usr/jdk/entsys-j2se/ SERVER_PROTOCOL=http SERVER_HOSTNAME=LoadBalancer-3.example.com SERVER_PORT=90 SERVER_DEPLOY_URI=amserver DISTAUTH_PROTOCOL=http DISTAUTH_HOSTNAME=AuthenticationUI-1.example.com DISTAUTH_PORT=1080 DISTAUTH_DEPLOY_URI=/distAuth APPLICATION_USERNAME=amadmin APPLICATION_PASSWORD=4m4dmin1 NOTIFICATION_URL=http://AuthenticationUI-1.example.com:1080/ distAuth/notificationservice DEBUG_LEVEL=message DEBUG_DIR=/tmp/distAuth COOKIE_ENCODE=false DISTAUTH_VERSION=7.0
-
Create the war file by issuing the following command
# /usr/sfw/bin/gmake -f Makefile.distAuthUI
This creates a war file named distAuthUI.war .
-
Rename the generated file.
# mv distAuthUI.war distAuth_AccessManager-1.war
-
Copy distAuth_AccessManager-1.war from the local host where you built the Distributed Authentication UI server (AccessManager–1) to the remote host where the Distributed Authentication UI server will be deployed (AuthenticationUI-1).
In this deployment example, the desintation directory is /tmp.
-
Log in as a root user to the Authentication UI-1 Web Server.
-
Start the Authentication UI-1 Web Server.
# cd /opt/SUNWwbserver # #cd https-AuthenticationUI-1.example.com # # ./start
-
Deploy the Distributed Authentication UI WAR file.
On the host AuthenticationUI-1, in the directory where you copied the distAuth_AuthenticationUI-1.war file, run the wdeploy command using the following form:
wdeploy deploy -u uri_path -i instance -v vs_id
[ [-V verboseLevel ]| [-q] ] [-n] [-d directory] war_file
For example, in this Deployment Example:
# cd /opt/SUNWwbsvr/bin/https/bin # ./wdeploy deploy -u /distAuth -i https-AuthenticationUI-1.example.com -v https-AuthenticationUI-1.example.com -d /opt/SUNWwbsvr/https-AuthenticationUI-1.example.com/webapps/distAuth /tmp/distAuth_AuthenticationUI-1.war
-
Restart Web Server.
# cd /opt/SUNWwbserver # cd https-AuthenticationUI-1.example.com # ./stop; ./start server has been shutdown # Sun ONE Web Server 6.1SP5 B06/23/2005 18:00 info: CORE3016: daemon is running as super-user info: CORE5076: Using [Java HotSpot(TM) Server VM, Version 1.5.0_04] from [Sun Microsystems Inc.] # info: WEB0100: Loading web module in virtual server [https-AuthenticationUI-1.example.com] at [/distAuth] info: WEB0100: Loading web module in virtual server [https-AuthenticationUI-1.example.com] at [/search] info: HTTP3072: [LS ls1] http://AuthenticationUI-1.example.com:8080 ready to accept requests startup: server started successfully
Next Steps
The web module is loaded in the following directory:
/opt/SUNWwbsvr/https-AuthenticationUI-1.example.com/webapps/distAuth
 To Install a Container for Distributed Authentication
UI Server 2
To Install a Container for Distributed Authentication
UI Server 2
-
As a root user, log in to host AuthenticationUI-2.
-
Start the Java Enterprise System installer with the -nodisplay option.
# /mnt/Solaris_sparc # ./installer -nodisplay
-
When prompted, provide the following information:
Welcome to the Sun Java(TM) Enterprise System; serious software made simple... <Press ENTER to Continue>
Press Enter.
<Press ENTER to display the Software License Agreement>
Press Enter.
Have you read, and do you accept, all of the termsof the preceding Software License Agreement [No]
Enter y.
Please enter a comma separated list of languages you would like supported with this installation [8]
Enter 8 for “English only.”
Enter a comma separated list of products to install,or press R to refresh the list []
Enter 3 to select Web Server.
Press "Enter" to Continue or Enter a comma separated list of products to deselect... [1]
Press Enter.
Enter 1 to upgrade these shared components and 2 to cancel [1]
You are prompted to upgrade shared components only if the installer detects that an upgrade is required.
Enter 1 to upgrade shared components.
Enter the name of the target installation directory for each product: Web Server [/opt/SUNWwbsvr] :
Accept the default value.
System ready for installation Enter 1 to continue [1]
Enter 1.
1. Configure Now - Selectively override defaults or express through 2. Configure Later - Manually configure following installation Select Type of Configuration [1]
Enter 1.
Common Server Settings Enter Host Name [AuthenticationUI-2]
Accept the default value.
Enter DNS Domain Name [example.com]
Accept the default value.
Enter IP Address [xxx.xx.87.180]
Accept the default value.
Enter Server admin User ID [admin]
Enter admin.
Enter Admin User's Password (Password cannot be less than 8 characters) []
For this example, enter web4dmin.
Confirm Admin User's Password []
Enter the same password to confirm it.
Enter System User [root]
Accept the default value.
Enter System Group [root]
Accept the default value.
Enter Server Admin User ID [admin]
Enter admin.
Enter Admin User's Password []
For this example, enter web4dmin.
Enter Host Name [AuthenticationUI-2.example.com]
Accept the default value.
Enter Administration Port [8888]
Enter 1080.
Enter Administration Server User ID [root]
Accept the default value.
Enter System User ID [webservd]
Enter root.
Enter System Group [webservd]
Enter root.
Enter HTTP Port [80]
Enter 8888.
Enter content Root [/opt/SUNWwbsvr/docs]
Accept the default value.
Do you want to automatically start Web Serverwhen system re-starts.(Y/N)[N]
Accept the default value.
Ready to Install 1. Install 2. Start Over 3. Exit Installation What would you like to do [1]
When ready to install, enter 1.
 To Build and Deploy Distributed Authentication
UI Server 2
To Build and Deploy Distributed Authentication
UI Server 2
-
Log in as a root user to an Access Manager host.
For this example, log into AccessManager-2.
-
Copy the Distributed Authentication UI files to another workspace on the same (local) host.
cd /opt/SUNWcomm/SUNWam cp README.distAuthUI amauthistui.war Makefile.distAuthUI /opt/SUNWam
-
Edit the Makefile.distAuthUI file and set the following properties:
JAVA_HOME=/usr/jdk/entsys-j2se/ SERVER_PROTOCOL=http SERVER_HOSTNAME=LoadBalancer-3.example.com SERVER_PORT=90 SERVER_DEPLOY_URI=amserver DISTAUTH_PROTOCOL=http DISTAUTH_HOSTNAME=AuthenticationUI-2.example.com DISTAUTH_PORT=1080 DISTAUTH_DEPLOY_URI=/distAuth APPLICATION_USERNAME=amadmin APPLICATION_PASSWORD=4m4dmin1 NOTIFICATION_URL=http://AuthenticationUI-2.example.com:1080/ distAuth/notificationservice DEBUG_LEVEL=message DEBUG_DIR=/tmp/distAuth COOKIE_ENCODE=false DISTAUTH_VERSION=7.0
-
Create the war file by issuing the following command
gmake -f Makefile.distAuthUI.war
This creates a war file named distAuth_deploy.war.
-
Rename the generated file.
mv distAuthUI.war distAuth_AccessManager-2.war
-
Copy distAuth_AccessManager-2.war from the local host where you built the Distributed Authentication UI (AccessManager—2) to the remote host where the Distributed Authentication UI will be deployed (AuthetnicationUI-2).
# cp distAuth_AccessManager-2.war /net/AuthenticationUI-2/ tmp/distAuth_ AuthenticationUI-2.war
-
Deploy the Distributed Authentication UI WAR file.
On the host AuthenticationUI-2, in the directory where you copied the distAuth_ AuthenticationUI-2.war file, run the wdeploy command using the following form:
wdeploy deploy -u uri_path -i instance -v vs_id
[ [-V verboseLevel ]| [-q] ] [-n] [-d directory] war_file
For example, in this Deployment Example:
# ./wdeploy deploy -u /distAuth -i https-AuthenticationUI-2.example.com -v https-AuthenticationUI-2.example.com -d /opt/SUNWwbsvr/https-AuthenticationUI-2.example.com/webapps/distAuth /tmp/distAuth_ AuthenticationUI-2.war
-
Restart Web Server.
# cd /opt/SUNWwbserver # cd https-AuthenticationUI-2.example.com # ./stop; ./start server has been shutdown # Sun ONE Web Server 6.1SP5 B06/23/2005 18:00 info: CORE3016: daemon is running as super-user info: CORE5076: Using [Java HotSpot(TM) Server VM, Version 1.5.0_04] from [Sun Microsystems Inc.] # info: WEB0100: Loading web module in virtual server [https-AuthenticationUI-2.example.com] at [/distAuth] info: WEB0100: Loading web module in virtual server [https-AuthenticationUI-2.example.com] at [/search] info: HTTP3072: [LS ls1] http://AuthenticationUI-2.example.com:8080 ready to accept requests startup: server started successfully
Next Steps
The web module is loaded in the following directory:
/opt/SUNWwbsvr/https-AuthenticationUI-2.example.com/webapps/distAuth/distAuth
 To Import the Root CA Certificate for the
Access Manager Load Balancer into Authentication UI Server 1
To Import the Root CA Certificate for the
Access Manager Load Balancer into Authentication UI Server 1
In this procedure, you import a Certificate Authority (CA) certificate. The certificate enables the Authentication UI server to trust the certificate from the Access Manager load balancer (Load Balancer 3), and to establish trust with the certificate chain that is formed from the CA to the certificate.
-
Log in as root to Authentication UI Server 2.
-
Copy the root CA certificate into a directory.
After the certificate authority (CA) sends you the certificate, copy the certificate text into a file. In this example, the file is /export/software/ca.cer.
-
Import the root CA certificate into the Java certificate store.
# /usr/jdk/entsys-j2se/jre/bin/keytool -import -trustcacerts -alias OpenSSLTestCA -file /export/software/ca.cer -keystore /usr/jdk/entsys-j2se/jre/lib/security/cacerts -storepass changeit Owner: EMAILADDRESS=nobody@nowhere.com, CN=OpenSSLTestCA, OU=Sun, O=Sun,L=Santa Clara, ST=California C=US Issuer: EMAILADDRESS=nobody@nowhere.com, CN=OpenSSLTestCA, OU=Sun, O=Sun,L=Santa Clara, ST=California C=US Serial number: 97dba0aa26db6386 Valid from: Tue Apr 18 07:66:19 PDT 2006 until: Tue Jan 13 06:55:19 PST 2009 Certificate fingerprints: MD5: 9f:57:ED:B2:F2:88:B6:E8:0F:1E:08:72:CF:70:32:06 SHA1: 31:26:46:15:C5:12:5D:29:46:2A:60:A1:E5:9E:26:64:36:80:E4:70 Trust this certificate: [no] yes Certificate was added to keystore. -
Verify that the root CA certificate was imported into the keystore.
# /usr/jdk/entsys-j2se/jre/bin/keytool -list -keystore ./cacerts -storepass changeit | grep -i open openssltestca, Nov 8, 2006, trustedCertEntry
-
Restart AuthenticationUI-1.
# cd /opt/SUNWwwbsvr/https-AuthenticationUI-1.example.com # ./stop server has been shutdown #./start Sun ONE Web Server 6.1SP5 B06/23/2005 18:00 info: CORE3016: daemon is running as super-user info: CORE5076: Using [Java HotSpot(TM) Server VM, version 1.5.0_04 ] from [Sun Microsystems Inc.] info: WEB0100: Loading web module in virtual server https-AuthenticationUI-1.example.com] at [/distAuth] info: WEB0100: Loading web module in virtual server https-AuthenticationUI-1.example.com] at [/search] info: HTTP3072: [LS is 1] http://AuthenticationUI-1.example.com:1080 ready to accept requests startup: server started successfully
 To Verify that Authentication Through Authentication
UI Server 1 is Successful
To Verify that Authentication Through Authentication
UI Server 1 is Successful
Find a host that has direct network connectivity to both Authentication UI servers and the external facing load balancer of the Access Manager servers. One natural place is the Distributed Authentication UI server host itself.
-
Open a web browser and go to the following URL:
http://AuthenticationUI-1.example.com:1080/distAuth/UI/Login?goto= http://LoadBalancer-3.example.com:90
-
Log in to the Access Manager console using the following information:
- Username
-
amadmin
- Password
-
4m4dmin1
After successful authentication, you should be redirected to the index page for Access Manager's Web Server.
-
Log out of the Access Manager console.
 To Import the Root CA Certificate for the
Access Manager Load Balancer into Authentication UI Server 2
To Import the Root CA Certificate for the
Access Manager Load Balancer into Authentication UI Server 2
In this procedure, you import a Certificate Authority (CA) certificate. The certificate enables the Authentication UI server to trust the certificate from the Access Manager load balancer (Load Balancer 3), and to establish trust with the certificate chain that is formed form the CA to the certificate.
-
Log in as a root user to Authentication UI Server 2.
-
Copy the root CA certificate into a directory.
After the certificate authority (CA) sends you the certificate, copy the certificate text into a file. In this example, the file is /export/software/ca.cer.
-
Import the root CA certificate into the Java certificate store.
# /usr/jdk/entsys-j2se/jre/bin/keytool -import -trustcacerts -alias OpenSSLTestCA -file /export/software/ca.cer -keystore /usr/jdk/entsys-j2se/jre/lib/security/cacerts -storepass changeit Owner: EMAILADDRESS=nobody@nowhere.com, CN=OpenSSLTestCA, OU=Sun, O=Sun,L=Santa Clara, ST=California C=US Issuer: EMAILADDRESS=nobody@nowhere.com, CN=OpenSSLTestCA, OU=Sun, O=Sun,L=Santa Clara, ST=California C=US Serial number: 97dba0aa26db6386 Valid from: Tue Apr 18 07:66:19 PDT 2006 until: Tue Jan 13 06:55:19 PST 2009 Certificate fingerprints: MD5: 9f:57:ED:B2:F2:88:B6:E8:0F:1E:08:72:CF:70:32:06 SHA1: 31:26:46:15:C5:12:5D:29:46:2A:60:A1:E5:9E:26:64:36:80:E4:70 Trust this certificate: [no] yes Certificate was added to keystore. -
Verify that the root CA certificate was imported into the keystore.
# /usr/jdk/entsys-j2se/jre/bin/keytool -list -keystore ./cacerts -storepass changeit | grep -i open openssltestca, Nov 8, 2006, trustedCertEntry
-
Restart AuthenticationUI-2.
# cd /opt/SUNWwwbsvr/https-AuthenticationUI-2.example.com # ./stop server has been shutdown #./start Sun ONE Web Server 6.1SP5 B06/23/2005 18:00 info: CORE3016: daemon is running as super-user info: CORE5076: Using [Java HotSpot(TM) Server VM, version 1.5.0_04 ] from [Sun Microsystems Inc.] info: WEB0100: Loading web module in virtual server [https-AuthenticationUI-2.example.com] at [/distAuth] info: WEB0100: Loading web module in virtual server [https-AuthenticationUI-2.example.com] at [/search] info: HTTP3072: [LS is 1] http://AuthenticationUI-2.example.com:1080 ready to accept requests startup: server started successfully
 To Verify that Authentication Through Authentication
UI Server 2 is Successful
To Verify that Authentication Through Authentication
UI Server 2 is Successful
Find a host that has direct network connectivity to both Authentication UI servers and the external facing load balancer of the Access Manager servers. One natural place is the Distributed Authentication UI server host itself.
-
Open a web browser and go to the following URL:
http://AuthenticationUI-2.example.com:1080/distAuth/UI/Login?goto= http://LoadBalancer-3.example.com:90
-
Log in to the Access Manager console using the following information:
- Username
-
amadmin
- Password
-
4m4dmin1
After successful authentication, you should be redirected to the index page for Access Manager's Web Server.
- © 2010, Oracle Corporation and/or its affiliates
